Have you ever wondered why you stay logged into Facebook or Gmail even after closing and reopening your browser? It’s thanks to something called a ‘session’.
But what if a malicious actor could ‘steal’ that very login session? Welcome to the world of session hijacking, a stealthy attack that enables hackers to take control of your accounts, often without requiring your password.
In this guide, we will explain what is session hijacking using simple examples. We will show you exactly how it works. Most importantly, we will provide clear and actionable steps to help you protect yourself. Even experts in ethical hacking study these techniques to help organizations strengthen defenses. Join me as I show you how to lock your digital “door” tight.
Short on time? Here’s the essential rundown on session hijacking. It’s an attack where hackers steal your active login “key” to break into your accounts without ever needing your password.
- What is session hijacking? It’s an attack where a hacker steals your temporary “session ID” (think of it as a digital key card) stored in a browser cookie. This allows them to access your online accounts and impersonate you without ever needing your password.
- How do attackers steal your session? They use several methods, most commonly by “sniffing” it from unsecured public Wi-Fi networks. They can also use malicious links (phishing/XSS) or malware already on your computer to steal your browser’s cookies directly.
- How can you prevent it? The best defense is a layered one. Always use a VPN on public Wi-Fi, only visit secure HTTPS websites, and avoid clicking suspicious links. A strong antivirus program is also essential to block cookie-stealing malware.
- Log out and use MFA. When you’re finished with a website, log out to invalidate your session key. For critical accounts, enabling Multi-Factor Authentication (MFA) provides a powerful final barrier, often stopping a hijacker even if they manage to steal your session.
1. What is session hijacking?
Before we can understand how a session is hijacked, we need to know what a session is in the first place. The easiest way to think about it is with a real-world comparison: The hotel key card.
1.1. Let’s start with the basics: What is a session?
When you log into a website using your username and password, it resembles checking into a hotel. Instead of asking for your ID (username and password) each time you want to enter your room, the front desk (the website) provides you with a temporary key card. This key card is referred to as a session ID.
This key card, typically stored in your web browser as a small text file called a cookie, serves as your temporary proof of identity. Whenever you click a link or load a new page on that site, your browser automatically presents the key card to the website. The website recognizes it and responds, “Ah, I know you. You’re checked in. Come on in.” This mechanism enables you to remain logged in while navigating the site. This entire process is part of the website’s session management system, establishing a continuous web session between you and the server.
From my experience, this whole system is built for convenience. Without sessions, the internet would be incredibly frustrating. You would have to re-enter your username and password every single time you clicked a link on a website, which would make browsing sites like Amazon or YouTube nearly impossible.
1.2. So, what is session hijacking?
Now that you understand the “hotel key card” concept, defining the attack becomes incredibly simple.
Session hijacking, which is also commonly called cookie hijacking, is the act of an attacker stealing or copying your unique “digital key card” (your session ID).
The consequences of this are exactly what you’d expect. Once the hacker obtains a copy of your key card, they can approach the “hotel” (the website) and present the stolen key. The website’s server will then grant them access to your “room” (your account) without hesitation.
From there, the attacker can do almost anything you could do. This results in complete unauthorized access to your personal accounts and sensitive data. They can read your private emails, post on your social media profile, access your personal information, or even transfer money from your account. Such actions can escalate into direct financial theft if the hijacker targets banking sessions.
This kind of direct information theft can escalate into far more severe account compromise. The most chilling part of a session theft attack is that the hacker accomplishes all of this without ever needing to know your actual password.
To the website, the attacker, holding your valid session key, looks exactly like you. This is why it’s also sometimes referred to as session token hijacking. Attackers rely heavily on stolen session token values because they act as temporary proof of identity.
