That unsettling feeling that someone might be watching you is hard to shake, and learning how to check if my phone is being tracked is the first step to regaining your peace of mind. In today’s world, sophisticated spyware and stalkerware can be installed on your device without your knowledge, silently monitoring everything from your private messages to your real-time location. This isn’t just paranoia; it’s a very real threat to your privacy and safety.
As a cybersecurity specialist at Safelyo, I’ve seen firsthand how these invasive tools work and the distress they cause. But feeling anxious doesn’t have to be the end of the story. This guide is designed to empower you, transforming uncertainty into clear, actionable steps.
In this comprehensive diagnostic guide, you’ll discover:
- The 10 most common warning signs of a compromised phone.
- A step-by-step checklist to actively search for spyware on Android and iPhone.
- A clear action plan for what to do if you find something suspicious.
- Proven methods to protect your phone from future attacks.
Don’t let fear take control. Let’s turn your anxiety into action and secure your digital life, starting right now.
Feeling unsafe? Do this first.
If your gut tells you something is seriously wrong, take these immediate steps before you even finish reading this article.
| Immediate Step | What to Do and Why |
| 1. Disconnect | Turn off your Wi-Fi and mobile data. I always tell people to cut the connection first. Spyware needs the internet to send your data out, so this is like shutting the door on the thief. It buy you crucial time to investigate safely. |
| 2. Check Permissions | Do a quick 30-second review. Go to your phone’s settings and look at which apps can access your camera, microphone, and location. A simple game that wants access to your contacts is a huge red flag. |
| 3. Run a Scan | Use a trusted mobile security app. If you already have one from a reputable source like Norton or Bitdefender, run a full system scan immediately to catch any known threats. |
| 4. Don’t Panic | Take a deep breath. Seriously. Panicking can lead to mistakes. You’re in the right place, and this guide will give you the clear, step-by-step instructions you need to take back control. |
1. Who might be tracking your phone? Understanding the threats
Before we dive into the technical signs, it’s important to understand who might be behind the tracking. In my experience helping people secure their devices, knowing the potential source of the threat makes it much easier to find and eliminate. The “who” often tells you the “how.”
Here are the most common culprits:
- Stalkerware from someone you know
This is, unfortunately, the most common scenario I encounter. It involves someone with physical access to your phone, like a current or former partner, a family member, or even a roommate, installing a hidden app.
Simple example: They might borrow your phone for a few minutes “to make a call,” but in that time, they install an app disguised with a generic name like “System Service” or “Backup.” This app then silently reports your location, messages, and calls back to them.
- Commercial spyware bought online
Some companies openly sell powerful spy software, often marketing it deceptively for “employee monitoring” or “parental control.” These tools are incredibly invasive and can be used for malicious purposes.
Simple example: Think of a software that, once installed on your phone, lets someone else view your screen in real-time from their own computer, almost as if they were looking over your shoulder. They can see every tap you make and every message you type.
- Malware from phishing attacks
This type of tracking is usually motivated by financial gain. Criminals trick you into installing the malware yourself through deceptive links.
Simple example: You receive a text message that looks like it’s from a delivery service like FedEx, claiming there’s a problem with your package. The message urges you to click a link to “track your shipment.” That link leads to a fake website that downloads spyware onto your phone, which then steals your banking passwords.
- Government or law enforcement agencies
This is what you see in spy movies. While it’s technically possible, this type of surveillance is highly targeted, legally complex, and requires warrants. Frankly, unless you’re a person of significant interest to a government, this is the least likely scenario. For 99.9% of people, the threat comes from one of the first three categories.

Now that you have a better idea of the potential threats, let’s look at the specific warning signs your phone might be giving you.
2. The 10 warning signs that your phone is being tracked
Spyware is designed to be sneaky, but it almost always leaves subtle clues. From my years of analyzing compromised devices, I’ve learned that it’s rarely one single sign, but a pattern of unusual behavior that exposes a hidden tracker. Think of yourself as a detective and your phone as the crime scene. Here are the clues to look for.
