Ever had that heart-stopping moment when a blaring, red pop-up screams that your computer is riddled with viruses? If you have, you’re probably asking, “How can I protect myself against fake antiviruses?” You’ve come to the right place. These are not legitimate security alerts but sophisticated scams known as scareware, designed to manipulate your fear into a costly mistake.
With over a decade of experience analyzing malware and online threats, I’ve seen firsthand how these scams prey on panic to steal money and sensitive data. But here’s the good news: with a bit of knowledge, you can spot these digital con artists from a mile away.
In this comprehensive guide, you’ll discover:
- What a fake antivirus truly is and why it’s so dangerous.
- The psychological tricks scammers use to make you panic.
- The crystal-clear warning signs of a fake.
- A step-by-step action plan to stay protected and remove any threats.
It’s time to trade fear for facts. Let Safelyo guide you through every step to secure your digital life for good.
1. What is a fake antivirus, and why is it so dangerous?
Think of a fake antivirus as a digital wolf in sheep’s clothing. On the surface, it looks like a legitimate security program, complete with a professional-looking interface and urgent warnings. In the industry, we call this rogue security software or, more commonly, scareware – because that’s exactly what it’s designed to do: scare you.
But its real goal isn’t to protect your computer. It’s to:
- Trick you into paying for a useless subscription that does absolutely nothing.
- Steal your credit card details when you enter them on the fake payment page.
- Install genuinely harmful malware, like keyloggers that record your passwords or spyware that watches your every move.
Imagine a plumber knocking on your door, claiming your house has a massive, invisible leak, and demanding you pay for an expensive, immediate repair. That’s exactly how a fake antivirus operates. It invents a problem to sell you a worthless “solution.”
The danger goes far beyond losing $50. At Safelyo, we’ve analyzed countless cases where a simple fake antivirus scam led to significant financial and data loss for unsuspecting users. I’ve personally seen situations where one click on a fake alert led to thousands of dollars in fraud and months of stress trying to reclaim a stolen digital identity. The initial scam is often just the beginning.
2. How fake antivirus scams trick you
These scams are less about sophisticated code and more about sophisticated psychology. They work by hijacking your emotions, bypassing your rational brain to create a sense of overwhelming panic. In my experience, the entire attack follows a simple but brutally effective three-step playbook.
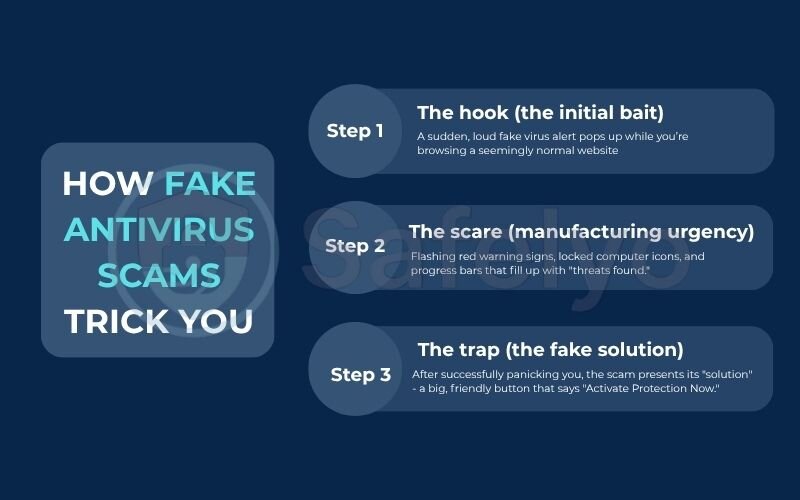
Step 1: The hook (the initial bait)
First, they need to get their fraudulent message in front of you. This usually happens in one of three ways:
- A sudden, loud fake virus alert pops up while you’re browsing a seemingly normal website.
- You receive a phishing email disguised as a warning from a known company like Microsoft or Google.
- You download a “free” program or file from an untrustworthy source, which has the scareware bundled inside.
