We hear a lot about encryption – the process of locking our data away in a digital safe. But what happens next? Decryption is the act of using the right key to unlock that safe, turning scrambled code back into information you can actually read.
In our digital lives, this process happens silently in the background every single day, protecting everything from our bank details to our private messages. Without decryption, secure communication would be a one-way street; we could lock our data, but never safely use it again.
As a security analyst, I’ve noticed people are often fascinated by encryption – the unbreakable lock. But true digital security is a complete cycle. Understanding what is decryption is just as crucial, because a lock is only as good as the process for opening it safely. It’s the moment of truth where your data is either securely revealed to you or remains useless code.
In this comprehensive guide, you’ll discover:
- What decryption is, explained with a simple lockbox analogy.
- The different types of “keys” used to unlock your data.
- How the decryption process works in the tools you use daily, like VPNs.
- The critical difference between encryption vs decryption.
Your data’s security relies on both a strong lock and a secure key. Let me demystify the art of unlocking digital secrets and show you how your information is kept safe, every step of the way.
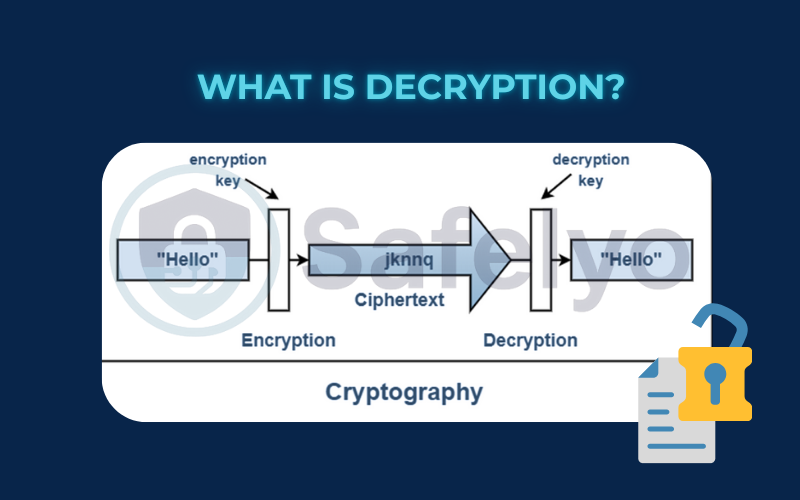
What is Decryption in 30 seconds?
Decryption is the process of converting encrypted data back into a readable format (plaintext). It serves as the crucial counterpart to encryption (the locking process). To decrypt data, you require two components: The correct decryption key and the corresponding decryption algorithm. You can think of it as using the right key to unlock a secret box.
1. What is decryption?
The best way I’ve found to explain the world of cryptography is to forget about computers for a moment and think about sending a secret message. This simple analogy is the key to understanding the entire cycle of data security.
- Plaintext (The Secret Message): Imagine you want to send a secret message to a friend. The original, readable message – “Meet me at noon” – is called plaintext.
- Encryption (Locking the Box): You wouldn’t just send that message on a postcard for anyone to see. To protect it, you put it in a special lockbox. The act of placing the message inside and locking the box is encryption.
- Ciphertext (The Locked Box): Once locked, the box and its contents are scrambled and unreadable to anyone who intercepts it. It might look like “Xq$#fG&j*K”. This locked, unreadable jumble is now ciphertext.
- Decryption (Unlocking the Box): Your friend receives the locked box. Decryption is the process of using the correct key to open the lockbox, turning the scrambled ciphertext back into the original, readable plaintext message: “Meet me at noon.”
To successfully open the box, your friend needs two things: The right decryption key (the physical key itself) and knowledge of how the lock works (the decryption algorithm). Without both, the box remains a useless, unreadable jumble of data.
So, what is decryption in essence? It’s the crucial final step that makes secure communication possible, ensuring that only authorized individuals holding the right key can access the protected information.
2. Encryption vs. Decryption: Two sides of the same coin
As you can see from our lockbox analogy, encryption vs decryption aren’t opposing forces. They are two essential halves of a single, secure process. One cannot exist meaningfully without the other. When I’m evaluating the security of an app, I’m not just looking at how strong its encryption is, but also how securely it handles the decryption process.
Here’s a simple breakdown of their relationship:
| Aspect | Encryption (Locking) | Decryption (Unlocking) |
| Purpose | To protect data by making it unreadable to unauthorized parties. | To make encrypted data readable again for authorized parties. |
| Input | Plaintext (readable data) | Ciphertext (scrambled data) |
| Output | Ciphertext (scrambled data) | Plaintext (readable data) |
| Requirement | An encryption key & algorithm | A decryption key & decryption algorithm |
| Analogy | Putting a message in a lockbox and snapping the lock shut. | Opening the lockbox with the correct key to read the message. |
| Direction | Turns something useful into something secret. | Turns something secret back into something useful. |
Thinking about ciphertext vs plaintext is the easiest way to remember the difference. Encryption creates ciphertext, and decryption reveals the original plaintext. They are the start and end points of a secure data journey.
