What is a rootkit? Imagine a digital master of disguise, an invisible intruder designed to seize total control of your system while remaining completely hidden from you and your security software.
Unlike a noisy virus that often announces its presence with obvious symptoms, a rootkit’s primary danger is its absolute stealth. It’s built to dig deep into the core of your operating system, making detection and removal an immense challenge. This isn’t just another piece of malware; it’s one of the most sophisticated and persistent threats you can face.
With years of hands-on experience in malware analysis, I’ve seen how these stealthy tools act as a ‘skeleton key’ for cybercriminals, holding the door open for other threats like ransomware and spyware to operate undetected. Understanding rootkits isn’t just for cybersecurity experts; it’s crucial knowledge for anyone who wants to be truly secure online.
In this comprehensive guide, you’ll discover:
- What a rootkit is and why it’s so different from a virus.
- How it infects your system and the damage it can do.
- The main types of rootkits and where they hide.
- How to detect the signs of an infection and protect yourself.
Don’t let the most dangerous threats be the ones you can’t see. Let me illuminate these hidden dangers and empower you to take back control of your digital security, starting right now.
1. What is a rootkit, and why is it different?
Let’s break down the name itself, because it tells you almost everything you need to know. The “root” part comes from the world of Unix and Linux systems, where the “root” user is the super-administrator with the highest possible level of access. Think of it as having the master key to every single room in an entire building. The “kit” part simply means it’s a set of software tools.
So, what is a rootkit? It’s a toolkit designed specifically to gain and maintain that all-powerful “root” access, all while hiding its own existence.
And to be crystal clear, yes, a rootkit is absolutely a type of malware. In fact, it’s one of the most advanced and dangerous kinds because its entire purpose is to be invisible.
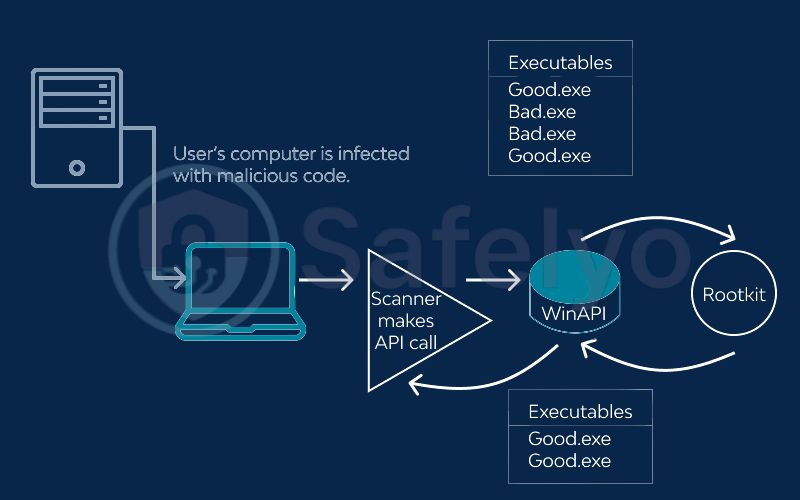
In my years of analyzing cyber threats, the biggest misconception I see is people lumping rootkits in with viruses. A virus wants to spread, like a biological cold. A rootkit has a completely different job. It’s not the disease itself; it’s the spy who silently picks the lock, disables the security cameras, and then holds the door open for other, more disruptive malware (like ransomware or keyloggers) to sneak in and operate without ever being caught.
To make the distinction clearer, here’s a simple breakdown:
Rootkit vs. virus vs. trojan: Key differences
| Characteristic | Rootkit | Virus | Trojan |
|---|---|---|---|
| Main Purpose | Hide its presence and other malware to maintain secret access. | Replicate and spread itself to other programs and systems. | Deceive the user into running it to deliver a malicious payload. |
| Stealth Level | Extreme. Designed to modify the operating system to become invisible. | Low to Medium. Often causes noticeable symptoms to aid its spread. | High (Initially). It hides by pretending to be a legitimate program. |
| Mechanism | Alters core system functions and APIs from deep within the OS. | Attaches its code to legitimate files and executables. | Masquerades as a useful application or file. |
| Removal Difficulty | Very Hard. Often requires a complete system wipe and reinstallation. | Medium. Most modern antivirus software can detect and remove common viruses. | Medium. Can be removed once identified, but might have already installed other malware. |
2. How does a rootkit infect a system, and what does it do?
A rootkit doesn’t usually kick down the front door. Instead, it sneaks in through a side entrance you might have accidentally left open. In my experience, most infections aren’t the result of a brute-force attack but rather a moment of human error or a simple oversight.
