If you’ve spent more than five minutes researching VPNs, you’ve seen the promise everywhere: a strict “no-logs policy.”
It’s hailed as the single most important feature for your online privacy, the very foundation of digital anonymity. But here’s the uncomfortable truth: For many providers, it’s just a promise. How can you be sure a VPN is telling the truth and not just using a popular marketing buzzword?
As a privacy analyst, I’ve spent years digging through dense privacy policies and verifying providers’ claims. I’ve learned that understanding what is no-logs policy is only the first step. The real power comes from knowing how to verify it.
This guide goes beyond simple definitions. I’m giving you a complete investigative toolkit to see past the sales pitch. You’ll discover:
- What different types of user data a VPN can log?
- How to use Safelyo’s Trust Pyramid, our unique framework for grading a VPN’s trustworthiness.
- The critical role of independent audits and RAM-disk servers.
- The real-world proof that separates genuine privacy from empty promises.
It’s time to stop taking VPN providers at their word. Let me show you how to look beyond the marketing and become an expert in verifying a VPN’s privacy claims.
No-Logs Policy in 30 Seconds
A no-logs policy is a VPN’s promise not to store or share your online activity, like your browsing history or IP address. However, not all promises are equal. The most trustworthy VPNs prove their claims through independent audits, use special RAM-disk servers that can’t store data, and have passed real-world tests where their servers were seized.
1. What is no-logs policy?
At its heart, a no-logs policy is a straightforward promise from a VPN provider: They do not collect, store, or share any information that could be used to identify you or your online activity.
Think of a VPN as a private, encrypted tunnel for your internet traffic. A no-logs policy is the guarantee that the tunnel’s owner doesn’t install any cameras, keep a list of who comes and goes, or record where they’re heading. Your journey through that VPN tunnel is completely ephemeral – it happens, and then it’s gone.
From my experience testing and analyzing these services, the most privacy-focused companies view user data not as an asset, but as a toxic liability. Why? Because if a VPN doesn’t have your data, they have nothing to:
- Hand over to government agencies or law enforcement.
- Sell to advertisers or data brokers.
- Lose in a data breach or server hack.
Simply put, no logs means no risk. It’s the ultimate privacy guarantee, but as we’re about to see, the devil is in the details.

2. Not all logs are created equal: What VPNs might log
This is where the marketing promises can get murky. The term “no-logs” isn’t officially regulated, so some VPNs play fast and loose with the definition. In my years of analyzing privacy policies, I’ve found that the most important skill is learning to distinguish between the data that directly compromises your privacy and the data needed to simply run the service.
To make it simple, let’s break them down into two distinct categories.
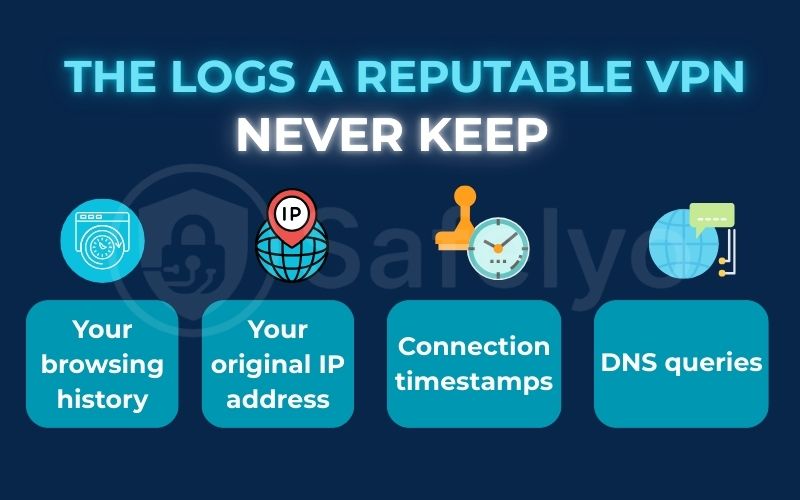
2.1. The logs a reputable VPN will never keep (activity logs)
Think of it like this: When you check into a hotel, they know you’re a guest. But they have no business recording what you do inside your room – the TV channels you watch, the calls you make, or the websites you visit on their Wi-Fi.
