What is malware? Think of it as a catch-all term for any type of “malicious software” designed to be an unwanted guest on your computer – one that messes with your files, spies on you, or just generally causes chaos.
In an age where we live our lives online, understanding these digital threats isn’t just for tech wizards; it’s a fundamental part of staying safe. Whether you’re banking, shopping, or just scrolling through social media, malware is a persistent risk that can turn a good day into a costly nightmare.
With over a decade of experience in cybersecurity, I’ve seen firsthand how a seemingly harmless download or a convincing-looking email can unleash havoc. The most common mistake people make is thinking they aren’t a target. But the reality is, if you’re online, you’re in the field. Malware isn’t some complex magic; it’s a tool used by attackers, and knowledge is your best shield.
In this simple guide, you’ll discover:
- A clear, no-jargon definition of what malware is.
- The 10 most common types, from annoying adware to dangerous ransomware.
- How malware actually gets onto your devices.
- Simple, actionable steps to detect, remove, and prevent it.
Don’t wait for a suspicious pop-up to take your security seriously. Let me walk you through everything you need to know to protect your digital life.
1. What is malware?
Malware is short for “malicious software.” It’s the official name for any software or code intentionally designed to damage or disrupt a computer, steal data, or generally make a mess of your digital life.
Think back to that uninvited guest we mentioned. While a software bug might be like a clumsy guest who accidentally spills a drink, malware is the guest who shows up with the specific goal of breaking your windows, reading your private messages, and stealing your credit card information.
Cybercriminals create malware for a handful of nasty reasons: to extort money, to steal sensitive personal information for identity theft, to hijack your computer’s resources, or sometimes, just to prove they can cause widespread chaos.
A common point of confusion is the difference between “malware” and a “virus.” It’s actually very simple:
Malware is the general category, while a virus is a specific type. Think of it like the word “vehicle.” A virus is a “car,” a trojan is a “truck,” and ransomware is a “motorcycle.” They are all different types of vehicles, but you wouldn’t call a motorcycle a car. In the same way, all viruses are malware, but not all malware is viruses. We’ll explore all these different types in just a moment.
You may also be interested in: What is antivirus? Basic facts you should know in 2025
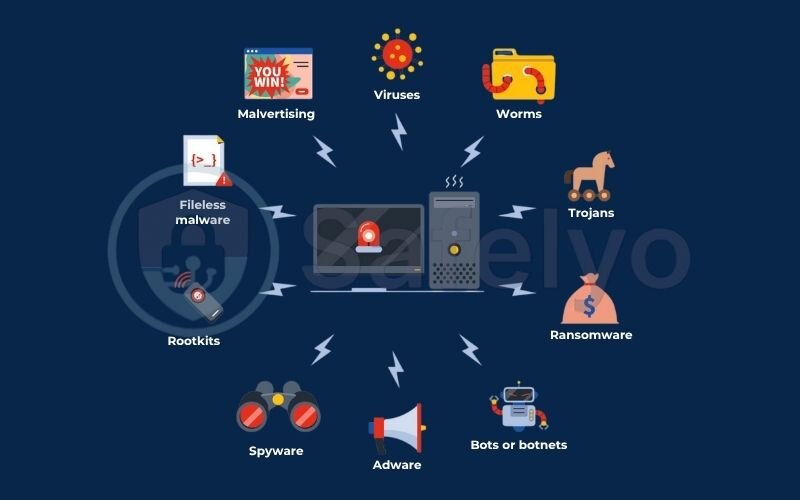
2. The 10 most common types of malware you need to know
Now that you know what malware is, let’s meet the usual suspects. While there are many variations, most threats fall into a few key categories. Understanding how each one operates is the first step in knowing how to fight back.
Here’s a quick cheat sheet to help you tell the most common ones apart at a glance.
| Malware Type | Primary Goal |
| Virus | Attaches to clean files and spreads when the file is opened. |
| Worm | Spreads across networks on its own, without human help. |
| Trojan Horse | Disguises itself as a useful program to trick you into installing it. |
| Ransomware | Encrypts your files and demands a payment to unlock them. |
| Spyware | Secretly hides on your device to watch and record your activity. |
| Adware | Automatically displays or downloads unwanted advertisements. |
| Keylogger | A type of spyware that specifically records every key you press. |
Now, let’s break down each of these threats – and a few more advanced ones – in more detail.
2.1. Virus
Just like its biological counterpart, a computer virus needs a host to survive and spread. It attaches itself to a legitimate program or file, and when you run that file, the virus activates and starts replicating.
Imagine you have a perfectly good sandwich (a clean file). A virus is like a tiny bit of mold that gets on one slice. The sandwich still looks fine, but when you share it with a friend (send the file), the mold spreads to their sandwich, too.

