Passwords alone are often the weakest link in website security, leaving your site vulnerable to brute-force attacks and credential theft. Relying on a single layer of protection puts your data at risk.
A much stronger defense is learning how to set up two-factor authentication on WordPress, which ensures that even if a hacker steals your password, they cannot access your dashboard.
-
Install a 2FA plugin
Choose and activate a reliable plugin like WP 2FA or Wordfence from the WordPress directory to enable authentication features.
-
Configure your method
Select your preferred verification type, such as Time-Based One-Time Passwords (TOTP) via an app or email codes.
-
Link an authenticator app
Scan the QR code provided by the plugin using an app like Google Authenticator or Authy to sync your device.
-
Save backup codes
Download or print your recovery codes immediately to ensure you can still log in if you lose access to your phone.
1. What is two-factor authentication (2FA) in WordPress?
Before diving into how to set up two-factor authentication on WordPress, it’s important to understand what 2FA is and how it fits into your overall WordPress security strategy. This section lays the foundation by defining 2FA and how it compares to other login protections.
1.1. Overview of 2FA
Two-factor authentication (2FA) is a security method that requires users to provide two forms of identification before accessing their accounts. In WordPress, this usually means entering your password plus a code sent to your mobile device or generated by an authentication app.
According to OWASP, 2FA helps defend against account takeovers by requiring access to something you know (your password) and something you have (a code from your phone).
1.2. How it strengthens WordPress login security
WordPress is one of the most targeted CMS platforms globally, and brute-force login attempts are common. Adding 2FA dramatically lowers the risk of a hacker gaining access, even if they manage to steal your password.
In my case, after enabling 2FA, I noticed zero successful unauthorized logins despite repeated attempts. The extra step made it practically impossible for bots or bad actors to break in.
Here are the main benefits at a glance:
- Stops unauthorized access with stolen credentials
- Makes brute-force attacks ineffective
- Adds peace of mind for site admins and users
1.3. Differences between 2FA, MFA, and authenticator apps
- 2FA (Two-Factor Authentication): Requires exactly two verification steps, usually a password and a code.

- MFA (Multi-Factor Authentication): A broader term that may require more than two steps, such as biometrics or hardware keys. Some enterprise setups even allow biometric login, such as using a fingerprint scanner as part of authentication.
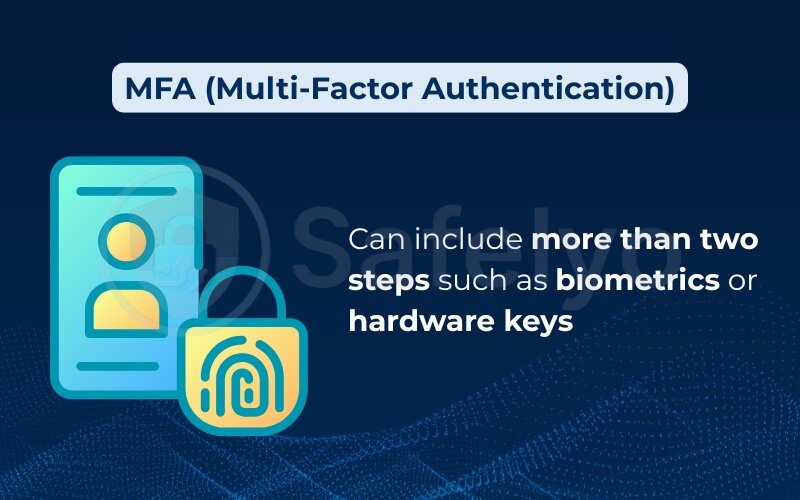
- Authenticator apps: Tools like Google Authenticator or Authy generate time-based codes for 2FA without needing a network connection.
For WordPress, 2FA via authenticator apps is the most practical and widely supported option.
>> You may also like this article: How to install WordPress on a local server (2 easy methods)
2. Benefits of enabling two-factor authentication
Now that we’ve covered what 2FA is, let’s explore why it’s worth your time. Enabling WordPress two-factor authentication adds more than just another login step. It builds a stronger security foundation for your entire site.
2.1. Stops brute-force attacks and phishing attempts
Hackers often launch brute force attacks by trying thousands of password combinations until they get lucky. Even if your password is strong, bots can eventually get lucky, unless 2FA is in place.
