Has your browsing ever been interrupted by a loud, flashing pop-up screaming that your PC is riddled with viruses? That heart-stopping moment is exactly what is scareware designed to create. It’s a digital con-artistry, a fake virus warning meant to send you into a panic.
But before you reach for your credit card or call that “support” number, take a deep breath. As a cybersecurity analyst, I’ve seen these digital ghost stories countless times. They aren’t sophisticated viruses that have breached your defenses; they are cheap psychological tricks designed to prey on one thing: your fear.
This guide will serve as your shield and sword. I will dissect these scams so you can spot them from a mile away. You’ll learn:
- The simple definition of scareware and its true goal.
- How to recognize the tell-tale signs of a fake alert.
- The immediate, safe steps to take when you encounter one.
- Proactive tips to make your browser a no-go zone for these tricks.
Knowledge is the best antivirus for fear. Let me walk you through how to dismantle these scare tactics, so you can take back control of your screen – and your peace of mind.
1. What is scareware? The anatomy of a digital ghost story
At its core, scareware is not a virus – it’s a psychological trick. It’s a form of what we in the industry call a social engineering attack, which is a fancy way of saying it’s a scam that plays on your emotions, not a technical hack that breaks into your computer’s code.
Let me give you a real-world analogy. Imagine a stranger sprints up to your car at a traffic light, points frantically at your engine, and yells, “It’s smoking! Your car is about to explode!” Then, in your moment of panic, they try to sell you a tiny, overpriced, and completely fake fire extinguisher.

That’s scareware in a nutshell. The scammer’s goal isn’t to damage your computer directly. Their objective is to frighten you into making a bad decision, fast. They want to panic you into:
- Buying their worthless “antivirus” software.
- Calling their fraudulent “tech support” hotline.
- Giving up your credit card details to “fix” a problem that never existed.
In my years analyzing digital threats, I’ve seen that the most successful scams aren’t always the most technically complex. Scareware is a prime example. It’s effective because it bypasses your computer’s security and targets a much more vulnerable system: The human brain.
You may also be interested in: What is antivirus? Basic facts you should know in 2025
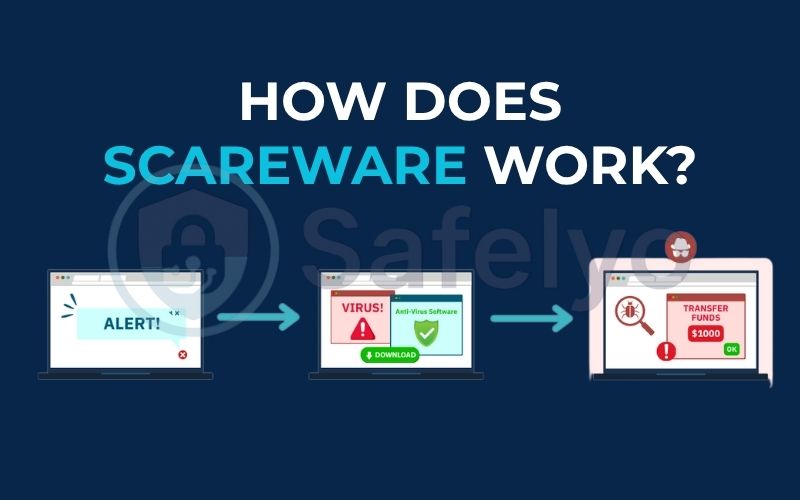
2. How does scareware work? From pop-up to panic
Think of a scareware attack as a badly written play with a predictable, four-act script. Once you know the script, you’ll never fall for the performance again.
Step 1: Delivery (The bait is set)
First, the scareware has to get on your screen. It doesn’t need to “infect” you in the traditional sense. It usually sneaks in through two main doors:
- Malicious ads (malvertising): Scammers buy ad space on websites, but instead of a normal ad, they display a fake warning. You could be reading a perfectly safe news article or recipe blog when it appears.
- Hacked websites: Sometimes, a legitimate but poorly secured website gets compromised, causing it to display these pop-ups to its visitors.
You haven’t done anything wrong. You just happened to be in the wrong digital place at the wrong time.
Step 2: The fake alert (The curtain rises)
This is the main event. A pop-up explodes onto your screen, often with flashing red borders, loud warning sounds, and aggressive messages. You’ll see things like:
- URGENT: Your PC is infected with 17 viruses!