Activity logs are the digital equivalent of that. These logs are your private diary, and a trustworthy VPN should never, ever keep them. This includes:
- Your browsing history: A complete list of every website you visit.
- Your original IP address: The unique digital address assigned by your internet service provider (ISP) that can identify your location.
- Connection timestamps: The exact times you connect and disconnect from the VPN.
- DNS queries: A record of the “phonebook lookups” your device makes to find websites.
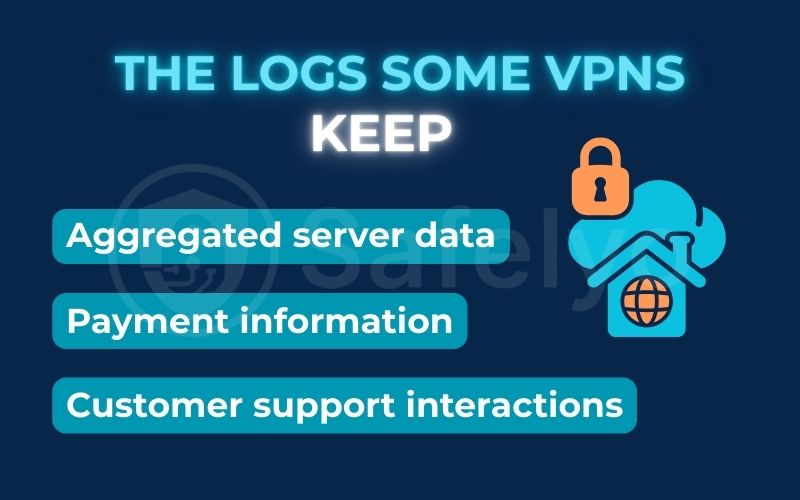
2.2. The logs some VPNs might keep (minimal connection logs)
Now, this is where things get more nuanced. To keep their network running smoothly, some VPNs need to collect a small amount of non-identifying, temporary data. The key here is that this data can never be tied back to a specific user’s activity.
This can include:
- Aggregated server data: A provider might see that their New York server is using 80% of its total bandwidth, but they have no idea who is using that 80%. This helps them manage network performance.
- Payment information: If you pay with a credit card, the VPN will naturally have your name and billing details. This is why I often recommend paying with cryptocurrency for maximum anonymity if your chosen provider supports it.
- Customer support interactions: Your emails or live chats with their support team are typically stored to improve service quality.
Let’s be crystal clear: A true ‘no-logs’ policy means a VPN does not keep any activity logs. Some minimal, anonymized connection data for service maintenance is generally considered acceptable, but the best VPNs are constantly finding ways to eliminate even this.
3. How to verify a no-logs policy
A VPN can say they have a no-logs policy, but how do you actually know you can trust them? Over the years, I’ve developed a method for cutting through the noise. I call it the Trust Pyramid.
It’s a simple framework that ranks the evidence for a no-logs policy from the weakest (the foundation) to the strongest (the peak). When you evaluate a VPN, you start at the bottom and see how high up the pyramid it can climb.
| Trust Level | Type of Evidence | What It Means |
| Level 5: The Peak | Real-World Proof | The policy has been tested in a real crisis (server seizure, court case) and proven to be true. |
| Level 4: High | Independent Audits | A reputable third-party firm has inspected their systems and verified their no-logs claims. |
| Level 3: Medium | Supporting Technology | They use privacy-enforcing tech like RAM-disk servers, making it impossible to store logs long-term. |
| Level 2: Low | Clear Privacy Policy | Their legal documents are transparent, easy to read, and explicitly state what they don’t log. |
| Level 1: Foundation | The Website Promise | The basic marketing claim is made on their homepage. Necessary, but not sufficient on its own. |
3.1. Level 1 (The foundation): The website promise
This is the bare minimum. Every single VPN provider will have “Strict No-Logs Policy!” splashed across their homepage. It’s a necessary first step, but let’s be honest – it’s just marketing.
