Imagine this: You’re reading the news on a major website you trust and visit every day. You don’t click on a single ad. Suddenly, your computer locks up with a ransomware demand. How could that possibly happen? Welcome to the sneaky world of malvertising – one of the most sophisticated cybersecurity threats online today.
In this guide, we will explain what is malvertising in simple terms. We will cover how it works and the key differences between malvertising and adware. Most importantly, we will provide a clear checklist to help you stay safe. Join me as I pull back the curtain on these malicious ads.
Short on time? Here’s the bottom line on malvertising. These attacks exploit the massive reach of online advertising, making harmful code appear inside ads you normally trust. It’s a cyberattack where hackers use legitimate online ads to infect your devices, often without a single click from you.
- What is malvertising? It’s a cyberattack where hackers hide malware inside legitimate-looking ads. This hidden code often includes forms of malicious software designed to activate the moment the ad is displayed. In many cases, these ads secretly deliver malicious software designed to infiltrate your device without being noticed. These dangerous ads are then placed on trusted, popular websites you visit every day, abusing your trust to infect you.
- Infection can happen without a click. This means no user action is required at all for the attack to succeed. The most dangerous computer virus uses a “drive-by download” to install malware on your device the moment the ad loads on your screen. You don’t have to interact with it at all. These silent drive-by downloads remain one of the most dangerous forms of malware attacks.
- It’s different from adware. Think of malvertising as the attack method—it’s like the syringe that delivers the payload. On the other hand, adware is a type of malware that gets installed and resides on your computer, similar to a disease.
- A layered defense is the best protection. The most effective way to prevent malvertising is by using a combination of three key tools: an ad blocker, keeping your browser constantly updated, and running a strong antivirus program.
1. What is malvertising?
Let’s break down the term itself. Malvertising is a simple combination of two words: “malicious” and “advertising.” At its core, it is the use of legitimate online advertising networks to deliver malware to an unsuspecting user’s computer.
The easiest way to understand this is to think of the classic Trojan Horse story. Modern cybercriminals rely on this exact tactic, disguising dangerous payloads inside harmless-looking ad creatives.
In this scenario, hackers are the Greek soldiers. They create a digital “horse” – an ad that looks completely normal and harmless. But hidden inside this ad is their army: Malicious code (malware). They then pay to have this ad placed on a legitimate, trusted ad network, just like any other company would.
That ad network, unaware of the hidden danger, then distributes the ad. It places the “horse” right in front of your city gates – on the major news outlets, recipe blogs, and popular websites you visit and trust every day.
What makes the malvertising definition so insidious is that it abuses your trust. From my experience analyzing these attacks, this is the most dangerous part. You aren’t visiting a shady website or downloading a pirated file. You are on a legitimate site you know and love, but the threat is injected into that safe environment through a channel that is supposed to be trustworthy.
2. Malvertising vs. adware
This is easily the biggest point of confusion when talking about malicious ads, so let’s clear it up right now. While they sound similar and are related, malvertising and adware are not the same thing. In my experience, understanding this difference is key to understanding the threat.
Think of malvertising as the delivery method. It’s the action of using a legitimate ad on a trusted website to transport a malicious payload to your computer.
On the other hand, adware is a specific type of malware. It’s the actual unwanted program that gets installed on your device. Its primary job is to bombard you with pop-ups, banners, and other annoying ads, often while tracking your browsing habits. Some adware strains also generate endless spam messages, overwhelming users with unwanted content. This constant tracking can seriously undermine your user privacy. In some cases, adware is also used to commit click fraud, generating revenue for attackers.
Here’s the best analogy I’ve found to make the difference stick: Malvertising is the contaminated syringe; adware is the disease you get from it. The malicious ad (the syringe) injects the malware into your system and is then gone. The adware (the disease) is what’s left behind, persistently living on your computer and causing symptoms.
To make the malvertising vs adware distinction even clearer, here’s a direct comparison:
| Feature | Malvertising | Adware |
| Nature | A method to deliver malware | A type of malware |
| Location | Lives on legitimate websites (temporarily) | Lives on your computer (persistently) |
| Goal | To infect your device with malware (ransomware, spyware, etc.) | To show you unwanted ads and track you |
