Many people worry about privacy on their devices, but signs of monitoring are often subtle and easy to miss. Hackers, employers, or even family members could be tracking your activity without your knowledge. This guide will show you how to know if your computer is being monitored, including the warning signs of spyware and suspicious activity. It also covers tools to detect threats and practical steps to protect your personal data.
Here’s what you’ll discover in this guide:
- Identify common warning signs such as unusual system performance, unexpected pop-ups, and unknown programs.
- Learn to detect spyware and remote monitoring software using built-in tools and antivirus programs.
- Discover proactive measures to protect your privacy and secure your computer from unauthorized access.
Keep reading to learn how to detect any monitoring on your computer and take control of your privacy before sensitive information is compromised.
1. Why you might be concerned about computer monitoring
Monitoring can happen for many reasons, ranging from legitimate workplace oversight to unauthorized access by hackers or even people you know. Understanding why someone might monitor your computer helps you take the right precautions and protect sensitive data such as passwords, personal files, or financial information. By being aware of the risks, you can act early to secure your system and prevent data theft or misuse.
Common reasons your computer may be monitored:
- Employers tracking activity on work devices: Many companies install monitoring software to ensure productivity, track emails, or monitor internet usage. While this may be legitimate on company-issued devices, it highlights the importance of separating personal data from work systems.
- Hackers or cybercriminals installing spyware: Malicious actors may use spyware, keyloggers, or remote access tools to steal sensitive information like login credentials, banking details, or personal documents. They often use social engineering tactics, such as phishing emails, to trick you into installing malicious software. This type of monitoring is illegal and can have severe financial and privacy consequences, and even lead to identity theft
- Family members or roommates monitoring usage: Sometimes, monitoring occurs within a household, intentionally or not, to keep track of children, shared computers, or cohabitants. While the intent may not always be malicious, it can still compromise your privacy.
- Remote access tools or keyloggers capturing sensitive information: Spyware can record keystrokes, capture screenshots, or transmit files remotely without your knowledge. These programs often run silently in the background, making them difficult to detect until noticeable signs appear, such as slow performance or unexpected pop-ups.
2. How to know if your computer is being monitored
Monitoring software can often run silently in the background, making it hard to detect. However, several warning signs can reveal its presence. Paying attention to these signals early helps protect your sensitive data and prevent unauthorized access.
2.1. Rapid battery drain on your laptop
If your laptop battery suddenly drains much faster than usual, hidden monitoring software could be running in the background. Spyware often transmits data continuously, even when your device seems idle. Consistent rapid battery depletion may indicate unauthorized activity that consumes significant power.
2.2. Frequent overheating of your computer
Unexpected overheating of your CPU or GPU can suggest that hidden tasks are running without your knowledge. Monitoring software often increases system load, causing your device to heat up more than normal. If your computer gets hot even during light use, it’s a potential warning sign.
2.3. Applications behaving unusually
Apps that crash, freeze, or open unexpected windows may be manipulated by spyware or malware. Malicious software can interfere with legitimate programs to hide its activities. Observing repeated or strange app behavior can help you identify potential monitoring.
2.4. Overall system running slowly
A sluggish system, delayed commands, or unusually long boot times may indicate hidden processes consuming CPU or memory. Spyware and remote access tools often operate in the background, affecting system performance. Monitoring resource usage can help detect these unauthorized activities.
2.5. Webcam activating without consent
If your webcam light turns on unexpectedly, it could mean spyware is accessing your camera without permission. Covering your webcam when not in use and checking app permissions regularly can prevent unauthorized recordings. Any unexplained activation should be treated as a serious privacy concern.
2.6. Lights blinking unexpectedly
Random flickering of hard drive or network lights can indicate active data transmission to external sources. Monitoring software frequently sends collected information without your knowledge. Consistent, unexplained activity from these indicators is a red flag.
2.7. Frequent and odd pop-up messages
Unexpected pop-ups may be attempts by malware to communicate, trick you into downloading additional malicious software, or steal information. Avoid interacting with unknown prompts and run an immediate antivirus or anti-malware scan. These messages often signal ongoing monitoring or infection.