I remember in the early days of personal computing, the most common way viruses spread was through infected floppy disks. Someone would bring a “free game” to a friend’s house, and by the end of the day, both computers would be infected. The delivery method has changed (it’s now email attachments and downloads), but the principle is exactly the same.
2.2. Worm
Unlike a virus, a worm doesn’t need a host program. It’s a standalone piece of malware that spreads on its own across networks, exploiting security vulnerabilities to jump from one computer to another. They are masters of replication.
If a virus is mold on a sandwich you have to physically share, a worm is like a rumor that spreads through an office by itself. One person hears it, tells two colleagues, those two tell four more, and soon the entire office knows without anyone actively trying to spread it.

I’ve seen worms cripple entire corporate networks in a matter of hours. The infamous “Conficker” worm from years ago was a prime example. It exploited a Windows vulnerability, and because many businesses were slow to update their systems, it spread like wildfire, causing massive slowdowns and security risks.
2.3. Trojan (or Trojan horse)
Named after the famous Greek story, a Trojan disguises itself as a legitimate program to trick you into installing it. It looks like a useful utility, a game, or even an antivirus app. Once inside, it opens a “backdoor” for other malware to enter.
You order a large, beautiful birthday cake online. It gets delivered to your door, and it looks perfect. But once you bring it inside your house, a team of burglars jumps out of the cake. The cake was just a disguise to get past your front door.

The most common trojans I help people remove are disguised as free software. I once had a client who downloaded a “free video converter” from a shady website. The converter worked, but it also silently installed a keylogger (we’ll get to that next) that captured their online banking details.
2.4. Ransomware
This is one of the most terrifying and costly types of malware today. Ransomware locks up your files and encrypts them, making them completely inaccessible. The attackers then demand a ransom payment (usually in cryptocurrency) in exchange for the decryption key.
It’s digital kidnapping. Imagine a criminal breaks into your house, puts all your family photos, important documents, and valuables into a safe, and then walks away with the only key. To get the key back, you have to pay them.
I received a panic call from a small business owner whose entire server was hit by ransomware. All their customer records, invoices, and financial data were encrypted. They faced a terrible choice: pay thousands of dollars to anonymous criminals with no guarantee of getting their data back, or lose their business. This is why having backups is non-negotiable.
2.5. Spyware
As the name suggests, spyware is designed to be sneaky. It hides on your computer and secretly monitors your activity. This can include tracking your browsing habits, recording your login credentials, or even accessing your webcam and microphone.
Spyware is like having a tiny, invisible spy hiding in your room, writing down everything you do, who you talk to, and what you type into your computer. You have no idea they are there, but they are collecting information about you.

Many “free” browser toolbars or extensions come bundled with spyware. A user might install a “weather toolbar” for convenience, not realizing it’s also reporting every single website they visit back to a marketing company. It’s a huge privacy invasion masquerading as a free feature.
2.6. Adware
While often less malicious than ransomware, adware is incredibly annoying. Its sole purpose is to bombard you with unwanted advertisements. It can hijack your browser, change your homepage, and plaster pop-up ads all over your screen.
Adware is like having an extremely aggressive salesperson follow you around a store, constantly shouting product deals in your face and shoving flyers into your hands, no matter how many times you say no.

The classic sign of an adware infection is when a user tells me, “I can’t even open my browser without ten pop-ups appearing for things I never searched for.” It’s often bundled with other free software, and users click “agree” on the installation without reading the fine print that they’re also consenting to the adware.
Read more:
2.7. Keylogger
A keylogger is a particularly invasive form of spyware that records every single keystroke you make. Its goal is to capture sensitive information like passwords, credit card numbers, and private messages as you type them.
Imagine someone is secretly looking over your shoulder every time you use an ATM, watching you type in your PIN. That’s exactly what a keylogger does, but for everything you type on your keyboard.

