So, what is a worm virus? Think of it as a standalone digital pest that doesn’t need to hitch a ride on another program. It’s a unique type of malware designed to tunnel through networks all by itself, replicating and spreading from one computer to another without a single click from you.
In the world of cybersecurity, the terms virus, worm, and Trojan are often thrown around interchangeably, creating a fog of confusion. However, knowing the difference isn’t just for tech experts; it’s a critical piece of knowledge for anyone who wants to stay safe online. A worm’s defining feature – its autonomy – makes it uniquely dangerous.
Having analyzed countless malware incidents over my career, I’ve seen firsthand how a single worm can bring down an entire corporate network in a matter of hours. Its ability to exploit one small vulnerability and multiply exponentially is what makes it such a formidable threat.
In this simple guide, you’ll discover:
- What a computer worm is and how its core components work.
- The clear differences that separate it from a virus and a Trojan.
- How worms spread and the real-world damage they’ve caused.
- The essential steps to protect your devices from this sneaky threat.
Don’t wait for your system to slow to a crawl. Let me arm you with the knowledge to recognize and defend against one of cybersecurity’s most persistent invaders.
1. What is a worm virus?
In my experience helping people clean up their infected devices, I’ve noticed the word ‘virus’ is often used as a catch-all term for any digital nasty. But I always take a moment to clarify that a computer worm is a distinct and often more dangerous threat for one key reason: its autonomy.
At its heart, a computer worm is a standalone piece of self-replicating malware that spreads through computer networks without any human help. Think of it like this: if a virus is a parasite that needs to attach to a host (like a flu virus latching onto a cell), a worm is like an earthworm tunneling through the soil all by itself. It doesn’t need to be carried; it actively moves from one place to another.
This definition hinges on two unique characteristics:
- It’s self-replicating: A worm is programmed to make endless copies of itself.
- It’s independent: This is the game-changer. Unlike a virus that must piggyback on a legitimate file (like an .exe program or a Word document) and wait for you to open it, a worm travels across networks on its own, actively looking for its next victim.
To understand how a worm achieves this, it’s helpful to know that it’s essentially built from two critical parts: the propagation engine and the payload.
The propagation engine is the worm’s legs and navigation system. Its only job is to spread. It constantly scans the network searching for security loopholes, like an unpatched operating system. Once it finds an opening, it uses that doorway to copy itself onto the new machine.
The payload is the malicious cargo the worm delivers after a successful infection. The damage can vary wildly. Some payloads simply slow down the network by consuming bandwidth, while others are far more destructive – deleting files, installing a “backdoor” for hackers, or even delivering another piece of malware like the ransomware deployed by the infamous WannaCry worm.
At Safelyo, we’ve observed that the greatest danger of modern worms isn’t just the initial infection. It’s their self-replication capability that can turn thousands of computers into a botnet army in mere hours, ready to be used for massive DDoS attacks or to spread ransomware. This is why keeping your systems patched isn’t an option – it’s an absolute necessity.
2. Worm vs. Virus vs. Trojan: understanding the key differences
This is probably the number one point of confusion I encounter, and for good reason. These terms are often used so loosely that they lose their meaning. But understanding their differences is crucial because they each require a slightly different mindset to defend against.
Let’s break it down in the simplest way possible. First, a quick cheat sheet, and then we’ll dive into the details.
| Feature | Worm: The Independent Traveler | Virus: The Parasite | Trojan: The Deceptive Gift |
|---|---|---|---|
| How it Spreads | Automatically, through network vulnerabilities. | Requires a user to run an infected file. | Tricks a user into installing it. |
| Needs a Host File? | No. It’s a standalone program. | Yes. It must attach to a file (e.g., .exe, .doc). | No. It disguises itself as the program. |
| Primary Goal | Replicate and spread to as many machines as possible. | Infect files and replicate when the host file is run. | Open a “backdoor” for attackers or deliver a payload. |
2.1. The virus: the parasite
Think of a computer virus exactly like the biological flu virus. It cannot exist or spread on its own; it needs a host cell. In the digital world, that “host cell” is a legitimate file or program, like a document, a spreadsheet, or an application’s executable file (.exe).
The virus injects its malicious code into this host file and then lies dormant. It does absolutely nothing until you, the user, execute that file. When you double-click that infected invoice from a strange email, you’re not just opening the invoice; you’re activating the virus, allowing it to replicate and infect other files on your system.
