If you have ever hesitated before clicking a suspicious link in an email, you have already faced the risk of phishing.
This article explains what is phishing in simple terms and shows how it has evolved in 2025. You will discover:
- The exact meaning and definition of phishing
- How attackers use new tricks such as QR codes, deepfakes, and MFA fatigue
- The main types of phishing attacks targeting both individuals and businesses
- Warning signs that help you spot a phishing attempt early
- Prevention steps and recovery actions you can apply at home and at work
With that foundation, let’s begin by answering the most important question “What is phishing?”
1. What is phishing?
At its core, what is phishing in cyber security? It’s a social engineering cyberattack that tricks people into revealing sensitive data (passwords, card numbers), installing malware, or sending money.
As CISA puts it, “Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization.” (CISA, 2021).
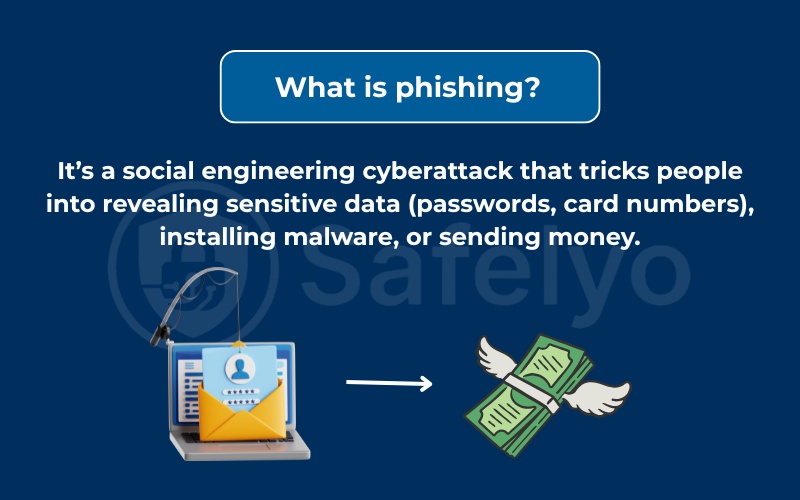
Phishing meaning in practice: attackers impersonate trusted brands, colleagues, or services to trick victims. The goal can be to gain direct access to money, plant malware, or prepare a larger cyberattack such as ransomware.
Before we move on, here’s a fast way to anchor the concept:
- Common goals: credential theft, account takeover, identity theft, monetary theft, credit card fraud and staging ransomware or a data breach.
- Common channels: email phishing (the classic “verify your account”), texts (smishing), calls (vishing), social DMs, help-desk chats, and physical posters with QR codes.
- Why it works: persuasive pretexts, spoofed domains, and pressure tactics that override caution.
You’ll also see the term “what is phishing attack” or “what is phishing scams” used interchangeably with phishing; both describe the same deception-driven technique.
Read more:
2. How phishing works today
Phishing has adapted to modern defenses. Attackers no longer rely only on poorly written spam emails. Instead, modern phishing techniques combine psychological manipulation with technical tricks to bypass filters and fool even experienced users.
Many campaigns are automated, highly targeted, and supported by underground phishing-as-a-service kits.
2.1. How social engineering tricks users
At the heart of phishing is social engineering. Criminals know that the weakest link in cybersecurity is often human error. They create believable stories that pressure people into quick action.
A few common pretexts include:
- Fake security alerts from banks or cloud providers
- HR messages about salary or benefits
- Urgent requests from a “manager” to process payments
When users feel rushed or afraid, they are more likely to click links or download attachments without checking carefully.
2.2. Spoofing and fake domain tactics
Phishers often build look-alike websites with domains such as microsoftsupport-login.com or paypa1.com. These mimic trusted services but harvest credentials.
Attackers also manipulate email headers to make messages appear as if they came from a genuine source.
According to ENISA’s 2023 Threat Landscape Report, domain spoofing remains one of the most persistent phishing vectors across Europe.
2.3. SPF, DKIM, DMARC, and BIMI
To fight spoofing, companies use email authentication protocols:
- SPF (Sender Policy Framework): verifies sending servers
- DKIM (DomainKeys Identified Mail): attaches cryptographic signatures
- DMARC: enforces rules for handling failed checks
- BIMI: displays brand logos in supported inboxes
When properly implemented, these measures block many fraudulent emails. However, misconfigured policies are still common, leaving gaps that attackers exploit.