Think of it like a digital tripwire. You’re just walking along the internet, and suddenly, you’ve stumbled into their trap.
Step 2: The scare (manufacturing urgency)
This is where the psychological manipulation kicks in. The pop-up will use every trick in the book to short-circuit your critical thinking:
- Alarming visuals: Flashing red warning signs, locked computer icons, and progress bars that fill up with “threats found.”
- Urgent language: Phrases like “IMMEDIATE ACTION REQUIRED,” “YOUR SYSTEM IS AT RISK,” and “PRIVACY BREACH DETECTED.”
- A terrifying list of infections: It will pretend to scan your system and show you a long, scrolling list of scary-sounding viruses that it “found.” I’ve seen these lists claim to find hundreds of critical threats in under 10 seconds – a clear impossibility designed purely to overwhelm you.
It’s the digital equivalent of a fire alarm going off. Your first instinct isn’t to investigate; it’s to find the nearest exit. The scammers count on this.
Step 3: The trap (the fake solution)
After successfully panicking you, the scam presents its “solution” – a big, friendly button that says “Remove All Threats” or “Activate Protection Now.” This is the final, critical part of the con. Clicking that button does one of two things:
- It takes you to a professional-looking payment page to buy their useless software.
- It directly downloads the actual malware onto your computer.
This isn’t a small-time issue. According to the FBI’s Internet Crime Complaint Center (IC3), tech support and scareware scams result in hundreds of millions of dollars in losses for victims each year. It’s a classic bait-and-switch, where the promise of security is the bait, and the switch costs you your money and your data.
3. 7 warning signs of a fake antivirus (with real examples)
Once you know what to look for, spotting a fake antivirus becomes much easier. Scammers rely on your panic to make you overlook these obvious red flags. Based on the hundreds of rogue programs I’ve analyzed, they almost always share the same clumsy characteristics. Let’s train your eyes to see them.
3.1. Constant, aggressive pop-ups and warnings
A legitimate antivirus program works quietly in the background. It will notify you of a real threat, but it won’t scream at you. Fake antiviruses, however, are relentless. They bombard you with pop-ups that are difficult or impossible to close.
- Simple Example: Think of it this way: a real security guard will discreetly inform you of a problem. A fake one will run up to you, wave a giant red flag in your face, and shout that the building is on fire when it isn’t.
3.2. Unprofessional design and grammar mistakes
Top security companies like Norton or Bitdefender spend millions on their user interface and branding. Their software is polished and professional. I’ve seen countless fakes with pixelated logos, awkward layouts, and glaring spelling or grammar mistakes (e.g., “Your computer has been infected”).
- Simple Example: You wouldn’t trust a fancy restaurant if its menu was full of typos, right? Apply the same logic to your security software. Professionalism is a key sign of legitimacy.
3.3. Vague or generic names
Scammers use generic, important-sounding names to sound official without infringing on trademarks. Be highly suspicious of names like “Antivirus Defender Pro,” “PC Security Shield,” or “WinGuard 2024.”
- Simple Example: It’s like buying a product labeled “Cola Drink” instead of “Coca-Cola.” The generic name is a huge red flag that it’s a cheap, untrustworthy knock-off.
3.4. Demands for immediate payment to fix problems
This is the biggest giveaway. Real antivirus software will let you scan your computer for free. They may ask you to upgrade to a paid version to enable premium features, but they will never find threats and then hold the “fix” hostage until you pay.
- Simple Example: This is like a mechanic who looks under your car’s hood for two seconds, claims the engine is broken, and demands your credit card before he’ll even tell you what’s wrong. It’s pure extortion.
3.5. High-pressure sales tactics
Scareware uses language designed to make you feel helpless and rushed. You’ll see countdown timers, warnings that your data is being stolen “right now,” and phrases like “Act immediately to prevent data loss!”
- Simple Example: I always tell people this is the digital version of a “limited time offer” from a pushy salesperson. They create false urgency to stop you from thinking clearly and doing your own research.
