What is a computer virus? Think of it as the digital equivalent of a biological flu. It’s a malicious piece of code designed to latch onto a clean program, replicate itself, and spread from one computer to another, often causing damage without the user’s knowledge.
While many people use the term “virus” to describe any digital threat they encounter, a true computer virus has very specific characteristics that set it apart. In my years of analyzing cybersecurity incidents, I’ve seen that understanding these key differences isn’t just for tech experts – it’s the first and most critical step for anyone who wants to protect their digital life effectively.
-
What is a computer virus?
A computer virus is a malicious program that attaches itself to legitimate files, requiring user action to spread. It behaves like a digital parasite, causing damage without the user’s knowledge.
-
Virus vs. Worm vs. Trojan
Viruses need a host and user activation to spread, worms self-replicate across networks without user input, and trojans disguise themselves to trick users into activation.
-
How does a computer virus spread?
A virus spreads through four stages:
Attachment to a clean file, execution upon user activation, replication to infect other files, and delivery of its malicious payload.
-
The main types of computer viruses
The main types include: File infector viruses, macro viruses, boot sector viruses, polymorphic viruses, and resident viruses.
-
How to protect yourself from computer viruses
To protect yourself, use reliable antivirus software, be cautious with email attachments, keep software updated, download from trusted sources, and scan removable media before use.
In this guide, we’ll demystify exactly:
- What a computer virus is and its core traits.
- How it differs from its infamous cousins: worms and trojans.
- The essential, practical steps you can take to keep your devices virus-free.
Don’t let confusing jargon leave you vulnerable. Let me break it down for you, starting now.
1. What is a computer virus?
At its core, a computer virus is a malicious computer program written to alter the way a computer operates. But what truly defines it is its parasitic nature. The best way to think of it is as a digital parasite: it cannot survive or spread on its own and must latch onto something else.
This parasitic behavior gives a true computer virus two defining characteristics that you must understand:
- It needs a host program to survive. A virus is just a piece of code, not a standalone application. It must attach itself to a legitimate file or program – often an executable file (.exe) or a document with macros (like a Microsoft Word file). For example, it might hide inside a free calculator app you downloaded. The app itself is the “host.”
- It requires human action to spread. This is the most crucial difference. The virus remains completely dormant until you, the user, unwittingly activate it. In my experience, this is the classic infection method. You might run the infected calculator app or open a booby-trapped Word document sent via email. That single click is the green light that awakens the virus, allowing it to execute its code and begin looking for new hosts to infect on your system.
It’s important to remember that a virus is just one specific category within the broader world of malware. To understand the full landscape, read our complete guide on what malware is.
2. Virus vs. Worm vs. Trojan
In my years helping people with their computer security, the single biggest point of confusion I encounter is the mix-up between viruses, worms, and trojans. People often use these terms interchangeably, but in the world of cybersecurity, they are as different as a pickpocket, a burglar, and a con artist. They all have malicious goals, but their methods are completely distinct.
To clear this up once and for all, let’s break down their core differences. This table is the most important tool you’ll have for understanding these threats.
| Characteristic | Virus | Worm | Trojan |
|---|---|---|---|
| Self-replicates? | Yes, it makes copies of itself. | Yes, it makes many copies of itself. | No, it cannot replicate on its own. |
| Needs a host file? | Yes (Parasitic). It must attach to a clean file to exist. | No (Independent). It’s a standalone program that can live on its own. | No (Disguised). It is the program; it pretends to be something useful. |
| Spreads via…? | User Action. You have to run the infected file. | Network Vulnerabilities. It spreads automatically across networks, no clicking required. | Deception. It tricks you into downloading and running it yourself. |
To put it simply:
- A virus is a parasite that needs you to give it a ride by opening an infected file.
- A worm is an independent traveler that can spread through a whole network on its own, often without anyone doing anything. I’ve seen a single worm infect an entire office of computers in a matter of hours.
- A trojan is a master of disguise, tricking you into willingly letting it into your home because you think it’s something it’s not.