2.4. Adversary-in-the-middle (AiTM) proxies
A more advanced method is the AiTM proxy attack. Here, victims are directed to a malicious site that relays traffic to the legitimate service.
The login process appears normal, but every credential or MFA code entered is captured in real time. This allows criminals to hijack sessions without ever “breaking” the authentication system.
2.5. OAuth consent phishing and token theft
Instead of stealing passwords, attackers sometimes abuse OAuth apps. They create a fake application and trick users into granting it permissions like reading emails or accessing files.
Once the victim clicks “Allow,” the attacker gets a valid access token. With that token, they can operate invisibly inside the account until the consent is revoked. This technique is especially dangerous in Microsoft 365 and Google Workspace environments.
2.6. MFA fatigue (push bombing) attacks
Multi-factor authentication (MFA) helps, but it is not perfect. Attackers may flood a victim with repeated push notifications until the person, annoyed or exhausted, clicks “Approve” just to stop the noise.
This method, called MFA fatigue or push bombing, shows that even strong technology can fail when combined with human impatience.
2.7. Quishing: malicious QR codes
Quishing is a newer technique that uses malicious QR codes. These may be embedded in phishing emails, sent in chat apps, or even printed on posters in public spaces.
When scanned, the QR code leads to a fake login page. Because QR codes look harmless and are hard to verify at a glance, users often trust them without suspicion.
2.8. Phishing with deepfakes and voice clones
The rise of AI-generated content has introduced new risks. Attackers can now create convincing deepfake videos or clone voices of executives.
Imagine receiving a video message from your “CEO” instructing you to urgently wire funds.
According to Wired (2024), such AI-assisted phishing has already caused multimillion-dollar corporate fraud losses.
Read more:
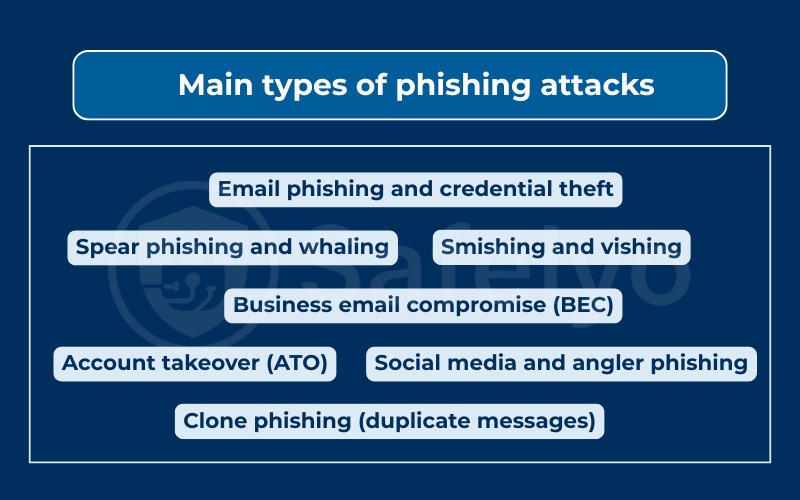
3. Main types of phishing attacks
Phishing has evolved into many subcategories. Each type uses a different channel or tactic, but the objective is the same: trick the victim into giving up sensitive data, money, or system access. Below are the most common variants you should know about.
3.1. Email phishing and credential theft
What is phishing in email? It is the classic and most widespread form of phishing. Attackers send fraudulent emails that appear to come from well-known brands, banks, or online services.
These emails often include:
- A fake login link (e.g., Microsoft 365 or PayPal)
- A malicious attachment that installs malware
- A spoofed sender address that looks authentic at first glance
When a user clicks the link and enters login details, the attacker collects the credentials. Those stolen credentials can then be used for account takeover, data breaches, or even ransomware deployment.
Example: a “security alert” email from “Google” asking you to re-enter your account password to prevent suspension.
3.2. Spear phishing and whaling
What is spear phishing? It is a more advanced and targeted form of phishing. Instead of sending thousands of random emails, the attacker researches one specific person and crafts a personalized message.
The attacker might mention a recent project, a colleague’s name, or even the victim’s phone number to appear legitimate. These details make spear phishing emails much harder to recognize.