Here are the most common ways a rootkit gains entry:
- Phishing and malicious attachments.
This is the classic trick. You receive an email that looks legitimate – maybe a shipping notification or an urgent invoice – and click on a link or open a file. That single click is all it takes to run the installer.
- Bundled with other software.
That “free” video converter or game you downloaded from a sketchy website might come with an unwanted passenger. The rootkit is bundled into the installation package and gets installed silently in the background.
- Exploiting security vulnerabilities.
Think of this as a digitally unlocked window. If your operating system, web browser, or an application like Adobe Reader isn’t up to date, it might have a known weakness that attackers can exploit to inject the rootkit directly.
- Physical access.
This is less common for the average person, but highly effective. If an attacker can get their hands on your computer for even a few minutes, they can install a rootkit directly from a USB drive.
Once inside, a rootkit’s mission isn’t to cause chaos; it’s to establish complete, hidden control. Its first job is always to erase its own footprints. Then, it gets to work on its main goals:
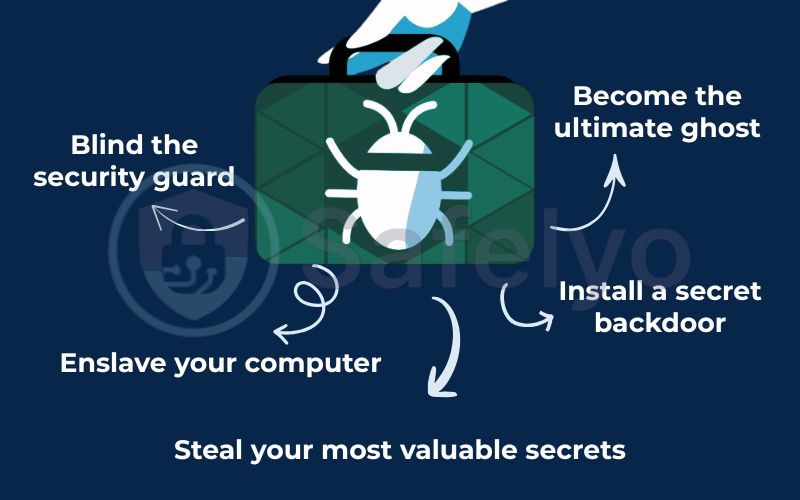
- Become the ultimate ghost. It modifies core parts of your operating system to hide its own files, processes, and network connections – and those of any other malware it brought along.
- Install a secret backdoor. This allows the attacker to access your system remotely whenever they want, completely bypassing your firewall and security.
- Blind the security guard. From its privileged position, a rootkit can disable or tamper with your antivirus software, telling it that everything is perfectly fine.
- Steal your most valuable secrets. With full system access, it can deploy keyloggers to capture passwords, bank details, and personal conversations.
- Enslave your computer. Your machine can be forced into a “botnet” – a network of infected computers – to send spam, mine cryptocurrency, or launch attacks on other websites, all without your knowledge.
The entire attack chain is often deceptively simple: User clicks a phishing link -> Rootkit installs silently -> Rootkit hides itself -> Attacker now has a secret key to the system.
A BRIEF HISTORY
How rootkits evolved from corporate tools to cyber weapons
The idea of a rootkit isn’t new, but its purpose has changed dramatically. What started as a niche tool for system administrators evolved into a notorious weapon used by corporations and even governments. Two specific events really brought rootkits into the global spotlight.
First, there was the Sony BMG scandal in 2005. To prevent music piracy, Sony secretly included rootkit software on millions of its audio CDs. When you played the CD on your computer, this rootkit installed itself without permission. Its purpose was to control how many times you could copy the music. The real problem? It created massive security holes that other malware quickly began to exploit. This was the first time the public became widely aware of how a trusted company could use such a devious tool against its own customers.

Then, in 2010, the game changed entirely with Stuxnet. This was no ordinary malware; it was a highly sophisticated, state-sponsored cyber weapon. Stuxnet contained a powerful rootkit that allowed it to infect and hide within the industrial control systems of Iranian nuclear facilities. Its goal was to subtly manipulate machinery, causing centrifuges to spin out of control and self-destruct. Stuxnet proved that rootkits weren’t just for stealing data – they could be used to cause real-world, physical destruction.
