That sinking feeling that your phone is acting weird isn’t just paranoia; it’s a valid concern in our digital-first world. Wondering how to know if your phone has been hacked often starts with small but unsettling clues – a battery that drains too fast, sluggish performance, or strange pop-ups that appear out of nowhere. These aren’t just annoyances; they can be warning signs of a serious privacy breach.
Your phone holds the keys to your life – from banking details to private conversations and personal photos. Securing it isn’t a “tech-savvy” option; it’s a fundamental necessity for everyone. Ignoring these signs is like leaving your front door unlocked and hoping for the best.
As a cybersecurity analyst at Safelyo, I’ve seen countless users alternate between panic and dismissal when they spot these red flags. The most common mistake is waiting too long to investigate. A compromised phone is more than an inconvenience; it’s a direct threat to your digital identity and financial security.
In this definitive guide, I will walk you through:
- The top 10 warning signs that your phone has been compromised.
- Simple, practical steps to check for spyware and confirm your suspicions.
- An emergency action plan to take back control immediately.
- Proven strategies to secure your phone against future attacks.
Don’t let the anxiety take over. Let’s start diagnosing the problem and reclaiming your digital security, step-by-step.
1. The top 10 warning signs your phone has been hacked
This is the most critical part of answering the question, “How to know if your phone is hacked.” Think of these as symptoms of a sick device. They might appear on their own, but if you notice several happening at once, it’s a strong signal that something is wrong. Let’s break down exactly what to look for.
1.1. Significant and unexpected battery drain
Malware and spyware are greedy. They run constantly in the background, tracking your activity, using your phone’s hardware, and communicating with a hacker’s server. All this activity consumes a massive amount of power.
Simple example: You go to bed with your phone at 80% battery and wake up to find it at 30%, even though you didn’t use it. That’s not normal aging; that’s a sign of a hidden process draining its life.
I once noticed my phone’s battery dropping 40% overnight while completely idle. I dug into the battery usage stats and found an unfamiliar app I didn’t recognize was constantly using location services. It was spyware. This is often the first and most obvious clue.
1.2. Sluggish performance and frequent crashing
If your phone suddenly feels like it’s running through mud, a hacker could be the cause. Malicious software hijacks your phone’s processor (CPU) and memory (RAM) to do its dirty work, leaving very little for your own tasks.
Simple example: Apps that used to open instantly now take forever to load. Typing on your keyboard has a noticeable delay, and your phone freezes or crashes when you’re just trying to scroll through social media.
1.3. Unusually high data usage
Spyware’s main job is to steal your information – messages, contacts, photos, location history – and send it back to the hacker. This transfer uses your internet connection, leading to a spike in your data consumption.
Simple example: You have a 10GB monthly data plan that usually lasts the whole month. Suddenly, you get a notification that you’ve used 80% of it in the first week, even though your browsing habits haven’t changed. This is your data plan “leaking” your personal information.
1.4. Unfamiliar apps you didn’t install
This is one of the most blatant signs of a breach. Finding a strange app on your phone is like finding a stranger’s coat in your closet – you know for a fact you didn’t put it there. Hackers often disguise these apps with generic names like “System Service” or “Sync Manager” to avoid suspicion.
1.5. Constant pop-ups and strange ads
If you’re seeing pop-up ads even when your browser is closed, your phone is likely infected with adware. While less dangerous than spyware, adware is designed to aggressively display ads and can often link to more malicious websites or scams. A healthy phone should not be bombarding you with ads on its home screen.
1.6. Your phone gets hot for no reason
It’s normal for a phone to get warm when you’re gaming for an hour or recording a 4K video. It is not normal for it to feel hot to the touch when it’s just sitting on the table or in your pocket. This overheating is caused by the processor working overtime to run malicious code in the background.
1.7. Strange activity on your online accounts
Your phone is often the hub for all your online accounts. If a hacker gets in, they can access saved passwords or session tokens. The first signs might not even appear on your phone itself.
Simple example: You get an email notification that your Facebook password was reset, but you didn’t do it. Or a friend asks why you sent them a weird link on Instagram that you know you never sent.
1.8. Outgoing calls or texts you didn’t make
Some types of malware are designed to use your phone to send SMS messages to premium-rate numbers, racking up charges on your bill. Others will text malicious links to everyone in your contact list to spread the infection.