2.1. #1 – Your battery drains unusually fast
This is the most common complaint I hear. Spyware is constantly working in the background, logging your keystrokes, tracking your location via GPS, and recording audio. All that activity consumes a lot of power.
Imagine leaving Google Maps running all day, even when you’re not driving. That’s the kind of drain spyware can cause. If your phone used to last a full day and now suddenly struggles to make it to lunchtime without a change in your habits, it’s a major red flag.
2.2. #2 – Your phone is abnormally hot
A phone that’s warm to the touch, even when you think it’s idle, is a classic symptom. That heat is generated by the phone’s processor working overtime. While it’s normal for a phone to get warm during a long gaming session or while charging, it shouldn’t feel like a hand warmer when it’s just sitting on the table.
Expert tip:
Do the “pocket test.” If you pull your phone out of your pocket after not using it for an hour and it’s surprisingly warm, something is running in the background.
2.3. #3 – You see a spike in data usage
Spyware is useless if it can’t send the information it collects back to the person monitoring you. This transmission uses your mobile data or Wi-Fi.
Think of your data plan like a bucket of water. Spyware is like a hidden leak, constantly dripping water out. You won’t notice it at first, but at the end of the month, your bill shows a massive overage. Check your phone’s data usage settings; a sudden, unexplained increase is a digital breadcrumb trail leading straight to a data-hungry app.
2.4. #4 – Your phone reboots or acts strangely
Does your phone’s screen light up for no reason? Do apps open or close on their own? Does it randomly restart? These are signs that someone could have remote access to your device. While modern spyware tries to be more discreet, poorly made or malfunctioning versions can cause these glitches.
2.5. #5 – You receive bizarre text messages
I’ve seen cases where a user receives text messages that look like complete gibberish, just random strings of letters, numbers, and symbols. These aren’t always wrong numbers. Some older or simpler spyware apps use coded SMS messages as a way for the tracker to send commands to the device, like “start recording audio now.”
2.6. #6 – There are strange sounds during calls
This is rarer nowadays with digital calls, but it’s still possible. If you frequently hear persistent static, clicking, or a faint echo during your phone calls (and you’ve ruled out bad reception), it could be a sign that a third-party app is intercepting and recording your conversations.
2.7. #7 – It takes a long time to shut down
When you tell your phone to shut down, it has to close all running processes first. If a malicious app is actively trying to finish transmitting data, it can hang up the shutdown process. If you notice your phone’s shutdown sequence suddenly takes much longer than usual, it’s trying to close something that doesn’t want to be closed.
2.8. #8 – You find apps you don’t remember installing
This is a dead giveaway. I always advise people to scroll through their entire app list, not just their home screen. Spyware often disguises itself with generic names like “System Service,” “Sync Manager,” or “WifiService” to blend in and avoid suspicion. If you see an app and think, “I have no idea what that is,” you need to investigate it immediately.
2.9. #9 – Your camera or microphone indicator turns on unexpectedly
This is a fantastic security feature in modern Android and iOS. You’ll see a small green or orange dot in the corner of your screen when an app is using your camera or microphone. If you see that dot appear when you’re just scrolling through your home screen or using an app that has no business using them (like a calculator), you are potentially being watched or listened to in that exact moment.
2.10. #10 – Your location or Bluetooth turns on by itself
Many tracking apps rely on GPS to pinpoint your location. If you are diligent about turning off your location services to save battery, but you find them mysteriously turned back on, an app is likely responsible. The same goes for Bluetooth, which can be used for proximity tracking.
3. The diagnostic checklist: How to actively check for spyware
Recognizing the warning signs is the first step. Now, it’s time to roll up our sleeves and actively search for evidence. In my diagnostic process, I always move from general checks to platform-specific ones. This method is efficient and ensures we don’t miss anything.
3.1. For both Android and iPhone users
These initial checks are your universal first line of investigation, regardless of the phone you own.