3. Visualizing the battlefield: Where rootkits hide in your system
To truly understand why rootkits are so formidable, you need to stop thinking of your computer as a single object. Instead, picture it as a building with several floors, each with a different level of security and authority. The “higher” floors are the applications you see and interact with every day, while the “deeper” floors are the foundations that make everything else run.
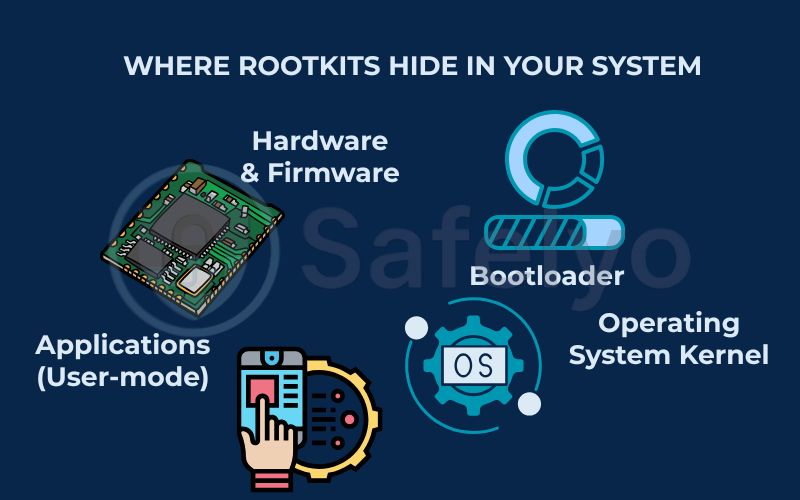
Here’s a simple way to visualize these layers, from top to bottom:
- Applications (User-mode): This is the top floor where all your programs live – your web browser, your games, Microsoft Word.
- Operating System Kernel: This is the secure control room in the basement. The kernel is the core of the OS (like Windows or macOS), managing everything from your memory to your CPU. It’s the ultimate authority that dictates what all the applications on the top floor are allowed to do.
- Bootloader: This is the building’s ignition switch. It’s the very first piece of software that runs when you press the power button, responsible for “waking up” the operating system kernel.
- Hardware & Firmware: This is the building’s concrete foundation and electrical wiring. It’s the physical hardware and the permanent software etched onto those chips (like the BIOS/UEFI on your motherboard).
The fundamental rule of a rootkit attack is this: the deeper it hides in these layers, the more powerful and undetectable it becomes. A rootkit operating at the kernel level can lie to any security program running on the application level. A rootkit hiding in the firmware is even more terrifying, as it controls the system before your OS or antivirus even has a chance to load.
Now, let’s explore the main types of rootkits, categorized by which “floor” of the system they choose to invade.
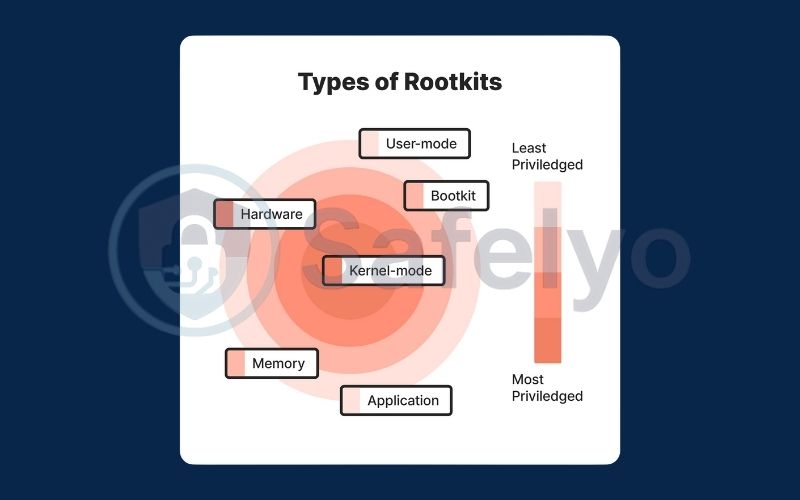
4. The main types of rootkits explained
Rootkits are not a one-size-fits-all threat. They are specialists, each designed to infiltrate a specific layer of your system. Understanding the different types is key to grasping the scale of the risk they pose.
