What is AES-256 encryption? Think of it as the unbreakable digital safe for your online life – a powerful standard that locks down your private data, from passwords to financial details, making it unreadable to anyone without the key.
In an era where our personal information is constantly at risk, understanding the technology that protects you isn’t just a bonus – it’s essential. Whether you’re banking online, sending a private message, or connecting to public Wi-Fi, this specific type of encryption is often your first and strongest line of defense. With years of experience in the cybersecurity field, I’ve seen how easily people are intimidated by technical terms. My goal is to show you that AES-256 isn’t just a buzzword; it’s a tangible shield for your information.
In this guide, I will break it all down for you. You’ll discover:
- What AES-256 is, explained with a simple analogy.
- Why it’s considered the gold standard of digital security.
- How it protects you every day in ways you might not realize.
- The real difference between AES-256 and its alternatives.
Don’t let technical jargon stand in the way of your security. Let’s demystify AES-256 together so you can navigate the digital world with confidence.
AES-256 Encryption in 30 Seconds
AES-256 is a highly secure encryption method used to protect digital data. Think of it as an unbreakable digital safe (AES) that uses a 256-bit key – a password so long it’s virtually impossible to guess – to lock your information. It’s considered the ‘gold standard’ for security and is used by governments, banks, and top security apps like VPNs.
1. What is AES-256 encryption?
The best way to understand what AES-256 encryption is to stick with our analogy of the digital safe. Instead of throwing complex technical terms at you, let’s just break down how this safe and its key work, piece by piece.
First, you have your treasure. Imagine your most sensitive personal information – passwords, private messages, bank details, and browsing history – as a collection of priceless jewels. In my line of work, I constantly see people underestimate the value of this data. This isn’t just information – it’s the digital key to your life.
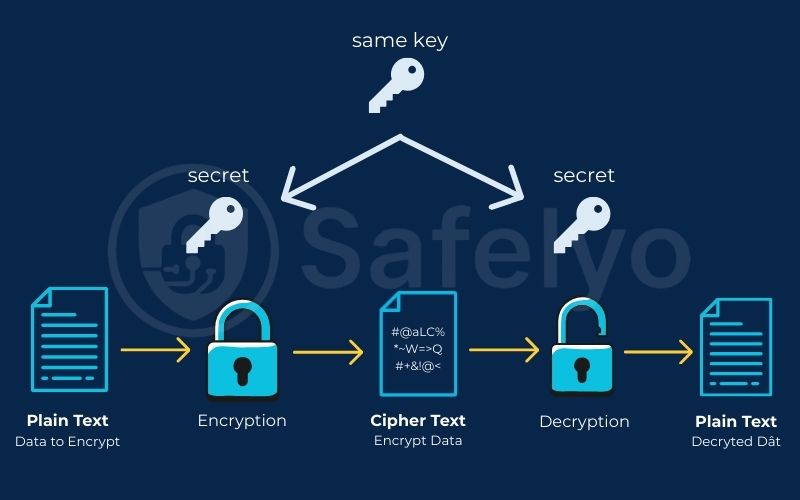
Next, you need to secure that treasure. Encryption is the process of putting these jewels into a digital safe and locking the door. Once locked, the contents are instantly scrambled into an unreadable mess of gibberish. To anyone who tries to peek inside without permission, your valuable data looks like complete nonsense.
But not all safes are created equal. AES, which stands for Advanced Encryption Standard, is a very specific and globally trusted design for this digital safe. It’s so reliable that the U.S. government selected it to protect its own classified information. When I review a security tool for Safelyo, the presence of AES is a non-negotiable benchmark for trust.
Finally, and most importantly, you have the key. AES-256 gets its name from its 256-bit key – the secret combination used to lock and unlock the safe. But this isn’t a simple password like “P@ssword123”. A 256-bit key has more possible combinations than there are atoms in the observable universe. It’s a level of complexity that is, for all practical purposes, infinite.