- CRITICAL THREAT DETECTED – IMMEDIATE ACTION REQUIRED
- A fake progress bar that quickly “finds” hundreds of issues.
It’s all theatre. I’ve analyzed hundreds of these alerts, and they all rely on the same cheap props: scary-looking icons (like skulls or biohazard symbols) and language designed to cause maximum alarm.
Step 3: The call to action (The demand is made)
The pop-up won’t just scare you; it will offer a “solution.” It will desperately urge you to click a button like “Scan Now,” “Remove All Threats,” or “Activate Protection.” Sometimes, it will even freeze your browser and demand that you call a “Microsoft Certified Technician” at a provided phone number.
Step 4: The trap (The floor gives way)
Suppose you take the bait, the trap springs. Clicking the button will either redirect you to a payment page for a useless, fake antivirus program or, worse, initiate the download of actual malware. If you call the number, you’ll be connected to a scammer who will try to get your credit card information or trick you into giving them remote access to your computer.
The psychology behind the scare: WHY THESE TACTICS WORK
So, why do these seemingly obvious tricks work so well? It’s because they exploit basic human psychology. The scammers are banking on three things:
- Fear appeal: When we’re scared, our rational thinking shuts down. A flashing warning about “imminent data loss” triggers our fight-or-flight response, making us want to solve the problem now without stopping to think if the threat is even real.
- Urgency bias: By using countdown timers or words like “IMMEDIATELY,” they create a false sense of urgency. This is a classic high-pressure sales tactic designed to prevent you from taking a moment to research or ask for a second opinion.
- Authority bias: The pop-ups often use logos from well-known companies like Microsoft, Google, or Apple. When I started in this field, I was amazed at how effective a stolen logo could be. Seeing a familiar brand makes the scam feel legitimate, tricking us into trusting the warning.
3. The ultimate guide to spotting scareware: Real-world examples
The single best way to defeat scareware is to know what it looks like. Think of this section as your field guide. After years of dissecting these scams, I’ve learned they all have “tells” – giveaways that expose them as fakes. Let’s shine a light on the most common ones you’ll encounter in the wild.
3.1. The classic fake antivirus warning
This is the original scareware model. A pop-up appears that tries its best to imitate a legitimate security program, like Windows Defender or McAfee. It will often show a fake scan in progress, rapidly “discovering” dozens of threats.
It’s all in the details. The design is what I call “almost right.” The colors might be a little too bright, the font slightly off, or the logo blurry and pixelated. But the biggest giveaway is the language.
- Look for bad grammar and typos. You’ll often see clumsy phrasing like “Your computer is infected” or “Threats have been detected.” Professional software companies have proofreaders; scammers usually don’t.
- Watch for misspelled brand names. I’ve seen things like “Microsoft Security” or “Windows Defender.” It’s a subtle but surefire sign of a fake.
3.2. The urgent tech support scam
This one is more aggressive. Your entire screen might go blue or red, displaying a terrifying error message that looks like a system crash. The message insists your data is at risk and provides a “toll-free” number to call for immediate help from “Microsoft” or “Apple” technicians.
This is where I need you to remember one golden rule from my experience: Microsoft, Apple, and Google will never, ever display a random pop-up with a phone number and demand you call them. They simply don’t operate that way. Their support is initiated by you through their official websites.
- The phone number is a scam. A legitimate system error will never ask you to call someone.
- The message creates false authority. It uses familiar logos to trick you into believing the alert is official when it’s just an image displayed in your web browser.
3.3. The browser-locking alert
This one feels especially scary because it traps you. You try to close the tab or the browser, but the pop-up keeps reappearing, making it seem like your entire computer is hijacked.
Take a breath. This isn’t your operating system being held hostage; it’s just a simple piece of web code (JavaScript) running in a loop. It’s the digital equivalent of someone holding a door shut, not them having barricaded your entire house. The goal is to make you panic and think the only way out is to click their malicious link or call their number.
- You can’t close the tab. This is the defining feature of this tactic.
- The alert message is persistent. No matter what you do within the browser, the warning message won’t go away. We’ll show you exactly how to break out of this trap in the next section.
