Feeling that gut-wrenching anxiety about how to remove spyware from iPhone? The thought that someone could be monitoring your every move is deeply unsettling. While sensational headlines often spotlight sophisticated state-level spyware, the reality for most people is far less cinematic and usually involves a much more personal threat.
With over a decade of experience in personal and mobile security, I’ve consulted on countless cases where individuals felt their privacy was compromised. The pattern is almost always the same: the breach doesn’t come from a shadowy international hacker, but from someone who had a brief moment of physical access to an unlocked phone. This isn’t about being a tech expert; it’s about understanding the real risks.
In this realistic, no-panic guide, you will learn:
- The two most common ways spyware gets onto an iPhone.
- How to use Apple’s powerful, built-in security tools to fight back.
- A clear, step-by-step plan to find, remove, and lock out any threats.
- How to secure your device to prevent this from ever happening again.
Let me guide you through a calm, methodical process to secure your iPhone and reclaim your privacy.
Quick Spyware Check
Ask Yourself These 3 Questions
Before we dive deep, let’s perform a quick reality check. The answer to your problem is often found in one of these three simple questions.
- Has someone else had recent, unsupervised physical access to my unlocked phone? (Yes/No)
This is the number one vector for spyware. It could be a suspicious partner, an ex, or even a roommate who had just a few minutes alone with your device while it was unlocked. - Is my iPhone jailbroken? (Do I see unfamiliar apps like Cydia or Sileo?) (Yes/No)
Jailbreaking removes many of Apple’s built-in security protections, opening the door for unauthorized apps, including spyware. - Have I recently installed a “Configuration Profile” from a source I don’t fully trust? (Yes/No)
Sometimes a malicious app or website will trick you into installing a profile that gives it broad access to monitor your device. Think of it like giving someone a master key to your phone.
If you answered ‘Yes’ to any of these questions, you should proceed with the removal steps below immediately.
1. How to remove spyware from your iPhone: A 5-step action plan
Alright, it’s time to move from detective work to direct action. We’re going to follow a methodical plan that escalates from simple fixes to a complete wipe. Start with step one and only proceed to the next if your issue isn’t resolved. This approach respects your time and data, ensuring we don’t use a sledgehammer when a simple key turn will do.
1.1. Step 1: Update to the latest version of iOS
Before you do anything else, do this. It’s the single easiest and often most effective step you can take. I always tell my clients that an updated phone is a protected phone. Apple’s security teams are constantly working to find and fix vulnerabilities that spyware could exploit. Each iOS update is like a free security upgrade for your device.
- Why it works: The spyware on your phone might be exploiting a known security loophole in an older version of iOS. Updating the software patches that hole, effectively evicting the spyware.
- How to do it: Go to Settings > General > Software Update. If an update is available, download and install it.
1.2. Step 2: Scan for unknown apps and configuration profiles
If someone manually installed something on your phone, you need to find it. This means hunting for two things: Suspicious apps and, more importantly, hidden profiles.
First, look for apps you don’t recognize. Swipe through your home screens and check your App Library (swipe all the way to the last home screen page). Stalkerware apps often use generic names like “Sync” or “Device Manager” to avoid suspicion. If you see something you don’t remember installing, delete it.
Next, and this is crucial, check for configuration profiles. In my experience, this is where most stalkerware hides. A profile can give an app broad administrative powers over your phone.
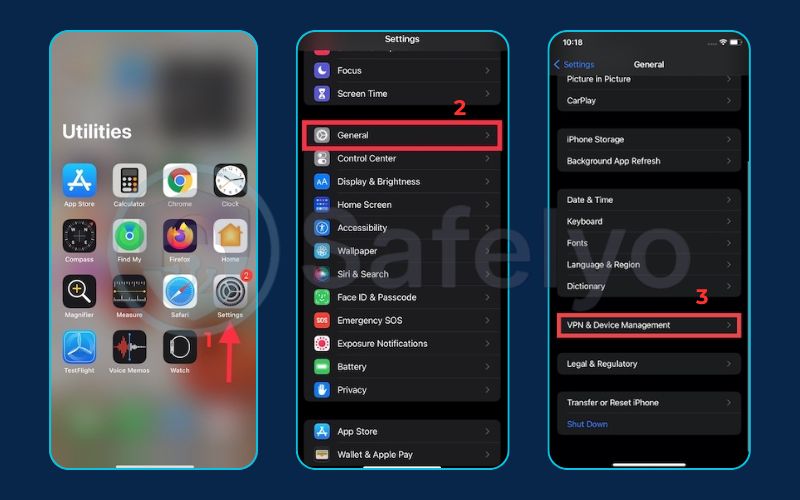
How to check for profiles
Go to Settings > General > VPN & Device Management. If you don’t have any profiles installed, you might not even see this menu option. If you do, tap on it. Look for any profile you don’t recognize. Unless it was installed by your employer or school for work/academic purposes, any unknown profile is a massive red flag and should be removed immediately.