1.9. Your camera or microphone turns on unexpectedly
This is one of the most chilling signs. On modern Android and iOS devices, you’ll see a small green or orange dot in the corner of your screen when the camera or microphone is active. If you see this dot appear when you aren’t actively using an app that needs them, it could mean someone is watching or listening in.
Real-world threat: This isn’t just theory. Sophisticated spyware like the infamous Pegasus was specifically designed to gain this level of control, showing how severe this threat can be.
1.10. Difficulty shutting down your phone
Malware wants to remain active and hidden. To do this, some strains can interfere with the phone’s power-off sequence. If you try to shut down your phone and it takes an unusually long time, fails to shut down, or restarts itself, the malware might be fighting to keep its connection alive.
You may also be interested in:
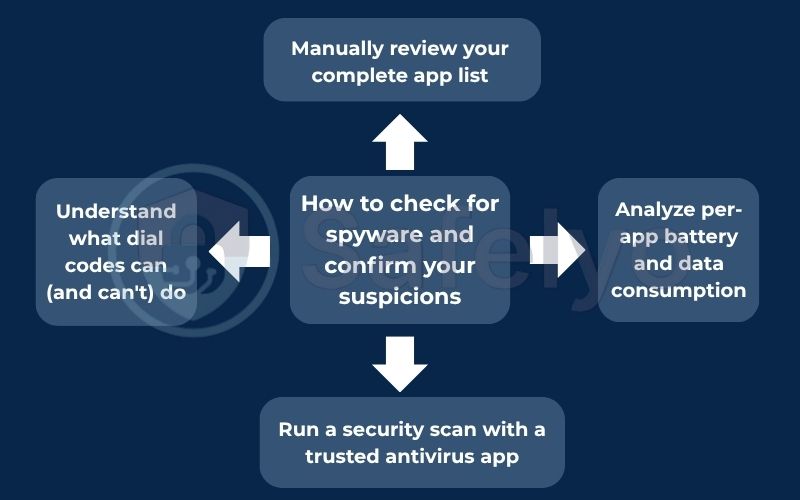
2. How to check for spyware and confirm your suspicions
Recognizing the signs is step one. Now, let’s play detective. If you suspect a hacker has targeted your device, you don’t have to guess. Here are the concrete steps you can take to find the evidence and move from suspicion to confirmation.
2.1. Manually review your complete app list
This is the digital equivalent of checking for intruders in your house. Hackers rely on you not looking too closely at your installed applications.
- For Android users: Go to Settings > Apps > See all apps. Take your time and scroll through the entire list.
- For iPhone users: Go to Settings > General > iPhone Storage. This will show you a list of all your apps and how much space they occupy.
Look for any app that you do not remember downloading. Hackers are clever and often use generic names (e.g., “Update,” “System Service,” “Backup”) to blend in. A pro tip: if you see an app and don’t know what it is, do a quick Google search for its name. You’ll quickly find out if it’s a legitimate part of your operating system or a known piece of malware.
2.2. Analyze per-app battery and data consumption
Remember those symptoms of sudden battery drain and high data usage? This is where you find the culprit. Your phone keeps detailed logs of which apps are the biggest resource hogs.
- To check battery usage: Go to Settings > Battery > Battery usage.
- To check data usage: Go to Settings > Network & internet > Data usage (or “Cellular” on iPhone).
Look for mismatches. A simple note-taking app you open once a day should not be at the top of your battery consumption list. A weather app shouldn’t be using gigabytes of data. If an app’s resource use seems wildly out of proportion with how you use it, you’ve found a major red flag.
2.3. Understand what dial codes can (and can’t) do
Let’s clear up a big myth. You’ll find many articles claiming you can dial special codes to see if you’re hacked. This is mostly misleading. These codes are useful diagnostic tools for your mobile carrier settings, primarily for checking call forwarding, but they cannot detect malware or spyware.
As an expert, it’s my job to give you the truth. Using these codes won’t hurt, but don’t rely on them as a hacking test. Here’s what they actually do:
| Dial Code | Real Purpose |
| *#21# | Checks if your calls, messages, and other data are being unconditionally forwarded to another number. It’s useful for seeing if your calls are being diverted without your phone even ringing. |
| *#62# | Checks where calls, texts, and data are being forwarded to when your phone is unreachable (i.e., turned off or out of service area). |
| ##002# | This is a universal code to disable all call forwarding. If you suspect your calls are being diverted, this is a quick way to switch it off. |
Knowing these is good for your general security, but it’s not a hacking diagnostic tool.