2.2. The worm: the independent traveler
As we’ve covered, a worm is the complete opposite. It doesn’t need a ride. It’s a self-contained traveler that moves under its own power.
So, to answer the common question, is a worm a virus? The answer is a definitive no. The key difference is that a worm exploits network vulnerabilities to spread automatically. Imagine an entire office gets infected just because one person’s computer was running an outdated version of Windows. The worm found that vulnerability, let itself in, and then used that computer as a launchpad to scan the office Wi-Fi and jump to every other vulnerable machine – all without a single person clicking anything.
2.3. The Trojan: the deceptive gift
If a virus is a parasite and a worm is a traveler, then a Trojan is a spy in disguise. Its name comes from the ancient Greek story of the Trojan Horse, and it works exactly the same way.
A Trojan masquerades as something desirable and legitimate – a free game, a useful utility, or a movie file. The trick is that you willingly let it in, believing it’s something you want. Once you install or run the program, the “wooden horse” opens its doors, and the malicious payload gets to work. Unlike a virus or a worm, a Trojan’s primary goal isn’t to replicate. Its job is to create a secret backdoor into your system, allowing attackers to steal your passwords, spy on you, or use your computer for other nefarious purposes.
Read more:
3. How do computer worms spread?
One of the most common questions I get is, “If I didn’t click anything, how did I get infected?” The answer lies in the multiple, clever pathways worms use to travel. Understanding how computer worms spread is the key to building an effective defense. They are masters of infiltration, typically using one of these three routes.
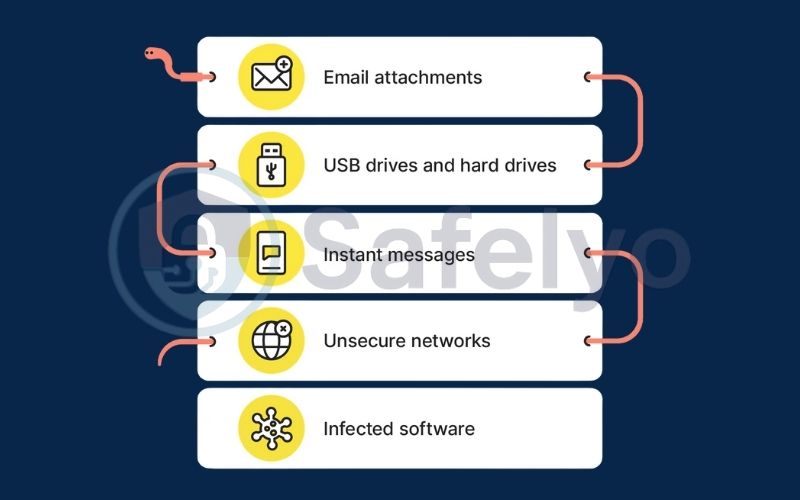
3.1. Through network vulnerabilities
This is the classic and most dangerous method. Imagine every software program and operating system on your computer has thousands of doors and windows. When developers discover a weak lock on one of them, they release a security patch – an update – to fix it.
A worm is designed to do one thing: scour the network and jiggle the handle on every single door and window it can find. If it finds a computer that hasn’t installed the latest security patch, it’s found an unlocked digital door. It lets itself in, infects the system, and immediately starts using that computer to look for more unlocked doors on other machines.
- Real-world Example: This is exactly how the WannaCry worm caused global chaos in 2017. It exploited a specific vulnerability in Microsoft Windows called “EternalBlue.” It didn’t need an email or a click. It simply found vulnerable computers connected to the internet, forced its way in, and unleashed its ransomware payload. I remember watching reports of entire hospital systems in the UK being shut down, all because of one unpatched vulnerability.
3.2. Via email and instant messaging
This method weaponizes our own social connections. A worm can arrive as an email attachment or a link in a message, often from someone you know and trust whose account has already been compromised.
But here’s the worm’s clever twist: once you open the malicious file, it doesn’t just infect your machine. Its propagation engine immediately accesses your email address book or contact list and sends a copy of itself to everyone you know. It’s like a self-sending chain letter from hell.