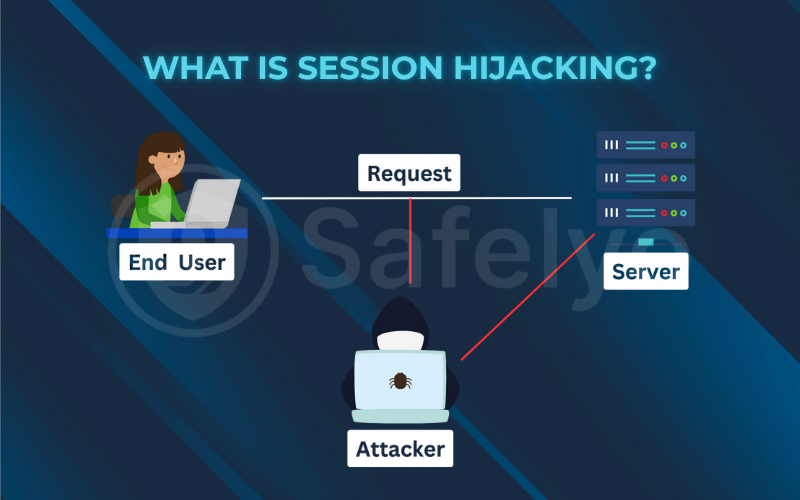
3. How a session hijacking attack works
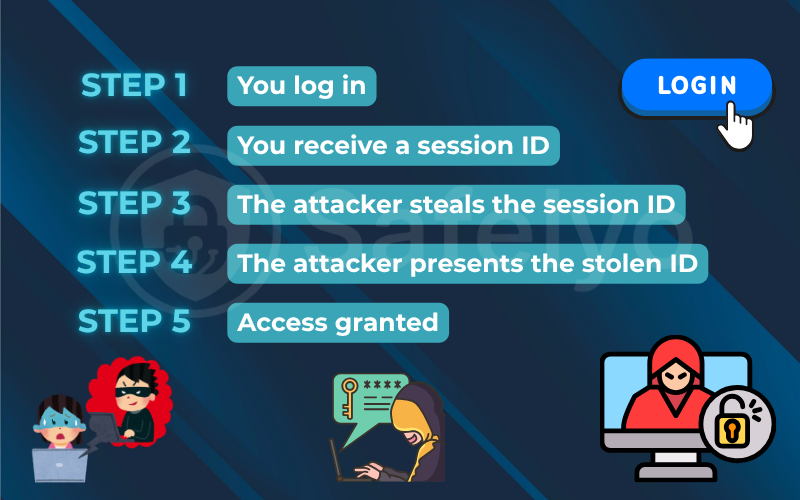
While the methods for stealing a session ID can be technical, the overall process of a successful attack follows a logical, five-step path. Understanding this flow helps demystify how does session hijacking work.
- Step 1: You log in. This initial user authentication step establishes trust between your browser and the server. This action initiates a new web session that remains active until you log out or the server ends it. You visit a website, let’s say yourbank.com, and enter your username and password to start a new session.
- Step 2: You receive a session ID. In many systems, this identifier is essentially a session token that grants continued access until it expires. The bank’s server verifies your credentials and sends a unique session ID back to your browser, which is stored in a cookie. You are now logged in.
- Step 3: The attacker steals the session ID. This is the critical step. The hacker uses one of several techniques (which we’ll cover next) to intercept or steal that session cookie from you.
- Step 4: The attacker presents the stolen ID. With the valid session token attached, the server treats the malicious request as legitimate. The hacker then goes to yourbank.com and sends a request to the server, but they attach your stolen temporary cookie to that request.
- Step 5: Access granted. The bank’s server receives the request. It sees a valid session ID that it recognizes and trusts. Believing the request is coming from you, it grants the hacker full access to your account.
From the server’s perspective, steps 4 and 5 are completely legitimate. It has no way of knowing that the valid session ID is now in the hands of the wrong person.