Keyloggers are a cybercriminal’s favorite tool for financial theft. I’ve dealt with cases where victims had their social media, email, and bank accounts compromised all at once because a keylogger captured the password they used for all of them.
2.8. Botnet (and Bots)
This is a bit different. A single “bot” is a computer that has been infected with malware, allowing a criminal to control it remotely. A “botnet” is a network of these infected “zombie” computers, all controlled by a single attacker.
Think of your computer as a person. A bot infection turns that person into a zombie. They still look normal, but they are now taking orders from a zombie master (the attacker). A botnet is the attacker’s personal zombie army, ready to be used for large-scale attacks.

Your computer could be part of a botnet right now, and you might not even know it, aside from it running a bit slower. Attackers use these botnets to send massive amounts of spam emails or to conduct Distributed Denial-of-Service (DDoS) attacks that take websites offline. Your device becomes an unwilling accomplice in a larger crime.
2.9. Rootkit
Rootkits are among the most dangerous and difficult-to-detect types of malware. A rootkit is designed to give an attacker “root” or administrative-level control over a computer system while actively hiding its own presence.
A rootkit is like an intruder who not only has a master key to every door in your house but is also wearing an invisibility cloak. They can come and go as they please, do whatever they want, and you’ll never see any sign they were there. Standard security cameras (like antivirus software) might not even spot them.

Removing a rootkit is a nightmare. Because they bury themselves so deeply into the operating system, a standard antivirus scan often misses them. In many of the severe cases I’ve handled, the only 100% guaranteed way to get rid of a rootkit was to completely wipe the hard drive and reinstall the operating system from scratch.
2.10. Fileless Malware
A new and increasingly popular form of attack, fileless malware doesn’t install any files on your hard drive. Instead, it operates directly in your computer’s memory (RAM). It uses legitimate, built-in system tools (like PowerShell on Windows) to carry out its attacks.
Think of a traditional malware as a burglar who leaves muddy footprints (files) all over your house. Fileless malware is like a ghost. It floats through your house, does what it wants, and when it leaves (or you restart your computer), it vanishes without a trace, leaving no footprints to investigate.