Whaling is spear phishing aimed at high-level executives such as CEOs, CFOs, or board members. Since these individuals often have authority to approve financial transfers, a single successful attack can cause massive financial losses.
Example: a fake invoice sent to a company’s CFO, with the attacker pretending to be the CEO requesting urgent payment.
3.3. Business email compromise (BEC)
BEC attacks combine phishing with account hijacking. Criminals first compromise a company’s email account (for example, through stolen credentials). They then use that account to send convincing payment requests to finance staff or business partners.
Because the message comes from a legitimate account, employees are more likely to trust it. According to the FBI’s Internet Crime Report (2023), BEC schemes have led to billions of dollars in reported losses globally.
Example: an accounts payable team receives an email from a real vendor’s address, instructing them to update the bank account details for future payments.
3.4. Account takeover (ATO)
Phishing often leads directly to account takeover. Once criminals steal login details, they log into the victim’s email, social media, or banking account.
From there, they may:
- Change passwords to lock out the owner
- Use stored payment information for fraudulent purchases
- Send phishing messages to the victim’s contacts to spread the attack further
This creates a cycle where one compromised account can lead to many more.
3.5. Smishing and vishing
What is smishing? It is phishing carried out via SMS text messages. Victims receive a message that looks like a delivery notice, a tax refund, or a banking alert. The text includes a shortened link that leads to a malicious site.
What is vishing? It is phishing conducted over voice calls. Attackers pretend to be bank agents, IT staff, or even government officials. They pressure victims into sharing MFA codes, passwords, or financial information.
Both methods are powerful because many people inherently trust phone messages more than emails. With mobile phones now being the primary communication tool, smishing and vishing continue to rise sharply.
Example: a text claiming to be from a postal service with a link to “pay a small delivery fee,” which actually steals credit card details.
3.6. Social media and angler phishing
What is angler phishing on social media? It is when attackers impersonate customer support or brand accounts to trick users on platforms like Facebook, Instagram, or X (formerly Twitter).
This type of scam often targets people who have already posted complaints or support requests. A fake “support account” then contacts the victim, asking for login details or payment information to “resolve” the issue.
Example: after tweeting about a banking issue, a victim receives a DM from a fake “Bank Support” account with a phishing link.
3.7. Clone phishing (duplicate messages)
What is clone phishing? It is a subtle attack where criminals copy a legitimate email the victim has already received but replace the original link or attachment with a malicious one.
Because the email looks familiar and often comes from a spoofed sender that appears trusted, victims are much more likely to click without hesitation.
Example: a user receives a second copy of a conference registration email but this time the “Download Schedule” button leads to malware.
See also:
4. What are the signs of phishing?
Spotting phishing early is the best defense. Attackers rely on victims overlooking small details or reacting emotionally. By learning the common red flags, you can pause before clicking and avoid falling into a trap.
4.1. Psychological pressure: urgency and fear
Most phishing attempts create psychological pressure. The attacker wants you to panic and act quickly.
Typical phrases include:
- “Your account will be suspended in 24 hours.”
- “Immediate action required to avoid fees.”
- “Confirm your identity now to continue service.”
When you feel rushed, it is easier to make mistakes. This manipulation is a classic social engineering tactic.
4.2. Suspicious senders and domains
Always check the sender’s email address carefully. A phishing message might look like it is from “support@paypa1.com” instead of “support@paypal.com.”
Even small typos or extra characters in a domain name can reveal a scam. Attackers also use free mail services (like Gmail or Outlook) to impersonate corporate addresses.
4.3. Link and attachment anomalies
Phishing often hides danger in links and attachments. Hovering over a link can reveal a mismatched URL that points somewhere completely different.
Common examples include:
- Links that lead to domains with strange endings, such as .xyz or .top
- Attachments disguised as invoices or resumes but actually containing malware
If the file format is unusual (e.g., .exe or .scr), treat it as a red flag.
4.4. Payment or data requests
Be cautious if an email asks for credit card details, login credentials, or wire transfers. Legitimate companies rarely request sensitive data through email or SMS.
For businesses, attackers may pretend to be a supplier asking to “update” bank details. This is a hallmark of business email compromise (BEC) scams.
4.5. Generic greetings and language mistakes
Professional organizations usually address customers by name. A message that starts with “Dear user” or “Dear valued customer” should raise suspicion.