1.3. Step 3: Use Apple’s Safety Check (your privacy superpower)
This tool is one of Apple’s best-kept secrets for personal security, and it’s designed for the exact situation you might be in. Safety Check gives you a clear dashboard of which people and apps have access to your information and allows you to quickly revoke that access.
- Why it’s powerful: It was built specifically to help people in domestic or intimate partner situations who fear they are being monitored. It’s a targeted solution from Apple itself.
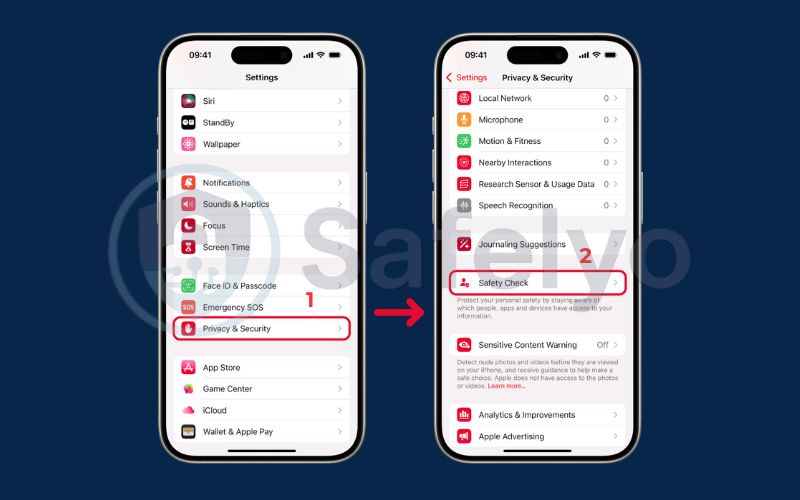
- How to use it: Go to Settings > Privacy & Security > Safety Check. You’ll see two main options:
- Emergency Reset: This is your panic button. It immediately resets access for all apps and people, signs you out of iCloud on all other devices, and lets you review your emergency contacts. Use this if you feel you are in immediate danger.
- Manage Sharing & Access: This is a more surgical approach. It guides you step-by-step through reviewing who has access to your location, photos, and other data, allowing you to revoke permissions selectively.
1.4. Step 4: Reset all settings
If the steps above haven’t given you peace of mind, this is a less drastic measure than a full factory reset. It won’t delete any of your data (apps, photos, messages), but it will reset all your system settings to their defaults.
- Why it can work: This action can sever connections that spyware relies on by resetting network settings, location permissions, and privacy settings. Think of it as a system-wide permission reset.
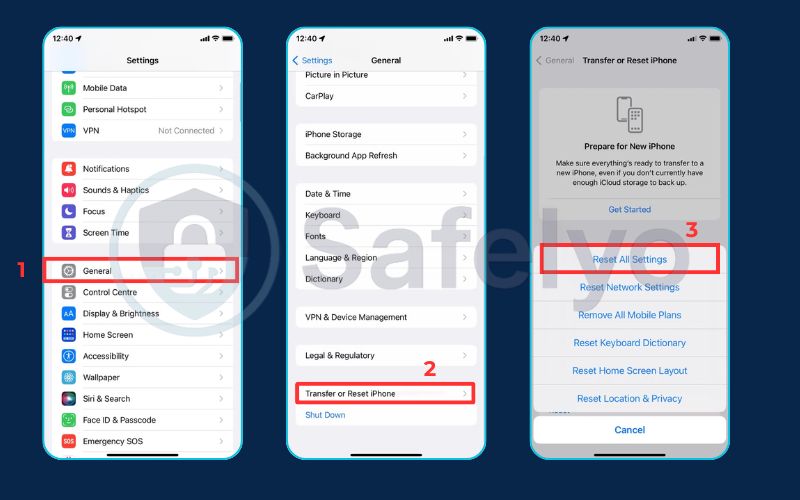
- How to do it: Go to Settings > General > Transfer or Reset iPhone > Reset > Reset All Settings. You will need to re-enter your Wi-Fi passwords and reconfigure some settings afterward, but your personal data will remain intact.