2.8. Unexpected changes to your homepage
If your browser homepage or search engine changes without your input, spyware or adware may be responsible. Regularly reviewing settings and removing unfamiliar extensions helps you maintain control. Such unauthorized changes are a common tactic to track browsing behavior.
2.9. Browser automatically redirecting websites
Frequent redirects to unexpected websites can indicate browser hijacking or malware infection. This behavior may compromise personal data or download additional threats. Monitoring these redirects is crucial to protect your privacy and prevent further infections.
2.10. Unfamiliar programs appearing on your PC
Programs you didn’t install could be spyware, keyloggers, or remote access tools. Regularly checking your software list and uninstalling suspicious apps helps maintain system security. Unknown applications running in the background are a major indicator of unauthorized monitoring.
2.11. Suspicious activity in your web browser
Unexpected logins, toolbar additions, or search engine changes may signal monitoring activity. Spyware can alter your browser to track behavior or steal sensitive information. Regularly reviewing extensions, active sessions, and browser settings helps detect unauthorized activity.
2.12. Notifications of ransomware or malware attacks
Alarming pop-up messages may indicate active malware or ransomware infections. Only rely on trusted antivirus tools to scan your system, as interacting with these alerts can worsen the problem. Early detection is key to preventing data theft or permanent damage.
2.13. Task Manager or Activity Monitor not working
If Task Manager (Windows) or Activity Monitor (Mac) is disabled, spyware may be hiding its processes from detection. Using safe mode or external security tools can help identify hidden threats. Preventing access to these monitoring tools is a common tactic used by malicious software.
2.14. Programs launching on their own
Applications starting automatically without your consent may indicate remote access software. This can include legitimate tools like a remote desktop connection being abused for unauthorized access. Regularly check startup items, scheduled tasks, and background services for unauthorized entries. Programs that launch on their own often signal someone is monitoring or controlling your computer remotely.
3. How to detect and remove spyware on your computer
Detecting spyware requires a combination of manual checks and trusted software. Following these steps can help identify and remove monitoring tools before they compromise your data.
3.1. Check for suspicious processes through Task Manager
Monitoring your computer for unusual processes is a key step in detecting spyware. Spyware often runs quietly in the background, consuming resources while stealing data. By reviewing active processes, you can spot suspicious activity and take action before your information is compromised.