Spelling mistakes, poor grammar, or odd phrasing are also strong indicators. While advanced attackers now use AI to write polished text, language quality is still a useful signal, especially when combined with other red flags.
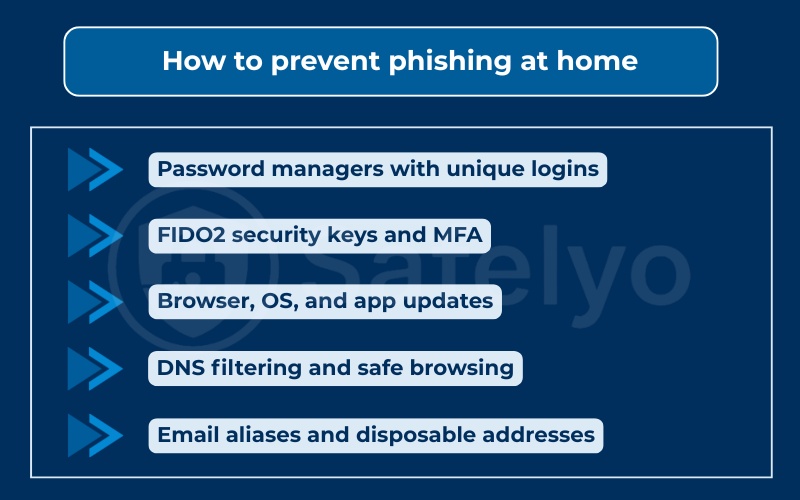
5. How to prevent phishing at home
Phishing attacks at home usually target individuals who don’t have enterprise-grade protections. But that doesn’t mean you are defenseless. By combining the right tools with smarter online habits, you can make it much harder for attackers to succeed.
5.1. Password managers with unique logins
One of the biggest risks in phishing is password reuse. If you use the same password for your email, online banking, and shopping sites, a single stolen credential can lead to multiple account takeovers.
A password manager solves this by:
- Generating random, complex passwords for every account
- Storing them securely in an encrypted vault
- Auto-filling logins on legitimate sites only
Example: I tested Bitwarden and LastPass on my laptop. Both flagged when I tried to enter my credentials on a fake PayPal site because the domain did not match the saved one.
5.2. FIDO2 security keys and MFA
Multi-factor authentication (MFA) adds an extra layer beyond passwords. However, not all MFA is equal. SMS codes can be intercepted or stolen by attackers using MFA fatigue or SIM swapping.
The most secure option for home users is a FIDO2 hardware security key such as YubiKey or Google Titan. These keys confirm the real website’s domain using cryptographic checks before approving login.
This means:
- If you accidentally click a phishing link, the fake website cannot trigger a valid login
- Even stolen passwords are useless without the physical key
For less critical accounts, using app-based authenticators (Google Authenticator, Authy, Microsoft Authenticator) is still far safer than SMS codes.
5.3. Browser, OS, and app updates
Phishing sometimes delivers malware through attachments or drive-by downloads. Outdated software is an easy target.
Best practices include:
- Enable automatic updates on Windows, macOS, iOS, and Android
- Keep browsers like Chrome, Firefox, or Edge updated since they block known phishing domains in real time
- Update apps regularly, especially financial, email, and messaging apps
Example: Chrome’s “Enhanced Safe Browsing” mode proactively warns if you type credentials on a suspected phishing page. I enabled it during testing and it successfully blocked a fake Dropbox login site.
5.4. DNS filtering and safe browsing
Another strong layer is DNS filtering. Tools like OpenDNS (Cisco), Cloudflare Family, or NextDNS block access to domains flagged as phishing or malware sites.
Advantages:
- Protection applies across all devices connected to your Wi-Fi, including smart TVs and IoT gadgets
- Prevents your browser from even loading a malicious page
- Gives parents control to protect children from scam sites
If you cannot set up custom DNS, enabling built-in protections like “Safe Browsing” in Chrome or “Enhanced Tracking Protection” in Firefox also adds a safeguard.
5.5. Email aliases and disposable addresses
Using your main email address everywhere increases the risk of being added to phishing lists after a data breach.