4. The most common types of session hijacking attacks
An attacker can’t just magically guess your session ID; they have to actively steal it. Many ethical hacking training programs replicate these attacks in controlled environments to test system resilience. While the methods can get technical, they generally fall into a few common categories. These techniques represent some of the most widely exploited attack vectors in modern web security.
| Attack Type | How It Works | Primary Defense |
| Session Sniffing | Attacker “listens” for your session ID on unsecured Wi-Fi. | Use a VPN on public networks. |
| Cross-Site Scripting (XSS) | An attacker injects malicious code into a trusted website you visit. | Be cautious of suspicious links. |
| Malware Attack | A virus on your computer steals cookie files directly from your browser. | Install a strong antivirus. |
| Session Fixation | Attacker tricks you into using a session ID they already know. | Avoid clicking strange links in emails. |
Now, let’s look at each of these methods in more detail.
4.1. Session sniffing (or side-jacking): Eavesdropping on public Wi-Fi
Some security experts also refer to this technique as session side jacking, especially when the attacker captures session cookies through open or weakly protected wireless traffic. This is one of the oldest and still one of the most effective methods, especially on unsecured networks. This technique is also widely known as session side jacking, especially when done over unsecured Wi-Fi.
Imagine you’re at a coffee shop using their free public Wi-Fi. If that network is not properly encrypted (i.e., it doesn’t have a password or uses old security standards), your data is sent “in the clear.” This opens the door to traffic interception, where attackers capture everything you send or receive. This makes it easy for attackers using packet sniffing tools to capture your session ID. A hacker on the same network can use simple software to “sniff” or listen in on all the network traffic.
On poorly secured networks, this can escalate into a full man-in-the-middle attack where all traffic is intercepted. When you log into a non-secure website, your session cookie is sent across this open network, and the hacker can easily intercept and copy it. This is why I personally never do any sensitive browsing on public Wi-Fi without a VPN.
4.2. Cross-site scripting: Injecting malicious code
This attack is more sophisticated. Here, the hacker doesn’t target you directly but instead targets a vulnerability in a website you trust.
The attacker finds a flaw on a website – for example, in its comment section – that allows them to inject a small piece of malicious JavaScript code. Such security vulnerabilities make it easier for attackers to inject harmful scripts. Some scripts are delivered through sophisticated phishing lures that direct users to compromised pages. The website, not realizing that the code is dangerous, saves it.
Later, when you visit that legitimate page, your browser executes everything on it, including the hacker’s hidden script. That script’s job is simple: Grab your session cookie for that site and send it back to the attacker.
4.3. Malware attacks: Stealing from your own computer
Sometimes the attack comes from a vulnerability much closer to home: Your own device. A severe malware infection can quietly harvest session IDs long before the user notices any symptoms.
If your computer gets infected with certain types of malware, like a Trojan or spyware, that malware can have far-reaching access. It can be designed to specifically look for and steal the cookie files stored by your web browsers. It then sends this treasure trove of session data directly to the attacker, giving them access to any site where you have an active session.
4.4. Session fixation: Giving you a key before you log in
This is a clever social engineering trick. Instead of stealing your key after you log in, the attacker gives you one of their own keys first.
In this scenario, the hacker might email you a link stating, “Log in to your account to view this special offer.” This link includes a specific session ID known to the attacker. When you click on it and log in, you essentially instruct the website to associate that attacker-generated session ID with your account. As a result, the hacker can then use that same session ID to gain access to your account.

5. How to prevent session hijacking (protection for everyday users)
While the attack methods sound scary, the good news is that protecting yourself relies on a few simple but powerful security habits. You don’t need to be a cybersecurity expert to stay safe. Here is a clear checklist for how to prevent session hijacking.
5.1. Avoid unsecured public Wi-Fi (or use a VPN)
This is the number one rule to prevent session sniffing. Treat all public Wi-Fi networks – at cafes, airports, and hotels – as potentially hostile. A hacker could be on the same network, monitoring your activity. If you absolutely must use public Wi-Fi, always connect through a reputable VPN first. A VPN encrypts your entire internet connection, scrambling your data and making your session cookies unreadable to anyone trying to eavesdrop. Strong encryption ensures intercepted traffic is unreadable even if captured.