So, when you see that a service uses AES-256 encryption, you know it’s locking your data in a government-approved safe with a combination so impossibly long that no one could ever guess it.
2. How secure is AES-256?
It’s one thing to say the key is complex, but it’s another to truly grasp what that means. So, just how hard is it to guess the combination to this digital safe?
Hackers have a method for this called a “brute-force attack.” It’s exactly what it sounds like: A computer systematically tries every single possible key combination, one by one, until it finds the right one. Think of a thief sitting in front of our safe, methodically trying every number combination starting from 000…001.
The number of possible keys for AES-256 is 2 to the power of 256 (2^256). It’s a number so vast it’s hard to write out, let alone comprehend.
So let’s put that into perspective. In my years analyzing cybersecurity threats, I’ve seen incredible advancements in computing power. But even those advancements are a complete joke compared to AES-256.
- The Time Factor: If you took the fastest supercomputer currently on Earth and set it to work on cracking a single AES-256 key, it would take billions of years to go through all the possibilities. That’s many times longer than the entire age of the known universe.
- The Physical Analogy: Here’s another way to think about it that I find helps people grasp the scale. It would be like trying to find one specific, marked grain of sand out of all the beaches on the entire planet. And you have to check them one by one.
So when we say AES-256 is secure, it’s not an exaggeration or a marketing gimmick. For all practical purposes, it is mathematically impossible to break by brute force.

3. Symmetric encryption: Why AES-256 is so fast
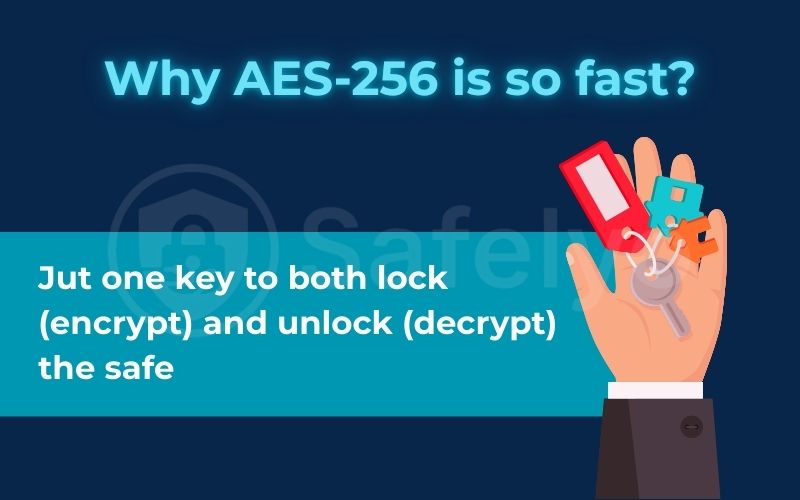
One of the key reasons AES-256 is so widely used is its incredible speed. This is because it’s a type of symmetric encryption. That might sound technical, but the concept is very straightforward.
It simply means AES-256 uses the exact same key to both lock (encrypt) and unlock (decrypt) the safe. Think of it like the key to your front door – you use the one and only key to lock the door when you leave and to unlock it when you return.
The advantage here is efficiency. Because the process only involves a single key, it’s extremely fast and doesn’t require a lot of computing power. This is crucial for tasks that need to happen in real-time. From my experience testing VPNs, if the encryption caused a noticeable lag, people simply wouldn’t use it. AES’s speed makes it perfect for encrypting large amounts of data on the fly, like when you’re:
- Streaming a movie over a VPN.
- Securing a live chat on WhatsApp.
- Protecting a file transfer.
This is different from asymmetric encryption, which uses two different keys – a public key to lock the safe, and a separate, private key to unlock it. While also highly secure, this two-key system is a slower process. It’s better suited for other jobs, like verifying digital signatures, not for the heavy-lifting of everyday data protection.
