A proxy server acts as a digital gateway between you and the internet. If you are asking what is a proxy server, the answer is simple. It is an intermediary system that separates end users from the websites they browse. By intercepting requests and forwarding them on your behalf, a proxy can mask your identity, filter content, or bypass regional restrictions.
This guide covers everything you need to know about proxy technology, from how it operates to the different types available for your specific needs.
Key takeaways:
- Definition: A proxy is an intermediary server that masks your IP address and routes internet traffic on your behalf.
- Main functions: It effectively bypasses geo-blocks, filters web content, and can improve speed through caching.
- Proxy vs. VPN: Unlike a VPN, a proxy typically does not encrypt your traffic, making it faster but less secure for sensitive data.
- Types: Common variations include Forward proxies for personal anonymity and Reverse proxies for server load balancing.
1. What is a proxy server?
Proxy servers act as intermediaries between your device and the Internet, forwarding your requests while masking your original IP address. Let’s break down the concept, its evolution, and how it differs from other network tools.
1.1. Proxy server definition
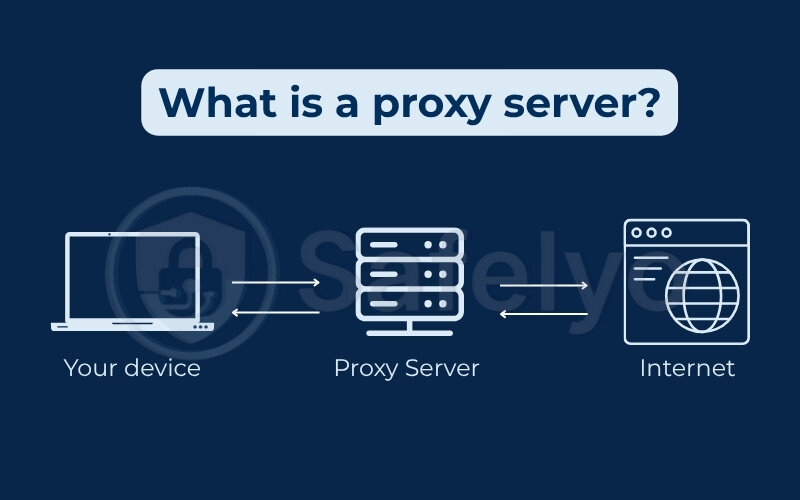
A proxy server is a system or router that acts as a gateway between users and the Internet. It intercepts requests from a client (like a web browser), forwards them to the destination server, and then returns the server’s response back to the client.
In simple terms:
You → Proxy Server → Internet
Internet → Proxy Server → You
This setup allows the proxy to:
- Mask your IP address
- Filter content
- Monitor user activity
- Cache frequently accessed data.
1.2. History and evolution of proxy technology
Proxy servers originated in the early days of the Internet as caching tools to speed up content delivery on corporate networks. In the 1990s, web proxies became popular for shared Internet access and security filtering.
Over time, the technology evolved to include:
- Transparent proxies for content filtering in schools and libraries
- Anonymous and elite proxies for privacy seekers
- Reverse proxies are used by major web platforms for performance and load balancing
- Rotating and residential proxies are adopted by marketers and developers for large-scale data scraping and account management
1.3. Key differences from VPNs and firewalls
While proxies and VPNs both hide your IP address, they differ significantly in functionality:
| Feature | Proxy Server | VPN |
|---|---|---|
| IP masking | Yes | Yes |
| Encryption | No (most types) | Yes (tunnels all traffic) |
| Device-wide coverage | No (app-level) | Yes (system-wide) |
| Speed impact | Typically faster, less secure | Slightly slower, more secure |
| Use case | Bypass filters, anonymity, caching | Privacy, security, encrypted browsing |
Firewalls, on the other hand, are security filters that block or allow specific traffic. They don’t route requests like proxies or encrypt data like VPNs.
According to Norton Cybersecurity, “A proxy server provides a valuable layer of privacy, but it should not be confused with a VPN, which offers stronger encryption and anonymity.”
Next, we’ll explore how a proxy server actually works under the hood and how it handles your data requests.
Read more:
2. How does a proxy server work?
Knowing what is a proxy server also means understanding how it manages traffic and modifies your online requests. Let’s look at how it operates. From routing web requests to masking your identity, proxies follow a clear flow that determines their speed, privacy, and effectiveness.
2.1. The client-proxy-server flow
Here’s how a typical interaction works:
This system creates a buffer layer between you and the Internet. The proxy can modify headers, block certain websites, or replace your IP address before forwarding your request.
- You type a URL or make a request from an app.
- The request goes to the proxy server, not directly to the website.
- The proxy forwards the request to the target server (e.g., a website).
- The target server responds, sending data back to the proxy.
- The proxy returns the data to your browser.