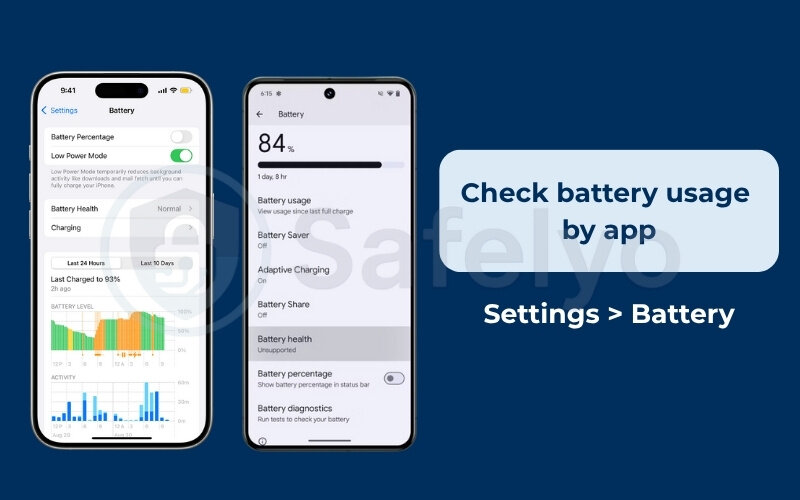
- Check battery usage by app:
Go into your phone’s Settings > Battery. This screen will show you a list of apps and the percentage of battery each one has consumed. You’re looking for anomalies. It’s normal to see your browser or a social media app at the top if you use them a lot. It is not normal to see an unknown app or a utility you never use consuming 20% of your battery.
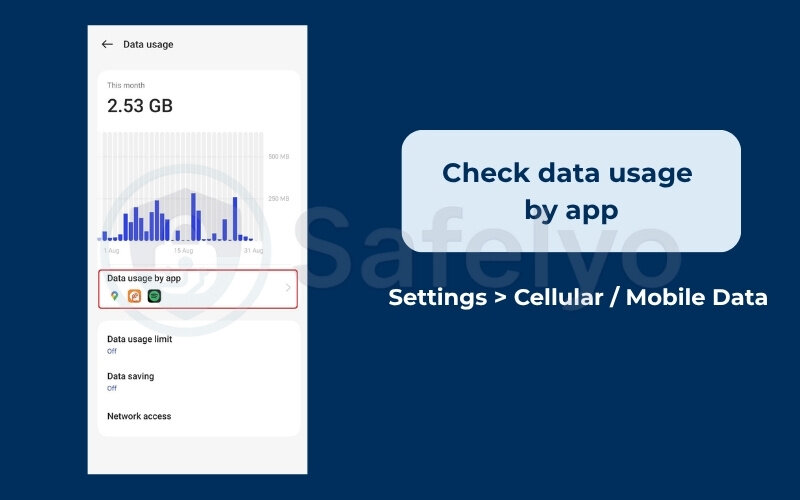
- Check data usage by app:
Similar to the battery check, go to Settings > Cellular / Mobile Data. Review the list of apps using your data. I once helped someone who discovered an app named “DeviceHealth” had used over 2GB of mobile data in a month. The app was disguised as spyware, and the 2GB was the user’s private data being uploaded.
- Run a reputable antivirus scan:
The easiest way to find known spyware is to let a professional tool do the work. Install a security app from a trusted brand like Norton, Bitdefender, or Avast and run a full system scan. These apps have extensive databases of known threats and can often identify and quarantine malicious software you might miss on your own.
3.2. Checking specifically on Android
Android’s open nature makes it more flexible, but also a more common target for spyware. Here’s where to look.