Rootkit types at a glance
| Rootkit Type | Hiding Spot (System Layer) | Simple Analogy (How it Works) | Danger Level | Removal Difficulty |
|---|---|---|---|---|
| User-mode | Applications | “The liar in the crowd.” It tricks your programs into hiding malicious files. | Low | Medium |
| Kernel-mode | Operating System Core (Kernel) | “The corrupt police chief.” It rewrites the system’s own rules to become invisible. | High | Hard (Wipe & Reinstall) |
| Bootkit | Bootloader (MBR/UEFI) | “The ignition key thief.” It runs before your OS, giving it total control from the start. | Very High | Very Hard |
| Firmware | Hardware Chip (BIOS/UEFI) | “The altered DNA.” It infects the physical hardware, surviving OS reinstalls. | Extreme | Near Impossible (Replace Hardware) |
| Memory | System RAM | “The ghost in the machine.” It lives only in active memory and vanishes on reboot. | Medium | Easy (Reboot System) |
4.1. User-mode rootkits
Danger Level & Detection: Relatively low.
Think of user-mode rootkits as the most common and “friendliest” of the bunch – if you can call any rootkit friendly. They operate on the same level as your everyday applications, like your web browser or Notepad. They don’t try to break into the system’s core (the kernel); instead, they cheat.
How they work: A user-mode rootkit works by intercepting the communication between your applications and the operating system. For example, when you open Task Manager to see what processes are running, Task Manager has to ask the OS kernel for that list.
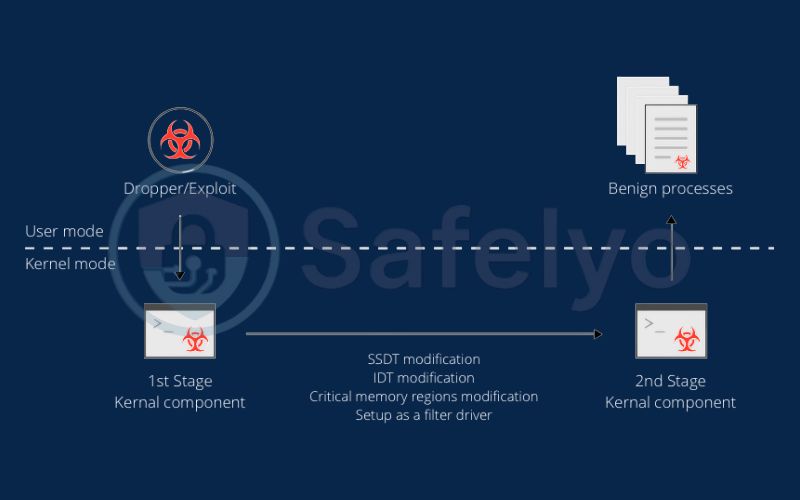
A user-mode rootkit sits in the middle and alters the answer. It’s like asking a security guard, “Is anyone suspicious in the building?” and a spy standing next to him whispers, “Tell them no,” before the guard can answer. The rootkit essentially forces your own tools to lie to you, hiding its malicious files and processes from view.
I’ve found that because these rootkits don’t have deep system privileges, they are the easiest to deal with. Most modern antivirus programs are quite good at spotting the signatures of well-known user-mode rootkits or detecting the hooks they place on system functions. A thorough scan will often catch them.
4.2. Kernel-mode rootkits
Danger Level & Detection: Extremely high.
This is where things get serious. If a user-mode rootkit is a pickpocket in a crowd, a kernel-mode rootkit is a corrupt chief of police. It doesn’t operate at the application level; it burrows deep into the very core of the operating system – the kernel.
How they work: The kernel is the ultimate authority. It handles every critical task and has complete access to all your system’s hardware. By infecting the kernel, this type of rootkit doesn’t just break the rules; it fundamentally rewrites the entire rulebook of your computer. When your antivirus software asks the kernel, “Show me all running processes,” the compromised kernel simply replies, “There are no malicious processes here,” and your antivirus software believes it. It has been completely blinded by the one part of the system it is built to trust.