3.4. The ‘official’ law enforcement notice
This is the most intimidating tactic of all. A pop-up appears with the logo of the FBI, CIA, or your local police force. It accuses you of a serious crime, like accessing illegal content or software piracy, and demands you pay a “fine” immediately (often in cryptocurrency or gift cards) to unlock your computer.
This scam relies purely on fear and authority. But it’s also the easiest to debunk with a little common sense. I can assure you, law enforcement agencies do not conduct investigations via browser pop-ups.
- They demand untraceable payment. Real government agencies will never ask for payment in Bitcoin, Amazon gift cards, or wire transfers to avoid jail time. This is the reddest of red flags.
- The process is all wrong. Legal action involves warrants, subpoenas, and official, in-person communication – not a pop-up that appears while you’re browsing the internet.
4. Scareware vs. Ransomware
In the world of digital threats, it’s crucial to know who you’re dealing with. People often confuse scareware with its much more sinister cousin, ransomware. From my experience helping users navigate these issues, making this distinction is the first step toward a proper response.
The core difference is simple: Scareware is a bluff. Ransomware is a real attack.
Let’s break that down.
Scareware is like a con artist telling you they’ve locked your front door and demanding money for the key. In reality, the door was never locked. The entire threat is a lie designed to trick you. The real danger only happens if you fall for the bluff and hand over your money or install the fake “fix” they offer.
Ransomware, on the other hand, is a digital burglar who has actually broken into your house, changed all the locks, and is now demanding payment to let you back in. It actively encrypts your files – your photos, documents, and videos – making them completely unusable. The damage is real, immediate, and devastating.
Think of it this way:
- Scareware attacks your mind.
- Ransomware attacks your files.
Here is a simple table to make the scareware vs ransomware distinction crystal clear:
| Feature | Scareware (The Bluff) | Ransomware (The Real Attack) |
|---|---|---|
| Primary Goal | To trick you into paying for fake software or giving up personal information. | To force you to pay a ransom fee to get your encrypted files back. |
| Method | Displays fake pop-ups and warning messages to create panic. | Silently runs in the background, encrypting your personal files with a key only the attacker has. |
| Actual Damage | None, initially. The software itself doesn’t harm your files. The damage comes after you follow its instructions. | Immediate and severe. Your files are locked and inaccessible until a ransom is paid (and even then, there’s no guarantee). |
| How to Handle | Calmly close the browser or pop-up. Do not click anything. Run a scan with your trusted antivirus later. | This is a serious security incident. Disconnect from the internet immediately and seek professional help or use decryption tools. |
Recognizing you’re facing a scareware bluff, not a ransomware hostage situation, empowers you to react correctly. Instead of panicking, you can simply close the curtain on the bad performance.
5. How to remove scareware: An immediate action checklist
Alright, so a scary pop-up has taken over your screen. You’ve correctly identified it as scareware. What now? The most important thing is not to panic. Over the years, I’ve walked countless people through this exact scenario. The solution is usually much simpler than you think.
Follow these steps calmly. Do not interact with the pop-up itself.
YOUR IMMEDIATE ACTION PLAN
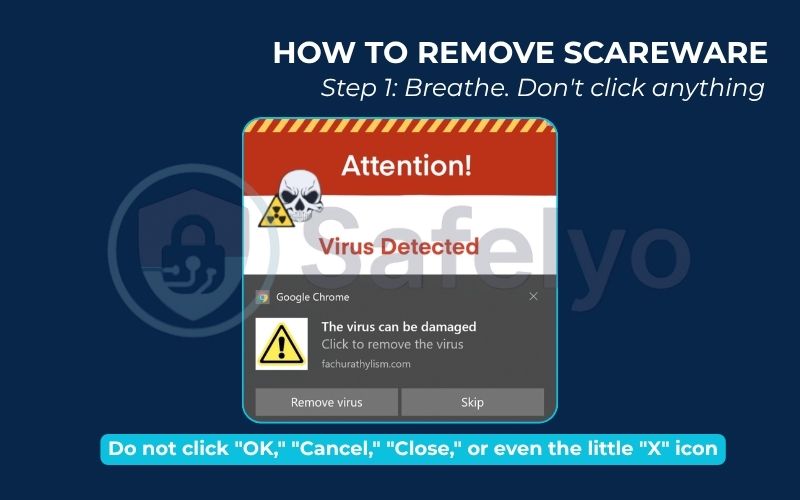
Step 1: Breathe. Don’t click anything.