Check for suspicious processes on Windows
- Press Control + Shift + Escape to open Task Manager.
- Look through the list of running processes and note any programs using unusually high CPU, memory, or disk resources.
- Research unfamiliar process names online to determine whether they may be malicious.
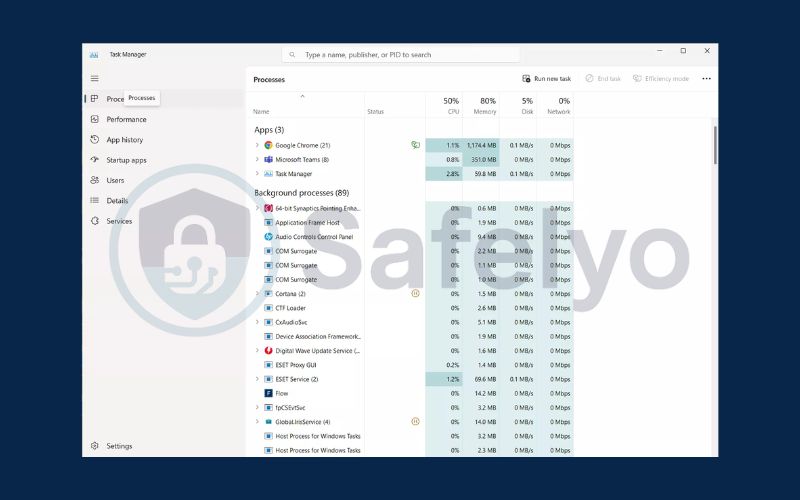
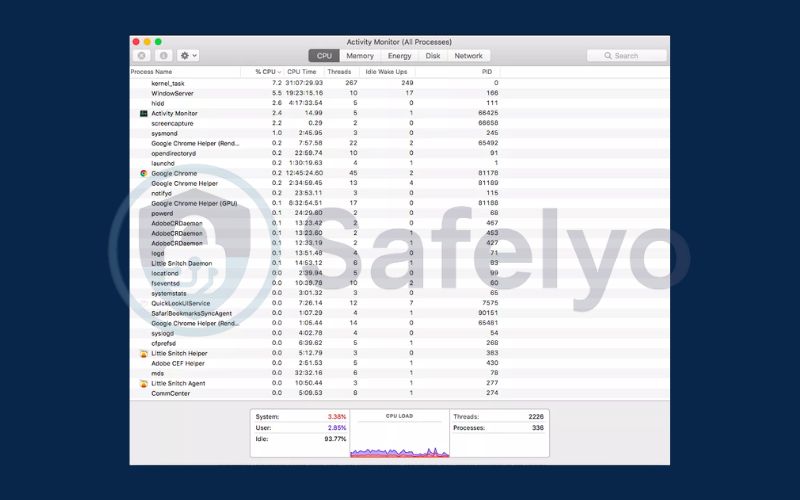
Check for suspicious processes on macOS
- Press Command + Spacebar to open Spotlight, then search for Activity Monitor.
- Open Activity Monitor and review the processes consuming the most CPU or memory.
- Verify any unknown or suspicious process names to identify potential spyware or unauthorized applications.
3.2. Use a trusted antivirus
Installing reliable antivirus software is one of the most effective ways to detect and remove spyware, malware, and other monitoring tools from your computer. A trusted antivirus provides real-time protection, scans your system for threats, and can prevent unauthorized access before it occurs.
Steps to use antivirus software effectively:
- Choose a reputable antivirus program:Select a well-known solution such as Bitdefender, Norton, Kaspersky, or Malwarebytes. Free options can also work, but paid versions often offer more comprehensive protection.
- Install and update the software: Make sure the antivirus is fully updated to recognize the latest threats. Updates include virus definitions and security patches essential for detecting modern spyware.
- Run a full system scan: Perform a deep scan of your entire computer, including all files, folders, and connected drives. Quick scans may miss hidden spyware or keyloggers running in the background.
- Follow the antivirus instructions: Once the scan completes, carefully review detected threats. Use the software to quarantine, remove, or repair infected files as recommended. Do not ignore any alerts, as leftover spyware can continue monitoring your system.
- Schedule regular scans: Set your antivirus to run automatic scans weekly or daily to maintain ongoing protection and catch new threats early.
3.3. View active internet connections
Spyware and monitoring tools often use your internet connection to transmit data without your knowledge. By reviewing active network connections, you can identify unusual activity that may indicate someone is tracking your online behavior. This is an effective step to detect potential spyware or unauthorized programs communicating over the internet.
View active internet connections on Windows
- Press Windows key + R to open the Run dialog box.
- Type resmon and press Enter to launch Resource Monitor.
- Navigate to the Network tab and examine the TCP Connections section.
- Look for unusual or unexpected connections, especially to foreign IP addresses, which could indicate spyware activity.