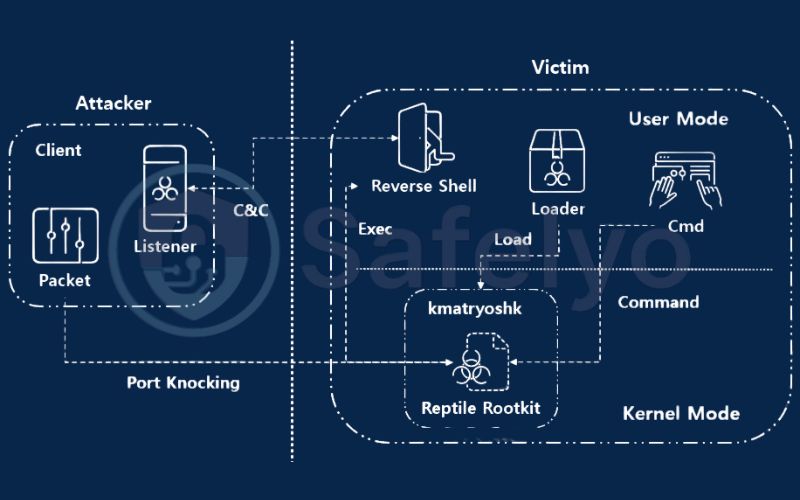
This is the type of threat that keeps cybersecurity professionals up at night. Because they compromise the system at its core, they can effectively neutralize most security software. Detecting them requires specialized rootkit scanners that can analyze the system from an outside perspective or look for subtle behavioral anomalies that indicate the kernel is lying.
4.3. Bootkits (bootloader rootkits)
Danger Level & Detection: Extremely high.
A bootkit takes the attack to an even deeper level. It targets the very beginning of your computer’s startup sequence, infecting the Master Boot Record (MBR) or Volume Boot Record (VBR).
How they work: Think of a bootkit like a thief who replaces your car’s ignition system with their own. Before your car’s main engine (the operating system) even starts, the thief’s system is already running and in full control. A bootkit loads before Windows or macOS even begins to wake up. This gives it absolute power to control the loading of the entire operating system and to subvert any security measures from the very first moment.
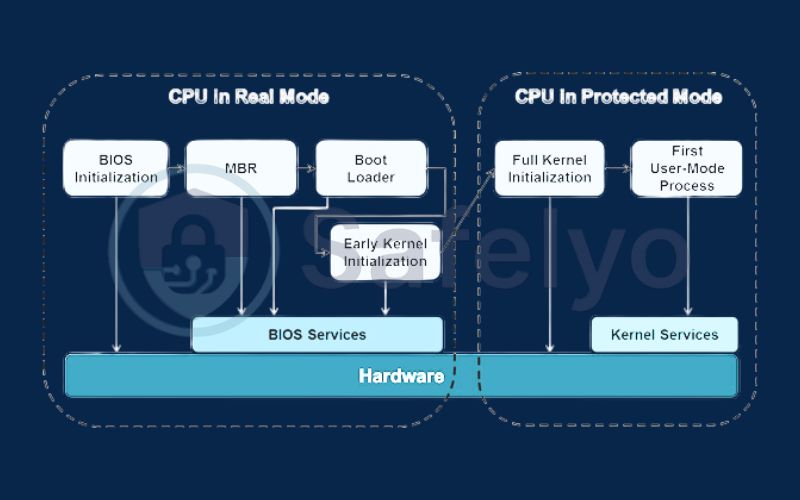
From personal experience, these are some of the most frustrating infections to deal with. I’ve had to explain to users that simply formatting their C: drive and reinstalling Windows won’t work, because the bootkit lives outside of the main partition in a place that reinstallation doesn’t touch. Removal is incredibly complex and often requires specialized tools to rewrite the MBR.
4.4. Firmware and hardware rootkits
Danger Level & Detection: The highest possible.
Welcome to the nightmare scenario. A firmware rootkit is the apex predator of the malware world. It doesn’t infect your software; it infects the physical components of your computer. It hides within the firmware – the permanent software etched onto chips – of your motherboard’s BIOS/UEFI, your network card, or even your hard drive itself.
How they work: Infecting the firmware is like altering a living thing’s DNA. No matter how many times you change its clothes (reinstall the operating system) or even perform major surgery (replace the hard drive), the fundamental code that makes it work is still compromised. A firmware rootkit can survive a complete system wipe. It’s the ultimate persistent threat. One real-world example, a UEFI rootkit named “CosmicStrand,” demonstrated this terrifying capability, staying hidden on motherboards for years.