I once worked with a client who ran an e-commerce site on WordPress and regularly faced login attempts from dozens of IPs each hour. After enabling 2FA using a plugin, the login flood didn’t stop, but not a single unauthorized login ever succeeded again. It was the simplest fix with the biggest impact.
2FA also protects against phishing, where attackers trick users into giving up passwords. Even if a user falls for it, the attacker won’t have the second authentication factor.
2.2. Enhances user trust and protects admin accounts
When your site allows user accounts, especially for content contributors, editorial staff, or subscribers, security becomes a shared responsibility. Enforcing 2FA on admin and editorial staff roles signals that your site takes safety seriously.
Many of my clients see increased user confidence when they know that security isn’t optional. One even added a short note on their login page: “Protected with 2FA for your security.” It boosted their credibility in the eyes of customers and contributors alike.
2.3. Supports GDPR/data security compliance
If you handle any user data, especially from EU visitors, then security isn’t just a best practice – it’s a legal requirement. While GDPR doesn’t mandate specific technologies, using two-factor authentication can be a strong defense if a breach ever occurs.
According to CISA, enabling multi-factor authentication is one of the most effective steps organizations can take to prevent unauthorized access.
3. How to set up two-factor authentication on WordPress
Setting up 2FA on your WordPress site doesn’t require coding skills or expensive tools. In fact, the process can be completed in under 15 minutes using reliable plugins. In this section, I’ll walk you through the key steps from plugin selection to backup configuration and testing.
3.1. Choose a plugin (free vs premium options)
The first step is to select a 2FA plugin that suits your needs. Free plugins work well for most personal blogs or small sites, while premium options are better for teams or eCommerce environments.
Here are a few popular choices:
| Plugin Name | Free Version | Best For |
| WP 2FA | Yes | Beginners, basic 2FA setup |
| Two-Factor | Yes | Open-source enthusiasts |
| miniOrange | Yes | Enterprise-level security |
| Rublon | No | Identity access management |
When I first enabled 2FA, I started with WP 2FA because it was free and beginner-friendly. Later, as my team grew, I switched to miniOrange to support role-based enforcement and enterprise-level control.
3.2. Plugin installation steps
Once you’ve selected a plugin, installation is straightforward:
- Log in to your WordPress admin dashboard.
- Go to Plugins > Add New.
- Search for the plugin (e.g., “WP 2FA”).
- Click Install Now, then Activate.
Some plugins will launch a setup wizard immediately after activation. Others may require manual configuration under Settings. Always double-check the plugin’s settings to ensure email, SMS, or app methods are enabled properly.
3.3. Configure 2FA methods: TOTP, email, SMS
After installation, choose how users will authenticate. Common options include:
- TOTP (Time-Based One-Time Passwords): Codes generated via apps like Google Authenticator, Authy, or Microsoft Authenticator.
- Email: A verification code is sent to the user’s email address. This extra verification step prevents attackers from relying only on stolen passwords.
- SMS: A code is texted to the user’s phone.
I’ve found Time-based One-Time Password to be the most reliable and secure option. For teams with stricter compliance needs, you can also integrate a hardware security key as an additional method. It works offline and avoids delays that often occur with email or SMS. Some plugins also let you generate one-time security codes that can be stored safely for emergencies. For clients who preferred convenience, I offered email-based 2FA as a fallback.
3.4. Backup code setup
Backup codes are critical in case you lose access to your authentication device. Most plugins allow you to generate and download a set of single-use backup codes.
Be sure to:
- Save them in a password manager.
- Avoid storing them on the same device as your authenticator.
- Regenerate them if you suspect they’ve been compromised. Some plugins use the term recovery codes, but the concept is the same—single-use emergency login tokens.
I once had a client lose their phone without saving any backup codes. We had to disable 2FA via database access, not ideal. Since then, I have always emphasized saving these codes first.
3.5. Testing the configuration
Before rolling out 2FA to your team or users, test it yourself:
- Log out of WordPress
- Attempt to log in with your username and password
- Confirm you receive the second factor prompt
- Use your app, email, or SMS code to complete the login
If everything works, you’re ready to move forward. If not, most plugins include a support link or troubleshooting page.