| Analogy | A contaminated syringe | The disease you get from the syringe |
3. How does a malvertising attack work?
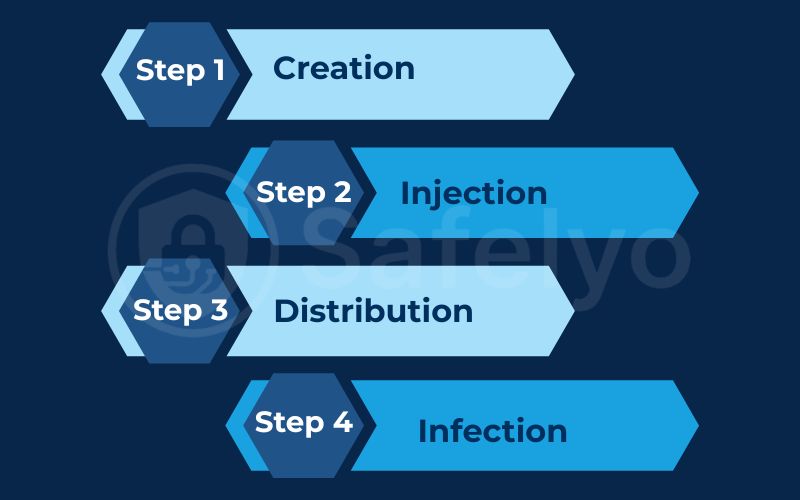
Understanding the mechanism of an attack can be complex, but in my experience, it’s best to think of it as a four-step supply chain. Here is how does malvertising work in simple terms:
- Step 1: Creation. A hacker creates an advertisement. It might look like a normal banner for a shoe sale, or it could be just a tiny, invisible pixel. Hidden inside the image file or the ad’s underlying code is a malicious script.
- Step 2: Injection. The hacker pretends to be a legitimate advertiser and submits this ad to a major advertising network. They pay for it just like a real business would, ensuring it gets into the legitimate distribution cycle.
- Step 3: Distribution. The ad network automatically accepts the ad (sometimes their checks aren’t thorough enough) and pushes it out to thousands of reputable publisher websites. The website owners usually have no idea it’s there.
- Step 4: Infection. You visit one of these trusted sites. Your browser loads the page, including the malicious ad. At this point, one of two things happens:
- Click-based: The ad tricks you into clicking it with a fake alert (“Your computer is infected!”), redirecting you to a malicious site. This often triggers a redirection to a website controlled by attackers
- Drive-by download (the scariest one): You don’t click anything. Just loading the page is enough. The ad silently activates an exploit kit – a tool that scans your browser for vulnerabilities (like an outdated plugin) and forces a malware download in the background. In many cases, this silent process involves multiple hidden redirection steps that route your browser through attacker-controlled servers before the malware is delivered.
I’ve investigated incidents where victims swore they didn’t touch anything, and they were right. They were victims of a drive-by download, which is what makes malvertising so uniquely dangerous.
4. Real-world malvertising examples
To understand that malvertising isn’t just a theoretical threat, it helps to look at a few high-profile cases. These incidents prove that even the most reputable corners of the internet can be used as a delivery vehicle for malware. For many victims, the result was a rapid infection that happened before they even realized an unsafe ad had loaded.
The New York Times & BBC (2016)
This was a landmark case that brought malvertising into the mainstream spotlight. A sophisticated group of hackers managed to place malicious ads on the websites of major news outlets, including The New York Times, BBC, and AOL. When users visited these sites, the ads would attempt to infect their computers with a notorious piece of ransomware known as CryptoWall. This malvertising example was a wake-up call for many.
Spotify (2016)
It’s not just news websites. Users of Spotify’s free desktop version were targeted in a campaign where malicious ads would automatically open malware-hosting websites in their browsers, even without a click. These ransomware ads exploited the ad network that served promotions to free-tier listeners.
As a security analyst, these examples show that no website is too big or too trusted to be a potential victim of a malvertising campaign. The issue isn’t with the websites themselves, but with the complex, automated ad networks they rely on. This entire digital advertising chain can be compromised when just one malicious advertiser slips through. Your trust in the website, unfortunately, doesn’t always extend to the ads it displays.
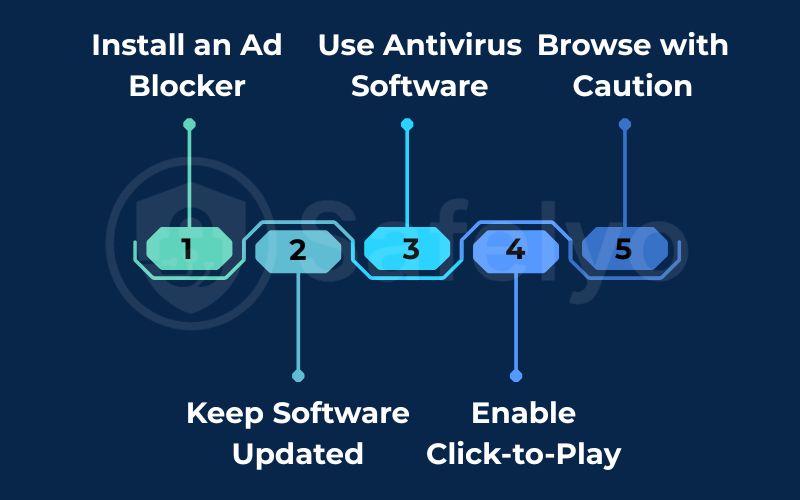
5. How to prevent malvertising: A simple 5-step checklist
The good news is that while malvertising is sneaky, defending against it is straightforward. Effective malvertising protection relies on a layered defense strategy. Here’s a quick overview of the most effective steps you can take today.
| Action | Why does it work against malvertising |
| 1. Install an Ad Blocker | Prevents malicious ads from loading in the first place. |
| 2. Keep Software Updated | Patches security holes that “drive-by download” attacks exploit. |
| 3. Use Antivirus Software | Acts as a safety net to detect and block malware if an ad gets through. |
| 4. Enable Click-to-Play | Stops vulnerable browser plugins from running automatically. |
| 5. Browse with Caution | Your own judgment can spot suspicious ads that automated filters miss. |
Now, let’s explore why each of these steps is a critical part of your defense. Strengthening your digital security reduces the chances of malicious ads ever reaching your device.