Seriously, take a breath. Remember what we’ve learned: this is a trick. Do not click “OK,” “Cancel,” “Close,” or even the little “X” icon on the pop-up window. In many scams, these buttons are programmed to do the opposite of what they say – they can trigger a malicious download.
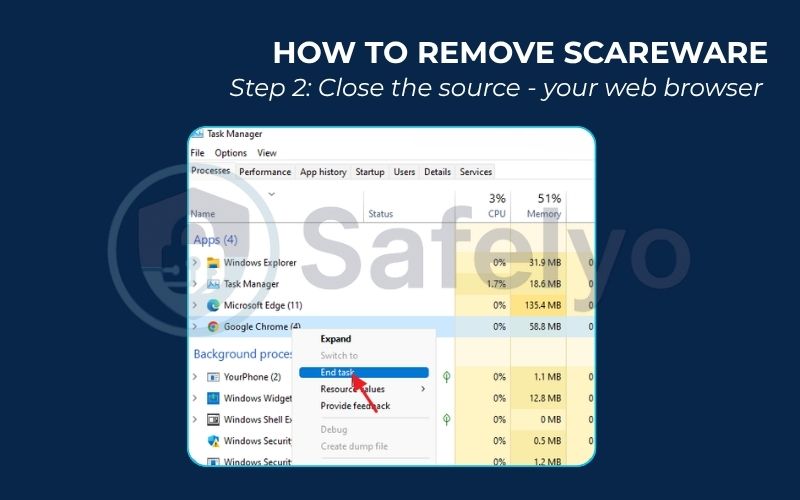
Step 2: Close the source – your web browser.
The scareware is almost always contained within a single browser tab or window.
- First, try to close the browser tab. If that doesn’t work, try closing the entire browser window.
- If the browser is locked and won’t close (a common tactic we discussed), you need to force it to shut down. This will not harm your computer. It’s like turning off a TV that’s stuck on one channel.
- On Windows: Press Ctrl + Shift + Esc to open the Task Manager. Find your web browser (e.g., Google Chrome, Microsoft Edge) in the list of applications, select it, and click “End Task.”
- On a Mac: Press Command + Option + Esc to open the Force Quit Applications window. Select your browser from the list and click “Force Quit.”
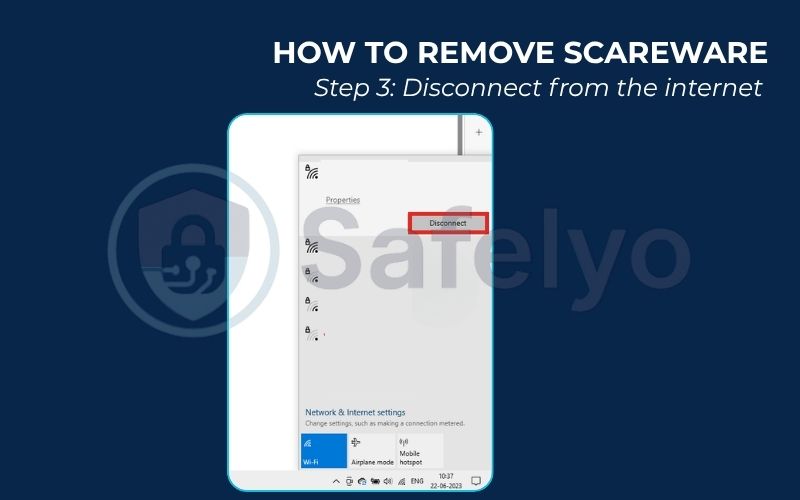
Step 3: Disconnect from the internet (optional but good practice).
If you’re worried you might have accidentally clicked something, disconnecting from the internet by turning off your Wi-Fi or unplugging the Ethernet cable is a smart safety measure. This prevents any potentially downloaded malware from “phoning home” or downloading more harmful components.