4. Example: How to set up 2FA WP on WordPress
Below are step-by-step instructions to install and configure the plugin 2FA WP properly.
4.1. Install and activate the plugin
- Go to your WordPress dashboard → Plugins > Add New
- Search for WP 2FA – Two-Factor Authentication
- Click Install Now, then Activate
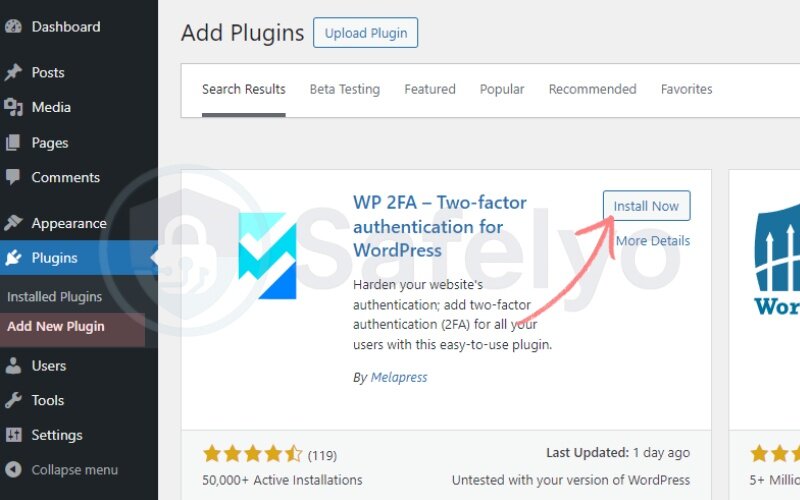
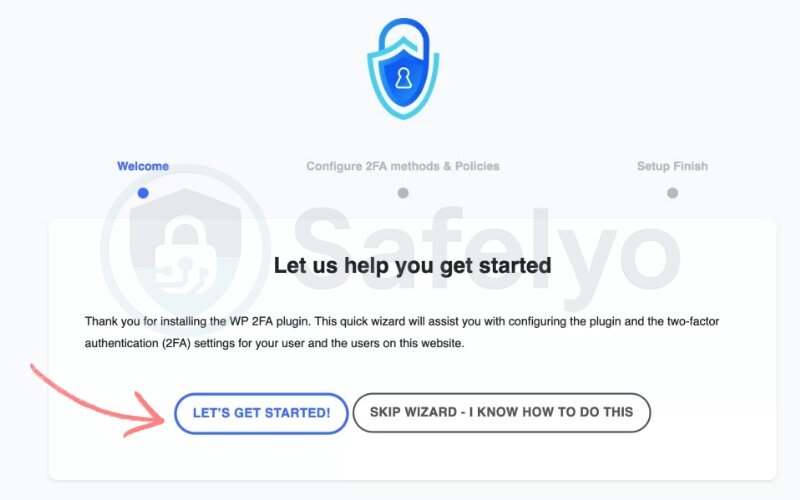
4.2. Launch the setup wizard
- After activation, the plugin will launch its setup wizard
- If it doesn’t start automatically, go to Users > Two-Factor Authentication
- Click Let’s get started to begin setup
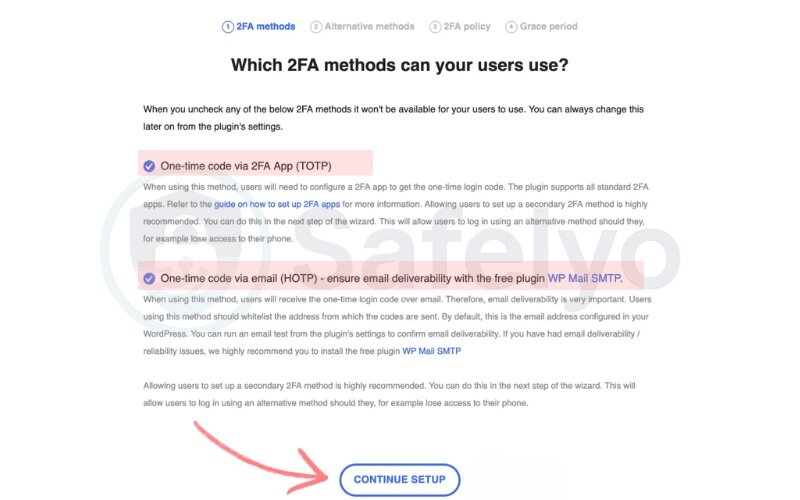
4.3. Choose authentication methods
- Select your preferred methods:
- Time-based one-time password via authenticator apps (e.g., Google Authenticator, Authy)
- Email codes as a backup or alternative
- Optionally, enable backup codes
4.4. Choose alternative methods
- Select Backup codes as your alternative method.