This type of malware is a huge challenge because it fools traditional antivirus programs that are designed to scan files on a hard drive. I’ve seen security systems give a computer a clean bill of health, only for the user to keep experiencing strange issues. It was fileless malware running in the background, which requires more advanced, behavior-based detection tools to catch.
3. How to tell if your device is infected with malware
Malware isn’t always obvious. While some types, like ransomware, announce themselves in the worst way possible, others are designed to stay hidden. However, they almost always leave behind clues. Think of these as the digital symptoms of a sick computer.
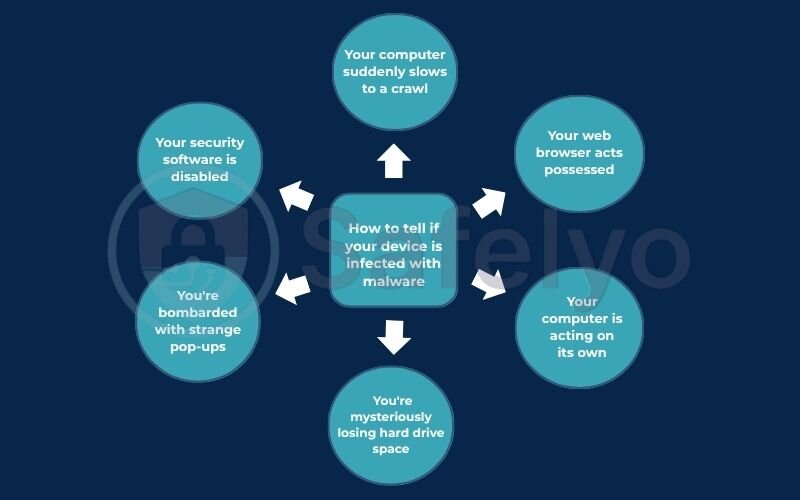
If you’re experiencing several of these, it’s a strong sign you might have an unwanted guest.
3.1. Your computer suddenly slows to a crawl
This is the most common symptom. If your computer used to be snappy but now takes forever to start up, open programs, or even just browse the web, malware could be hogging your system’s resources (like its memory and CPU) in the background.
It’s like trying to run a marathon while carrying a heavy, invisible backpack. You can still move, but everything is much slower and requires more effort because something is secretly weighing you down.
When a client tells me “my computer just got really slow overnight,” my first suspect is always malware. I’ve seen botnet infections that use up 90% of a computer’s processing power to mine cryptocurrency or send spam, leaving almost nothing for the user’s actual tasks.
3.2. You’re bombarded with strange pop-ups
If you’re seeing pop-up ads appearing on your screen even when your web browser is closed, that’s a classic sign of an adware infection. These ads are often for sketchy products, online gambling sites, or fake “You’ve won!” messages.
This is the digital equivalent of finding junk mail flyers stuck to the inside of your refrigerator. They have no business being there, and it means someone got into your house without your permission.
A tell-tale sign is when the pop-ups are completely unrelated to what you’re doing. I once helped someone who was getting casino ads while working on a Microsoft Word document. That’s a clear red flag that the ads aren’t coming from a website but from malware installed directly on the system.
3.3. Your web browser acts possessed
Has your default homepage or search engine suddenly changed without your permission? Are you being constantly redirected to websites you didn’t intend to visit? This is a strong indicator of a “browser hijacker,” a type of malware designed to drive traffic to specific sites.
Imagine your car’s GPS was hijacked. You type in “grocery store,” but it keeps trying to route you to a mechanic shop you’ve never heard of. Your browser is doing the same thing – taking you where the attacker wants you to go, not where you want to go.
The most frequent hijacker I see changes a user’s default search engine from Google to a weird, unknown search site filled with ads. Every search they make generates revenue for the attacker. It’s sneaky and incredibly frustrating for the user.
3.4. Your security software is disabled
This is a major red flag. More advanced malware will actively try to disable your antivirus software or firewall to prevent itself from being detected and removed. If you find that your security tools are turned off and you can’t turn them back on, you likely have a serious infection.
This is like a burglar cutting the wires to your home security alarm before they break in. It’s a deliberate act to make sure they can operate without getting caught.
I’ve had cases where a user clicks to open their antivirus program, and the window flashes for a second and then disappears. That’s the malware actively killing the security process. It’s a clear sign the malware has gained significant control over the system.
3.5. You’re mysteriously losing hard drive space
Some types of malware, especially viruses and worms, will replicate themselves or download other malicious files, which can start eating up your available storage space for no apparent reason.
It’s like finding that your closet is suddenly full of clothes you never bought. Something is adding clutter to your space without your knowledge.
3.6. Your computer is acting on its own
Are you noticing mouse movements you didn’t make? Are programs opening and closing by themselves? Is your webcam light turning on when you’re not using it? This is a terrifying but clear sign that an attacker may have remote access to your device, often through a Trojan or a rootkit. This is a critical emergency.
If you ever see your cursor moving on its own, the very first thing you should do is immediately disconnect the computer from the internet (unplug the network cable or turn off the Wi-Fi). This severs the connection to the remote attacker and gives you time to figure out how to clean the machine.
4. How does malware get onto your computer?
Malware doesn’t just magically appear on your device. It needs a way in, and cybercriminals have developed some very clever tricks to deliver it. Think of these as the primary “infection vectors.” Most of them rely on tricking you into opening the door for them.
Here are the most common ways malware spreads:
4.1. Phishing emails and malicious attachments
This is, by far, the number one delivery method. You receive an email that looks legitimate – it could pretend to be from your bank, a delivery service like FedEx, or even your boss. The email creates a sense of urgency and asks you to either click a link or open an attachment.
It’s like getting a formal-looking letter in the mail with the bank’s logo on it. The letter says there’s a problem with your account and you need to call a number immediately to fix it. But the number doesn’t go to your bank; it goes to a scammer. The malicious link or attachment in an email works the same way.
In my line of work, I’d estimate over 80% of security incidents start with a single click in a phishing email. The classic tells are urgent subject lines (“Action Required: Your Account is Suspended”) and generic greetings (“Dear Valued Customer”). The attachments are often disguised as harmless PDFs or Word documents, but they contain hidden scripts that execute when opened.
4.2. Drive-by downloads from infected websites
Sometimes, you don’t even have to click on anything specific. A drive-by download can happen when you simply visit a malicious or compromised website. The site exploits a vulnerability in your web browser or its plugins to automatically and silently download malware onto your device.
This is like walking past a building where someone throws a bucket of “malware water” on you from an open window. You didn’t do anything wrong except walk down that particular street.
I’ve seen legitimate websites of small businesses get hacked. The owner often has no idea, but their site is now silently trying to infect every visitor. This is where a top-tier antivirus with real-time web protection is invaluable – it acts as your digital umbrella, blocking these malicious sites before they can load.
4.3. Bundled with “free” software
Everyone loves a freebie, and attackers know it. Malware, particularly adware and spyware, is often bundled into the installers of free programs, games, or utilities downloaded from untrustworthy sources.
It’s the classic “free lunch” trap. A restaurant offers you a free sandwich, but to get it, you have to agree to let one of their salespeople follow you around for the rest of the day, shouting advertisements in your ear.
I always advise people to be cautious of download portals that host tons of free software. When you run an installer, always choose the “custom” or “advanced” installation option. You’ll often find pre-ticked boxes trying to install extra browser toolbars or “PC optimizer” tools. Uncheck them all. They are almost always unwanted programs.
4.4. Unpatched software vulnerabilities
Software isn’t perfect. Developers are constantly finding and fixing security holes, or “vulnerabilities,” in operating systems (like Windows and macOS), web browsers (like Chrome), and applications (like Adobe Reader). Attackers actively search for devices that haven’t installed the latest security updates.
Your software is like your house. A vulnerability is like forgetting to lock your back window. You might not know it’s unlocked, but a burglar (the attacker) who is actively checking every house on the block will find it and use it to get inside.
This is the most critical and most overlooked aspect of personal security. When your computer or phone pesters you with an “Update Available” notification, it’s not just about getting new emojis or features. Most of those updates contain vital security patches that close those “unlocked windows.” Ignoring updates is one of the biggest and most dangerous security mistakes you can make.