4. AES-128 vs. AES-256: Which one do you need?
You might occasionally see another version of AES mentioned: AES-128. This naturally leads to the question of which one is better or which one you actually need.
The answer is simpler than you think. The only functional difference between them is the length of the key – the “password” for our digital safe. AES-128 uses a 128-bit key, while AES-256 uses a 256-bit key.
So, is AES-128 secure?
Absolutely.
Even with a “shorter” key, AES-128 is still considered unbreakable by any current or foreseeable technology. A brute-force attack against it would also take more time than the age of the universe. For most of your daily online activities, it provides more than enough security. In fact, many highly reputable services use it.
Then why do we have AES-256?
Because it offers an even higher security margin against future threats, including the theoretical potential of quantum computing. This is why it has become the standard for:
- Top-secret government and military files.
- Financial institutions protect sensitive transaction data.
- Premium security applications like the VPNs and password managers I recommend here at Safelyo.
AES-256 requires slightly more processing power, but on modern devices – from your laptop to your smartphone – this difference is so tiny it’s practically unnoticeable.
Think of AES-128 as a vault that’s completely impossible to break into. AES-256 is the same vault, but with even thicker walls. For your personal data, both are excellent choices, but AES-256 is the undisputed “gold standard” that gives you the ultimate peace of mind.
To make it even clearer, here’s a quick side-by-side look.
AES-128 vs. AES-256 at a glance
| Feature | AES-128 | AES-256 |
| Security Level | Extremely secure (uncrackable) | Even more secure (top-secret standard) |
| Speed | Extremely fast | Fast (negligibly slower) |
| Used By | Most commercial applications | Governments, military, high-security services |
| Right for You? | Yes, perfect for everyday needs. | Yes, the “gold standard” for maximum peace of mind. |
5. Where you see AES-256 every day (without realizing it)
AES-256 isn’t just a theoretical concept or something reserved for spies. You benefit from its protection constantly, often without even knowing it. As a tech analyst, part of my job is to look under the hood of the services we use daily, and I can tell you that this encryption is the bedrock of modern digital security.
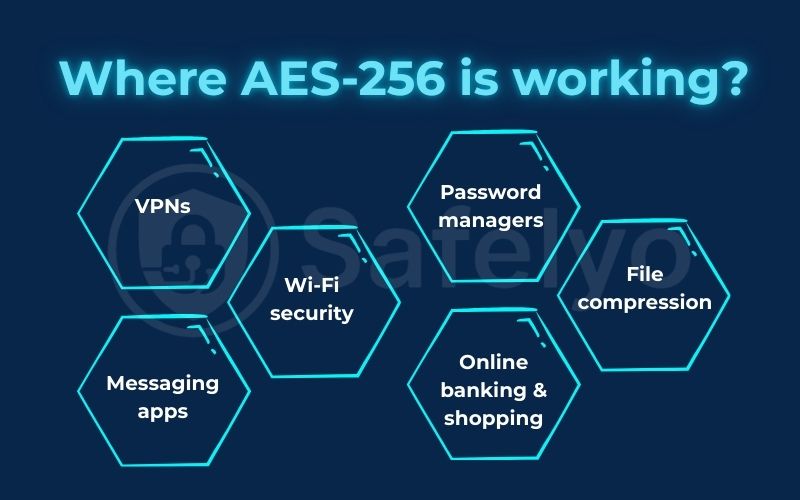
Here are just a few places where AES-256 is working behind the scenes to keep you safe:
- VPNs: When you turn on a top-tier VPN like NordVPN or ExpressVPN, it creates a secure, private VPN tunnel for all your internet traffic. That tunnel is fortified by AES-256 encryption, making your data unreadable to your internet provider, hackers on public Wi-Fi, or anyone else trying to snoop.
- Messaging apps: End-to-end encrypted apps like Signal and WhatsApp use powerful security protocols that incorporate AES-256 to ensure only you and the person you’re talking to can read your messages.