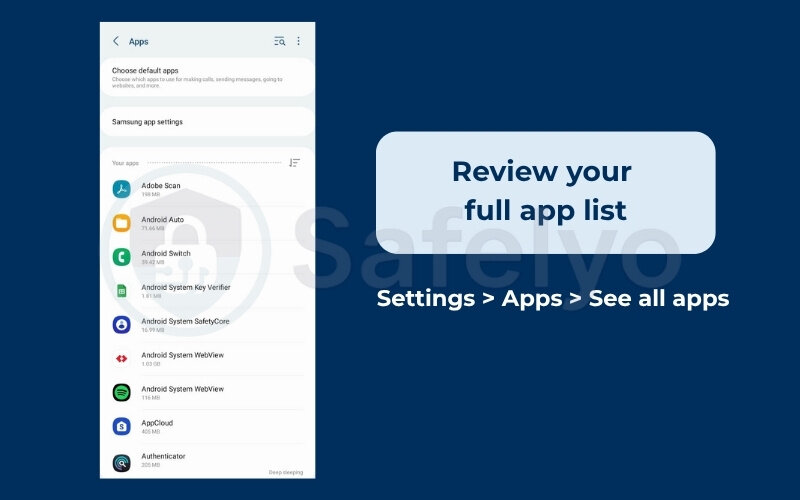
- Review your full app list (not just the home screen):
Go to Settings > Apps > See all apps. Take your time and scroll through the entire list. Spyware won’t put itself on your home screen. Look for apps with suspicious names or apps you know for a fact you did not install.
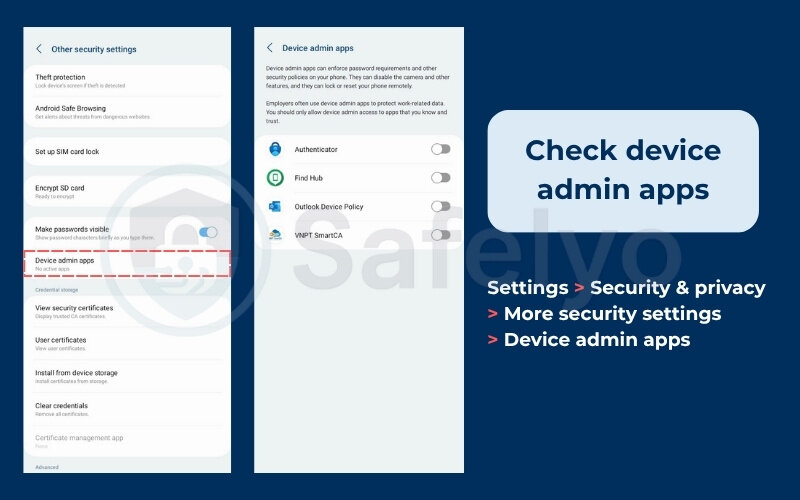
- Check device admin apps:
This is one of the most critical checks. Go to Settings > Security & privacy > More security settings > Device admin apps. This permission gives an app powerful control, like the ability to erase your phone or change your screen lock. No app should have this permission unless you explicitly trust it (like a corporate email app from your employer). If you see an unrecognized app here, this is a serious red flag. Disable its access immediately.
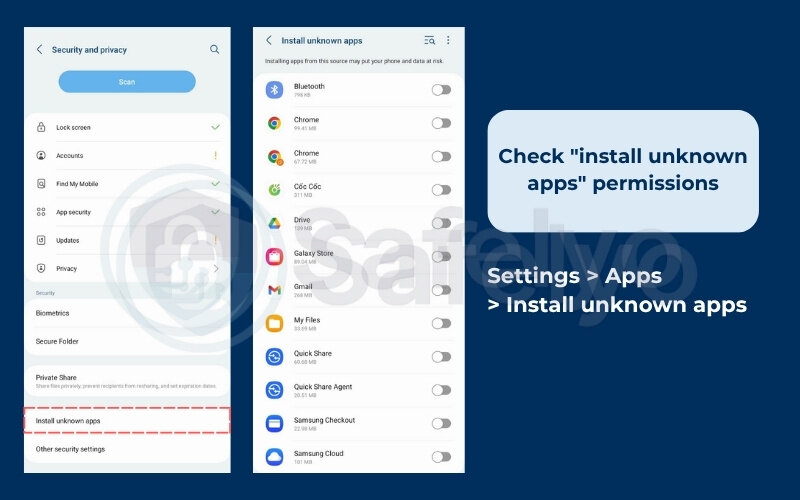
- Check “install unknown apps” permissions:
This feature, also known as sideloading, is how most spyware gets onto Android phones outside of the official Play Store. Go to Settings > Apps > Special app access > Install unknown apps. This will show you which apps on your phone are allowed to install other apps. For example, your Chrome browser might have this permission. If you see an app you don’t recognize with this permission, disable it.