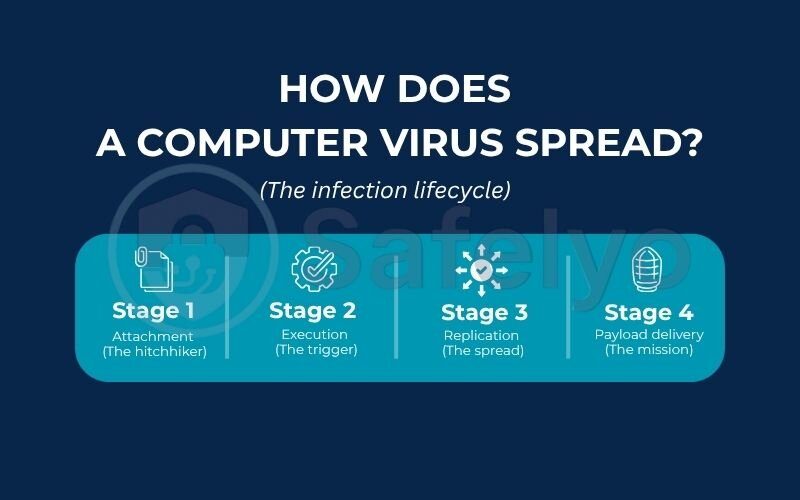
3. How does a computer virus spread? the infection lifecycle
A computer virus doesn’t just magically appear on your system; it follows a predictable, four-stage lifecycle, much like a real-world illness. Understanding this process is key to realizing how a single, seemingly harmless click can lead to a major problem.
Here’s the typical journey of a virus from creation to infection:
Stage 1: Attachment (The hitchhiker)
The virus begins by “hitching a ride” on a clean file. This host can be almost anything you interact with: a program installer (.exe), a Microsoft Word or Excel document (using macros), or even a script on a website. It lies dormant inside this host file, waiting.
Stage 2: Execution (The trigger)
This is the critical moment that depends entirely on you. The virus is triggered when you run the infected program or open the compromised document. For example, you double-click that free game you downloaded or enable macros on a suspicious invoice sent to your email. That simple action is the green light that awakens the virus.
Stage 3: Replication (The spread)
Once awake, the virus’s primary instinct is to survive and multiply. It begins to make copies of itself and searches your computer for other clean files to latch onto. It’s like one bad apple trying to spoil the whole barrel, one by one.
Stage 4: Payload delivery (The mission)
After successfully replicating, the virus proceeds to execute its “payload” – its ultimate, malicious purpose. This is the part you actually notice. A payload can range from being mildly annoying to completely destructive.
At Safelyo, we’ve dealt with cases where a single infected document, opened just once, quietly spread its code to dozens of essential programs. A week later, the payload activated, and the user was faced with constant system crashes and pop-up ads, all stemming from that one initial click. Payloads can include:
- Displaying messages or images on your screen.
- Corrupting or deleting your personal files.
- Stealing passwords and sensitive information.
- Making your computer unusable.
>> Read more:
4. The main types of computer viruses
Just as the biological flu has different strains, computer viruses come in various forms, each designed to attack your system in a unique way. From my experience, knowing the common types helps you understand where the threats might be hiding. Let’s look at the main culprits you should be aware of.
4.1. File infector virus
This is the classic, old-school virus. It works by attaching its code to executable files, which are the files that run programs (commonly ending in .exe or .com). When you launch what you think is a normal program, you’re also launching the virus hidden inside it. Think of it like a mechanic who sabotages a car’s engine; the car looks fine, but the moment you turn the key, the damage begins.

4.2. Macro virus
This is one of the most common threats today because it hides in plain sight. It infects Microsoft Office files (like Word and Excel) by using their built-in macro language. Macros are simple scripts meant to automate tasks, but they can be exploited to run malicious commands. The virus spreads when you open an infected document and click “Enable Content” or “Enable Macros.”

SAFELYO’S EXPERT TIP
Be extremely cautious with any Office file that asks you to “Enable Macros,” especially if you weren’t expecting it. I’ve seen countless infections start this way. If you receive an unexpected invoice or report from a sender, even a trusted one, always verify with them before enabling anything. This is the primary gateway for this type of attack.