For example, when I needed to test how a client’s e-commerce site appeared in different countries, I used a residential proxy to simulate local traffic from Germany, Japan, and Brazil. The client-proxy-server model lets me “appear” to be in each region, without leaving my desk.
2.2. IP masking and traffic routing
A major reason people use proxies is IP address masking. Your IP address identifies your device and location. A proxy hides your IP and replaces it with its own, shielding your real location from websites, apps, or trackers.
Some proxies even rotate IPs to make traffic appear more organic or anonymous. This is helpful for:
- Avoiding IP bans
- Bypassing geo-restrictions
- Conducting secure competitor research
- Running multiple accounts
I once worked with a digital ad agency that was constantly getting blocked while pulling campaign performance data across multiple regions. Switching to a rotating proxy solved the issue by randomizing their IP footprint with every request.
You may also like these articles:
2.3. Transparent vs. explicit configurations
Not all proxies work the same way. There are two key configuration types:
- Transparent proxy: Intercepts traffic without the user’s knowledge. Often used in schools, workplaces, or ISPs to monitor usage or block content.
- Explicit proxy: Users configure their devices or browsers to route traffic through the proxy. You control when and how it’s used.
Each has its pros and cons. Transparent proxies are simple for admins but may invade privacy. Explicit proxies give users more control, especially for bypassing filters or securing browsing.
When I helped set up a small office proxy environment, we used explicit settings for team members handling sensitive data. It gave them full awareness and let us apply strict security rules through the proxy platform.
Next, we’ll dive into the different types of proxy servers from basic forward proxies to high-security anonymous and rotating variants.
3. Types of proxy servers and how they differ
Once you’ve grasped what is a proxy server, it’s important to explore the many types that exist.
Proxy servers come in many forms, each designed for specific levels of privacy, performance, or use cases. Whether you’re masking your location or balancing web traffic, the type of proxy you choose matters.
3.1. By role: Forward proxy and reverse proxy
Proxy servers can be classified by their network role, either acting on behalf of the client (forward proxy) or the server (reverse proxy).
3.1.1. Forward proxy
A forward proxy sits between the user and the Internet. It processes outbound requests, hides the user’s IP address, and can enforce access rules.
Key functions:
- Hides client identity
- Filters content and blocks websites
- Bypasses geo-restrictions
Use case:
Individuals use forward proxies to browse anonymously or access blocked content. Organizations use them to monitor or restrict employee access.
Example: I once helped a marketing team access region-locked social media tools using a forward proxy, enabling successful campaign testing abroad.
You may be interested in this article: How to browse the web anonymously: A 4-step guide
3.1.2. Reverse proxy
A reverse proxy sits in front of web servers and handles incoming requests. Clients connect to the proxy, which then forwards requests to the appropriate backend server.
Key functions:
- Load balancing
- Hides server identity
- Protects against DDoS attacks
- Handles SSL termination
Use case:
Businesses use reverse proxies to distribute traffic and protect internal infrastructure from direct exposure.
Example: For a client’s e-commerce site, we implemented a reverse proxy to balance traffic between two backend servers, reducing page load times during sales events.
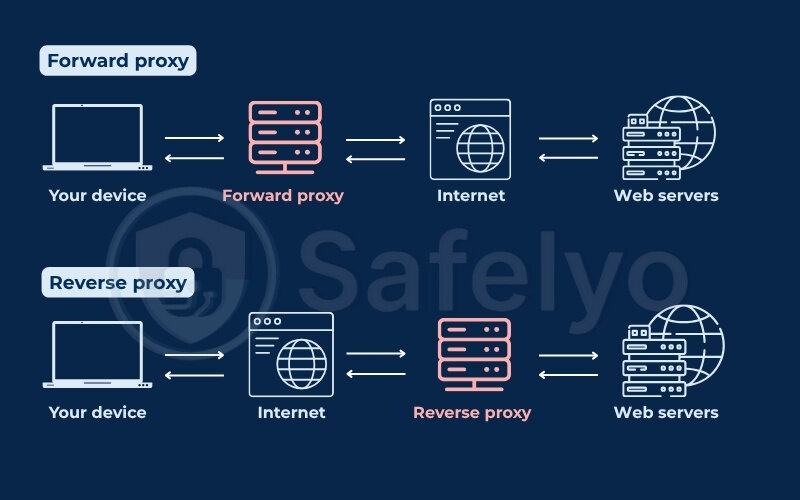
Here’s a quick overview about type of proxy by role:
| Type | Forward Proxy | Reverse Proxy |
|---|---|---|
| Sits between | Client and Internet | Internet and Server |
| Controls | Outbound traffic | Inbound traffic |
| Used by | Individuals, schools, offices | Enterprises, platforms, hosting |
| Purpose | Anonymity, filtering, access | Security, load distribution |
3.2. By anonymity level: Transparent, anonymous, high anonymity, and distorting
Proxy servers offer different levels of privacy based on how much information they reveal to the websites you visit. Some show your real IP address, while others fully hide your identity and even trick the website into thinking you’re in a different location.