3.3. Checking specifically on iPhone
While iPhones are generally more secure due to Apple’s “walled garden” ecosystem, they are not immune. Infection is less common, but it does happen, usually in one of these ways.
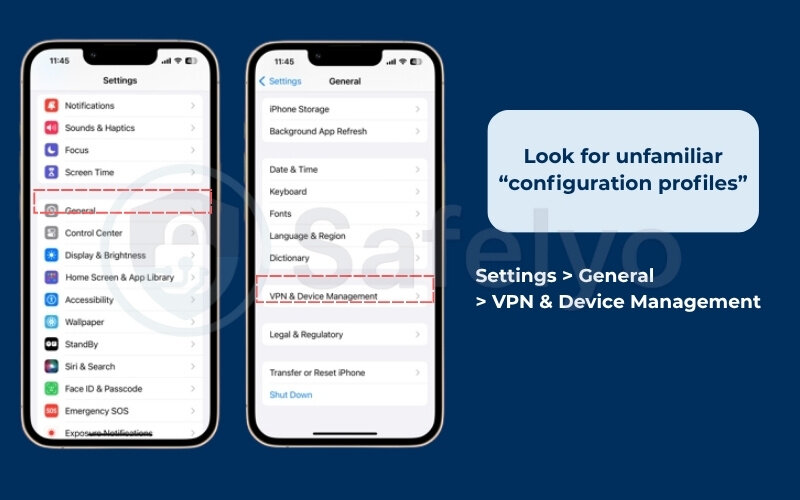
- Look for unfamiliar configuration profiles:
This is the most likely culprit on a non-jailbroken iPhone. Go to Settings > General > VPN & Device Management. If you see a “Configuration Profile” listed here that you don’t recognize, it could be spyware. These are often used by employers or schools to manage devices, but they can be abused by commercial spyware to monitor you.
- Check for signs of jailbreaking:
A jailbroken iPhone has its core security restrictions removed, making it highly vulnerable. The user would likely know if they did this, but someone else could have done it without their knowledge. Look for apps like “Cydia” or “Sileo” on the home screen. If you see them, your phone is jailbroken and should be considered compromised.
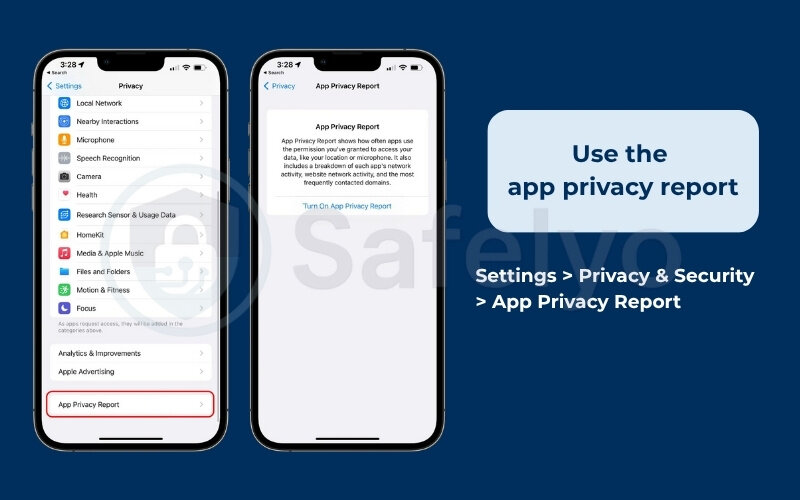
- Use the app privacy report:
This is your iPhone’s built-in detective. Go to Settings > Privacy & Security > App Privacy Report. This feature shows you exactly which apps have accessed your location, microphone, camera, and other data, and how often. If you see the Facebook app accessing your microphone when you haven’t used it for a day, or a simple game accessing your contacts, you’ve found a problem.