2.4. Run a security scan with a trusted antivirus app
While the manual checks above are a great start, the most reliable and efficient way to confirm a hacking attempt is to use a tool built for the job. You can’t always spot sophisticated malware with the naked eye.
A reputable mobile antivirus or security app is designed to:
- Scan all your files and applications against a massive, up-to-date database of known threats.
- Identify hidden spyware, trojans, adware, and other malicious code that you might miss.
- Safely quarantine or remove the threat without you having to manually dig through system files.
Think of it this way: You can look for symptoms of an illness yourself, but a doctor with the right diagnostic tools will give you the definitive answer. A good security app is that doctor for your phone.
3. Your emergency action plan: What to do if your phone is hacked
Okay, so you’ve found compelling evidence – or you’re certain enough – that your phone has been compromised. The most important thing to do now is not to panic. Panicking leads to mistakes. Instead, follow this step-by-step emergency plan. I’ve ordered these steps from the least invasive to the most drastic, so you can regain control methodically.
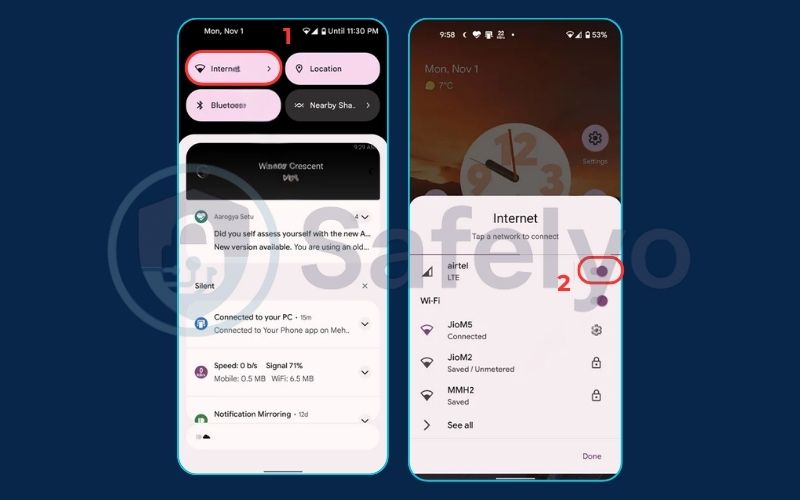
3.1. Step 1: Disconnect from the internet immediately
The first and most critical action is to cut the hacker’s connection. A compromised phone is only useful to an attacker if it can send them your data.
- How to do it: Swipe down from the top of your screen and turn off both Wi-Fi and Mobile Data. If you’re not sure, just enable Airplane Mode.
Think of this as unplugging a burglar’s getaway car. They can’t steal anything else from your house if they have no way to transport it. This simple action stops any ongoing data theft in its tracks and gives you a safe window to work.
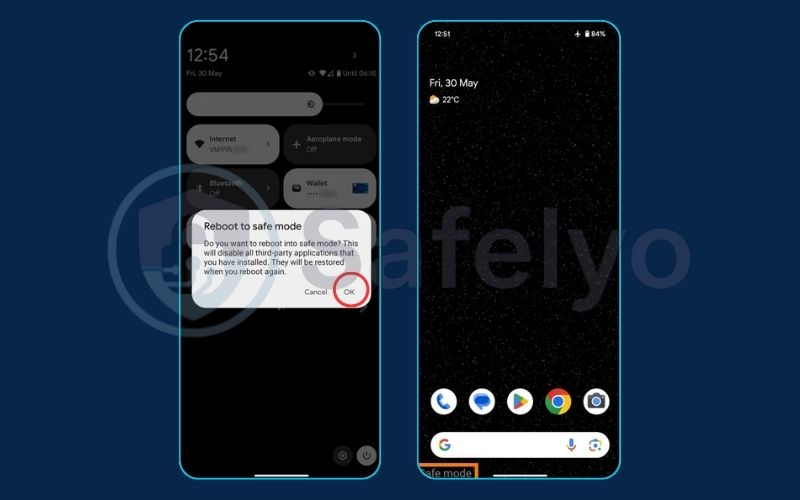
3.2. Step 2: Boot into safe mode and remove suspicious apps
Safe Mode is a diagnostic startup mode that loads your phone’s operating system without running any third-party apps. If a malicious app is causing problems, it won’t be able to run in Safe Mode, making it easier for you to uninstall it.