5. How to remove and prevent malware infections
Okay, you’ve seen the warning signs and you suspect your device is infected. Don’t panic. The next steps are about taking back control. And once your device is clean, the focus shifts to making sure this never happens again. Prevention is always better than a cure.
5.1. Step 1: How to remove malware from your device
If you suspect an active infection, follow these steps in order.
Disconnect from the internet immediately.
This is your first and most critical move. Just like cutting the strings on a puppet, this stops the malware from communicating with its master. It can’t send your data out or receive new commands. Unplug the Ethernet cable or turn off your Wi-Fi.
Enter "Safe Mode".
Most malware is designed to load automatically when your computer starts normally. Safe Mode is a special diagnostic startup mode that loads only the absolutely essential programs needed for your operating system to run. This often prevents the malware from activating.
I’ve had countless situations where I couldn’t even open an antivirus program in normal mode because the malware would instantly shut it down. Booting into Safe Mode is the trick that allows you to get around the malware’s defenses so you can actually run a scan. (A quick search for “How to enter Safe Mode on Windows 10/11” or “macOS” will give you the specific key combination for your device).
Run a full scan with a trusted antivirus program.
Once in Safe Mode, open your security software and run a full, deep scan. A “quick scan” isn’t enough here. You need the program to check every single file and folder on your system. Let it run until it’s completely finished.
PRO TIP:
If you don’t have an antivirus or you suspect yours is compromised, you can use another computer to download a “rescue scanner” or a “second opinion scanner” (like Malwarebytes Free) onto a USB drive. You can then run that on your infected machine while it’s disconnected from the internet.
Delete and quarantine the threats.
Your antivirus will present you with a list of detected threats. For most users, the best course of action is to follow the recommended action, which is usually to “Quarantine” or “Delete” the malicious files. Quarantining safely isolates the file so it can no longer do any harm.
Restart your computer and reconnect.
After the scan is complete and the threats have been dealt with, restart your computer in normal mode. Reconnect to the internet and monitor your device closely. Does it seem faster? Are the pop-ups gone? If so, you’ve likely succeeded.
See also:
5.2. Step 2: How to prevent malware (The best long-term strategy)
Removing malware is great, but not having to deal with it in the first place is even better. Good digital hygiene is your best defense.
Use a powerful antivirus program (and keep it updated).
This is your number one, non-negotiable line of defense. A modern antivirus doesn’t just scan for known viruses; it provides real-time protection that actively blocks malicious downloads, flags dangerous websites, and detects suspicious behavior from new, unknown threats. This is the single most important security tool you can have.
Keep your software updated.
I can’t stress this enough. When you see that “Update Available” pop-up for Windows, macOS, Chrome, or any other app, install it as soon as possible. These updates contain critical security patches that close the backdoors attackers love to exploit.
Ignoring a software update is like getting a letter from your lock company saying your front door lock is faulty, and then choosing to leave it as is. You’re just asking for trouble.
Be suspicious of emails and downloads.
Treat every unsolicited email with a healthy dose of skepticism. Never click a link or open an attachment unless you are 100% certain who it’s from and what it is. If an email from your “bank” seems odd, don’t click the link. Instead, open your browser and type in the bank’s website address manually.
Use strong, unique passwords and two-factor authentication (2FA).
Malware can sometimes steal your passwords. If you use the same password everywhere, a single breach can compromise your entire digital life. Use a password manager to create and store complex, unique passwords for every account. And wherever possible, enable 2FA. That extra code sent to your phone is an incredibly powerful barrier against attackers.
Back up your important files.
This is your ultimate safety net, especially against ransomware. If an attacker encrypts all your files, you can simply wipe your computer, reinstall your system, and restore your files from your backup. They lose all their power over you.
The clients I’ve worked with who had good, recent backups were the ones who recovered from a ransomware attack with minimal stress. Those who didn’t face devastating consequences. Use a cloud service or an external hard drive and set up automatic backups today.