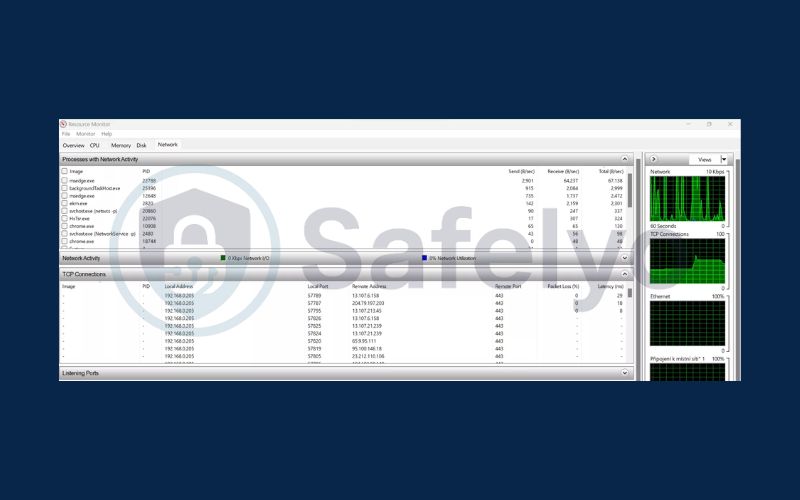
View active internet connections on macOS
- Press Command + Spacebar to open Spotlight and search for Activity Monitor.
- Open Activity Monitor and switch to the Network tab.
- Review all active connections and monitor any suspicious data usage or unknown destinations, which might signal hidden monitoring.
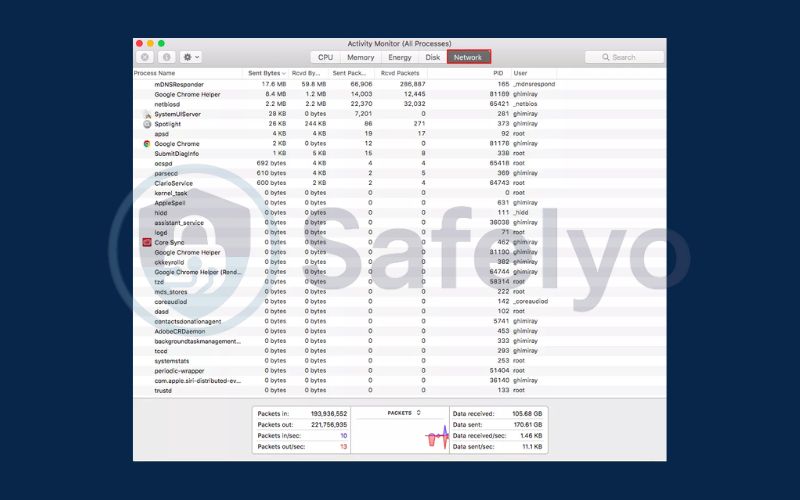
3.4. Watch for open ports
Open ports on your computer act as gateways for internet traffic, but they can also be exploited by hackers if left unsecured. Each application uses specific ports to communicate online, and having unnecessary open ports increases the risk of unauthorized access. Regularly checking your ports helps you spot vulnerabilities before they can be targeted.
Check open ports on Windows
- Press Windows key + R to open the Run dialog box.
- Type resmon and press Enter to launch Resource Monitor.
- Go to the Network tab and locate the Listening Ports section.
- Review the list of open ports and identify any that seem unusual or unnecessary. Close any suspicious ports to reduce your exposure to potential attacks.