3.2.1. Transparent proxy
A transparent proxy does not hide your identity. It passes your real IP address to the website and also tells the website that it’s a proxy.
- How it works:
When you access a website, the request goes through the proxy. But the website can still see who you are and knows you’re using a proxy. - Purpose:
Used by schools, offices, and public Wi-Fi networks to monitor or filter content without needing user permission. - Example:
At a cafe I visited, the free Wi-Fi blocked YouTube and TikTok. That was done using a transparent proxy to filter traffic. - Privacy level: No privacy. Your real IP is exposed.
3.2.2. Anonymous proxy
An anonymous proxy hides your real IP address, so websites can’t see where the request originally came from. However, it does identify itself as a proxy.
- How it works:
The proxy replaces your IP with its own, but tells the website, “This is a proxy server.” - Purpose:
Used when users want basic online privacy, like avoiding tracking cookies or IP-based ads. - Example:
I once used an anonymous proxy to check airline prices from another region without being shown higher prices based on my real location. - Privacy level: Moderate. Your IP is hidden, but the site knows you’re using a proxy.
3.2.3. High anonymity (elite) proxy
A high anonymity proxy, also called an elite proxy, offers the highest level of privacy. It hides your IP and also does not reveal that it’s a proxy.
- How it works:
The proxy fully masks your identity. The target website sees the proxy’s IP and assumes it’s a real user, not a proxy. - Purpose:
Used for maximum anonymity, avoiding IP bans, or accessing sensitive services without being tracked. - Example:
When managing multiple social media accounts for a client, I used elite proxies to avoid getting flagged for suspicious logins from the same IP. - Privacy level: Very high. Most secure and private option.
3.2.4. Distorting proxy
A distorting proxy hides your real IP but intentionally sends a fake IP address to the website. It also reveals itself as a proxy.
- How it works:
The proxy replaces your IP with a false one, often from a different country, and tells the website it’s a proxy. - Purpose:
Used to bypass geo-blocks or trick regional filters. - Example:
I tested a distorting proxy to access a shopping site that offered lower prices to users from specific countries. - Privacy level: Variable. It hides your real IP but is not fully anonymous due to proxy detection.
Here’s a quick overview about type of proxy by anonymity level:
| Proxy Type | Hides Real IP | Reveals It’s a Proxy | Sends Fake IP | Privacy Level | Best For |
|---|---|---|---|---|---|
| Transparent | No | Yes | No | Low | Web filtering in schools, cafes |
| Anonymous | Yes | Yes | No | Moderate | Basic privacy, avoiding IP tracking |
| High anonymity | Yes | No | No | Very high | Secure browsing, managing accounts |
| Distorting | Yes | Yes | Yes | Variable | Geo-spoofing, bypassing restrictions |
3.3. By origin: Residential proxy, datacenter proxy, and public vs. private proxy
Proxies can also be categorized by where the IP address comes from, whether it’s a real home device or a server in a data center. This affects how trustworthy and detectable the proxy is to websites.
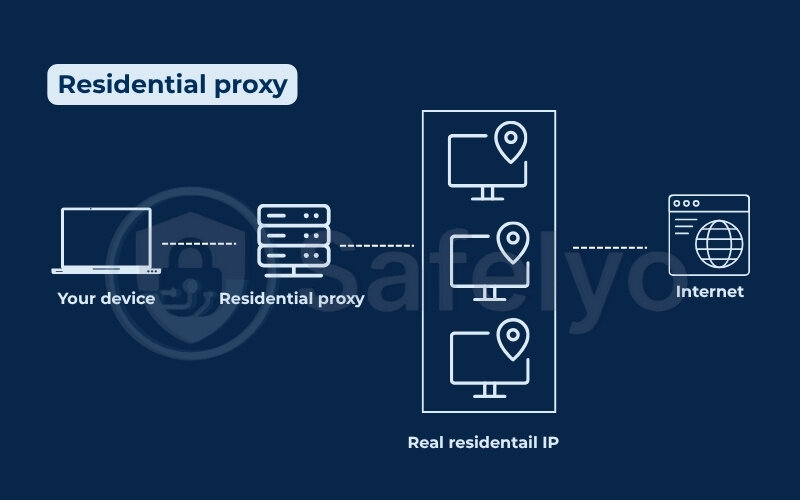
3.3.1. Residential proxy
A residential proxy uses an IP address assigned to a real person’s home by an Internet service provider (ISP). This makes it look like the traffic is coming from a real human user.