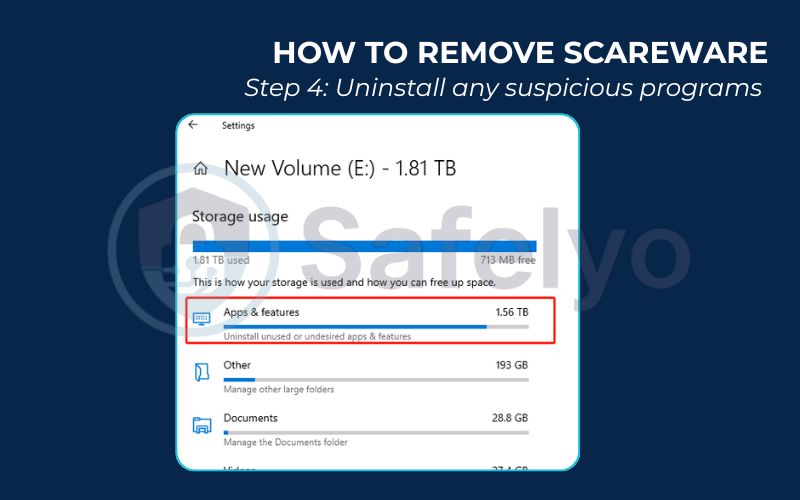
Step 4: Uninstall any suspicious programs.
Did the scareware trick you into installing a “cleaner” or “antivirus” tool? Go to your computer’s control panel and uninstall it immediately.
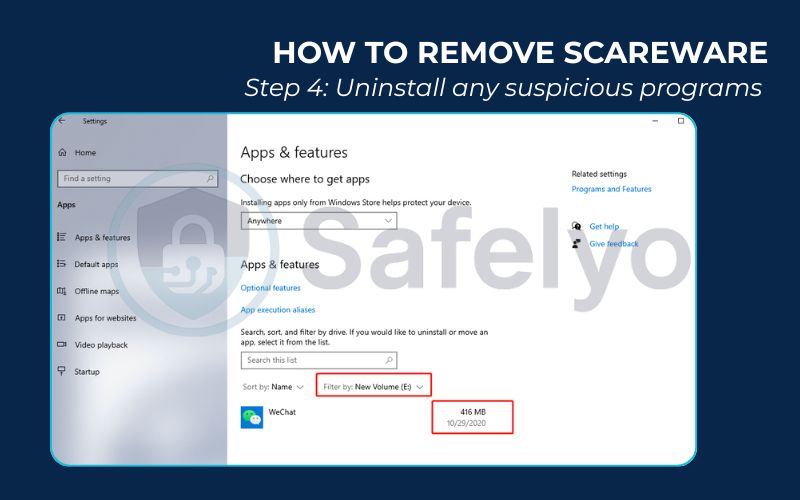
- On Windows: Go to Settings > Apps > Apps & features.
- On a Mac: Open your Applications folder.
Look for any program you don’t recognize, especially anything installed around the time the pop-ups started. If you’re unsure, a quick Google search of the program’s name can tell you if it’s legitimate.
Step 5: Scan with a trusted security tool.
After the immediate threat is gone, it’s time for a peace-of-mind check. Run a full system scan using a reputable, pre-installed antivirus program. This will find and remove any residual malware that might have snuck past during the confusion.

>> If you’re unsure which tool to trust, or don’t have one installed, our team has tested the best Antivirus Software of 2025 to help you perform a thorough and safe scan.
Following this checklist resolves 99% of the scareware incidents I’ve ever encountered. The key is to remember your power: you can always shut down the performance by simply closing the browser.
Read more:
6. How to avoid scareware in the future
Dealing with a scareware attack is one thing; making sure you never have to deal with one again is the real goal. The good news is that preventing scareware doesn’t require you to be a tech wizard. It’s about building a few simple, smart habits.
Based on my experience at Safelyo, the most common mistake people make is thinking of security as something you only do after a problem appears. True digital safety is about prevention, not just reaction. Here are the most effective shields you can put up.
- Use a pop-up blocker.
This is your first and strongest line of defense. Most modern browsers like Chrome, Firefox, and Safari have built-in pop-up blockers, but make sure they are enabled. A good blocker will stop most scareware alerts before you even see them. It’s the digital equivalent of having a bouncer at the door of your browser.
- Keep your software updated.
This is non-negotiable. Always install updates for your operating system (Windows or macOS) and your web browser as soon as they’re available. These updates frequently contain critical security patches that close the very loopholes “malvertising” uses to deliver scareware pop-ups.