A promise alone is not proof. This level is the foundation of the pyramid, but if this is the only evidence a VPN offers, you should be extremely skeptical.
3.2. Level 2: A clear and readable privacy policy
The first thing I do when evaluating a new VPN is ignore the marketing page and go straight to their privacy policy. A trustworthy provider will have a policy written in plain English, not confusing legalese designed to hide loopholes. If the document is vague, contradictory, or requires a law degree to understand, that’s a major red flag.
Use this table as you read through a VPN’s privacy policy:
| Item to check | What to look for |
| Clear Language | Is it written for humans, not just lawyers? |
| Specifics on Activity Logs | Does it explicitly say “we do not log your browsing history, DNS queries, or original IP address”? |
| Jurisdiction Information | Does it clearly state which country’s laws they operate under? |
3.3. Level 3: Privacy-friendly technology (RAM-disk servers)
Now we move from technology promises. The top VPN providers now run their entire server network on RAM-disk servers.
Here’s a simple way to understand it: A traditional server stores data on a hard drive, where it stays until it’s manually erased. A RAM-disk server, however, runs exclusively on volatile memory (RAM). This means all data on the server is automatically wiped clean every time it’s rebooted.
From a technical standpoint, this is a powerful guarantee. The system is designed so that it can’t store your data long-term, adding a layer of technological enforcement to the company’s promise. There’s nothing to log because no activity data is ever written to a physical disk.
3.4. Level 4: Independent third-party audits
This is where the evidence gets serious. A VPN at this level pays a reputable, independent auditing firm – like PwC, Deloitte, or Cure53 – to come in, inspect their servers, and scrutinize their code. The auditor’s job is to professionally verify if the VPN’s no-logs claims are actually true.
Think of it like a financial audit for privacy. A VPN that has passed multiple recent audits is significantly more trustworthy. For example:
- NordVPN has been repeatedly audited by PricewaterhouseCoopers (PwC).
- ExpressVPN has had its policies and technology verified by firms like KPMG and Cure53.
When a VPN publishes a clean audit report, they are putting their money where their mouth is.
3.5. Level 5 (The peak): Real-world proof
This is the ultimate test – the trial by fire. Has a VPN’s no-logs policy been tested in a real-world crisis and survived? This is the rarest and most powerful proof of all. Two famous examples immediately come to my mind:
- ExpressVPN in Turkey (2017): Turkish authorities, as part of a high-profile investigation, physically seized an ExpressVPN server. They searched it for connection logs to identify a user, but were unable to find any data whatsoever. This wasn’t a report; it was undeniable proof that the no-logs policy was real.
- OVPN in Sweden (2020): OVPN was taken to court and served a warrant demanding user information. The company proved in a court of law that they had no user data to hand over, and the case was dismissed.
A VPN that reaches this peak has proven its commitment to privacy not with words, but with action under extreme pressure.
>> Check out the best no-log VPN in 2025 (only proven & audited services) to find your perfect match.
4. A special warning: What about free VPNs?
It’s the most tempting offer in the digital world: Complete privacy and security for free. But as a privacy analyst, I have to be blunt: When it comes to your security, you almost always get what you pay for. Remember the old saying: “If a service is free, you are not the customer; you are the product.”
Running a global server network, developing secure apps, and providing 24/7 customer support costs a significant amount of money. Free VPN providers have to cover these costs somehow, and their methods often directly contradict the goal of privacy. They typically make money by:
- Logging and selling your data: Many free VPNs secretly record your browsing habits, the websites you visit, and even your location, then sell this valuable data to advertisers and data brokers.
- Injecting ads into your browser: Some services will bombard you with their own pop-ups and banner ads while you surf the web.
- Using severe limitations: They will often impose slow speeds, tiny data caps, and crowded servers to frustrate you into upgrading to their paid plan.