- For Android users: The process can vary slightly, but it generally involves pressing and holding the power button, then long-pressing the “Power off” option until a “Reboot to safe mode” prompt appears. Once in Safe Mode (you’ll see the words “Safe Mode” on the screen), go to Settings > Apps and uninstall the suspicious app you identified earlier.
- For iPhone users: iPhones don’t have a user-accessible “Safe Mode” like Android devices. The closest equivalent action is to immediately delete the suspicious app. If the app is preventing you from using your phone properly, the next steps (changing passwords and factory reset) become even more critical.
3.3. Step 3: Inform your contacts and change your passwords
The hacker may have used your phone to send malicious links to your friends and family or gained access to your accounts. You need to perform damage control.
- First, warn your people: Send a quick message from a trusted device (or call them) to let them know your phone was hacked and to ignore any strange messages from you.
- Then, lock down your accounts: Using a different, secure device (like a laptop or a family member’s phone), immediately change the passwords for your most important accounts. Start with these:
- Your primary email (Google, Outlook, etc.)
- Banking and financial apps
- Social media accounts (Facebook, Instagram, X/Twitter)
- Your Apple ID or Google Account password.
3.4. Step 4 (the last resort): Perform a factory reset
If you can’t find the malicious app, or if you simply want to be 100% certain the threat is gone, a factory reset is your nuclear option. This will completely erase everything on your phone – apps, photos, settings, and all malware – and return it to its original, out-of-the-box state.
Warning: This will delete all your data. Ensure you have a recent backup of your essential files (photos, contacts) before you proceed.
I always tell people to treat a factory reset as the ultimate cleansing tool. While it feels drastic, the peace of mind you get from knowing your device is completely clean is invaluable. Don’t hesitate to use it if you have any doubts.
Here’s how to do it:
- How to factory reset an iPhone:
- Go to Settings > General.
- Scroll down and tap Transfer or Reset iPhone.
- Tap Erase All Content and Settings.
- You’ll be asked to enter your passcode and Apple ID password to confirm.
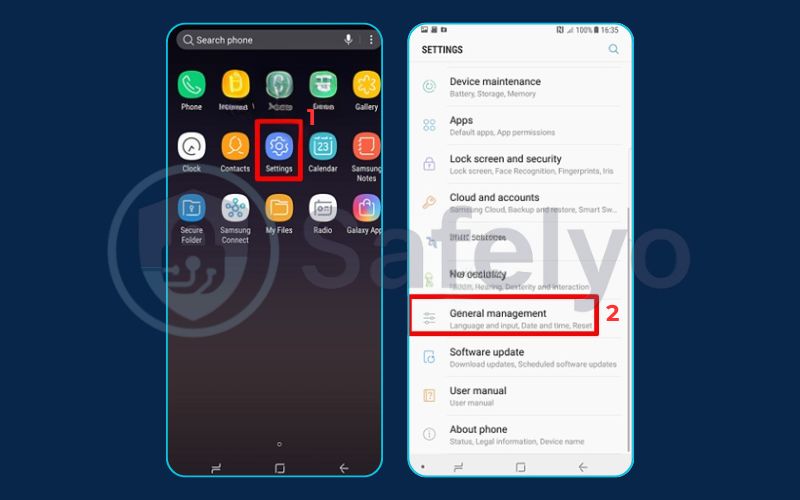
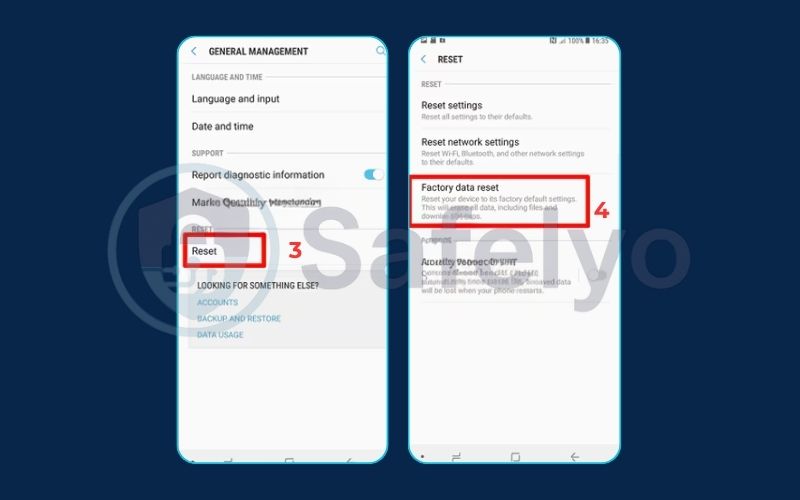
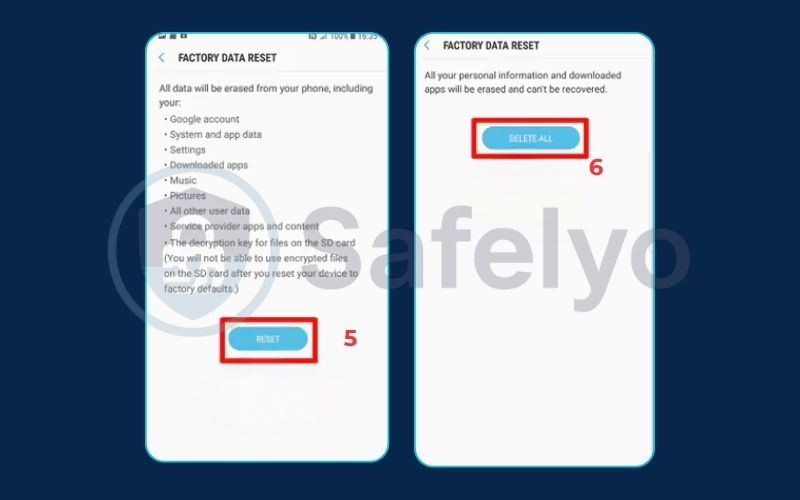
- How to factory reset an Android phone:
- Go to Settings > System (or “General Management” on Samsung devices).
- Find and tap Reset options.
- Select Erase all data (factory reset).
- You will need to confirm your choice and enter your PIN or password.
(Note: The exact menu names might differ slightly depending on your phone’s manufacturer, but the process is always found within the main settings menu.)
4. How do phones get hacked in the first place?
Understanding how a breach happens is the first step toward preventing one. Hackers don’t just magically appear on your device; they exploit common pathways that rely on human error or security oversights. From my experience in cybersecurity, nearly all phone hacks trace back to one of these five entry points.