1.5. Step 5: Perform a factory reset (the final solution)
This is the nuclear option, but it is the only 100% guaranteed way to remove any and all spyware from your iPhone. A factory reset erases everything on the device and reinstalls a fresh version of iOS, returning it to the state it was in when you first took it out of the box.
The correct process:
- Manually back up your most essential data – like photos to iCloud or a computer, and ensure your contacts are synced with iCloud.
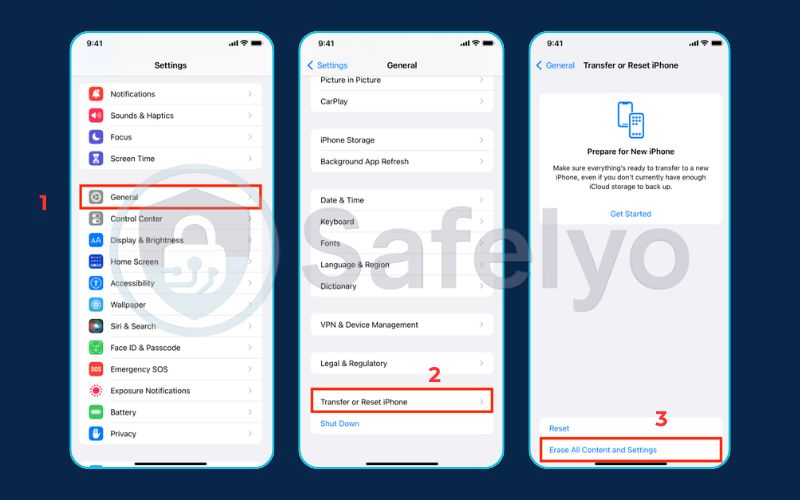
- Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
- Follow the prompts. When setting the phone up again, choose the option to “Set Up as New iPhone.” This is the key to ensuring a completely clean slate. I’ve walked many clients through this, and the relief they feel knowing their device is truly clean is worth the effort.
The critical warning
When you reset your phone, you will be given the option to restore from a backup. Do not restore from a recent backup! Doing so could reinstall the very spyware you’re trying to get rid of.
2. Signs of spyware on your iPhone (and what they might also mean)
Spyware is designed to be sneaky, but it’s rarely a perfect ghost. It leaves clues, but these clues can often be mistaken for everyday iPhone quirks. The key is not to panic at a single symptom, but to look for a pattern of unusual behavior. Think of yourself as a detective looking for evidence.
2.1. Rapid battery drain
Spyware is a marathon runner, not a sprinter. It’s constantly working in the background – logging your keystrokes, tracking your location, and uploading data. This non-stop activity consumes a lot of power, causing your battery to drain much faster than usual.
- Other possible causes: I’ve seen this happen countless times for benign reasons. A recent iOS update can cause temporary battery drain as your phone re-indexes files. A poorly coded app (even a popular one like Facebook) might be running wild in the background, or your battery might simply be old and losing its capacity.
- How to check: Go to Settings > Battery. Scroll down to see the list of apps and their battery usage. Is there an app you don’t recognize at the top of the list? That’s a major red flag.
2.2. Overheating device
If your iPhone feels unusually warm to the touch even when you’re not actively using it, it could be a sign that a hidden process is working overtime. The phone’s processor is like a tiny engine, and when it runs constantly, it generates heat.
- Other possible causes: This is highly dependent on context. Your phone will naturally get warm while charging, playing a graphically intense game like Genshin Impact, or streaming video for an extended period. Leaving it on your car’s dashboard on a sunny day will also turn it into a tiny furnace. The concern is when it’s hot for no apparent reason.
- How to check: Pay attention to when it overheats. If it’s warm while sitting idle on your cool desk, that’s suspicious. If it’s hot after a 45-minute FaceTime call, that’s completely normal.