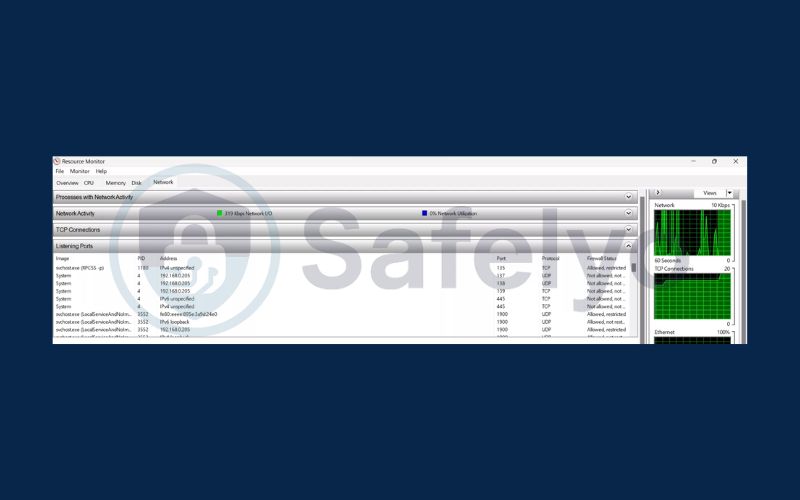
Check open ports on macOS
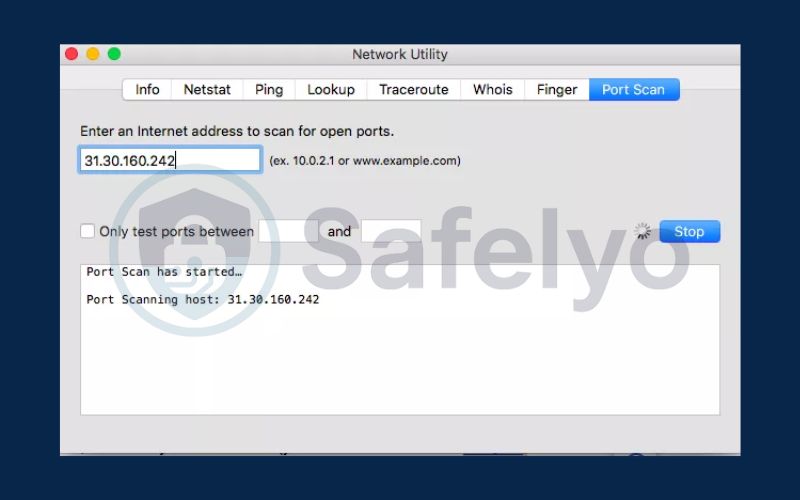
- Press Command + Spacebar to open Spotlight, then search for Network Utility.
- Open Network Utility and navigate to the Port Scan tab.
- Enter your IP address (you can find it using a free online tool) and click Scan.
- After scanning, examine the list of open ports and make note of any unexpected entries. Closing unused ports or configuring a firewall can help prevent unauthorized access.
3.5. Format your hard drive (as a last resort)
If your computer is heavily infected with spyware or other malware, sometimes the most effective way to regain control is to format your hard drive. Spyware can be very difficult to remove completely, and formatting ensures a fresh start by wiping all files, including malicious software, from your system. Before proceeding, make sure you back up any important documents or data, as this process will erase everything on the drive.
How to format a hard drive on Windows
- Press Windows key + X and select Disk Management from the menu.
- In Disk Management, find the drive you want to format.
- Right-click on the drive and choose Format.
- In the formatting window, select the File System (commonly NTFS) and set a Volume Label (the drive’s name).
- Click OK. You will see a warning that all data will be erased, confirm to begin the formatting process.
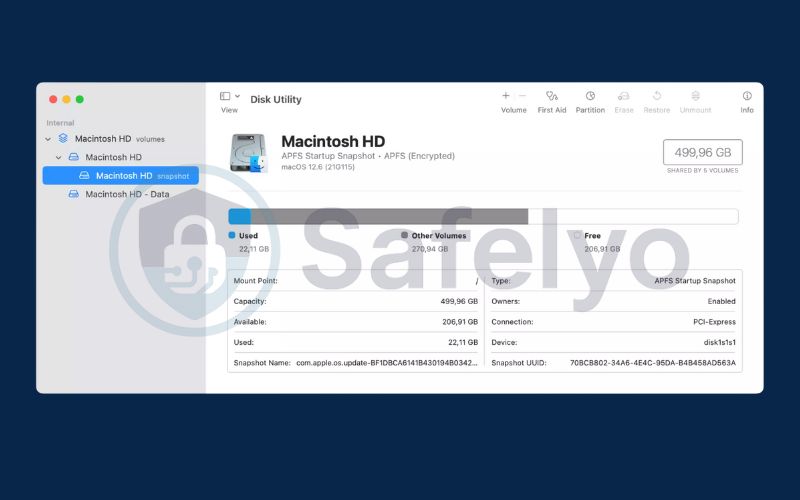
How to format a hard drive on macOS
- Press Command + Spacebar to open Spotlight, then search for and open Disk Utility.