- How it works:
When you connect through a residential proxy, your traffic is routed through someone’s actual home Internet connection. - Purpose:
Best for avoiding detection, bypassing anti-bot systems, or accessing geo-restricted content. - Example:
When testing a client’s ad campaigns in different cities, I used residential proxies to see exactly how the ads appeared to real users in each location. - Pros:
Harder to detect and block
Looks like normal user traffic
Good for sneaker bots, ad verification, and scraping - Cons:
Slower speed
More expensive
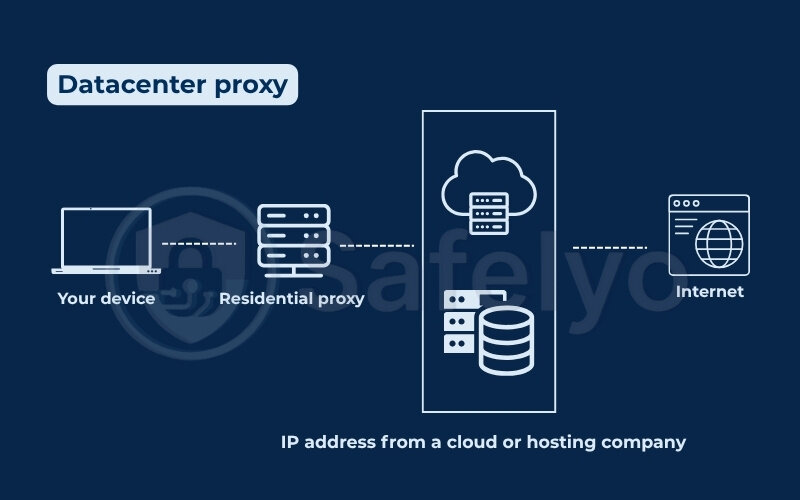
3.3.2. Datacenter proxy
A datacenter proxy uses an IP address from a cloud or hosting company, not from a real home. It’s fast and easy to create, but more likely to be detected by websites.
- How it works:
Your Internet requests go through a virtual machine or server in a data center. - Purpose:
Good for speed, cost savings, and basic tasks like market research or unblocking websites. - Example:
I used datacenter proxies for quick scraping projects that didn’t need high-level anonymity, like checking product prices across marketplaces. - Pros:
Fast speeds
Cheap and scalable
Easy to set up - Cons:
Easier for websites to detect as non-human traffic
Can get banned or blocked on sensitive platforms
3.3.3. Public vs. private proxy
These terms describe who has access to the proxy – everyone, or just you.
Public proxy:
- Open to anyone. Anyone on the Internet can use it.
- Usually free, but often slow and risky.
- Low privacy and security.
Warning: I once tested a public proxy for curiosity. It worked for a few minutes, but injected ads and even tried to redirect me to unsafe sites. I never used one again.
Private proxy:
- Dedicated or semi-dedicated. Only one user or a small group has access.
- Paid and managed by a provider.
- Reliable, fast, and much safer than public options.
For client projects involving account logins, I always use private proxies to avoid data leaks or performance issues.
Here’s a quick overview about types of proxy by origin:
| Type | Real IP Source | Speed | Detection Risk | Best Use Case |
|---|---|---|---|---|
| Residential proxy | Real home user | Slower | Low | Bypassing geo-blocks, ad testing, scraping |
| Datacenter proxy | Cloud server | Fast | Higher | Web scraping, automation, non-sensitive use |
| Public proxy | Any device | Very slow | Very high | Not recommended (too risky) |
| Private proxy | Controlled IP | Fast | Low | Secure browsing, business tools |
3.4. By function: Web proxy, CGI proxy, rotating proxy, DNS proxy, SSL proxy, and SOCKS proxy
Proxies can also be classified based on what specific tasks they perform. Some are designed for browsing websites, others for managing traffic or bypassing firewalls. Here are the main types based on function:
3.4.1. Web proxy
A web proxy is used through a browser, usually by visiting a website that lets you enter a URL to access another site.
- How it works:
You don’t need to install anything. Just go to a web proxy site, type in the address you want to visit, and the proxy fetches the content for you. - Use case:
Useful for quickly accessing blocked websites or browsing anonymously on public computers. - Example:
In college, I used a web proxy to visit Reddit when the school network blocked it. - Limitations:
Often slow, limited to web browsing, and may break page formatting or scripts.
3.4.2. CGI proxy
A CGI (Common Gateway Interface) proxy is a type of web proxy that runs on a website using server-side scripts to fetch and show content.
- How it works:
Similar to a basic web proxy, but uses CGI scripts (like PHP or Perl) to process your requests. - Use case:
Used when you want to hide browsing activity without changing browser or system settings. - Limitations:
Limited performance and compatibility with modern websites.
3.4.3. Rotating proxy
A rotating proxy automatically switches between different IP addresses at set intervals or with each request.