6. FAQ about malware
We’ve covered a lot of ground, but you might still have a few questions. Here are some quick, straightforward answers to the most common queries about malware.
What is malware in simple words?
Malware is just a shorter term for “malicious software.” In simple terms, it’s any computer program created with the intent to harm your device, steal your information, or cause disruption. Think of it as the overall category that includes everything from viruses and trojans to spyware and ransomware.
What’s the difference between malware and a virus?
Think of “malware” as the general term “vehicle.” A “virus” is just one specific type, like a “car.” Other types of malware include worms (motorcycles) and trojans (trucks). So, all viruses are malware, but not all malware is viruses.
How does malware get on your device?
The most common ways are through phishing emails (tricking you into clicking a bad link or opening an infected attachment), drive-by downloads from compromised websites, being bundled with “free” software, and by exploiting unpatched security holes in your operating system or applications.
How do you tell if you have malware?
The most common signs are a sudden and significant slowdown of your computer, a barrage of unwanted pop-up ads, your web browser being redirected or hijacked, your antivirus software being disabled, or your computer acting on its own (like the mouse moving by itself).
Can Macs get malware?
Yes, absolutely. While Macs were historically less targeted than Windows PCs, that is no longer the case. Cybercriminals have developed numerous types of malware specifically for macOS, including ransomware, spyware, and adware. No operating system is immune.
How do I remove malware?
The safest method is to first disconnect from the internet, then restart your computer in Safe Mode. From there, run a full, deep scan with a trusted antivirus program like those recommended by Safelyo. Allow the software to quarantine or delete all detected threats, then restart your computer normally.
7. Conclusion
Navigating the online world can feel like walking through a minefield, but understanding the threats is half the battle won. Malware, in all its forms, from annoying adware to destructive ransomware, is designed to prey on the uninformed. But now, you’re no longer in that group. You have the knowledge to recognize the dangers and the tools to protect yourself.
To stay safe, remember these key takeaways:
- Malware is any software designed to cause harm. A virus is just one specific type of malware.
- Be vigilant about how it spreads. Most infections happen because of a moment of carelessness, like clicking a suspicious email link or ignoring a software update.
- Know the warning signs. A slow computer, random pop-ups, and hijacked browsers are not normal – they are clear distress signals.
- Prevention is your best weapon. A proactive approach is far more effective than a reactive cleanup.
The ultimate defense against malware is a combination of smart habits and powerful tools. While being cautious online is crucial, having a top-tier security suite acting as your 24/7 guard is essential.
For expert-vetted recommendations and in-depth reviews, let Safelyo guide you. Explore our Antivirus category to find the perfect security software to keep your digital life safe, secure, and malware-free.