- Wi-Fi security: The WPA2 and WPA3 security protocols that protect most modern home and office Wi-Fi networks rely on AES encryption to prevent unauthorized access to your connection.
- Password managers: When I recommend tools like 1Password or NordPass, it’s because they use AES-256 to encrypt your entire vault of passwords. Your sensitive data is scrambled both on your device and on their servers.
- File compression: Have you ever password-protected a .zip file? Popular programs like 7-Zip and WinRAR use AES-256 to do that, turning your archive into a secure container.
- Online banking & shopping: When you see the padlock icon and “https://” in your browser’s address bar while visiting your bank or an e-commerce site, your connection is secured by the TLS protocol. AES is one of the most common and robust encryption ciphers used within TLS to protect your financial information.
6. FAQ about AES-256 encryption
I get asked about encryption all the time, and a few questions pop up more than others. Here are clear, direct answers to the most common queries about AES-256.
Is AES-256 unbreakable?
For all practical purposes, yes. No known practical attack can break AES-256 when it’s properly implemented. A brute-force attack (guessing every key) is mathematically impossible with current and foreseeable technology – it would take billions of years. While theoretical attacks exist in academic research, they are not a threat in real-world scenarios.
Is AES-256 still safe?
Yes, AES-256 is absolutely safe and remains the gold standard for security in 2025 and for the foreseeable future. It is the recommended encryption standard for governments, banks, and high-security applications worldwide, secure against all known practical forms of attack.
What does it mean when it says “secured with 256-bit encryption”?
It means your data is being protected using an encryption key that is 256 bits long. The length of the key determines its complexity. A 256-bit key offers a massive number of possible combinations (2^256), making it virtually impossible for anyone to guess the key and decipher your data. It is a direct indicator of a very high level of security.
What is the purpose of AES in encryption?
Its purpose is to provide a globally standardized, efficient, and extremely secure method for protecting digital information. AES serves as a reliable algorithm that developers can implement to ensure data confidentiality, preventing unauthorized parties from reading private data.
Who invented AES?
It was developed by two Belgian cryptographers, Vincent Rijmen and Joan Daemen, under the name “Rijndael.” Their algorithm won a public competition hosted by the U.S. National Institute of Standards and Technology (NIST) in 2001 to find the next-generation encryption standard.
What does “military-grade encryption” mean?
It’s a marketing term that almost always refers to AES-256 encryption. It became popular because the U.S. government and its military branches adopted AES-256 to protect their most sensitive, classified data. So, when a service uses this phrase, they are signaling that they use the highest public standard of security available.
Demystifying “Military-Grade”
You’ll see the term ‘military-grade encryption’ everywhere, but it’s important to know it’s a marketing phrase, not an official technical classification. It became popular because the U.S. National Security Agency (NSA) approved AES-256 to protect top-secret information. So, when a VPN says it uses ‘military-grade’ encryption, they’re telling you they use the same incredibly high standard of security trusted by intelligence agencies – which is a very good thing.
7. Conclusion
So, what is AES-256 encryption? At its heart, it’s the digital equivalent of a vault with walls thicker than the universe is old, silently protecting your most valuable online data. It’s not just a random string of letters and numbers; it’s a powerful and reliable promise of security that works for you every single day.
Here are the key takeaways to remember:
- It’s a symmetric encryption standard, using one incredibly complex key to lock and unlock your data with great speed.
- Its 256-bit key makes it practically impossible to break by brute force.
- It’s the gold standard trusted by governments, financial institutions, and top security apps.
- You’re already using it every day to secure your Wi-Fi, private messages, and online banking.
Now, the next time you see “AES-256 encryption” advertised, you won’t just see a technical term; you’ll understand it as a powerful mark of true digital protection. Here at Safelyo, we believe understanding these fundamentals is key to staying safe online. For more essential guides, explore our Privacy & Security Basics category to take full control of your digital life.