- How it works:
Each connection you make is routed through a different proxy server or IP address, making it harder to track or block you. - Use case:
Ideal for web scraping or managing multiple accounts. - Example:
I used a rotating proxy service to scrape product data from e-commerce sites without triggering rate limits. - Benefit:
Reduces the chance of being detected or banned.
3.4.4. DNS proxy
A DNS proxy intercepts and forwards DNS requests (used to translate website names into IP addresses).
- How it works:
Instead of connecting directly to a DNS server, your request goes through a proxy that can filter or reroute it. - Use case:
Used for content filtering, blocking specific websites, or parental controls. - Example:
I helped a client set up a DNS proxy to block access to social media on company devices. - Limitation:
It only affects domain name resolution, not full traffic routing.
3.4.5. SSL proxy
An SSL proxy decrypts and inspects secure HTTPS traffic between client and server.
- How it works:
It acts as a “man-in-the-middle,” decrypting the encrypted traffic so it can be monitored or filtered before re-encrypting it and sending it to the destination. - Use case:
Common in corporate environments for monitoring or enforcing policies on encrypted traffic. - Privacy warning:
It can inspect sensitive information like passwords, so it must be used carefully and ethically.
3.4.6. SOCKS proxy
A SOCKS (Socket Secure) proxy works at a lower level, handling all kinds of traffic, not just web browsing.
- How it works:
It passes data packets between the client and server regardless of protocol (HTTP, FTP, email, etc.). - Use case:
Great for torrents, gaming, or apps that aren’t just browsing websites. - SOCKS5 version:
Supports authentication and works better with firewalls and modern security protocols. - Example:
I used SOCKS5 proxies with a VPN tool to improve privacy while downloading large files securely.
Here’s a quick overview about type of proxy by function:
| Proxy Type | How It Works | Use Case | Limitations / Notes |
|---|---|---|---|
| Web Proxy | Access sites via a browser-based proxy page. | Bypass blocks on public/shared computers. | Slow, web-only, may break page layout. |
| CGI Proxy | Uses server-side scripts (e.g., PHP) to fetch content. | Private browsing without system changes. | Limited performance, poor compatibility. |
| Rotating Proxy | Switches IPs automatically per request/time. | Web scraping, multi-account management. | Needs reliable service to avoid detection. |
| DNS Proxy | Filters or redirects DNS requests. | Content filtering, parental control. | Affects domains only, not full traffic. |
| SSL Proxy | Decrypts and inspects HTTPS traffic (MITM). | Corporate traffic monitoring. | Privacy risks; use ethically. |
| SOCKS Proxy | Relays all traffic types at lower level (SOCKS5 supports auth). | Torrents, gaming, non-web apps. | No encryption unless paired with VPN. |
4. Common protocols used by proxy servers
Proxy servers rely on specific network protocols to handle, transmit, and secure data between the client and the destination server. Understanding “what is a proxy server” and these protocols helps users choose the right proxy setup for privacy, speed, and compatibility.
4.1. HTTP and HTTPS
HTTP (Hypertext Transfer Protocol) and HTTPS (HTTP Secure) are the most common protocols used by proxies for browsing websites.
- HTTP proxy:
Routes traffic for unencrypted websites. It’s fast but not secure—any data sent can be seen by the proxy or others on the network. - HTTPS proxy:
Handles encrypted traffic by tunneling through an SSL connection. It allows secure browsing without revealing your data to the proxy server. - Use case:
Basic browsing, content filtering, and caching. HTTPS is a must for handling sensitive data like passwords or payment info.
When I first experimented with a proxy for basic content filtering at a client’s small office, I used an HTTP proxy. It worked for general web control, but couldn’t handle secure login pages. Switching to an HTTPS proxy solved the problem and let users browse securely without breaking any sites.
4.2. SOCKS and SOCKS5
SOCKS proxies work at a lower level than HTTP, forwarding all kinds of traffic, not just web browsing. SOCKS5 is an upgraded version with better security.
- SOCKS:
Good for handling data from any protocol (e.g., FTP, email, torrents, apps). - SOCKS5:
Adds support for authentication and UDP (used by gaming and streaming apps), and can bypass firewalls more effectively. - Use case:
Ideal for peer-to-peer sharing, streaming, multiplayer gaming, and accessing restricted networks.
I once needed to download large legal files via a BitTorrent client while connected to a corporate Wi-Fi that restricted P2P traffic. An HTTP proxy didn’t work, but once I configured a SOCKS5 proxy with authentication, the downloads resumed without blocking or throttling.
4.3. SSL/TLS proxies
An SSL/TLS proxy decrypts secure web traffic (HTTPS) for inspection before re-encrypting it and forwarding it.