While a few reputable “freemium” VPNs exist (like Proton VPN’s free tier, which is supported by its paid users), you should be extremely skeptical of any service that promises unlimited protection for free. Their business model often relies on violating the very privacy a VPN is supposed to protect.
>> Read more:
- The 5 best free VPN in 2025 that are actually safe
- The best cheap VPN in 2025: Our top picks starting at just $1.99/mo
5. FAQ about the no-logs policy
We’ve covered a lot of ground, but you might still have some specific questions. Here are quick, direct answers to the most common queries our readers ask about no-logs policies.
What are VPN logs?
VPN logs are records of user data. They are typically broken into two types: activity logs (your browsing history, IP address), which trustworthy VPNs never keep, and minimal connection logs (like aggregated server load), which some VPNs may use for maintenance, but this data should always be anonymized.
What is a no-logs policy?
A no-logs policy is a VPN provider’s public promise that they do not record, store, or share your sensitive online activity. This includes your browsing history, connection timestamps, and original IP address. It is the most critical feature for ensuring your digital privacy.
Is a no-log VPN safe?
Yes, a verified no-logs policy is a cornerstone of a safe VPN. However, true safety also depends on other crucial features like strong AES-256 encryption and secure VPN protocols (like OpenVPN or WireGuard). A no-logs policy ensures your past activity can’t be exposed, even if the VPN’s security is somehow compromised.
Which VPN has a no-log policy?
Many top providers like NordVPN, ExpressVPN, and Surfshark have strict and audited no-logs policies. The best way to choose is not just to see who claims to have one, but to evaluate them using our Trust Pyramid to see how high they climb in terms of proof, from audits to real-world incidents.
Does NordVPN have a no-log policy?
Yes, NordVPN operates under a strict no-logs policy. Crucially, their claim has been independently audited and verified multiple times by the reputable auditing firm PricewaterhouseCoopers (PwC), placing them high on the Safelyo Trust Pyramid.
What is VPN jurisdiction, and why does it matter?
Jurisdiction is the country where the VPN company is legally based. It’s critical because some countries (like those in the 5/9/14 Eyes alliances) have data retention laws that can force companies to log user data. VPNs based in privacy-friendly jurisdictions like Panama, the British Virgin Islands, or Switzerland are generally preferred.
Can a VPN with a no-logs policy still see my traffic?
Technically, yes. The VPN server processing your traffic can see it in real-time as it passes through. However, a strict no-logs policy means this data is never written to a disk or stored in any way. It’s like a conversation that is heard for a split second but is never recorded.
Is a “zero-logs” policy the same as a “no-logs” policy?
Yes, these are marketing terms that are used interchangeably. What matters more than the specific term is the evidence backing it up, as outlined in our Trust Pyramid. Don’t get caught up in the branding; focus on the proof.
“No-Logs” doesn’t mean “No Data”
It’s crucial to understand that even the strictest no-logs VPN still needs some basic information to manage your account – namely, your email address and payment details. A ‘no-logs’ policy specifically refers to your online activity while connected to the VPN. The most privacy-conscious users can further enhance their anonymity by using a disposable email and paying with cryptocurrency, which top-tier VPNs now accept.
6. Conclusion
A no-logs policy is more than just a feature; it’s the foundation of trust between you and your VPN provider. In a world where data is a valuable commodity, choosing a service that actively refuses to collect it is the most powerful step you can take to protect your digital life. But as we’ve learned, you can’t rely on promises alone.
- A true no-logs policy means no activity logs are ever stored.
- Don’t just trust a VPN’s promise; verify it using our Trust Pyramid.
- Look for the highest levels of proof: independent audits, RAM-disk servers, and real-world incidents.
- Be extremely cautious with free VPNs, as their business model often involves logging your data.
By using this framework, you are no longer just a passive consumer. You are an informed investigator, capable of choosing a VPN that truly respects and protects your privacy.
At Safelyo, we only recommend VPNs that meet the highest standards of our Trust Pyramid. Explore our in-depth reviews of the best no-logs VPNs to find the Best VPN service you can truly rely on.