REAL-WORLD EXAMPLE:
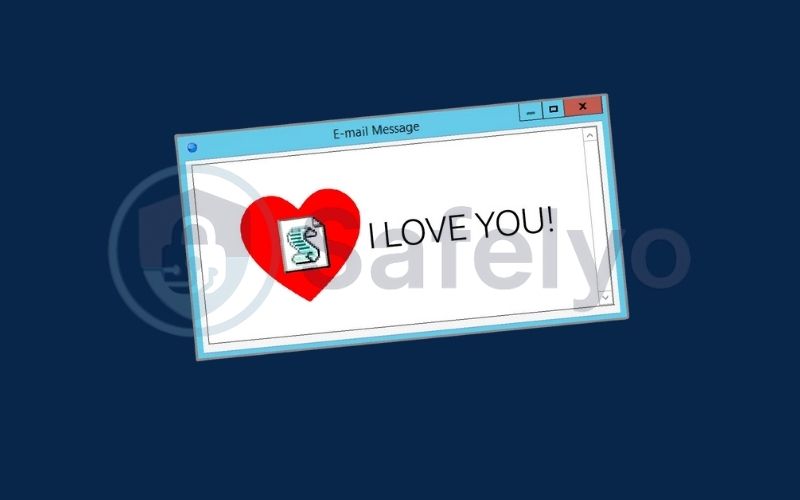
The ILOVEYOU worm from 2000 is the most famous case. It spread via an email with the subject line “ILOVEYOU” and an attachment named LOVE-LETTER-FOR-YOU.txt.vbs. The human curiosity was too much to resist. Once opened, it overwrote files on the victim’s computer and mailed itself to their entire Microsoft Outlook contact list, causing an estimated $10 billion in damages.
3.3. Through shared media
While it feels a bit old-school, this method is still surprisingly effective, especially in corporate or academic environments. Worms can copy themselves onto removable storage devices like USB flash drives, external hard drives, or memory cards.
When you plug an infected USB drive into a clean computer, the worm can automatically execute and infect the new machine. From that point on, any new USB drive you plug into that now-infected computer will also become a carrier. I’ve seen this happen in office settings where one employee’s personal USB stick ended up infecting an entire department’s computers in a single afternoon.
REAL-WORLD EXAMPLE:
The highly sophisticated Stuxnet worm, discovered in 2010, famously used this method as one of its key infection vectors to reach air-gapped (not connected to the internet) systems in an Iranian nuclear facility. It proves that even physically isolated systems aren’t safe from a worm that can travel on a portable drive.
4. The real-world impact: Famous computer worms in history
To truly understand the power of a worm, you have to look at the moments they brought the digital world to its knees. These aren’t just abstract threats; they are historical events that shaped the cybersecurity landscape we live in today. I’ve studied these cases for years, and they serve as powerful lessons.
Let’s look at a few famous computer worms that show just how destructive self-spreading malware can be.
4.1. The Morris worm (1988): the accidental catastrophe
This is the grandfather of all computer worms. Back when the internet was a small, academic community, a Cornell graduate student named Robert Morris created a worm, not to cause damage, but as an intellectual experiment to see how big the internet was.

However, a small error in its code made the worm far more aggressive than intended. Instead of spreading slowly, it began to replicate uncontrollably, infecting machines multiple times, consuming their processing power until they crashed. It was the first-ever denial-of-service attack caused by malware, paralyzing an estimated 10% of the entire internet at the time. The Morris Worm was a massive wake-up call, proving that even an accidental piece of self-replicating code could become a catastrophic threat.
4.2. The ILOVEYOU worm (2000): weaponizing human curiosity
Many of us remember this one. At the turn of the millennium, millions of people received an email with a simple, irresistible subject line: “ILOVEYOU.” It came with an attachment that looked like a text file: LOVE-LETTER-FOR-YOU.txt.
The temptation was too much for many. The file was actually a malicious script. Once opened, the worm overwrote critical files on the victim’s computer (including music and images) and, most devastatingly, it immediately emailed itself to every single contact in the user’s Microsoft Outlook address book. It spread like wildfire, infecting over 10 million computers worldwide and causing an estimated $10 billion in damages. ILOVEYOU taught us a hard lesson: the weakest link in cybersecurity is often the human behind the keyboard.
4.3. The WannaCry worm (2017): the ransomware hybrid
If the first two feel like ancient history, WannaCry is a much more recent and chilling reminder of a worm’s power. What made WannaCry so terrifying was that it was a hybrid threat. It combined the self-spreading, network-hopping ability of a worm with the data-encrypting payload of ransomware.
Here’s how it worked:
- The worm part exploited the EternalBlue vulnerability in Windows to spread rapidly across networks, infecting machine after machine without a single click.
- Once on a system, the ransomware payload activated, locking up all the user’s files and displaying a ransom note demanding payment in Bitcoin.