- How it works:
The proxy acts as a middle layer between the client and server, temporarily decrypting data to allow content filtering or monitoring. - Use case:
Often used in corporate networks to monitor employee activity or enforce data protection rules. - Caution:
Because it involves decrypting secure traffic, it can raise ethical and privacy concerns.
A client asked me to help configure SSL inspection to prevent staff from uploading sensitive files to unauthorized cloud services. We deployed an SSL proxy with controlled trust certificates on employee devices. It flagged multiple file-sharing attempts in the first week.
4.4. Smart DNS and DNS-over-HTTPS
These protocols are used more for bypassing geo-restrictions and improving DNS privacy.
- Smart DNS: Re-routes only the DNS queries related to location-based restrictions, allowing access to geo-blocked services without changing your IP.
- DNS-over-HTTPS (DoH): Encrypts DNS requests, hiding them from ISPs or local networks. It adds a privacy layer by preventing DNS snooping or manipulation.
- Use case: Useful for streaming content from other regions or protecting DNS requests from surveillance.
While traveling, I used Smart DNS to access U.S. Netflix from Europe. It didn’t change my IP, so my banking apps remained unaffected. Later, I enabled DNS-over-HTTPS in my browser to keep my DNS requests hidden from local ISPs at hotels.
5. Benefits of using a proxy server
People often search what is a proxy server because they want to know how it can improve their privacy, access, and performance online. Whether you’re an individual trying to stay anonymous or a business optimizing network performance, proxies provide flexible solutions.
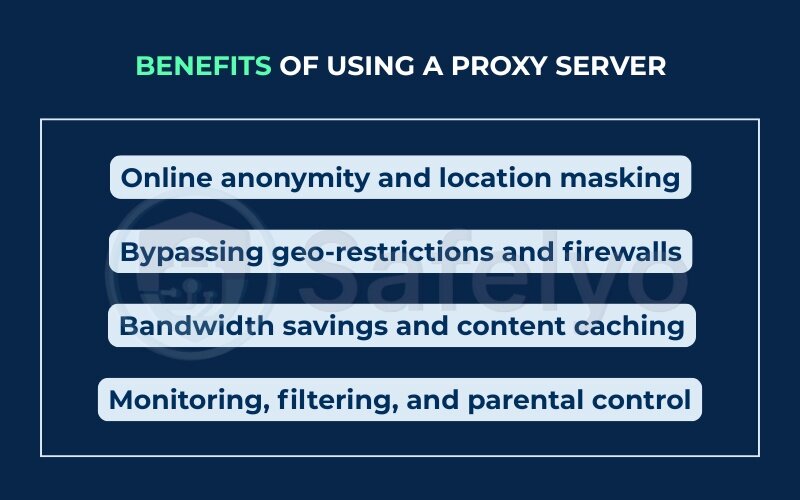
5.1. Online anonymity and location masking
One of the most valuable benefits of using a proxy server is hiding your IP address. When a request is made through a proxy, the destination server sees the proxy’s IP, not yours.
This helps:
- Maintain online anonymity
- Avoid targeted tracking
- Mask your physical location
Case in point: I once had a client who was conducting market research in multiple regions. Using residential proxies with location masking allowed them to view localized search results without traveling or revealing their real IP, an efficient, cost-effective strategy.
5.2. Bypassing geo-restrictions and firewalls
Proxies enable users to access content blocked by geography or network rules. By routing traffic through servers in allowed regions, they help:
- Unblock streaming services (e.g., Netflix, BBC iPlayer)
- Access censored websites in restrictive countries
- Bypass firewalls at schools or workplaces
Expert tip: When traveling to China, I couldn’t access Google services. A rotating proxy helped me bypass the Great Firewall temporarily. However, I combined it with encryption tools for added safety since proxies alone don’t encrypt your traffic.
>> You might also like this related article: Top 5 best VPN for streaming in 2025 (Tested)
5.3. Bandwidth savings and content caching
Proxies, particularly forward proxies, can store copies of frequently accessed content.
Benefits include:
- Reduced bandwidth usage
- Faster load times for repeat requests
- Lower strain on origin servers
Real-world example: I implemented a caching proxy for a nonprofit with a limited Internet connection. Frequently accessed educational materials are loaded instantly after the first visit, drastically improving user experience in low-bandwidth environments.
5.4. Monitoring, filtering, and parental control
Organizations and households use proxies to monitor and control Internet usage:
- Filter inappropriate or harmful content
- Restrict access during specific hours
- Monitor browsing activity for security or compliance
According to CISA, proxy servers are part of broader network perimeter defenses, especially in schools and enterprises where content control is critical.
MY TAKE
A friend of mine set up a proxy at home to block adult content and social media during homework hours. It gave their kids fewer distractions while giving the parents visibility and peace of mind.
6. Risks and limitations of proxy servers
While proxy servers offer notable advantages, they also come with risks and limitations, especially when misconfigured or used without proper security measures.