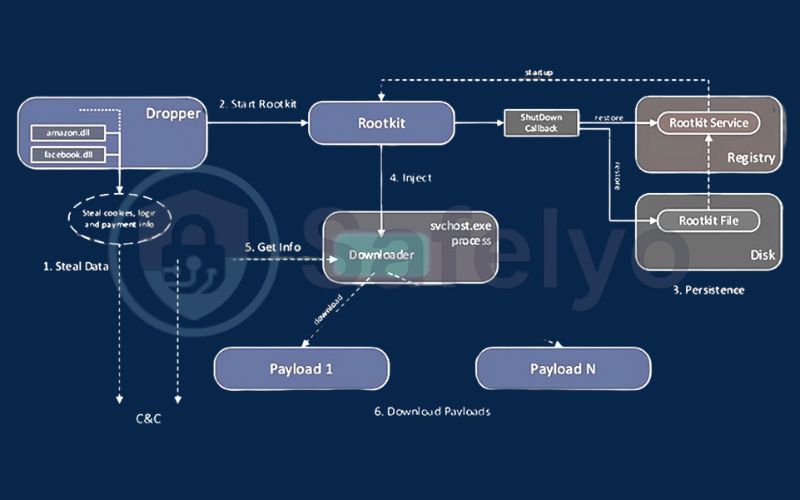
These are extremely rare for the average user but are the holy grail for state-sponsored attackers. They are nearly impossible to detect with software-based scanners, as they control the hardware beneath the operating system. Often, the only way to remove them is to physically replace the infected hardware component.
4.5. Memory rootkits
Danger Level & Detection: Medium danger, but very hard to analyze.
This type of rootkit is a ghost. It lives exclusively in your computer’s RAM (Random Access Memory) and avoids writing any of its malicious code to the hard drive.
How they work: Imagine writing a secret plan on a whiteboard. As long as you don’t erase it, the plan is active and can be acted upon. But the moment you wipe the board clean, all evidence of the plan vanishes. A memory rootkit works the same way. It operates while the computer is on, but as soon as you reboot or shut down your PC, it disappears completely.
This makes its impact non-persistent, but it also makes forensic analysis a nightmare. I’ve seen cases where system administrators, in an attempt to fix a problem, reboot a machine and, in doing so, accidentally destroy the only evidence of the intrusion.
While their effects don’t survive a restart, they are incredibly difficult to detect because they leave no traces on the disk for traditional antivirus scanners to find.
4.6. The modern frontier: Rootkits in IoT and the cloud
The battlefield is evolving. As our PCs have become more secure, attackers have shifted their focus to new, less-protected targets.
IoT Devices: Your smart TV, security camera, router, and even your smart toaster are all computers. At Safelyo, we’re seeing a clear trend of attackers targeting these devices because their security is often an afterthought. They are rarely updated and run on simplified operating systems, making them the perfect unguarded side-doors for rootkits to slip into your home network.
The Cloud: In the world of cloud computing, attackers have developed “hypervisor rootkits.” A hypervisor is the software that runs and manages multiple virtual machines (VMs) on a single physical server. Compromising it is like giving a malicious landlord a master key to every apartment in a building.
They can stealthily access, monitor, and manipulate any VM running on that server without the “tenants” ever knowing. This shows that even in the most modern environments, the core principles of the rootkit – gaining deep, hidden control – remain a critical threat.
Read more:
5. How to detect and remove a rootkit
Let’s be upfront: detecting a rootkit is notoriously difficult. Their entire purpose is to be invisible. You’re not looking for an obvious pop-up window; you’re looking for subtle, strange clues that something is fundamentally wrong with your system’s behavior.
5.1. Signs of a possible infection
While a rootkit is hiding, it can still cause ripples you might be able to spot. If you notice any of these, it doesn’t automatically mean you have a rootkit, but it’s a reason to investigate further:
- Your computer suddenly runs very slowly. If your system becomes sluggish without any obvious reason, it could be a sign of hidden processes consuming your resources.
- You experience frequent crashes or the “blue screen of death” (BSOD). A rootkit tampering with the kernel can cause system instability, leading to unexpected shutdowns.