4.3. Boot sector virus
This type is a formidable foe that targets the very heart of your computer’s startup process. It infects the Master Boot Record (MBR) on your hard drive, which is the first piece of software your computer reads when it turns on. By controlling the MBR, the virus loads itself into memory before your operating system even has a chance to start. It’s like a thief who changes the locks on your front door, taking control before you can even step inside.

4.4. Polymorphic virus
This is the shapeshifter of the virus world. A polymorphic virus alters its own code every time it replicates. It’s designed to outsmart antivirus programs that rely on “signature-based detection”, which is like looking for a specific fingerprint. Since the virus’s “fingerprint” is always changing, it becomes much harder to catch. Imagine trying to find a criminal who completely changes their appearance after every crime.

4.5. Resident virus
Unlike viruses that activate, infect, and then stop, a resident virus is a permanent lurker. It embeds itself directly into your computer’s memory (RAM). From this vantage point, it can monitor your system’s activity and infect any file you open or program you run. It’s like having a spy hiding in your attic who can interfere with anything happening in the house at any time, making it particularly persistent and difficult to remove.

VIRUS TYPES AT A GLANCE
To make it even clearer, here’s a quick summary of how these viruses differ:
| Virus Type | Primary Target | How it Activates | Key Characteristic |
|---|---|---|---|
| File Infector | Program files (.exe) | When you run the program. | The “Classic” Parasite |
| Macro Virus | Office documents | When you enable macros. | The “Office Sneak” |
| Boot Sector Virus | Hard drive’s boot record | When you start the PC. | The “Startup Hijacker” |
| Polymorphic Virus | Varies (often program files) | Varies by type. | The “Shapeshifter” |
| Resident Virus | Computer Memory (RAM) | Loads into memory and stays active. | The “Permanent Lurker” |
5. How to protect yourself from computer viruses
After learning about how viruses work, you might feel a bit worried. But the good news is that protecting yourself is entirely achievable. In my experience, a strong defense is built on two pillars: smart habits and the right tools. Think of it like driving a car – you need to be a cautious driver, but you also need your seatbelt and airbags.
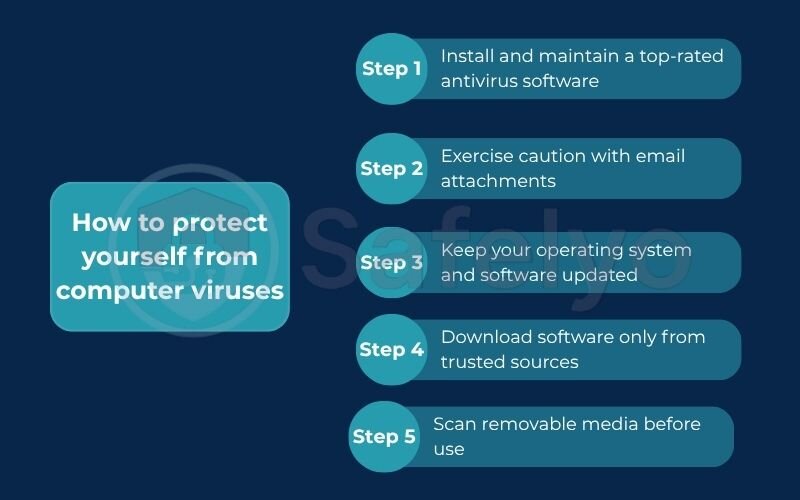
Here are the most effective steps you can take to keep your devices safe:
- Install and maintain a top-rated antivirus software. This is your non-negotiable safety net and the single most important step. A good antivirus program works quietly in the background, actively scanning files you download, emails you receive, and websites you visit. It’s designed to catch and block viruses before they can execute. It’s the digital equivalent of a 24/7 security guard for your computer.
- Exercise caution with email attachments. The golden rule I always tell people is: if you don’t know what it is, don’t open it. Cybercriminals love to disguise viruses in attachments named “Invoice.docx” or “Shipping_Details.pdf”. Even if it seems to be from a trusted source, if it’s unexpected, take a moment to verify with the sender through another channel. This simple habit alone prevents a massive number of infections.