It’s not enough to know what is a proxy server, you should also be aware of the risks involved in using the wrong kind.
Understanding these drawbacks is crucial for making informed decisions about proxy use.
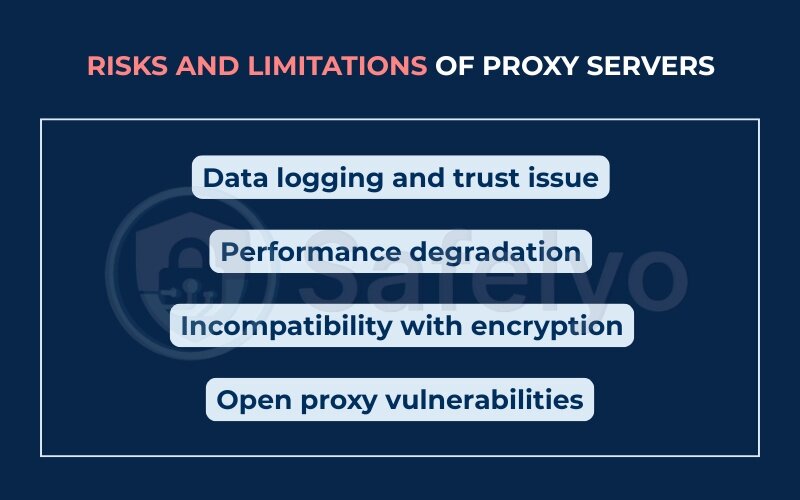
6.1. Data logging and trust issues
Not all proxy servers respect user privacy. Many log user data, including:
- IP addresses
- Browsing activity
- Login credentials (in worst-case scenarios)
Free or public proxies are particularly notorious for unethical logging practices. Some may even sell user data to advertisers or third parties.
As OWASP warns, “Improperly configured or untrusted proxies can intercept and manipulate sensitive traffic, leading to data breaches.”
Lesson learned: I once tested a free proxy to access geo-restricted content. Soon after, my email credentials were compromised. It turned out the proxy was logging login forms—an important reminder to use only trusted, reputable services.
6.2. Performance degradation
Because proxies introduce an extra layer between the client and the destination server, they can slow down your connection. Common causes include:
- Server congestion
- Poor hardware infrastructure
- Long-distance routing
In one project, I implemented a reverse proxy for load balancing but didn’t account for regional server latency. The result? Users in Asia experienced significant lag until we deployed a closer edge server.
6.3. Incompatibility with encryption
Some proxies, especially older or simpler ones like HTTP proxies, cannot handle encrypted traffic. This limits their ability to:
- Secure sensitive communications
- Access HTTPS-only websites
- Support secure apps and APIs
Additionally, SSL interception proxies (used for filtering HTTPS) may break end-to-end encryption if not configured correctly, raising serious privacy and compliance concerns.
6.4. Open proxy vulnerabilities
Open proxies, publicly accessible proxies, pose major security threats:
- They’re often exploited by cybercriminals
- Can be used to launch DDoS attacks
- Rarely offer encryption or user authentication
According to Cybersecurity & Infrastructure Security Agency (CISA), open proxies are frequently blacklisted and should be avoided in any secure network architecture.
PERSONAL ADVICE
A colleague once unknowingly used an open proxy for scraping data. Their IP was flagged, and they were temporarily banned from the target site. Switching to a private, rotating residential proxy resolved the issue and avoided further blocks.
7. Proxy server vs. VPN: What’s the difference?
Proxy servers and VPNs both help mask your IP address and bypass restrictions, but they differ in how they handle traffic, security, and scope.
A proxy server routes traffic from a specific app (like your browser) through an external server. It usually doesn’t encrypt your data. A VPN encrypts all Internet traffic on your device and routes it through a secure tunnel, offering stronger privacy and protection.
Key differences
| Feature | Proxy Server | VPN |
|---|---|---|
| IP masking | Yes | Yes |
| Encryption | No or limited | Full encryption (end-to-end) |
| Scope | Specific apps or browsers | Entire device |
| Speed | Often faster for light tasks | May be slower due to encryption overhead |
| Use cases | Web scraping, geo-testing, filtering | Secure browsing, public Wi-Fi, data safety |
| Privacy protection | Basic | Strong |
Proxies are better for lightweight tasks like bypassing restrictions or managing multiple accounts. VPNs are ideal for securing data, especially on public networks or when handling sensitive information.
>> See also my detailed explanation on this topic: Proxy vs VPN: What’s best for your online privacy?
8. Best practices for using proxy servers securely
Using a proxy server can significantly improve privacy and access, but only if it’s configured and managed properly. Here are the best practices I’ve learned (sometimes the hard way) to stay secure and effective with proxies.