Solutions include:
- Email aliases from services like SimpleLogin, DuckDuckGo Mail Protection, or Apple’s Hide My Email
- Disposable email addresses for one-time sign-ups, contests, or shopping deals
Example: I created a disposable alias for a free e-book download. A month later, that alias started receiving suspicious “update your account” phishing emails. Since it was not my main email, I simply disabled it and avoided exposure.
6. How to prevent phishing at work
Phishing at the workplace can have devastating consequences, from stolen employee credentials to multimillion-dollar business email compromise (BEC) fraud. Unlike at home, organizations need layered defenses that combine technology, policy, and human training.
6.1. Security awareness and user training
Employees are the first line of defense. A well-designed security awareness training program helps staff recognize red flags such as urgent payment requests, spoofed domains, or unexpected attachments.
Best practices include:
- Simulated phishing campaigns to test employee responses
- Short, recurring training sessions rather than long, one-time workshops
- Clear reporting channels (e.g., a “Report Phish” button in Outlook or Gmail)
6.2. Email gateways and sandboxing
Secure email gateways (SEGs) filter malicious emails before they reach inboxes. They analyze sender reputation, scan attachments, and detect links to suspicious domains.
Adding sandboxing allows attachments and links to open in a controlled environment. If malware executes, it is contained without infecting the real system.
Vendors like Proofpoint, Mimecast, and Microsoft Defender for Office 365 are commonly used in enterprises.
6.3. Zero trust and least privilege
Adopting a Zero Trust security model means that no user or device is automatically trusted, even inside the corporate network.
Key principles:
- Continuous verification of user identity and device health
- Least privilege access, granting employees only the resources they truly need
- Segmentation to limit lateral movement if an account is compromised
This approach ensures that even if phishing succeeds, the damage is contained.
6.4. EDR, SIEM, and SOAR integrations
Modern enterprises use advanced monitoring tools:
- EDR (Endpoint Detection & Response): Detects malicious behavior on laptops, desktops, and mobile devices.
- SIEM (Security Information and Event Management): Centralizes logs to spot suspicious activity across the network.
- SOAR (Security Orchestration, Automation, and Response): Automates responses to phishing alerts, such as blocking domains or isolating endpoints.
For example, if a phishing email delivers malware, the EDR agent can isolate the affected machine while SOAR workflows notify IT and revoke access tokens.
6.5. DMARC enforcement and monitoring
Organizations should enforce DMARC (Domain-based Message Authentication, Reporting & Conformance). Together with SPF and DKIM, DMARC prevents attackers from spoofing the company’s domain.
Benefits:
- Protects both employees and customers from fake emails pretending to be the company
- Provides reports so IT teams can monitor attempted spoofing campaigns
- Builds trust when customers see authenticated emails with BIMI brand logos
Companies that fully enforce DMARC reduce phishing attempts that abuse their domain, which strengthens overall brand reputation.
These measures form the backbone of organizational phishing prevention.
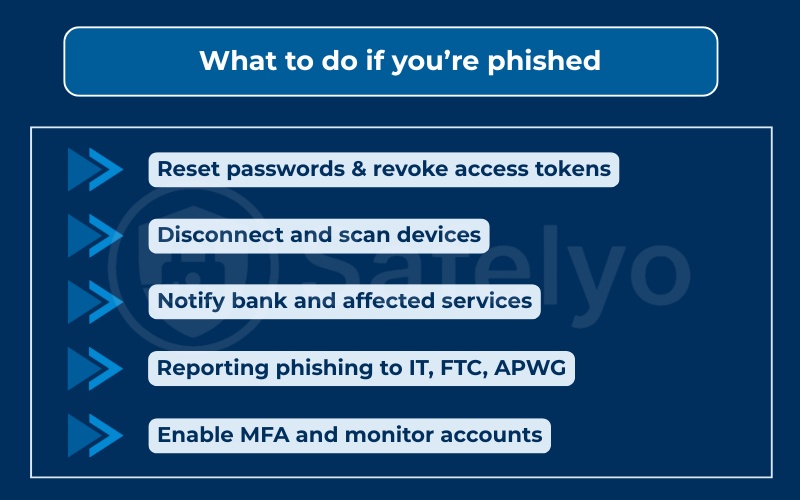
7. What to do if you’re phished
Even with the best defenses, phishing can still succeed. The key is to respond quickly to limit damage. The first 24 hours are critical because attackers often act immediately once they gain access.