3. The two types of keys: Symmetric vs. Asymmetric decryption
Not all locks and keys are created equal. In the world of cryptography, there are two fundamental methods for locking and unlocking our secret box. Understanding the difference between them is key to appreciating how modern security tools, from VPNs to secure messaging apps, actually work.
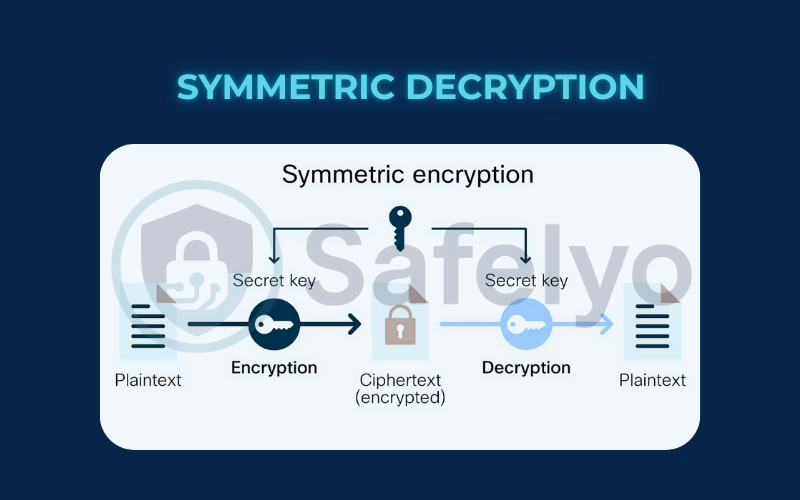
3.1. Symmetric decryption (the identical key)
This is the simplest method to understand. In symmetric encryption, the very same key is used to both lock and unlock the box.
- How it works: You write your message, secure it in the box, and send the locked box to your friend. However, you face a new challenge: how to deliver the key to them. You need to send an identical copy of the key through a separate, secure channel. If a spy intercepts the key, they could unlock the box.
- The Trade-off: The main challenge is securely sharing the key. However, the process itself is extremely fast and efficient.
Used For:
This speed makes it perfect for encrypting large amounts of data quickly. It’s the core technology behind the powerful AES encryption used in your VPN and for protecting the files on your hard drive.
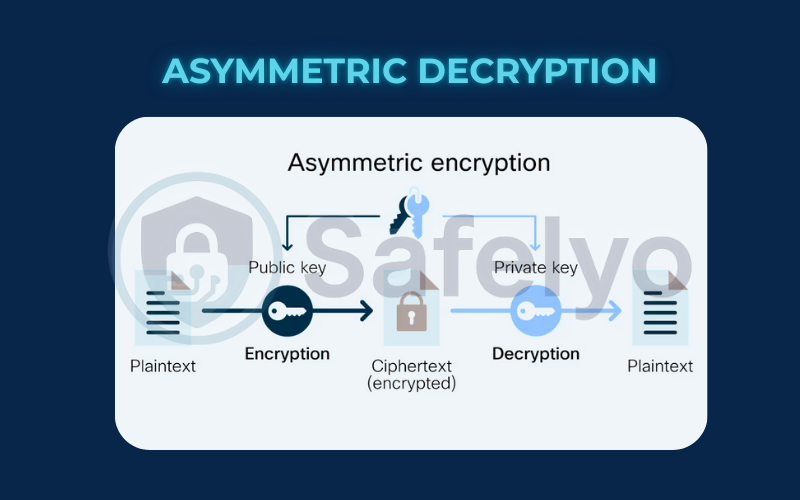
3.2. Asymmetric decryption (the two-key system)
This is a much more clever and elegant solution to the key-sharing problem. In what’s also known as public-key cryptography, your friend has two keys that work together as a mathematical pair:
- A public key, which is like an open padlock. They can give this padlock to anyone in the world without any risk.
- A private key, which is the one-of-a-kind key that can open that specific padlock. They guard this key with their life.
Used For:
Its incredible security for establishing connections makes it the backbone of the internet. It’s used to initiate secure communication when you visit an HTTPS website with the RSA algorithm. It’s also employed in end-to-end encrypted messaging apps like Signal and WhatsApp to securely exchange symmetric keys for the conversation.
- How it works: You want to send your friend a secret message. You ask for their public padlock, use it to lock your box, and send it off. Once that padlock is snapped shut, the only thing in the entire world that can open it is their unique private key. You never had to share a secret key.
- The Trade-off: This process is more complex and therefore slower than the symmetric method.
3.3. Symmetric vs asymmetric decryption
Here’s a quick summary of the symmetric vs asymmetric decryption approaches:
| Feature | Symmetric Decryption (One Identical Key) | Asymmetric Decryption (Two-Key System) |
| Keys Used | One shared secret key for both encryption and decryption. | A public key to encrypt and a separate private key to decrypt. |
| Speed | Very fast. Ideal for large amounts of data. | Slower. Best for small amounts of data, like sharing keys. |
| Key Management | Difficult. Securely sharing the secret key is the main challenge. | Easier. The public key can be shared openly without risk. |
| Primary Use | Bulk data encryption (VPN traffic, file encryption). | Secure key exchange, digital signatures, and start secure sessions. |
4. The decryption process in action in security tools
Decryption isn’t just a theoretical concept from a cryptography textbook. It’s a critical process happening thousands of times a day on your devices, often without you even noticing. As someone who analyzes security software, I find it fascinating to see how these elegant mathematical principles are put into practice to protect us.