3.6. Inability to close the program or access other functions
A classic move from these rogue programs is to take over your screen. They might disable your Task Manager, block access to your real antivirus, or make it impossible to close their warning window.
- Simple Example: A legitimate program is a guest in your digital home. A fake one locks the doors and won’t let you leave the room. If you feel like you’ve lost control of your computer, it’s a major sign of malware.
3.7. Scans run suspiciously fast
A full system scan by a legitimate antivirus can take anywhere from 30 minutes to over an hour, as it meticulously checks millions of files. I’ve watched fake antiviruses “scan” an entire hard drive in less than 15 seconds and claim to find hundreds of infections. This is technically impossible.
- Simple Example: It’s like a home inspector who claims to have checked every pipe, wire, and foundation beam in your entire house in just one minute. It’s a performance, not a real inspection.
Here is a simple table to help you remember the key differences:
| Feature | Legitimate Antivirus | Fake Antivirus (Scareware) |
| Source | Official company website (e.g., Norton.com) | Random pop-ups, spam emails, bundled downloads |
| Alerts | Calm, professional notifications | Loud, aggressive, constant warnings |
| Design | Polished, professional, no errors | Clumsy design, spelling/grammar mistakes |
| Payment | Offers a free scan; payment is for premium features | Demands immediate payment to “fix” problems |
| Control | You are always in control of the program | Tries to take over your screen, hard to close |
4. How can I protect myself against fake antiviruses
The best defense is a good offense. Instead of waiting for a scam to appear, you can build a strong digital fortress that keeps these threats out entirely. In my years of helping people secure their devices, I’ve found that a few simple, proactive habits are far more effective than any panicked cleanup effort.

Think of it like this: it’s much easier to lock your front door than to deal with a burglar who is already inside your house. Here’s your checklist to lock that door.
4.1. Install a trusted, legitimate antivirus software
This is your number one, non-negotiable line of defense. A top-tier antivirus from a reputable brand like Norton, Bitdefender, or McAfee does more than just scan for viruses. Its most powerful features for this problem are:
- Real-time protection: It scans files as you download them, stopping a fake antivirus installer before it can even run.
- Web protection: It actively blocks you from landing on malicious websites known for hosting these scammy pop-ups in the first place.
I can’t stress this enough: a quality antivirus is like having a vigilant, 24/7 security guard for your digital life. It’s the single best investment for your peace of mind.
4.2. Keep your operating system and browser updated
Scammers often exploit known security holes in outdated software to force their pop-ups onto your screen. When you see an update notification from Windows, macOS, Chrome, or Firefox, don’t ignore it.
- Simple Example: An outdated browser is like a house with a broken window lock. It’s an open invitation for trouble. Software updates are free, easy security upgrades.
4.3. Use a pop-up blocker and be skeptical of ads
Most modern browsers have a built-in pop-up blocker – make sure it’s turned on. While it won’t catch everything, it’s a great first filter. More importantly, adopt a healthy sense of skepticism toward online ads. If an ad promises something that seems too good to be true (like a free PC speed boost or a prize win), it’s almost always a trap.
PERSONAL TIP
I have a simple rule: I never click inside a pop-up window. Ever. If I can’t close it with the ‘X’, I close the entire browser tab. If that doesn’t work, I use the Task Manager (Ctrl+Shift+Esc on Windows) or Force Quit (Cmd+Opt+Esc on Mac) to shut the browser down.
4.4. Only download software from official sources
This is a critical habit. If you want to install a program, go directly to the developer’s official website or a trusted app store (like the Microsoft Store or Apple App Store). Never, ever download software from a link in an email, a random pop-up ad, or a third-party download site you don’t recognize.
- Simple Example: You wouldn’t buy a prescription medicine from a guy in a back alley; you’d go to a licensed pharmacy. Treat your software the same way. The source is everything.