- Windows or macOS settings change on their own. Have you noticed your screensaver changing, your taskbar hiding itself, or other settings being modified without your permission? This is a classic red flag.
- Your web browser acts possessed. If you are constantly redirected to strange websites, or if new bookmarks and toolbars appear out of nowhere, something is likely interfering with your browser at a deep level.

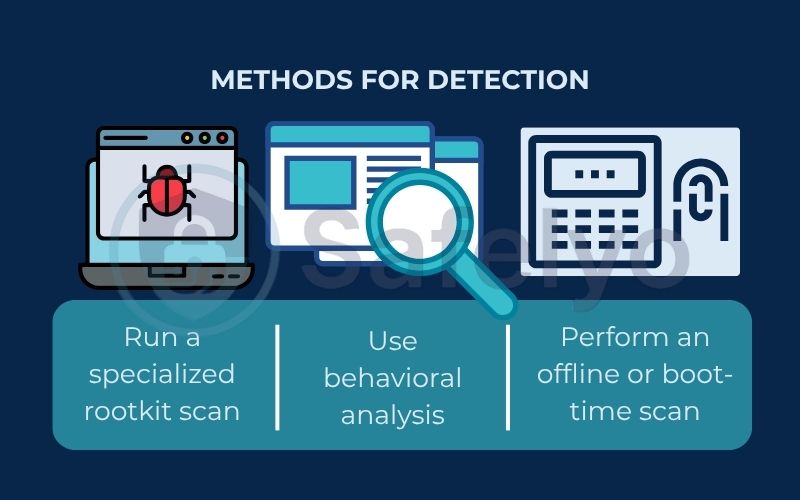
5.2. Methods for detection
If you suspect an infection, here are the methods you can use to try and uncover it:
- Run a specialized rootkit scan. Many top-tier antivirus suites include a dedicated “rootkit scanner.” These tools go beyond normal scans, specifically looking for the signs of system “hooking” and other tricks rootkits use to hide.
- Use behavioral analysis. This is a more advanced approach. Instead of looking for a known malicious file, this method watches for suspicious actions. It’s less about finding a smoking gun and more about noticing that the system is acting strangely – like a program trying to modify core system files when it has no reason to.
- Perform an offline or boot-time scan. This is one of the most effective methods. It involves using a “rescue disk” (often on a USB drive) to start your computer in a separate, clean environment. From there, you can scan your main system’s hard drive as an outsider. The rootkit isn’t active, so it has nowhere to hide.
5.3. The hard truth about rootkit removal
Here is where I have to give you the advice that many people don’t want to hear, but it’s the only responsible answer.
From years of dealing with these threats at Safelyo, we have to be honest: the only way to be 100% certain you’ve removed a deep-level rootkit (like a kernel-mode or bootkit) is to back up your essential data, completely format the storage drive, and reinstall the operating system from a trusted, clean source.
Why such a drastic step? Because a kernel-mode rootkit controls the very ground the antivirus software stands on. Asking a standard antivirus program to remove an active kernel rootkit is like asking a prisoner to arrest his own jailer – it’s a rigged game that the antivirus is destined to lose. While bootable rescue disks can sometimes be successful, there is no absolute guarantee that every single trace of the infection has been purged. Wiping the slate clean is the only way to be sure you’ve evicted the intruder for good.
6. How to protect yourself from rootkits
When it comes to rootkits, an ounce of prevention is worth a ton of cure. Given how difficult and destructive a deep-level infection can be, your best strategy is to build a strong digital fortress to keep them out in the first place.
Over the years, I’ve investigated countless rootkit infections, and the story often begins with a single, avoidable mistake. The goal is to minimize those opportunities for attackers. Here are the most effective steps you can take:
- Use a comprehensive security solution.
Don’t just settle for a basic, free antivirus. Invest in a reputable security suite that explicitly includes strong anti-rootkit and behavioral detection features. These tools are designed to spot not just known threats but also the suspicious actions that give away a hidden intruder.
- Update everything, always.
This is the single most important habit you can adopt. When Microsoft, Apple, or Google release a security patch, they are essentially fixing a known unlocked window. By applying these updates for your operating system, web browser, and other applications immediately, you are locking those windows before an attacker can climb through.
- Be paranoid about phishing.