Here are the most common ways your phone can be compromised:
- Phishing & Smishing: This is the number one method. Phishing involves receiving a deceptive email, while smishing (SMS phishing) uses text messages. The message creates a sense of urgency – like a fake package delivery notice or a bank alert – and tricks you into clicking a malicious link or downloading an infected file.
- Simple example: You get a text saying, “Your Netflix account has been suspended. Click here to reactivate.” The link leads to a fake login page that steals your credentials.
- Malicious Apps: You might download an app that seems legitimate but contains hidden malware. This is especially risky if you download apps from unofficial, third-party app stores. Even the official Google Play Store and Apple App Store can sometimes host malicious apps that slip through their review process.
- My advice: I always tell people to be wary of apps that ask for permissions they don’t need. A simple flashlight app has no business asking for access to your contacts and microphone.
- Unsecured Public Wi-Fi: When you connect to a free Wi-Fi network at a café, airport, or hotel, you could be connecting to a network set up by a hacker. They can position themselves between you and the internet in what’s called a “Man-in-the-Middle” (MITM) attack, allowing them to intercept your data, including passwords and credit card details.
- Physical Access & Spyware: Sometimes, the threat is closer to home. If someone has physical access to your unlocked phone, even for a few minutes, they can install spyware. This type of software is designed to be completely hidden and monitor all your activity.
- Zero-Day Exploits: This is the rarest but most dangerous method. A “zero-day” is a security vulnerability in your phone’s software that the manufacturer doesn’t know about yet. Highly sophisticated hackers and government agencies can use these flaws to target specific individuals. While unlikely for the average person, it highlights why keeping your software updated is so important – updates often contain patches for these very flaws once they are discovered.

5. How to secure your phone and prevent future attacks
You’ve worked hard to clean and secure your device. Now, let’s make sure you never have to go through that again. As the old saying goes, “an ounce of prevention is worth a pound of cure.” In cybersecurity, this is the golden rule. Adopting these simple habits will dramatically reduce your risk of being hacked in the future.
- Keep your operating system and apps updated.
Software updates aren’t just for new emojis and features. They contain critical security patches that fix the vulnerabilities hackers love to exploit. Enable automatic updates on your phone so you don’t even have to think about it.
- Use strong, unique passwords and a password manager.
Never reuse passwords across different accounts. If one account is breached, all your other accounts become vulnerable.