It didn’t just affect home computers; it crippled critical infrastructure, most notably the UK’s National Health Service (NHS), forcing hospitals to cancel thousands of appointments and surgeries. From personal experience in the security field, I can tell you that the day WannaCry hit was pure chaos. It was a stark demonstration that failing to perform one simple action – keeping your software updated – could have devastating, real-world consequences.
Understood. This next section is all about empowering the user with practical, easy-to-spot signs of an infection, backed by relatable experiences.
5. How to tell if you have a computer worm
Because a worm can infect your system without you doing anything, it can be tricky to detect. Unlike loud ransomware that announces its presence immediately, some worms try to stay quiet while they use your computer’s resources to spread. However, they almost always leave behind telltale clues.

Over the years, I’ve helped countless users diagnose mysterious system problems that turned out to be a worm infection. If you suddenly start noticing any of these signs of a worm infection, it’s time to be suspicious.
- Your computer is suddenly very slow or crashes.
This is the most common symptom. If your computer suddenly feels like it’s wading through mud, or it freezes and crashes for no apparent reason, it could be a worm hogging your CPU and memory to replicate and scan the network. If you suddenly notice your internet connection slowing to a crawl while your computer’s fan is spinning like crazy, it could be a sign that a worm is using your resources to spread itself.
- Your hard drive space is disappearing.
You haven’t downloaded any big files, but you notice your free storage space is shrinking rapidly. This is a classic sign of a worm making thousands of copies of itself, filling up your drive in the process.
- You find strange files, folders, or new icons on your desktop.
Worms can sometimes create new files or modify existing ones. If you see unfamiliar items appearing out of nowhere, or if some of your personal files have vanished, a worm could be the culprit.
- Your security software or firewall sends alerts.
Modern antivirus and firewall programs are pretty good at detecting suspicious outgoing network traffic. If you get a warning that an unknown program is trying to connect to the internet, don’t ignore it. It might be a worm attempting to phone home or spread to a new victim.
- Friends or colleagues are getting strange emails from you.
This is a dead giveaway for an email worm. If a friend messages you saying, “Hey, what was that weird link you just sent me?” and you have no idea what they’re talking about, your machine is likely compromised and is being used to spread the infection further. This is one of the most embarrassing symptoms for users, and often the one that finally prompts them to seek help.
6. How to remove and prevent computer worms
Now for the most important part: what you can actually do about it. When it comes to worms, an ounce of prevention is worth a ton of cure. It’s infinitely easier to lock the door than to evict a pest that has already moved in.
6.1. Prevention: Your first line of defense
I always tell my clients that good cybersecurity is about building strong habits. Preventing worms doesn’t require you to be a tech genius; it just requires a bit of vigilance.
- Keep everything updated.
This is non-negotiable. As we saw with WannaCry, worms thrive on unpatched vulnerabilities. Enable automatic updates for your operating system (Windows, macOS) and your web browser. This single action closes the doors that worms are constantly trying to open.
- Use a powerful antivirus and a firewall.
A modern antivirus solution is your active security guard. It’s designed to recognize and block malware before it can execute. A firewall acts as a gatekeeper for your network, monitoring all incoming and outgoing traffic and blocking suspicious connections. Think of it as a bouncer for your computer.
- Be skeptical of emails and links.
The ILOVEYOU worm proved how effective social engineering is. Treat every unsolicited email attachment and link with suspicion, even if it appears to come from someone you know. If an email from a friend feels off or contains a generic message like “Check out this cool link!”, it’s always best to verify with them through another channel (like a text message) before clicking.

>> Unsure which antivirus is right for you? Check out Safelyo’s review of the best antivirus software of [current year] to find a reliable security guard for your devices.