2.3. Unusually high data usage
Spyware is useless if it can’t send the information it collects back to its operator. This transmission requires data – often a lot of it. A sudden, unexplained spike in your cellular data usage can be a tell-tale sign that your phone is secretly communicating with someone else.
- Other possible causes: Before jumping to conclusions, check your habits. Have you been watching more TikTok or YouTube videos while away from Wi-Fi? Many apps are set to update automatically, and if this happens over cellular, it can consume a large chunk of data.
- How to check: Go to Settings > Cellular. Scroll down, and you will see a list of every app and exactly how much cellular data it has used. Look for anything unfamiliar or an app that is using a shockingly large amount of data relative to its function. A simple weather app shouldn’t be using gigabytes of data.
2.4. Strange texts or notifications
Sometimes spyware can cause weird behavior, like receiving odd-looking text messages with random characters or seeing notifications that disappear when you tap them. These can be command codes from the person controlling the spyware or simply glitches caused by the software’s interference.
- Other possible causes: Let’s be honest, the most likely culprit is regular spam. We all get bizarre phishing texts about a package delivery or a suspicious charge on an account we don’t have. It’s more likely you’re a target of a mass spam campaign than a specific spyware attack.
- How to check: The best check is simple critical thinking. Do not click any links in suspicious messages. Look for poor grammar and a sense of false urgency. These are hallmarks of spam, not sophisticated spyware.
3. The reality of spyware on iPhone: what you’re actually facing
It’s easy to spiral into panic, imagining sophisticated hackers targeting you from across the globe. But before you do, let’s take a deep breath and ground ourselves in reality. Your iPhone is, by design, a remarkably secure device. Understanding why it’s secure helps you understand the real threats you’re likely facing.
3.1. The “walled garden” protection
Think of your iPhone’s operating system (iOS) as a fortress with high walls and strict guards – what we in the tech world call a “walled garden.” Apple acts as the gatekeeper.
Every app you download from the official App Store has been vetted and approved. Furthermore, each app is “sandboxed,” meaning it’s forced to play in its own little area and isn’t allowed to access the core system or data from other apps without your explicit permission. This design makes it incredibly difficult for traditional malware to infect your device remotely.
3.2. The two most common infection methods
So, if the fortress is so strong, how do intruders get in? In my experience, they almost never scale the walls from the outside. Instead, they get in through one of two doors that were left open from the inside.
Physical Access (The "Stalkerware" Scenario)
This is, by far, the most common situation I’ve encountered. Someone you know gets hold of your unlocked iPhone, even for just a couple of minutes. In that short time, they can install a hidden tracking app or a “configuration profile” that monitors your location, messages, and calls. It’s not high-tech hacking – it’s a low-tech betrayal of trust.
Jailbreaking (The "Self-Sabotage" Scenario)
Jailbreaking your iPhone is like intentionally knocking down the fortress walls to have more freedom. It allows you to install apps from anywhere, not just the safe App Store. While this might sound appealing, it completely removes the security features that protect you, making your device an easy target for any spyware disguised as a useful app.
3.3. What about advanced spyware like Pegasus?
You’ve likely heard of military-grade spyware like Pegasus. Yes, it’s real, and it’s terrifyingly powerful. But it’s also crucial to understand who it targets.
According to cybersecurity research reports, these tools cost millions of dollars and are used by government agencies to target extremely high-profile individuals like journalists, activists, and political dissidents. For the average person, worrying about Pegasus is like worrying about a shark attack in your swimming pool. It’s not a realistic threat. The real danger is much closer to home.
Read more:
4. How to prevent spyware from returning: A security checklist
Removing spyware is only half the battle. The other half is ensuring your digital fortress is locked down so it never happens again. Think of this as changing the locks after an intrusion. The following steps aren’t complicated; they are fundamental security habits that address the most common ways iPhones are compromised.
Secure your lock screen
This is your front door. Use a strong, non-obvious passcode (not “123456” or your birthday). Better yet, rely on Face ID or Touch ID. In my experience, the moment of opportunity for a snooper is almost always when a phone is left unlocked and unattended, even for just 30 seconds.
Enable two-factor authentication (2FA)
This is one of the most powerful security features you can enable. It protects your Apple ID by requiring a second verification step (usually a code sent to a trusted device) before anyone can access your account, even if they have your password. This prevents someone from spying on you through your iCloud account.