Think of it like using the same key for your house, car, and office. If a thief steals that one key, they have access to everything.
MY PRO:
The best solution is to use a reputable password manager. It will generate and store incredibly strong, unique passwords for every site, and all you have to remember is one master password.
- Enable two-factor authentication (2FA) everywhere possible.
2FA is one of the most powerful security measures you can use. It requires a second form of verification (like a code sent to your phone or an authenticator app) in addition to your password. This means even if a hacker steals your password, they still can’t get into your account.
- Only download apps from official sources.
Stick to the Google Play Store for Android and the Apple App Store for iPhone. While not flawless, they have security measures in place to vet apps. Sideloading apps from random websites is like inviting a stranger into your home without checking who they are first.
- Be cautious of public Wi-Fi networks.
Avoid doing sensitive activities like online banking on unsecured public Wi-Fi. If you must use it, protect your connection with a Virtual Private Network (VPN). A VPN encrypts your traffic, making it unreadable to any eavesdroppers on the network.
- Learn to recognize phishing attempts.
Always be suspicious of unsolicited emails and texts that ask for personal information or create a sense of urgency. Look for red flags like spelling mistakes, generic greetings (“Dear Customer”), and suspicious links. When in doubt, don’t click.
- Regularly review app permissions.
Once a month, take two minutes to go through your app permissions (Settings > Apps > App permissions or Settings > Privacy). Does that game really need access to your microphone? Does that photo editor need your location? Revoke any permissions that don’t make sense. This limits what an app can do if it ever gets compromised.

See also:
6. FAQ about how to know if your phone has been hacked
Even with a detailed plan, it’s normal to have a few more specific questions. Here are clear, direct answers to some of the most common concerns we hear from users worried about their phone’s security.
What are the signs of a phone being hacked?
The most common signs include sudden and severe battery drain, unusually high data usage, sluggish performance or frequent crashes, the appearance of unfamiliar apps, and a constant barrage of pop-up ads.
Can you check to see if your phone is hacked?
Yes, absolutely. You can perform several checks yourself: manually review your list of installed apps for anything you don’t recognize, analyze your battery and data usage stats to find resource-hungry culprits, and for a definitive answer, run a full scan using a trusted mobile antivirus app.
Can you tell if someone is accessing your phone?
Yes. Beyond the general signs of hacking, you can look for direct evidence of remote access. This includes seeing the camera or microphone indicator light (a green or orange dot) turn on unexpectedly, noticing strange activity on your linked social media or email accounts, or finding outgoing calls and texts in your log that you never made.
Can you remove hackers from your phone?
Yes. In most cases, you can remove a hacker’s access by finding and uninstalling the malicious app responsible for the breach. For a guaranteed and complete removal of all malicious software, performing a factory reset is the most effective solution.
Does a factory reset remove all hackers?
Yes, in almost all cases. A factory reset erases all software and data from the device, including any malware, spyware, or trojans. It effectively returns your phone to a “clean slate” and is considered the most powerful tool for removing a persistent infection.
Can my phone be hacked by just answering a call or opening a text?
Simply answering a phone call poses a very low risk. However, opening a text and clicking a malicious link inside it (a technique called “smishing”) is one of the most common ways phones get hacked. Always be cautious of links from unknown or suspicious sources.
Are iPhones immune to hacking?
No device is 100% immune. While Apple’s “walled garden” ecosystem and strict App Store policies provide very strong security, iPhones can still be compromised, especially through sophisticated phishing attacks or advanced spyware. They are generally more difficult to hack than Android devices, but not impossible.
7. Conclusion
Knowing how to know if your phone has been hacked is the first and most powerful step toward protecting your entire digital life. By learning to recognize the warning signs and having a clear emergency plan, you can shift from a state of worry to one of confident action. You are now equipped to diagnose problems and handle threats effectively.
To keep your device secure, always remember these key points:
- Stay vigilant: Pay attention to the unusual signs your phone gives you – they are often the first alarm bell.
- Check regularly: Periodically review your apps, permissions, and resource usage.
- Act fast: If you suspect a breach, disconnect from the internet and begin your action plan immediately.
- Prioritize prevention: Strong security habits are your best defense against future attacks.
Don’t leave your digital safety to chance. For a solid and proactive layer of protection, explore the in-depth guides and expert reviews in Safelyo’s Antivirus section. Safelyo will help you find the best security solution to keep your phone and your data safe for the long haul.