- These codes are generated during setup and can be used once each.
- Click Continue Setup to proceed.
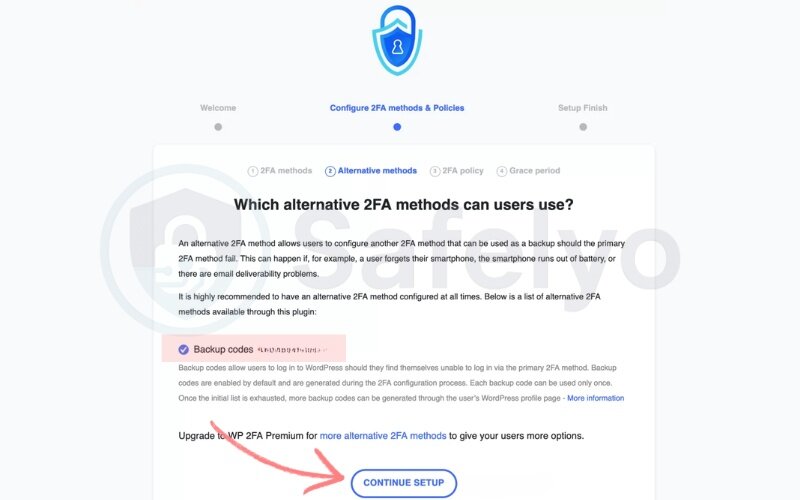
I always enable backup codes. Once, my phone ran out of battery while traveling, and these codes saved me from being locked out of my site.
4.5. Enforce 2FA for users or roles
- Decide who must use 2FA:
- All users
- Specific roles (e.g., Admins, Editors)
- Optional (users can choose to enable)

Personally, I require 2FA for admin roles to minimize risk.
4.6. Set a grace period (optional)
- Allow users a time window (e.g., 3–5 days) to complete 2FA setup before enforcement
- This helps avoid immediate lockouts

I configure a grace period, usually 2 days, so users can finish setup.
4.7. Configure 2FA for your account
- Click Configure 2FA Now
- Then choose between:
- One-time code via app (my go-to method)
- One-time code via email
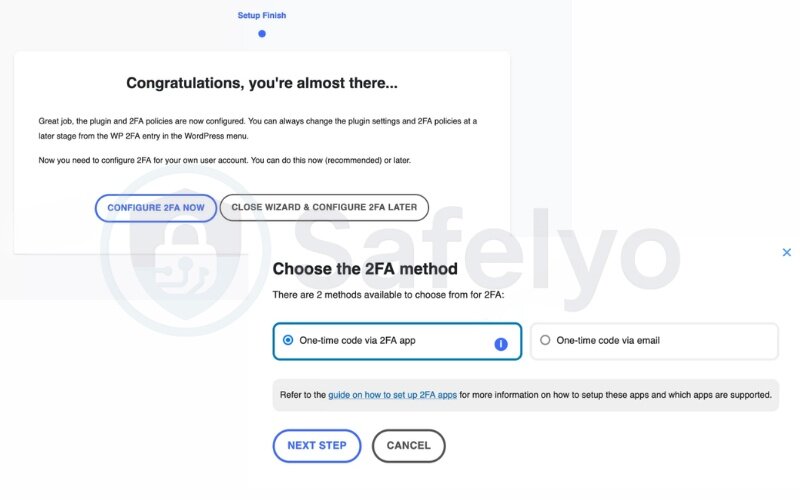
I always recommend using an authentication app for stronger protection.
4.8. Link your authenticator app
- Open your preferred two-factor authentication app, such as Google Authenticator, Authy, Duo, or Microsoft Authenticator. No matter which authenticator app you choose, make sure it supports backup or migration features.
- Scan the QR code shown in the WP 2FA plugin setup.