Here are a few real-world examples of how decryption works in the tools you might use every day.
4.1. When you use a VPN
This is a perfect example of symmetric encryption and decryption at work.
- Encryption: Before any data leaves your computer, your VPN app uses a powerful symmetric algorithm (like AES-256) and a secret key to encrypt it, turning your request into ciphertext.
- Transmission: This scrambled data travels securely through the internet to the VPN server.
- Decryption: The VPN server holds the same secret key. It performs the decryption process to understand your request (e.g., “I want to visit google.com”).
- Re-Encryption: The server then sends your request to Google. When Google responds, the VPN server encrypts that response and sends it back to you.
- Final Decryption: Your VPN app uses its key to decrypt the response, allowing you to see the Google homepage on your screen. This all happens in a fraction of a second.
4.2. When you use a password manager
Your password vault is a masterclass in data security and local decryption.
- The entire vault of your saved logins is stored on the provider’s servers (and synced to your devices) as a single, heavily encrypted block of ciphertext.
- When you type in your master password, you are essentially providing the final piece of the decryption key.
- The app then performs the decryption locally on your device, unlocking the vault so you can see your plaintext passwords. The provider never sees your master password and never has the key to decrypt your vault.
4.3. When you receive an end-to-end encrypted message
This is a beautiful combination of both methods.
- Asymmetric Encryption: When you first start a chat, your apps use an asymmetric (public/private key) system to securely exchange secret symmetric keys. These symmetric keys are then used for the remainder of the conversation.
- Symmetric Encryption: The actual messages you send are then encrypted and decrypted using these fast, efficient symmetric keys.
- Decryption on Your Device: A message arrives on your phone as unreadable ciphertext. The app uses the private key stored securely on your device to perform the final decryption, turning it back into readable text. Only your device and the sender’s device have the keys.
Safelyo’s Expert Insight: The Key is Everything
While we talk about powerful encryption algorithms, it’s crucial to remember that the entire security of the system rests on the secrecy and strength of the decryption key. A complex lock is useless if you leave the key under the doormat. This is why using a strong master password for your password manager or protecting your device’s private keys is so critical. The decryption algorithm is the unbreakable vault; the key is what you must protect at all costs.
5. FAQ about decryption
We’ve unlocked the basics of decryption, but you might still have a few questions. Here are short, direct answers to the most common queries we receive.
What is the decryption?
Decryption is the process of converting data that has been made unreadable through encryption (ciphertext) back into its original, readable form (plaintext). It is the essential final step in any secure communication cycle, making protected information usable again.
What is encryption and decryption?
They represent two sides of the same coin in cryptography. Encryption involves “locking” data by scrambling it with a key, while decryption is the process of “unlocking” the scrambled data using the correct key to restore readability. One safeguards data, while the other allows access.
What happens when you decrypt?
When you decrypt data, an algorithm uses a specific decryption key to reverse the mathematical operations that were applied during encryption. This systematically unscrambles the ciphertext, reorganizing it back into the original plaintext so that it can be read and understood by a person or a computer program.
What is a decryption example?
A simple decryption example happens every time you visit a secure website. When you go to your online banking page (an HTTPS site), the data sent from the bank’s server to your browser is encrypted. Your browser then performs decryption using a shared secret key, turning the scrambled website code back into the visual webpage you can interact with.
What is cryptography?
What is cryptography? It’s the broad science of secure communication techniques. It includes both encryption (locking information) and decryption (unlocking it), as well as other methods like digital signatures to verify identity and key exchange protocols to share keys safely.
Can something be decrypted without the key?
For modern encryption algorithms like AES, it is practically impossible. Attempting to guess the key is called a “brute-force attack,” and for a standard AES-128 key, it would take the world’s fastest supercomputers billions of years to succeed.
Is decryption the same as decoding?
No, decoding refers to converting data from one format to another (like Morse code to English). This process uses publicly available methods and does not require a secret key. In contrast, decryption involves unscrambling data that has been intentionally concealed and necessitates a secret decryption key for success.
6. Conclusion
In the end, decryption transforms an unreadable, locked box of data into a useful message. This process is only accessible to the person who holds the correct key. It is the necessary counterpart to encryption, completing the cycle that makes a private digital world possible.
- Decryption is the process of converting ciphertext back into plaintext.
- It is the counterpart to encryption, completing the cycle of secure communication.
- It always requires a decryption key and a specific decryption algorithm.
- It’s a fundamental decryption process that powers the security of your VPN, password manager, and messaging apps.
Understanding decryption helps you appreciate the incredible technology working silently in the background to protect your cybersecurity and privacy every single day.
Now that you understand how your data is unlocked safely through the article of Safelyo above. Explore the guides on the best tools that use this technology, like our reviews of the top VPNs and password managers in our Privacy & Security Basics section.