- Never download from unknown sources.
Only download software directly from the developer’s official website or a trusted app store. If a pop-up or an ad offers you a “free system scan” or a “PC performance booster,” ignore it. It’s almost always a trap.
- Use a comprehensive antivirus with real-time protection.
A solid antivirus program does more than just scan for files you tell it to. Its real-time protection feature acts as a constant guard, actively monitoring websites and downloads to block threats before they can execute. This is the difference between having a smoke detector and having a 24/7 security guard.
From the Safelyo Lab: An Expert’s Note
We’ve recently observed a significant rise in browser-locking scareware that specifically targets mobile users, especially on Android devices. These scams often use the phone’s vibration motor to create an even greater sense of panic and physical urgency. Remember, the same “force quit” principle applies. You can always close the browser app from your phone’s recent apps screen to escape the trap. Don’t let the buzzing fool you.
By layering these simple practices, you create a digital environment where scareware simply can’t find a foothold. You’re not just hoping to avoid threats; you’re actively making your devices a hostile territory for them.
7. FAQ about scareware
We’ve covered a lot of ground, but you might still have some specific questions. Here are clear, direct answers to some of the most common queries I hear about scareware.
What is scareware in computers?
In simple terms, scareware is a type of scam that uses fake, alarming pop-ups to trick you into thinking your computer has a serious problem, like a virus infection. Its real purpose is to scare you into buying useless software, calling a fraudulent tech support line, or giving up your personal information. It’s a psychological trick, not a real threat to your files.
Is scareware a virus?
Not exactly. Scareware itself is the tactic – the scary pop-up. Think of it as the bait. However, it is often used as a delivery method to trick you into downloading an actual virus or other malware. The pop-up isn’t the virus, but clicking on it can lead you to one.
What does a scareware attack usually look like?
A typical scareware attack involves a sudden, aggressive pop-up message that fills your screen. It often uses flashing colors, warning symbols (like skulls or shields), and urgent language like “CRITICAL THREAT DETECTED” or “Your PC is infected!” It will almost always demand immediate action, such as clicking a “Scan Now” button or calling a phone number.
How do I get rid of scareware?
The best way is to not interact with the pop-up at all. Simply close the browser window. If the browser is locked, use your computer’s Task Manager (Ctrl+Shift+Esc on Windows) or Force Quit feature (Command+Option+Esc on Mac) to shut down the browser. Afterward, run a full scan with your trusted antivirus software for peace of mind.
Can my Mac or iPhone get scareware?
Yes. Scareware is an equal-opportunity scam. Because it relies on tricking the user through a web browser, it can appear on any device that can access the internet, including Macs, iPhones, and Android devices. The method of attack and the way to handle it – by closing the browser – remains the same across all platforms.
What is the difference between scareware and ransomware?
The key difference is that scareware is a bluff, while ransomware is a real attack. Scareware just tells you there’s a problem, but your files are safe. Ransomware actually encrypts your files, making them unusable until you pay a ransom.
I already clicked and paid for the fake software. What should I do now?
Act quickly. First, contact your bank or credit card company immediately to report the fraudulent charge and ask for a chargeback. Second, uninstall the fake software you just installed. Finally, disconnect from the internet and run a full, deep scan of your computer using a reputable antivirus program to find any malware that may have been bundled with it.
8. Conclusion
Now that you know what is scareware, you are armed with the single most powerful weapon against it: knowledge. The moment a flashy, fear-mongering pop-up appears, you’ll no longer feel panic, but recognition. You’ll see the scam for what it is – a cheap trick, not a genuine crisis.
Remember these key takeaways to stay safe:
- Scareware is a psychological bluff, not a real virus infection. Its goal is to make you panic.
- Be suspicious of any pop-up that uses urgent language, bad grammar, or demands immediate payment or a phone call.
- If you see one, stay calm and close your browser. Never click on the pop-up itself, not even the “close” button.
- Prevention is your best defense. Use a pop-up blocker, keep your software updated, and run a trusted antivirus program.
Don’t let fear dictate your decisions online. By staying informed and skeptical, you take control away from the scammers. For complete protection against scareware and the entire spectrum of digital threats, explore the in-depth reviews and guides in the Antivirus category of Safelyo.