- Enter the 6-digit code generated by the app to confirm and activate the connection.
I personally use Authy because it allows cloud backup and multi-device sync, which saved me once when I switched phones and forgot to export my 2FA tokens. Still, I always double-check that the time on my device is accurate to avoid code mismatch issues.
Next, I’ll compare the top WordPress 2FA plugins, including their strengths, weaknesses, and compatibility with popular setups like WooCommerce or multisite.
5. Recommended WordPress 2FA plugins (with comparisons)
There’s no one-size-fits-all solution when it comes to WordPress two-factor authentication. Your ideal plugin depends on your site’s size, technical needs, and user base. This section breaks down four widely used 2FA plugins, including firsthand insights from using each on different client projects.
5.1. WP 2FA – strengths and limitations
WP 2FA is one of the most user-friendly options for beginners. It offers a setup wizard, support for multiple 2FA methods (TOTP, email), and easy enforcement by user role. It also makes it simple to enforce policies across different user roles without coding.
PROS
- Simple setup for non-technical users
- Supports backup codes and role-based enforcement
- Clean user interface
CONS
- Limited integration with third-party tools unless upgraded
- Lacks deep analytics or login reporting in the free version
I’ve used WP 2FA on several small business sites. One bakery owner appreciated that it guided her through the setup without needing IT help. However, she later upgraded to premium to enforce 2FA for staff logins.
5.2. Two-Factor – open-source community plugin
Two-Factor is a free, open-source plugin maintained by WordPress contributors. It supports Time-based One-Time Password and backup codes and integrates directly into WordPress user profile settings.
PROS
- 100% free and open-source
- Lightweight and no bloat
- Ideal for developers and technical users
CONS
- No onboarding wizard
- No built-in enforcement or team-wide controls
I once installed this plugin for a developer-focused site where users preferred manual control. It’s fast and reliable, but not ideal for non-technical teams.
5.3. miniOrange – enterprise-friendly features
miniOrange’s 2FA plugin offers powerful features geared toward enterprise sites or those with complex user environments.
PROS
- Wide range of authentication methods (including hardware keys)
- LDAP and SAML support
- Multi-site compatible
CONS
- The free tier is limited
- The interface can be overwhelming for beginners
A nonprofit client with multiple subdomains used miniOrange to enforce SSO and 2FA across the network. It took more time to configure, but the control it gave their IT team was worth it.
5.4. Rublon – identity management integrations
Rublon is a premium-only plugin designed for businesses that want integrated identity and access management (IAM). It offers risk-based authentication and advanced reporting.
PROS
- Strong IAM features
- Email-based 2FA and mobile app
- Admin dashboard with login reports
CONS
- No free version
- Requires registration and an external account
I helped a fintech startup use Rublon to secure client access portals. Its centralized dashboard and user audit logs made it a good fit for compliance-driven environments.

5.5. Plugin compatibility (WooCommerce, multisite, etc.)
When selecting a plugin, always consider compatibility with your tech stack:
| Feature/Use Case | WP 2FA | Two-Factor | miniOrange | Rublon |
|---|---|---|---|---|
| WooCommerce support | Yes | No | Yes | Yes |
| WordPress multisite | Yes | No | Yes | Yes |
| Role enforcement | Yes | No | Yes | Yes |
| Backup codes | Yes | Yes | Yes | Yes |
If your site still uses XML-RPC or legacy APIs, make sure the plugin you choose supports blocking or securing those endpoints. The same applies to the WP REST API, which should be secured alongside your login page for complete protection.
Each plugin offers something different. I typically recommend WP 2FA for small to mid-size sites, and miniOrange or Rublon for large organizations with IT departments. Up next, we’ll look at how to enforce 2FA for specific users and roles, especially if you manage a team, contributors, or multiple admins.
6. How to Enforce Two-Factor Authentication for teams and roles
If you manage a team of contributors, editors, or clients on your WordPress site, simply enabling 2FA isn’t enough – you need to Enforce Two-Factor Authentication to protect every account. This section walks you through how to ensure 2FA is required for specific roles or all users, while avoiding common pitfalls like user lockouts.
6.1. Enforcing 2FA for admin/editor roles
Admins and content Editors are high-value targets for hackers. Fortunately, most modern plugins let you require 2FA based on user roles. Premium plugins often allow you to force setup only for the Administrator role, giving flexibility in enforcement.