7.1. Reset passwords & revoke access tokens
If you entered your password on a phishing site, change it immediately. Start with your email account, since attackers often use it to reset other logins.
For accounts connected through OAuth apps (Google, Microsoft 365, Facebook), check for any suspicious third-party applications and revoke their access tokens.
7.2. Disconnect and scan devices
If you downloaded an attachment or clicked on a suspicious link, disconnect the device from Wi-Fi or Ethernet. This prevents malware from calling back to its command-and-control server.
Next, run a full antivirus or EDR scan to detect and remove malware. For Windows users, Microsoft Defender provides real-time scanning, while Mac and Linux users can use tools like Malwarebytes or ClamAV.
7.3. Notify bank and affected services
If you entered financial information such as credit card or banking details, contact your bank immediately. They can:
- Freeze your account
- Issue new cards
- Monitor transactions for fraudulent charges
Banks can freeze your card to prevent credit card fraud and reissue secure replacements.
For online accounts (PayPal, Amazon, Netflix), log in through the official website, reset your password, and check for unauthorized activity.
7.4. Reporting phishing to IT, FTC, APWG
Reporting helps stop the attacker and protects others. Depending on your situation:
- At work: report to your IT or security team immediately
- In the US: forward phishing emails to phishing@apwg.org (Anti-Phishing Working Group) or report at reportphishing.ftc.gov
- In the EU/UK: report to your local cybersecurity agency (e.g., ENISA, NCSC UK)
According to CISA (2024), timely reporting allows organizations to block phishing infrastructure before it reaches more victims.
7.5. Enable MFA and monitor accounts
Once passwords are reset, enable multi-factor authentication (MFA) on all critical accounts. This adds an extra barrier if attackers still have your credentials.
Finally, monitor your accounts for unusual activity such as login attempts from new locations, password reset emails, or unexpected notifications. Many providers allow you to review recent login sessions and sign out remotely.
8. Phishing trends in 2025
Phishing has moved far beyond fake emails with spelling errors. Criminal groups are now using artificial intelligence, hybrid campaigns, and deepfake technology to launch attacks that look genuine and are much harder to detect. Staying updated on these trends is critical for both individuals and organizations.
8.1. AI phishing and defenses
Generative AI tools allow attackers to create fluent, professional-looking phishing emails in many languages. Victims no longer see the obvious mistakes that once gave scams away.
AI is also used to:
- Personalize emails with information gathered from LinkedIn or social media
- Generate hundreds of unique phishing messages to bypass spam filters
- Build fake chatbots that imitate customer support to steal credentials
Defenders are responding with AI-powered security. Platforms like Microsoft Defender, Google Workspace security, and Proofpoint analyze email tone, context, and intent rather than relying only on keywords.
8.2. Hybrid vishing and multichannel campaigns
Attackers often combine multiple channels in the same phishing attempt. This makes the scam appear more coordinated and therefore more believable.
A typical sequence could be:
- The victim receives a phishing email with a fake invoice
- A follow-up vishing call pretends to be company support, urging action
- A smishing text message provides a “direct link” to reinforce the deception
This kind of multichannel pressure tricks many users into compliance. According to Dark Reading (2024), hybrid phishing campaigns have doubled within the last two years.
8.3. Deepfakes in social engineering
One of the most alarming developments is the use of deepfake audio and video. Attackers can now clone a voice using just a few minutes of recorded audio.
For example, a scammer might call an employee with a voice that sounds exactly like their CEO, asking for an urgent transfer. In more advanced cases, criminals use real-time deepfake video calls that mimic the face of a trusted manager.

Deepfake audio can also be used for extortion, pressuring employees into releasing confidential information.
According to Wired (2024), several European businesses have already lost millions due to scams that used AI-cloned voices to demand wire transfers.
8.4. Quishing and visual deception
Quishing uses malicious QR codes placed in emails, flyers, or invoices. Because QR codes are familiar and often trusted, victims scan them without thinking. The scan then leads to a fake login page designed to capture credentials.
Attackers also experiment with deceptive visuals such as CAPTCHA-style phishing pages and fake login screens that closely imitate real applications. These tricks bypass automated filters and increase the chance of success.
9. Tools and resources
Protecting against phishing requires both the right security tools and reliable sources of information. Below is a practical list that home users and organizations can use to strengthen defenses.