- In Disk Utility, select the drive you wish to format from the left-hand sidebar.
- Click Erase in the top toolbar.
- In the Erase dialog box, choose the format (typically APFS) and set a Volume Name for the drive.
- Click Erase and confirm to start the formatting process. Once complete, your drive will be clean and free of malware.
Read more:
4. How to protect your computer from being monitored
Prevention is the most effective way to safeguard your computer from spyware, hackers, and other monitoring tools. By taking proactive measures, you can significantly reduce the risk of unauthorized access and keep your personal and sensitive information safe. Implementing simple security habits helps ensure your system remains secure without constant worry.
Practical tips to protect your computer:
- Keep your operating system and software updated: Regular updates patch security vulnerabilities that hackers and spyware often exploit. Enabling automatic updates ensures you are protected against the latest threats without needing to remember manual installations.
- Use strong, unique passwords and enable multi-factor authentication: Weak passwords are an easy entry point for intruders. Using complex, unique password manager for each account and adding two-factor authentication adds an extra layer of security, making unauthorized access much harder.
- Avoid downloading unknown files or clicking suspicious links: Many spyware programs are installed via malicious downloads or phishing links. Always verify the source before downloading files or opening attachments, and avoid visiting untrusted websites.
- Enable firewalls and anti-spyware programs: Firewalls help block unauthorized connections, while anti-spyware software detects and removes threats before they compromise your system. Keeping these tools active provides continuous protection.
- Consider using a VPN to secure your internet traffic: A virtual private network encrypts your online activity, hiding it from potential eavesdroppers and hackers. There are especially useful when using public Wi-Fi networks, which are common targets for monitoring attacks.
5. FAQs about computer monitoring
Even with precautions, many people have common questions about computer monitoring and spyware. Here are detailed answers to help you understand and protect your system:
Can my employer monitor my personal computer?
Generally, monitoring software on personal computers without consent is illegal in most countries. Employers are allowed to track activity only on work-issued devices or networks. Personal devices are usually protected under privacy laws, so you should know your rights and use secure practices to keep your personal data safe.
How do I know if someone installed spyware without my knowledge?
Common signs of hidden spyware include slow system performance, unexpected pop-ups, webcam activating without permission, or applications behaving unusually. Running antivirus scans, checking active processes in Task Manager or Activity Monitor, and reviewing network connections can help detect unauthorized software.
Is it illegal to monitor a computer I own?
Yes, monitoring your own computer is completely legal. However, installing spyware or monitoring tools on someone else’s device without their consent may violate laws, depending on your jurisdiction. Always ensure monitoring is done only on devices you legally own or are authorized to manage.
Can antivirus software detect all monitoring tools?
Most reputable antivirus and anti-spyware programs can detect common spyware and keyloggers, but some advanced monitoring software may evade detection. Combining manual checks of processes, network activity, and startup programs with antivirus scans provides a higher level of protection.
What is the safest way to remove spyware?
The safest approach is to use trusted antivirus software to scan and remove threats. If spyware persists, booting in safe mode, reviewing startup programs, or performing a clean OS installation can ensure complete removal. Backing up important files before taking drastic measures is highly recommended.
6. Conclusion
Understanding how to know if your computer is being monitored is crucial for safeguarding your digital privacy. By recognizing warning signs and applying protective measures, you can secure your system against unauthorized access and potential data theft.
Key takeaways:
- Look for unusual system behavior, such as slow performance, unknown apps, or erratic pop-ups, which may indicate monitoring.
- Use antivirus and anti-spyware tools to detect and remove threats effectively.
- Regularly check network connections, running processes, and open ports to spot suspicious activity.
- Keep your operating system updated, use strong passwords, enable firewalls, and consider a VPN to maintain privacy.
Follow these steps to fully understand how to know if your computer is being monitored and take action to protect your personal data from unwanted tracking. For more practical tech guides and security tips, visit Tech How-To Simplified category on Safelyo to explore all resources designed to help you stay safe online.