Here’s how I did it using WP 2FA:
- Go to the plugin’s settings in the WordPress dashboard.
- Navigate to the plugin’s settings and locate the Policies or User Rules section.
- Select roles like Administrator, Editor, and Super Admin if available.
- Set a grace period (e.g., 7 days) for users to configure their 2FA.
One client of mine had three admins managing a WooCommerce store. After enforcing 2FA for their roles, they noticed a drop in suspicious admin login efforts. It added a quick layer of protection without disrupting workflows.
6.2. Mandatory 2FA for new users
If you accept user registrations for memberships, subscriptions, or even blog comments, you may want all new accounts to enable 2FA by default.
Many 2FA plugins offer this via onboarding prompts or forced setup screens during the first login. You can also:
- Include 2FA setup instructions in welcome emails
- Auto-assign user roles that already have enforced 2FA policies
- Use plugins with redirection or enforcement hooks at login
When helping a membership-based fitness site implement this, we added a 2FA notice to their onboarding welcome message. The result? Nearly 90% of users activated 2FA within the first week.
6.3. Preventing accidental lockouts
The easiest way to Enforce Two-Factor Authentication is to apply mandatory setup during the first login of every new account. Enforcing 2FA can backfire if users get locked out, and you have no recovery plan.
Here’s how I avoid this:
- Enable backup codes for all users
- Whitelist admin IPs temporarily during rollout
- Maintain emergency access accounts without 2FA (with strong passwords)
- Clearly document how users can reset or recover their 2FA (see Section 6)
I once had to recover access for a site where all admins enabled 2FA, but none saved backup codes. The only solution was database access via cPanel, which took hours. Since then, I have included backup code setup in every 2FA enforcement plan.
6.4. Plugin-based policy control
On WordPress multisite networks, enforcing 2FA for the Super Admin role is especially important, since this account controls every site. Most premium 2FA plugins offer granular policy tools, such as:
- Forcing 2FA for specific roles or user IDs
- Blocking access to wp-admin if 2FA isn’t set
- Logging compliance per user
In miniOrange, for example, I used Role-based Enforcement Policies to separate staff and freelancers, giving only internal users access to more secure 2FA flows.
These controls help scale 2FA securely across large teams or multi-author blogs.
Next, we’ll explore how to troubleshoot common issues like login loops, device loss, or failed authentication codes. So you’re never locked out unexpectedly.
7. Troubleshooting two-factor authentication issues
Even with the best setup, things can go wrong. Whether it’s a lost phone or a misbehaving plugin, two-factor authentication issues can lock you and your users out of WordPress. This section covers the most common problems and how to solve them without compromising site security.
7.1. Can’t access 2FA codes (lost phone/device)
This is the most frequent issue I encounter with clients. A user switches phones and forgets to migrate their authenticator app, resulting in being locked out.
Solutions:
- Use backup codes if previously saved
- Log in via a recovery email (if enabled by your plugin)
- Access your site via FTP or cPanel to disable the plugin manually
- For plugins like WP 2FA, you can temporarily disable 2FA by renaming the plugin folder in /wp-content/plugins/
I always advise clients to save backup codes in a security code manager like Bitwarden or 1Password. One eCommerce client avoided a crisis thanks to that habit when her phone was stolen during travel.
7.2. Plugin conflicts or login loop issues
Sometimes 2FA plugins conflict with security plugins, caching layers, or custom login pages, causing login loops or failed authentication. In some cases, vulnerabilities in XML-RPC can also bypass weak login setups if two-factor authentication is not enforced.
Fixes:
- Clear your site and browser cache
- Temporarily deactivate other security plugins (e.g., Wordfence, iThemes)
- Revert to the default login page (/wp-login.php)
- Review plugin compatibility documentation
When this happened to a client using a custom login page builder, switching to the default login screen solved the issue instantly. We later re-enabled the builder after adjusting plugin priorities.