1. Use a reputable ad blocker
High-quality ad-blockers can stop these malicious ads before they ever load on your screen. This is your first and most effective line of defense. It’s simple logic: if a malicious ad cannot be loaded, it cannot harm you.
An ad blocker works by preventing your browser from communicating with ad servers in the first place, effectively cutting off the malvertising delivery chain before it starts. From my experience, this single tool stops the vast majority of malvertising attempts dead in their tracks.
2. Keep everything updated
This is absolutely critical. The most dangerous “drive-by download” attacks work by exploiting known security holes in outdated software. Make sure your operating system (Windows/macOS), your web browser (Chrome, Firefox, Edge), and any browser extensions are set to update automatically.
Outdated operating systems are especially vulnerable to automated exploit attempts from malicious ad scripts. Each update contains security patches that close the very doors malvertisers try to kick open. Regular security updates close the loopholes that malvertising campaigns attempt to exploit.
3. Install powerful antivirus
Think of this as your final safety net. Even with an ad blocker and updated software, a clever attack might slip through. A high-quality antivirus program is essential for malware protection because it actively scans for malicious activity.
If a malicious ad does manage to drop a piece of malware onto your system, the best antivirus can detect, quarantine, and remove it before it does real damage. This helps prevent dangerous outcomes like data theft from hidden malware dropped by malicious ads.
4. Enable 'click-to-play' plugins in your browser
While less common now, some attacks used to exploit plugins like Adobe Flash or Java. Modern browsers have mostly phased these out, but it’s still a good security habit. Older browser plug-ins were a common target for exploit kits bundled inside malicious ads. Go into your browser’s settings and ensure that any site plugins or media content are set to “ask first” or “click-to-play.” This prevents potentially malicious content from running automatically the moment a page loads.
5. Be cautious of suspicious ads
Even with an ad blocker, some ads might occasionally get through. Suspicious pop-up ads are especially likely to contain misleading or harmful content. Use your common sense. Many malicious ads are simply disguised online scams designed to lure users into unsafe actions.
If an ad makes an outrageous claim (“Congratulations, you’ve won a free iPhone!”), Displays a fake virus warning, or looks unprofessional, don’t click it. Common examples include fake virus pop-ups that lead to tech support scams. Some malicious ads even mimic phishing pages to steal your information. Treat online ads with a healthy dose of skepticism, even on websites you trust.
6. FAQs about malvertising
Have more questions? Here are quick answers to the most common queries about this sneaky threat.
What is malvertising?
Malvertising is a cyberattack method that uses malicious advertising to spread malware. Hackers hide malicious code within legitimate-looking digital ads, which are then distributed through trusted ad networks onto reputable websites.
Do I have to click on an ad to get infected by malvertising?
Not always. This is what makes it so dangerous. The most severe type of malvertising employs a “drive-by download” technique. This can infect your device just by the malicious ad loading on the webpage. No click or interaction from you is required.
How do I get rid of malvertising?
You don’t get rid of the malvertising attempt itself, but you must remove the malware it delivered. If you suspect you’ve been infected, the first steps are to run a full, in-depth scan with your antivirus software and clear your browser’s cache and cookies.
Can malvertising happen on mobile phones?
Yes, absolutely. Any device with a web browser is vulnerable, including iPhones, Android smartphones, and tablets. The attacks can occur through ads on mobile websites or even within free, ad-supported mobile apps.
Does using a VPN protect me from malvertising?
A standard VPN alone does not protect you, as its main job is to encrypt your connection, not block content. However, many premium VPN services now include built-in ad and malware blockers, which can be a very effective tool in your defense against malvertising.
7. Conclusion
Malvertising is a uniquely deceptive threat because it turns the places we trust most – reputable news sites and popular blogs – into potential minefields. Unlike other threats that require you to visit a shady website, this one brings the danger directly to your safe spaces, often infecting your device without a single click.
Ultimately, staying safe from malvertising isn’t about avoiding the internet, but about browsing smarter. Improving user awareness is one of the most effective ways to reduce exposure to malicious ads. By taking these proactive steps, you can browse your favorite sites with confidence, knowing you have a strong defense. For a deeper dive into other threats and how to stay safe online, explore more guides from Safelyo in our Antivirus section.