>> You may also be interested in: Best VPN for public Wi-Fi: Top 5 strong security & speed in 2026
5.2. Always look for https
Before you enter any login information, look at the website’s address bar. It should start with https://, not just http://. Regular HTTP connections send data unencrypted, exposing session IDs to anyone monitoring the network. The ‘S’ stands for ‘Secure’ and means your connection to that website is encrypted. This added encryption layer is key to preventing session theft during transmission.
This HTTPS / SSL protection makes it vastly more difficult for an attacker to sniff your session ID, even on a compromised network. Without it, any HTTP request could potentially reveal your session cookie. Modern browsers make this easy by showing a padlock icon for secure sites.
5.3. Be cautious of suspicious links and emails
This is your best defense against XSS and session locking attacks. Do not click on links in unsolicited emails or strange pop-ups. Many phishing attacks are specifically designed to steal cookies or session tokens. Always be skeptical. If an email claims to be from your bank, it’s safer to type the bank’s web address directly into your browser rather than clicking a link in the email.
5.4. Use a strong antivirus program
To protect yourself from malware-based attacks, a high-quality antivirus program is essential. It acts as a guard for your computer, scanning for and blocking Trojans and spyware that are designed to steal your browser’s cookie files. Keep it running and updated at all times.
>> Read more:
5.5. Enable multi-factor authentication (MFA)
MFA is a powerful layer of defense. Many secure websites, even if a hacker steals your session ID, will require a second verification step for critical actions like changing your password or making a payment. Multi-factor authentication (MFA), like a code sent to your phone, can stop a hijacker in their tracks even after they’ve gained initial access.
>> Learn more:
5.6. Log out when you’re done
It’s a simple habit, but an effective one. When you actively log out of a website, you are telling the server to invalidate your session ID. Manual logout is one of the simplest session management controls users can apply. This makes the session cookie stored in your browser useless. If an attacker steals it later, it’s like finding an expired key card – it simply won’t work.

6. FAQs about session hijacking
It’s normal to have more questions about this type of technical attack. Here are some quick, direct answers to the most common queries.
What is session hijacking?
Session hijacking is an attack where a hacker steals a user’s active session ID, often stored in a browser cookie. This stolen session token lets the attacker impersonate you without needing additional authentication. This allows the attacker to impersonate the legitimate user and gain unauthorized access to their online accounts without needing a password.
Is session hijacking the same as IP spoofing?
No. Attacks against SSO (Single Sign-On) systems are particularly dangerous because one stolen session can unlock multiple services. IP spoofing involves an attacker faking their IP address to appear as a trusted device. Session hijacking, on the other hand, involves stealing a valid session token after a real user has already logged in and authenticated themselves. They are different techniques.
Can a VPN prevent all session hijacking attacks?
A VPN is extremely effective against session sniffing on public Wi-Fi because it encrypts your connection. However, it cannot protect you from other methods like XSS attacks or malware that is already on your computer. This is why a layered defense is crucial.
How do I know if my session has been hijacked?
If you suspect compromise, following a structured incident response process helps contain further damage. Modern systems use anomaly detection to flag unusual login behavior caused by stolen sessions. It can be very difficult to detect in real-time. The most common signs are noticing activity on your accounts that you didn’t perform (like sent messages, posts, or financial transactions) or being unexpectedly logged out of a service mid-session.
In severe cases, this unauthorized activity can even lead to identity theft if sensitive data is misused. These unexpected actions usually indicate unauthorized access through a stolen session ID.
7. Conclusion
What is session hijacking is a question about a stealthy and real threat that turns the convenience of staying logged in into a potential security risk. The core danger stems from the unauthorized access a hacker gains without your password. Fortunately, while the attack is sophisticated, the methods to protect yourself are based on simple, smart browsing habits that anyone can adopt.
Cybersecurity isn’t about one single tool, but a collection of smart habits. Building strong security awareness habits is what truly protects you in the long run. Even unrelated threats like a DoS attack can create distractions that help attackers slip in unnoticed. By applying these steps, you make the job of a session hijacker significantly more difficult. At Safelyo, we’re committed to making these topics easy to understand. To learn more about identifying and preventing other online threats, explore more guides in our Antivirus section.