Never share your Apple ID password
Treat it with the same secrecy as your bank account PIN. Your Apple ID is the master key to your entire digital life – photos, messages, backups, and location. Don’t give that key to anyone.
Do not jailbreak your iPhone
I know the temptation for customization can be strong, but it’s simply not worth the risk. By jailbreaking, you are single-handedly dismantling the “walled garden” security that makes your iPhone so safe. Keeping your phone’s software as Apple intended is your best defense.
Be mindful of physical access: This brings us back to the most common threat. Don’t leave your phone unlocked and unattended around people you don’t fully trust. It sounds simple, but this basic habit thwarts the vast majority of real-world spyware incidents I’ve investigated.
Safelyo’s Expert Advice
Dealing with Stalkerware
The threat of being monitored by a partner, ex-partner, or family member is a serious and deeply personal violation of privacy. It’s a reality many people face, and it’s important to know you are not alone. Apple’s Safety Check feature is your first and best line of defense, designed specifically for this scenario. If you believe you are in immediate danger, please do not hesitate to contact local law enforcement. Securing your device is a critical step in reclaiming your personal safety and digital freedom.
5. FAQ about how to remove spyware from iPhone
We’ve covered a lot of ground, but you might still have some specific questions. Here are quick, direct answers to the most common concerns we hear about iPhone spyware.
How do I check if my iPhone has spyware?
There is no single “scan” button for spyware on an iPhone due to Apple’s security design. Instead, the check is a manual process:
- Look for unknown apps on your home screen and in your App Library.
- Go to Settings > General > VPN & Device Management to check for suspicious configuration profiles.
- Review your battery and data usage in Settings for any unrecognized apps consuming high resources.
- Use Apple’s Safety Check feature under Settings > Privacy & Security to review who and what has access to your data.
What is the code for iPhone to see if someone is spying?
There are no secret codes to detect spyware on an iPhone. You may see websites mentioning codes like *#21# or *#62#, but this is misinformation. These are network-level codes used to check the status of call forwarding, a feature provided by your mobile carrier, and have nothing to do with spyware installed on your device.
Can resetting an iPhone remove spyware?
Yes, a full factory reset is the most reliable and guaranteed method to remove all software, including any spyware. The most important step is to choose “Set Up as New iPhone” during the reinstallation process. Do not restore from a recent backup, as this could reintroduce the malicious software onto your clean device.
Are there any reliable spyware detection apps for iPhone?
Due to Apple’s “walled garden” security, apps from the App Store cannot scan the entire system or other apps for malware. Therefore, there are no traditional antivirus or anti-spyware scanning apps for iPhone. The best mobile security apps for iOS focus on preventative measures, such as blocking phishing websites, filtering scam texts, and securing your network connection with a VPN.
Can someone install spyware on my iPhone without touching it?
For the vast majority of people, the answer is a definitive no. Remote, “zero-click” infections are incredibly rare, expensive, and used to target high-profile individuals. The most common scenario always involves either someone gaining physical access to your unlocked phone or tricking you into installing a malicious profile or app.
6. Conclusion
Learning how to remove spyware from iPhone is ultimately about taking methodical steps, not panicking about sensationalized threats. By understanding that the most significant risks often come from physical access, you can focus your efforts on practical solutions that truly work. You are in control of your device’s security.
Key takeaways to remember:
- Focus on the most likely threats: Unsupervised physical access and jailbreaking are the main entry points for spyware, not remote hacks.
- Use Apple’s powerful built-in tools: Regular iOS updates and the Safety Check feature are your first and best lines of defense.
- A factory reset is your strongest weapon: When in doubt, erasing your device and setting it up as new provides a guaranteed clean slate.
- Proactive prevention is the best defense: A strong passcode, two-factor authentication, and being mindful of who uses your phone will prevent most issues from ever starting.
Your privacy is paramount. By understanding the real risks and knowing how to secure your device, you can use your iPhone with confidence. While these steps remove existing threats, ongoing protection against phishing and malicious websites is crucial. Explore the reviews of the best mobile security apps for iPhone from Safelyo to add an extra layer of defense. You can find more expert guides like this in our Antivirus category.