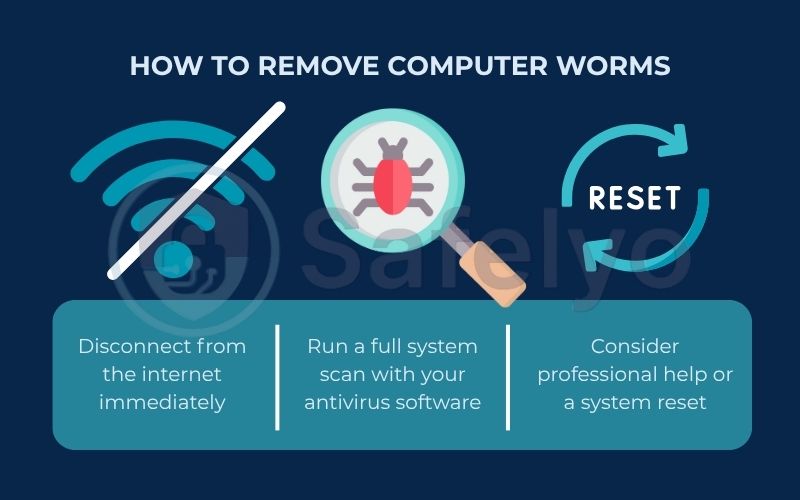
6.2. Removal: If you’re already infected
If you suspect a worm has already made its way onto your system, the immediate goal is to contain the threat and then eliminate it.
- Disconnect from the internet immediately.
This is the first and most critical step. Unplug the network cable or turn off your Wi-Fi. This cuts the worm off from the outside world, preventing it from spreading to other computers on your network or communicating with its creator.
- Run a full system scan with your antivirus software.
Make sure your antivirus software is fully updated (you might need to briefly reconnect to the internet just to get the latest definitions, then disconnect again). Perform a “full” or “deep” scan, not a quick one. This will check every file on your system. Follow the software’s instructions to quarantine or remove any threats it finds.
- Consider professional help or a system reset.
For some aggressive worms, an antivirus scan might not be enough. If the problems persist, you might need professional help. In the most severe cases, the only way to be 100% certain the worm is gone is to back up your essential data (photos, documents) to a clean external drive, and then completely wipe your hard drive and reinstall your operating system. It sounds drastic, but sometimes it’s the only way to ensure a clean slate.
See also:
7. FAQ about the worm virus
Let’s tackle some of the most common questions I hear about computer worms. Here are quick, straightforward answers to help you stay informed and clear up any lingering confusion.
What is the worm virus?
A “worm virus” is a common but technically inaccurate term. A computer worm is a standalone type of malware that replicates itself and spreads across computer networks automatically, without needing to attach to a host file or program.
Is a worm a virus?
No. While both are malware, the key difference is that a virus needs to attach itself to a program to spread and requires a human to run that program. A worm is a standalone program that can travel and replicate on its own across networks.
What are the symptoms of a worm virus?
The most common symptoms include your computer running unusually slow, a sudden decrease in hard drive space, strange new files appearing, high network activity even when you’re not doing anything, and friends receiving emails from you that you never sent.
What is a real-world example of a worm virus?
A perfect example is the WannaCry worm from 2017. It spread rapidly across the globe by exploiting a Windows vulnerability. Once inside a system, its payload – a piece of ransomware – would encrypt the user’s files and demand a payment.
What does a computer worm do after infecting a system?
A worm’s “payload” can do many things. It can consume network bandwidth, delete files, install a backdoor for hackers to gain access, or deliver other malware like ransomware. Its primary function, however, is always to find and spread to as many new systems as possible.
Can a worm steal my personal information?
Yes, absolutely. Many worms are designed with a payload that can steal sensitive data. This can include login credentials for your bank, financial information, or personal files, which are then sent back to the attacker.
Can you remove worm viruses?
Yes, worms can be removed. The first steps are to disconnect the infected computer from the internet to stop it from spreading, then run a full system scan with an updated, reputable antivirus program. In severe cases, a full system reset may be necessary.
Are computer worms still a threat today?
Definitely. Modern worms are often more sophisticated, combining with other threats like ransomware (as seen with WannaCry) or being used in highly targeted espionage attacks. This is why keeping your systems and software updated is more crucial than ever.
8. Conclusion
Understanding what is a computer worm – a self-sufficient, network-traveling pest – is the first and most powerful step toward building a solid digital defense. Unlike other malware that often relies on you making a mistake, a worm actively seeks out and exploits weaknesses on its own, making it a uniquely proactive threat.
To protect yourself, always remember these key points:
- Worms are self-replicating malware that spread independently across networks.
- They are fundamentally different from viruses, which require a host program to spread.
- Prevention through regular software updates and a reliable antivirus is your best and most effective strategy.
In my years of experience, I’ve seen that the most damaging attacks are often the ones people thought could never happen to them. Don’t underestimate the power of a threat that can spread by itself. Stay informed, stay protected, and continue building your cybersecurity knowledge by exploring more topics in Safelyo‘s Antivirus section to become an even smarter, safer internet user today.