Treat every unsolicited email with a healthy dose of suspicion. Never click on links or download attachments from unknown senders. I always tell people to follow this simple rule: if you weren’t expecting it, don’t open it. Go directly to the official website instead.
- Download software from official sources only.
The allure of a “cracked” or free version of expensive software is a classic trap. From my experience, these are some of the most common carriers of rootkits and other malware. There is no such thing as a free lunch in the world of software; you often pay with your security.
- Enable Secure Boot in your BIOS/UEFI.
Most modern computers have a feature called Secure Boot. When enabled, it checks that your bootloader is signed and trusted before allowing it to run. This is your single best defense against bootkits, as it prevents a malicious “ignition system” from ever taking over.
Safelyo’s Pro-Tip: Implement the 3-2-1 backup strategy now
Let me be blunt: your data is your responsibility. The best “insurance policy” you can have against a devastating rootkit attack is a rock-solid backup. The gold standard is the 3-2-1 rule:
- 3 copies of your data.
- On 2 different types of media (e.g., an external hard drive and cloud storage).
- With 1 copy stored off-site (in the cloud or at a different physical location).
When a rootkit strikes, a clean backup isn’t just a convenience; it’s your lifeline. It’s what allows you to confidently wipe your system clean, knowing you can restore your precious files without paying a ransom or losing everything.
See also:
7. FAQ about the rootkit
We’ve covered a lot of ground, but you might still have some specific questions. Here are clear, direct answers to some of the most common queries we get about rootkits at Safelyo.
Is a rootkit a virus?
No, they are different. A virus is designed to replicate and spread itself to other files and systems. A rootkit is designed for stealth; its main job is to hide itself and other malware to maintain long-term, hidden access to a computer. Think of a virus as a common cold that wants to infect everyone, and a rootkit as an invisible spy who wants to remain in one place undetected.
Can rootkits be removed?
Yes, but it’s very difficult. User-mode rootkits can often be removed by good antivirus software. However, for deeper infections like kernel-mode rootkits or bootkits, the only 100% guaranteed method is to back up your important files, completely format the hard drive, and reinstall the operating system from scratch.
What is an example of a rootkit?
One of the most famous examples is the Sony BMG rootkit scandal from 2005, where audio CDs secretly installed rootkits on PCs to prevent copying. A more modern and destructive example is Stuxnet, a cyber weapon that used a rootkit to physically damage industrial equipment in nuclear facilities.
How do you know if you have a rootkit?
It’s hard to know for sure because they are designed to be hidden. However, key warning signs include your computer running extremely slowly for no reason, frequent system crashes (the “blue screen of death”), browser redirects, and system settings that change without your permission.
What is the difference between a virus and a rootkit?
The key difference is their primary purpose. A virus’s goal is to spread, attaching itself to programs and moving from computer to computer. A rootkit’s goal is to hide. It doesn’t try to spread; it digs into the deepest levels of your system to provide a secret, persistent backdoor for an attacker.
Can a factory reset remove a rootkit?
A factory reset or a full OS reinstallation will remove most common rootkits, especially user-mode and kernel-mode types. However, it may not remove extremely advanced firmware or hardware rootkits that have infected the physical chips of your computer, though these are very rare for average users.
Can a rootkit infect a Mac or a phone?
Yes. While they are most famous on Windows, rootkits can theoretically exist on any operating system, including macOS, Linux, Android, and iOS. The core principle of attacking the system at a fundamental level remains the same, regardless of the platform.
8. Conclusion
Understanding what is a rootkit is the first and most critical step in defending yourself against one of the most insidious threats in the digital world. They aren’t just malware; they are the keys to the kingdom for cybercriminals, operating in the shadows to maintain control and conceal other malicious activities.
Here are the key points to remember:
- A rootkit’s primary job is to hide, not to spread. It provides stealthy, long-term access for attackers.
- They hide at different layers of your system, from simple applications all the way down to your physical hardware.
- The deeper a rootkit infects, the harder it is to detect and remove. Prevention is always the best strategy.
- A full system wipe and OS reinstallation is the only guaranteed way to remove a deep-level rootkit.
Don’t wait until your system starts acting strangely to take your security seriously. A proactive defense, built on reliable security software and smart browsing habits, is your strongest shield. To ensure you have the best protection, Safelyo invites you to explore our expert reviews on the best antivirus with anti-rootkit technology, right here in our Antivirus section.