7.3. 2FA is not prompting on login
In some cases, users simply haven’t enabled 2FA under their profile settings. If users aren’t being asked for a second factor, it may be due to:
- Role-based 2FA settings are incomplete
- Plugin misconfiguration or an outdated version
- Conflict with single sign-on (SSO) or caching tools
How to fix:
- Recheck the enforcement policies in the 2FA plugin
- Update the plugin to the latest version
- Exclude /wp-login.php from your caching rules
- Verify that 2FA is enabled per user under their profile settings
In one case, a site using WP Rocket had login caching enabled, which prevented the 2FA prompt from appearing. Adding exceptions for login URLs fixed the issue. Always test the verification process on multiple accounts to confirm enforcement is working.
7.4. Recovery from lockout scenarios
If all else fails, here’s how to regain access:
- Via FTP/cPanel:
- Log in to your hosting panel
- Go to /wp-content/plugins/
- Rename or delete the 2FA plugin folder
- Log in to your site and reinstall the plugin as needed
- Via database (phpMyAdmin):
- Access your database
- Locate the wp_usermeta table
- Search for user-specific 2FA keys and delete them
These steps should be handled with care. I’ve had to walk several clients through this process, and it’s not ideal unless absolutely necessary.
7.5. Migrating 2FA to a new device
When changing phones, always transfer your authenticator accounts first. Apps like Authy allow secure syncing across devices, making migration simple.
Steps:
- Install the authenticator app on your new phone
- Use app-specific backup or cloud restore options
- Scan your original site’s QR code if available
- Update your 2FA method in your WordPress profile if required
I always recommend using Authy over Google Authenticator for this reason. Its multi-device support has saved several clients from full lockouts.
With the right planning, you can prevent almost all 2FA issues before they happen. Now, let’s address some frequently asked questions to clear up any lingering doubts or confusion.
8. FAQs on how to set up two-factor authentication on WordPress
This section answers some of the most common questions WordPress users have when setting up or managing two-factor authentication. These responses are designed to be beginner-friendly, clear, and actionable.
Is two-factor authentication mandatory for WordPress?
No, WordPress does not require 2FA by default.
However, many managed hosting providers (like WP Engine and Kinsta) strongly recommend it.
If you manage sensitive user data or run an e-commerce store, enabling 2FA is considered a best practice.
Which 2FA plugin is easiest to use?
WP 2FA is often considered the most beginner-friendly plugin due to its guided setup wizard and intuitive interface.
It also includes backup codes and flexible authentication options like email or app-based codes.
What if my phone is lost or stolen?
Use backup codes you saved during setup. If unavailable, log in via FTP or cPanel to disable the 2FA plugin. Once you regain access, reconfigure 2FA with your new device. Plugins like Authy allow syncing across devices to prevent this issue.
How do I reset 2FA for another user?
As an Administrator, you can disable 2FA for a specific user in the plugin’s settings panel. Alternatively, remove the 2FA metadata from the user’s profile via phpMyAdmin if locked out. Some plugins also offer a “reset 2FA” option directly in the user management screen.
Does 2FA slow down the login process?
Slightly, but usually less than 10 seconds.
Most users adjust quickly and find the added security worth the extra step. Using TOTP via an authenticator app is the fastest and most reliable method.
9. Conclusion
Overall, learning how to Enforce Two-Factor Authentication is just as important as installing the plugin itself. Two-factor authentication might seem like a small step, but it can make a big difference in your site’s overall security posture. As we’ve seen throughout this guide, knowing how to set up two-factor authentication on WordPress is not just for developers or security experts – any site owner can (and should) do it.
To recap, 2FA helps you:
- Stop brute-force and phishing attacks
- Protect admin and editorial staff accounts from unauthorized access
- Comply with privacy and security standards like GDPR
- Build user trust and enhance your site’s credibility
Getting started is simple: choose a plugin like WP 2FA, configure your preferred authentication method (we recommend Time-based One-Time Password apps), and make sure backup codes are saved securely. Then, roll out enforcement policies to team members or user roles based on your site’s needs. Start with the Administrator account before expanding enforcement to other roles.
If you haven’t enabled 2FA yet, now is the perfect time to start. Once set up, it runs quietly in the background, giving you peace of mind every time you (or someone else) logs in.
Next steps:
- Choose your plugin and install it today
- Test 2FA on your admin account
- Gradually roll out 2FA to other users and roles
- Bookmark this guide for troubleshooting and reference
Want more guides like this? Visit Safelyo, where I make Tech How-To simplified.