4.5. Trust your instincts
Finally, listen to that little voice in your head. If a security warning feels overly dramatic, aggressive, or just plain wrong, it probably is. Legitimate companies don’t use fear to motivate you. Pause, take a deep breath, and close the window.
- Simple Example: As I always say, panic is the scammer’s best friend. A moment of calm is your greatest weapon.
Read more:
5. Help! I think I installed a fake antivirus. What now?
Okay, take a deep breath. If you think you’ve accidentally installed one of these malicious programs, the most important thing is not to panic. Following a clear set of steps can contain the damage and get your device back to normal. I’ve walked countless people through this exact process; it works.

Think of this as a digital emergency procedure. Here’s exactly what you need to do, in order.
Step 1: Disconnect from the internet
This is your absolute first move. Unplug the Ethernet cable or turn off your Wi-Fi immediately.
Imagine you’ve caught a burglar in your house who is on the phone with his accomplices. The first thing you do is cut the phone line. Disconnecting from the internet stops the malware from sending your personal data (like passwords or credit card info) out to the scammers or downloading more malicious files.
Step 2: Reboot your computer into Safe Mode
Safe Mode is a diagnostic version of your operating system that only loads the most essential programs. Since the fake antivirus isn’t essential, it usually won’t start up in this mode, making it much easier to remove.
Think of Safe Mode as starting your computer in a “ghost town” state. It’s quiet and empty, which makes it incredibly easy to spot the one troublemaker who doesn’t belong there.
- How to do it: On Windows, you can typically access this by holding the Shift key while clicking “Restart.” On a Mac, you hold the Shift key as it boots up.
Step 3: Locate and uninstall the malicious program
Once in Safe Mode, navigate to your list of installed programs.
- On Windows: Go to Control Panel > Programs > Uninstall a program.
- On macOS: Open your “Applications” folder.
Look for the fake antivirus program or any other software you don’t recognize that was installed around the same time. Select it and click “Uninstall” or drag it to the Trash.
Step 4: Run a full scan with a legitimate antivirus/anti-malware tool
Uninstalling the program is a great first step, but it often leaves hidden files behind. Now that you’ve kicked the main intruder out, it’s time to bring in the real security team.
This is like having a forensic team sweep your house after the burglar has been removed to ensure they didn’t leave any listening devices or hidden traps behind.
RECOMMENDATION
Install a trusted tool like Malwarebytes (which has a great free version for scanning and removal) or the scanner from a premium service like Norton 360. Let it run a full, deep system scan to find and quarantine any remnants.
Step 5: Change your passwords
As a final precaution, you must assume that your passwords may have been compromised. Once your computer is clean, log into a different device (like your phone) and change the passwords for your most critical accounts – especially your email, online banking, and social media.
PERSONAL ADVICE
This step is crucial. I’ve seen cases where the initial scareware was just a distraction to install a keylogger. Assume the scammers copied your house keys and changed all the important locks.
6. Real-life examples: Famous fake antivirus scams that fooled millions
You might think these scams are a recent problem, but the truth is, they’re just old tricks with a new coat of paint. Looking at some of the most infamous scams from the past shows us that the playbook rarely changes. I’ve personally helped clean up the aftermath of these, and the patterns are always strikingly similar.
6.1. Case Study 1: MacDefender (and its variants)
Back in 2011, there was a widespread belief that “Macs don’t get viruses.” Scammers exploited this by creating MacDefender.
- The Trick: It used pop-ups on websites that automatically started downloading a fake installer. Once run, it would perform a classic “fast scan” and display terrifying (but fake) results, claiming the Mac was infected with pornography-related malware to increase the user’s embarrassment and urgency to pay.
- The Lesson: This case proved that no platform is immune. It relied on the psychology of fear and used nearly all the warning signs we discussed: aggressive pop-ups, a fake scan, and a demand for immediate payment. I remember the shock in the Mac community as people realized they needed to be just as vigilant as Windows users.