4. I found something suspicious. What now?
Okay, take a breath. Finding something suspicious is jarring, but it’s also a victory. You’ve successfully moved from uncertainty to evidence. Now you have a target.
From my experience, the next hour is critical. You need to follow a precise plan to remove the threat and lock down your digital life. Do not deviate from these steps. This is your action plan to take back control.
YOUR EMERGENCY ACTION PLAN
- Follow these steps in order. For detailed instructions on how to perform each step, read the full explanations below.
- Document: Screenshot the evidence before deleting anything.
- Remove: Uninstall the suspicious app or remove the malicious profile, then reboot.
- Scan: Run another full scan with your mobile security app.
- Change Passwords: Use a different, clean device to change all your important passwords.
- Reset: For total peace of mind, perform a factory reset.
4.1. Step 1: Document everything
This is the step most people skip in a panic, but it can be the most important. Before you delete anything, take screenshots. Capture images of the suspicious app in your app list, the strange configuration profile, or the high battery usage screen.
Why is this so important?
If the tracking was done by a person you know, these screenshots are your evidence. They could be vital if you decide to involve your workplace, your school, or even law enforcement. You only get one chance to capture this proof before it’s gone.
4.2. Step 2: Remove the malicious app or profile
With your evidence saved, it’s time to evict the intruder.
- For apps (Android/iPhone): Go to your settings, find the application, and uninstall it. If the ‘Uninstall’ button is greyed out (a common trick on Android), go back to the ‘Device admin apps’ screen from the previous section, revoke the app’s admin privileges, and then you will be able to uninstall it.
- For profiles (iPhone): Go to Settings > General > VPN & Device Management, tap on the malicious profile, and select “Remove Profile.”
After you remove it, reboot your phone immediately. This helps ensure that any background processes tied to the app are fully terminated.
4.3. Step 3: Run a full security scan
Think of the app you removed as the main weed. Now you need to get the roots. Immediately run another full scan using your trusted mobile security app. This will help catch any leftover files, related components, or other malware that might have been installed alongside the main spyware.
4.4. Step 4: Change your critical passwords
You must assume that every password you’ve typed on your phone has been compromised. Do not perform this step on the potentially infected phone. Use a different, trusted device like a laptop or a family member’s computer.
Change the passwords for your most important accounts immediately, starting with:
- Your primary Apple ID or Google Account
- Your main email address(s)
- All banking and financial apps
- Your primary social media accounts
4.5. The ultimate solution: A factory reset
I’m going to be direct with you: a factory reset is the only way to be 100% certain that the spyware and all its remnants are gone. It’s a big step, as it erases everything on your phone and returns it to its out-of-the-box state.
If the feeling of being watched is causing you serious distress, the peace of mind a factory reset provides is invaluable. Just be sure to back up your essential data, like photos and contacts, first. Do not back up your apps, as you might accidentally restore the malware along with them.
5. How to protect your phone from being tracked in the future
Removing spyware is like pulling a weed. Preventing it from growing back requires tending to the garden. Now that your device is clean, adopting these security habits will make it a much harder target for any kind of tracking in the future. I consider these non-negotiable practices for all my clients.
- Use a strong passcode and biometrics: A simple 4-digit PIN is easy to guess. Use a longer, alphanumeric passcode and enable Face ID or fingerprint scanning. This is your first line of defense against someone trying to get physical access.
- Enable two-factor authentication (2FA): This is arguably the single most important security measure you can take. Enable 2FA on your critical accounts, especially your Apple/Google ID. It means that even if someone steals your password, they can’t get in without a second code from one of your other devices.