- Keep your operating system and software updated. Those annoying update notifications from Windows, macOS, or your web browser are there for a reason. They often contain critical security patches that fix vulnerabilities discovered by developers. Ignoring them is like leaving a window open in your house. Sooner or later, something unwanted will get in.
- Download software only from trusted sources. The allure of free or “cracked” software can be strong, but these are notorious hiding spots for viruses. Always download applications directly from the official developer’s website or reputable app stores. Getting a program from a shady website is like accepting a free meal from a complete stranger – you have no idea what’s really inside.
- Scan removable media before use. If you plug a USB flash drive or an external hard drive into your computer, especially one that’s been used by others, treat it as potentially contaminated. Most antivirus programs will allow you to right-click the drive and perform a quick scan. It takes just a few seconds and can save you from a world of trouble.
While good habits are essential, the most reliable way to block computer viruses is with a powerful antivirus program. See Safelyo’s expert-tested rankings of the best antivirus software of 2025 to find the ultimate protection.
6. FAQ about computer viruses
We understand there can still be a lot of questions about this topic. Here are quick, direct answers to some of the most common queries we receive at Safelyo.
What is the definition of a computer virus?
The definition of a computer virus is a type of malicious software that, when executed, replicates by inserting copies of its own code into other computer programs, data files, or the boot sector of a hard drive. It requires a host program to function and human interaction to spread.
What is a virus short answer?
A computer virus is a malicious piece of code that acts like a digital parasite: it latches onto a clean file and needs you to run that file to activate and spread itself to other files.
Which definition best describes a computer virus?
The definition that best describes a computer virus highlights its two core traits: 1) it must attach itself to a host program to survive, and 2) it relies on human action (like clicking a file) to spread from one computer to another.
What is a computer virus, and 5 examples?
A: A computer virus is a program that infects other files and spreads when those files are opened. Five famous or common examples include:
1. CIH (Chernobyl): Famous for being able to damage hardware.
2. Melissa Virus: A macro virus that spread rapidly via email attachments in 1999.
3. ILOVEYOU: Spread via email with a “LOVE-LETTER-FOR-YOU.txt.vbs” attachment, causing massive damage.
4. Elk Cloner: One of the very first microcomputer viruses to spread “in the wild.”
5. Sircam: Spread through email, carrying a copy of a random document from the infected user’s computer.
Is a computer virus a type of malware?
Yes, absolutely. A computer virus is a specific type of malware. Malware is the umbrella term for all malicious software, which also includes worms, trojans, ransomware, spyware, and more.
What was the first computer virus?
The “Creeper” program, created in 1971, is often considered the first conceptual virus. However, the “Elk Cloner” for Apple II systems in 1982 was the first to spread “in the wild,” meaning outside of a controlled lab environment.
Can a computer virus damage hardware?
It’s extremely rare for a virus to cause physical damage to hardware. Most viruses target software and data. However, a famous exception was the “CIH” or “Chernobyl” virus from the late 1990s, which could overwrite a computer’s BIOS, effectively rendering the motherboard unusable.
How do I remove a computer virus?
The safest and most effective method is to use a reputable antivirus program. Run a full system scan and allow the software to quarantine or delete the infected files it finds. For severe infections, you may need to run the scan in your computer’s Safe Mode.
7. Conclusion
Understanding what is a computer virus – and just as importantly, what it isn’t – is the first, most powerful step toward building a robust cybersecurity defense. The digital world is filled with confusing terms, but the core principles of protection are straightforward. By moving from uncertainty to clarity, you’ve already made your digital life safer.
Remember these key points:
- A virus is a parasite; it needs a host file and your action to spread.
- Worms spread automatically across networks, while trojans trick you into installing them.
- Prevention through cautious habits and reliable software is always better and easier than dealing with an infection.
Don’t leave your digital safety to chance. By combining smart online behavior with the right security tools, you can confidently navigate the internet without fear. To ensure you have the best defense, let Safelyo guide you. Explore comprehensive reviews in the Antivirus category and choose the ultimate protection for your needs today with Safelyo.