6.2. Case Study 2: Security Tool / XP Antivirus
These were some of the most notorious pieces of scareware in the Windows XP and Windows 7 eras. They were incredibly aggressive.
- The Trick: This program was a master of the hostile takeover. Its signature move was disabling your Task Manager and blocking your real antivirus from running, making you feel completely trapped. It would then plaster your screen with alerts and even hide your desktop icons to make you think your computer was completely broken.
- The Lesson: This demonstrates warning sign #3.6 (Inability to close the program) in its most extreme form. By creating a feeling of total helplessness, it pushed users to click “buy” as the only perceived way out. It’s a powerful reminder that if a program takes control away from you, it is not your friend.
These examples might seem old, but their tactics are recycled every single day in new scams. The names change, the logos are updated, but the core strategy of fear and deception remains exactly the same.
7. FAQ about fake antiviruses
We’ve covered a lot of ground, but you might still have some specific questions buzzing in your head. I’ve compiled the most common queries we receive at Safelyo to give you quick, straightforward answers.
Is a fake antivirus a virus itself?
Not exactly. It’s a type of malware called “scareware.” Its main goal is to trick you into paying or giving up your information. However, it very often installs real viruses, spyware, or keyloggers once you download it.
Can a fake antivirus steal my information?
Absolutely. That’s one of its primary goals. It’s designed to capture your credit card details during the fake “purchase” and may install malicious software to steal your passwords and other sensitive data long after the initial scam.
How to protect against fake antiviruses?
The best protection is proactive. The key actions are: installing a trusted, legitimate antivirus software, keeping your operating system and browser updated, only downloading software from official websites, and being highly skeptical of any urgent, unexpected pop-up warnings.
How to stop fake antivirus pop-ups?
Never click anything inside the pop-up window, not even the ‘X’ button. Instead, close the entire browser tab. If you can’t, use your computer’s Task Manager (Ctrl+Shift+Esc on Windows) or Force Quit feature (Cmd+Opt+Esc on Mac) to shut down the browser completely.
How can I tell if an antivirus free trial is legit?
Legitimate companies like Norton or Bitdefender offer free trials directly on their official websites. They will not pressure you with aggressive pop-ups. A real free trial won’t claim to find hundreds of viruses on a clean computer or demand payment to fix issues it finds.
Is there a genuinely free antivirus?
Yes, many reputable companies offer free versions (like Avast or AVG). They provide a good baseline of protection against common viruses. However, they usually lack the advanced web protection and real-time security features that are most effective at blocking fake antivirus scams at the source.
Is Windows Defender enough to protect me from these scams?
Windows Defender (now Microsoft Defender) is a solid, built-in antivirus. However, its web protection and ability to block sophisticated pop-up scams are generally not as robust as the multi-layered security offered by leading paid solutions.
How to make sure antivirus is off?
You should almost never turn your antivirus off, as it leaves your computer completely exposed. If you absolutely must disable it for a specific reason (like installing a trusted program it wrongly flags), you should do so temporarily through the antivirus program’s own settings menu, not through system tools.
8. Conclusion
You now have the knowledge and tools to answer the critical question, “How can I protect myself against fake antiviruses?” By understanding the psychology of fear that scammers use and learning to spot their tell-tale signs, you’ve already shifted the power back into your hands. You no longer need to be a victim of these digital con artists.
To keep yourself safe, always remember these key points:
- Be skeptical of urgency: Legitimate security warnings are calm and informative, not loud and panicked. High-pressure tactics are a huge red flag.
- Trust the source: Only download software from the developer’s official website. A random pop-up is never a trustworthy source.
- A real antivirus is your best shield: Proactive protection from a legitimate security suite is the single most effective way to block these scams before you even see them.
In the digital world, a healthy dose of skepticism is your best friend. Never let panic guide your decisions online. To ensure your devices are shielded by real, powerful protection, explore Safelyo expert guides and reviews in our Antivirus category and choose the right security tool for your needs.