- Never install apps from outside official app stores: This is the golden rule, especially for Android users. The Google Play Store and Apple App Store have security checks in place to vet apps. Installing an app from a random website or link is like opening your front door to a stranger. (This is especially critical for Android users.)
- Be careful with physical access: As we discussed, much stalkerware is installed by someone who gets their hands on your phone, even for just a minute. Don’t leave your phone unattended and unlocked around people you don’t fully trust.
- Regularly review privacy settings on iOS: Apple gives you powerful tools. Make it a monthly habit to check your App Privacy Report to see what your apps have been up to. For high-risk situations, explore using Lockdown Mode, which severely restricts your phone’s functions to prevent sophisticated spyware attacks.
- Install a reputable mobile security suite: A good antivirus app isn’t just for cleanup; it’s for prevention. It actively scans new apps you install and can warn you of suspicious links before you click them.
- Use a vpn on public wi-fi: A VPN encrypts your internet connection. This won’t stop spyware already on your phone, but it prevents “man-in-the-middle” attacks on insecure networks (like at a café or airport) where snoops could try to intercept your data.
After securing your device, choosing the right protection is vital. See our expert review of the Best Mobile Security Apps for 2025 to find the perfect shield for your phone.
6. FAQ about how to check if my phone is being tracked
Even after going through the checklist, you might still have specific questions. Here are the quick, direct answers to the most common ones we hear.
How can I detect a tracker on my phone?
You can detect a tracker by following a two-step process: 1. Look for warning signs like unusual battery drain, your phone being constantly hot, strange apps appearing, or high data usage. 2. Actively investigate by checking your app list, reviewing app permissions (especially Device Admin on Android), and running a scan with a reputable mobile security app.
What is the code to check if your phone is being monitored?
There is no single magic code to detect spyware. Codes like *#21# or *#62# only check for carrier-level call forwarding, not for monitoring apps installed on your device. Relying on these codes can give you a false sense of security. The only reliable method is to check your device as outlined in this guide.
How can I block my phone from being tracked?
You can block tracking by adopting strong security habits. The most effective methods are: using a strong passcode, enabling two-factor authentication (2FA) on your accounts, only installing apps from official stores, and being cautious about who has physical access to your phone. For network-level protection, using a VPN on public Wi-Fi is also recommended.
Can a factory reset remove all spyware?
Yes, in almost all cases. A factory reset is the most effective way to ensure a clean slate. It erases the phone’s entire operating system and all user data, including any malicious apps that were installed.
Can someone track my phone with just my number?
Generally, no. For the public, tracking a phone’s live location requires software installed on the device itself. However, your number can be used in phishing attacks to trick you into clicking a link that installs that software. While law enforcement has special methods, this is not something the average person can do.
What is stalkerware?
Stalkerware is a type of spyware sold commercially and often used by individuals to secretly monitor the phone of someone they know, like a partner or family member. It is hidden, invasive, and a serious form of digital abuse.
7. Conclusion
Learning how to check if my phone is being tracked is more than just a technical skill; it’s about taking back control of your personal space and digital security. By understanding the signs, knowing how to investigate, and having a clear action plan, you can move from a state of fear to one of empowered action. Your phone is an extension of your life, and you have every right to protect it.
To help you remember the most critical points, keep this final checklist in mind:
- Trust your instincts: If your phone’s battery, temperature, or data usage feels wrong, it probably is.
- Investigate proactively: Don’t just wonder. Actively check your app lists, device admin permissions (on Android), and privacy reports (on iPhone).
- When in doubt, reset: A factory reset is your ultimate guarantee of a clean slate and is the best tool for true peace of mind.
- Prevention is the best defense: A strong passcode, two-factor authentication, and downloading apps only from official stores are your most powerful shields.
Your digital safety is in your hands. Here at Safelyo, we are committed to providing you with clear, trustworthy guides to navigate modern threats. For more expert advice on identifying and defeating digital dangers, we invite you to explore our Hack & Scam Education Center. Stay safe.