Security tools
- Password managers such as Bitwarden, 1Password, or KeePass help prevent password reuse. If one account is compromised, unique credentials ensure other accounts stay safe.
- FIDO2 hardware security keys like YubiKey or Google Titan provide phishing-resistant MFA. These devices verify that you are logging in to the legitimate website before approving access.
- DNS filtering services including Cisco Umbrella (OpenDNS), NextDNS, or Cloudflare DNS block access to known phishing and malware domains at the network level.
- Endpoint protection and antivirus software such as Microsoft Defender or Bitdefender add another layer of defense by scanning attachments and links for malicious activity.
- Built-in browser protections like Google Chrome’s Safe Browsing, Microsoft Edge SmartScreen, and Firefox Enhanced Tracking Protection automatically warn users about suspected phishing sites.
Learning and awareness resources
- CISA Phishing Guidance (2023): step-by-step advice for reducing phishing risks at both personal and organizational levels.
- NIST Digital Identity Guidelines (SP 800-63B): official US standards recommending phishing-resistant authentication such as FIDO2 keys.
- ENISA Threat Landscape Reports: yearly insights into European cybersecurity, including phishing attack trends.
- FTC Consumer Alerts: frequent warnings about new scams targeting US consumers.
- APWG Phishing Activity Trends Reports: global statistics and analysis on phishing incidents.
Reporting channels
- Forward suspicious emails to phishing@apwg.org for analysis by the Anti-Phishing Working Group.
- Report scams to reportphishing.ftc.gov if you are in the United States.
- Use built-in reporting features such as Gmail’s Report phishing or Outlook’s Report message to alert providers.
- Contact your national cybersecurity authority (for example, NCSC UK, CERT-EU, or CISA in the US) if you suspect a large-scale or corporate phishing incident.
10. FAQs about what is phishing
Many people have the same questions about phishing. Below are concise answers that clear up common confusion.
Is phishing only done by email?
No. While email phishing is the most common, phishing can also appear in text messages (smishing), phone calls (vishing), social media DMs, QR codes (quishing), and even fake chatbots. Attackers adapt to whichever channel people trust most.
Can MFA stop phishing completely?
Not always. Multi-factor authentication (MFA) makes phishing harder, but attackers use tactics like MFA fatigue or adversary-in-the-middle proxies to bypass it. The most effective solution is phishing-resistant MFA, such as FIDO2 hardware keys, which verify the real website before approving login.
What is consent phishing?
Consent phishing is when attackers trick you into granting permissions to a fake app. Instead of stealing your password, they use OAuth access tokens to read emails or files directly. Always check which app is requesting access before clicking “Allow.”
How does DMARC stop phishing?
DMARC (Domain-based Message Authentication, Reporting & Conformance) prevents attackers from sending emails that pretend to be from your company’s domain. When combined with SPF and DKIM, it blocks spoofed messages and gives IT teams reports about suspicious activity.
What should I do right after clicking a link?
If you click a phishing link:
- Do not enter any information.
- Disconnect your device from the internet.
- Run a full antivirus or endpoint protection scan.
- Reset any passwords that might be exposed.
- Report the attempt to your email provider or IT team.
Quick action reduces the risk of account takeover or malware infection.
11. Conclusion
Understanding what is phishing is the first step in protecting yourself and your organization. Attacks today are more advanced, but the fundamentals remain the same: criminals exploit trust, urgency, and human error.
Key takeaways:
- Phishing uses social engineering to steal data, money, or account access
- Modern techniques include AI-written emails, quishing, MFA fatigue, and deepfakes
- Red flags include urgent messages, spoofed domains, suspicious links, and generic greetings
- Protection requires password managers, phishing-resistant MFA, DNS filtering, and regular updates
- Quick recovery steps include resetting passwords, scanning devices, contacting banks, and reporting incidents
From my own experience, I once received a fake Dropbox email that looked completely real at first glance. The only giveaway was the sender’s domain, which didn’t match the official site. Catching that detail saved me from entering my credentials on a cloned login page.
By applying the defenses covered here, you can avoid becoming the next victim of phishing scams. Stay alert, verify before you click, and use tools that give you extra protection.
For more practical guides on protecting your devices, explore the Antivirus section at Safelyo, where we explain how security software and smart practices work together to keep you safe online.