8.1. How to choose a reliable proxy service
When selecting a proxy provider, consider:
- Reputation: Look for trusted vendors with transparent privacy policies
- Server variety: Geographic diversity for geo-testing or access
- Anonymity level: High-anonymity (elite) proxies offer better privacy
- Support and uptime guarantees
Personal insight: I once chose a cheap proxy provider for a time-sensitive scraping project. Their IPs were already blacklisted and unreliable. After switching to a vetted provider offering fresh residential IPs, success rates jumped to 95%.
Tip: Services like Bright Data, Oxylabs, and Smartproxy are often favored by developers and researchers for large-scale tasks.
8.2. Avoiding public/open proxies
Free or open proxies are tempting but dangerous:
- Often lack encryption
- May inject ads or malware
- Could steal credentials or data
According to OWASP, open proxies pose serious security risks and are frequently used for malicious activities.
Best practice: Avoid public proxy lists entirely. Instead, use authenticated, private proxies—even if they come with a cost. Security and stability are worth it.
8.3. Combining proxies with other tools
Proxies are more powerful when combined with other privacy and security layers:
- VPN: Use a VPN and proxy together for added anonymity
- Antivirus and firewall: Protect against local threats and leaks
- Browser isolation: Use dedicated browser profiles or containers per proxy
Real-world scenario: I managed multiple ad accounts using separate proxy-browser pairings through tools like Multilogin. Each profile had its own IP, cookies, and user agent, minimizing cross-contamination and avoiding bans.
8.4. Legal and ethical considerations
Proxies can be misused. Ensure your use is legal and ethical by:
- Following the terms of service of the sites you access
- Avoiding data scraping where prohibited
- Respecting privacy laws (e.g., GDPR, CCPA)
According to the Electronic Frontier Foundation (EFF), proxy use isn’t illegal by default, but how you use it matters, especially if it involves bypassing protections or scraping restricted data.
Personal rule: If I wouldn’t do it with my real IP, I probably shouldn’t do it with a proxy either. That simple rule keeps projects safe and compliant.
>> You may be interested in reading this related article:
9. FAQs about proxy server
Here are clear, direct answers to common questions about proxy servers.
Is a proxy server safe to use?
A proxy server can be safe to use if it comes from a reputable, secure provider that does not log your data. However, free or public proxies often pose risks, such as data theft, malware injection, or session hijacking. For safety, it’s best to use a paid proxy service with strong security policies and HTTPS support.
Do proxies hide your IP address?
Yes, proxies are designed to mask your real IP address. When you connect through a proxy, websites and online services only see the proxy server’s IP, not your own. This helps protect your location and browsing identity from being tracked by third parties.
Can proxies access blocked websites?
Proxies are commonly used to bypass geo-restrictions and local firewalls. By routing traffic through servers in allowed regions, a proxy can help users access content that is otherwise unavailable in their location. However, some advanced websites may detect and block proxy traffic, especially from free or poorly configured proxies.
How is a proxy different from a VPN?
The main difference is in encryption and coverage. A proxy only reroutes traffic from specific apps or browsers and may not encrypt the data.
A VPN, on the other hand, encrypts all network traffic at the system level, offering greater security and privacy. While proxies are generally faster and more flexible for specific use cases like scraping or accessing restricted content, VPNs are preferred for secure, private browsing.
Are proxy servers legal to use?
Yes, proxy servers are legal in most countries when used for legitimate purposes such as content filtering, privacy protection, or business applications.
However, using proxies to perform illegal activities, like unauthorized data scraping, bypassing bans, or accessing copyrighted content, can still lead to legal consequences. Always follow local laws and the terms of service of the websites you visit.
10. Conclusion
Understanding “what is a proxy server” is key to navigating the modern Internet safely and efficiently.
Proxy servers play a crucial role in online privacy, access control, and network efficiency. This article explained what a proxy server is, how it works, and the different types available based on role, anonymity, origin, and function.
We’ve seen how proxies can:
- Mask IP addresses for anonymity
- Bypass geo-blocks and firewalls
- Cache content to save bandwidth
- Filter and monitor Internet traffic
At the same time, using proxies involves risks like data logging, reduced performance, and weak encryption, especially with free or poorly managed services.
When I first encountered the term “proxy server,” I assumed it was just another name for a VPN. But after struggling to access region-locked tools while working abroad, I dug deeper. That shift in understanding saved time, improved performance, and gave me more control online.
While proxies differ from VPNs in encryption and scope, both have unique use cases. Choosing the right tool depends on your specific needs for privacy, speed, or access.
When used responsibly, proxy servers are powerful tools for both individuals and businesses seeking greater control over their online activity.
Want to learn more about protecting your digital life? Explore our Privacy & Security Basics section at Safelyo for in-depth guides, expert tips, and beginner-friendly resources to help you stay safe online.













