Smartphones are no longer just communication devices, they have become mini-computers that carry your most personal information. From bank accounts and email logins to work files and private messages, everything lives on your phone. That makes it an attractive target for hackers who want to steal your data or exploit vulnerabilities.
This guide will walk you through how to protect your phone from hackers. You’ll learn why mobile security matters, the common tricks cybercriminals use, practical steps to secure your device, and advanced tools to help you stay safe.
In this article, you’ll discover:
- Why protecting your smartphone is critical today
- Common ways hackers break into mobile devices
- Step-by-step protection methods you can apply immediately
- Warning signs of a hacked phone and how to respond
- Advanced security measures for maximum protection
By the end, you’ll have a clear action plan to strengthen your phone’s security and protect your digital life.
1. Why protecting your phone from hackers is important
Your phone is more than just a communication device, it’s the center of your digital life. From personal accounts to sensitive work data, it holds information that hackers would love to exploit. Failing to secure your phone can have serious consequences, both financially and personally.
Key reasons to protect your phone from hackers:
- Financial security: Banking apps, mobile wallets, and payment platforms store sensitive financial details. If hackers gain access, they can initiate unauthorized transactions, steal credit card data, or empty your accounts. Recovering lost funds can be difficult and time-consuming.
- Identity protection: Smartphones contain login credentials for email, social media, and cloud storage. Hackers who steal this data can impersonate you, lock you out of your accounts, or use your identity to scam others. This can lead to long-term identity theft issues.
- Privacy concerns: Beyond financial harm, hackers can intrude on your private life. With access to your phone, they can spy on calls, read text messages, track your GPS location, or browse through personal photos. This invasion of privacy can be distressing and dangerous.
- Business risks: For professionals, a compromised smartphone isn’t just a personal issue, it can also be a corporate security threat. Hackers may use your device as a backdoor to infiltrate company emails, documents, and networks, potentially leading to data leaks and compliance violations.
- Reputation safety: Hackers may use stolen photos, conversations, or files for blackmail or public exposure. Even if no money is stolen, the damage to your personal or professional reputation can be severe and long-lasting.
2. Common ways hackers target smartphones
Hackers rarely “magically” break into phones. Instead, they exploit weaknesses, either in technology or in human behavior. By knowing the most common methods, you can recognize red flags and avoid falling into their traps.
2.1. Malicious apps and unsafe downloads
Not all apps are trustworthy. Cybercriminals often disguise malware inside free games, tools, or utility apps, then spread them through unofficial websites or third-party app stores. Once installed, these apps can log your keystrokes, steal passwords, or spy on your activity.
2.2. Phishing messages and fake links
Phishing remains one of the easiest and most effective ways to hack a phone. Attackers send emails, text messages, or social media links that look legitimate but lead to fake websites. Entering your login credentials gives hackers direct access to your accounts.
2.3. Public Wi-Fi and unsecured networks
Free Wi-Fi hotspots may be convenient, but they are rarely secure. Hackers can create fake Wi-Fi networks or intercept data flowing through legitimate ones. If you connect without protection, sensitive information like passwords or credit card numbers can be stolen.
3. How to protect your phone from hackers
Most smartphone threats can be avoided with a combination of smart habits and modern security tools. By taking these proactive measures, you know how to prevent someone from hacking my phone and stealing sensitive data.
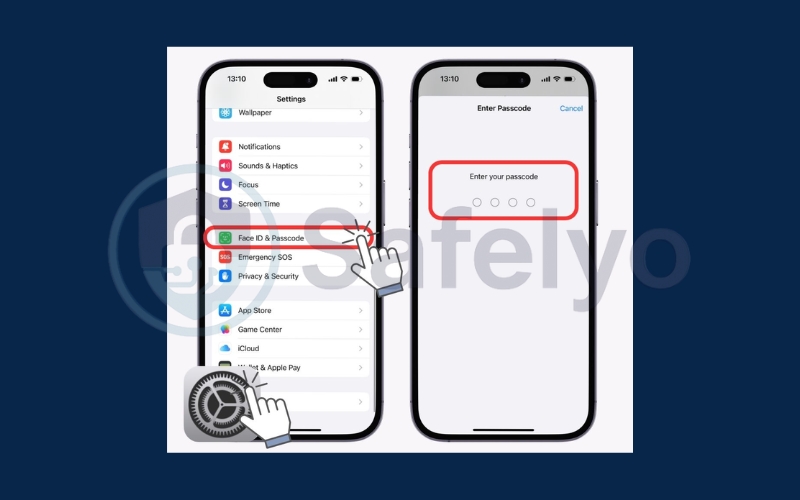
3.1. Use strong screen locks and biometric authentication
Your lock screen is your first layer of defense. A weak password or simple swipe pattern can be guessed in seconds. Instead, use a longer PIN or a complex password, and enable fingerprint or face recognition for added security. This makes it far harder for unauthorized users to access your phone if it’s lost or stolen.
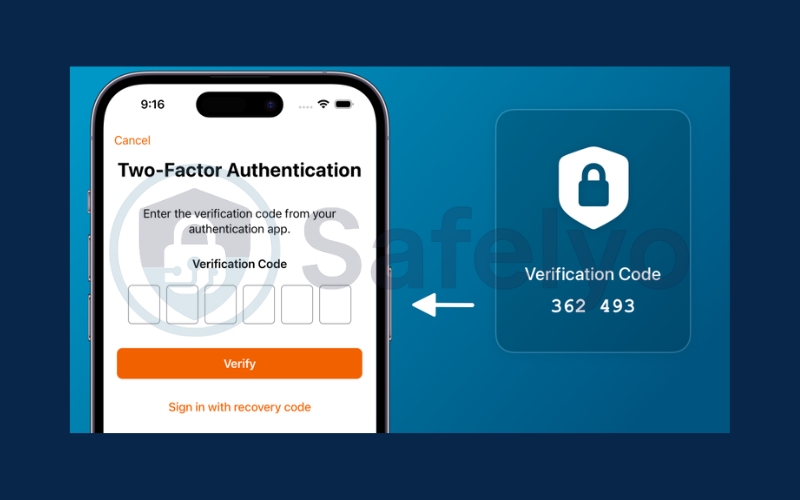
3.2. Enable two-factor authentication for important accounts
Two-factor authentication (2FA) adds a critical safety net. Even if a hacker gets your password, they won’t be able to log in without the second verification code.
Where to enable 2FA:
- Banking and payment apps
- Email accounts
- Social media
- Cloud storage services
Quick setup guide:
- Open your account’s Security Settings.
- Look for 2-Factor Authentication or Login Verification.
- Choose to receive codes via SMS, email, or an authenticator app.
For stronger protection, use an authenticator app like Google Authenticator or Authy instead of SMS.
3.3. Keep your operating system and apps updated
Outdated software is one of the easiest ways for hackers to break in. Updates often patch security flaws, so delaying them puts your phone at risk. Always allow automatic updates when possible, and check regularly for pending app and system updates.
3.4. Download apps only from official stores
Malicious apps often hide in third-party stores or shady websites. Google Play and Apple’s App Store perform security checks to reduce risks. Before installing, review app ratings, check the developer’s name, and avoid apps asking for excessive permissions.
3.5. Avoid connecting to unsecured public Wi-Fi
Public Wi-Fi networks are a common trap for hackers to intercept your data. If you must connect, avoid logging into sensitive accounts. A safer option is to use a Virtual Private Network, which encrypts your traffic and shields your activity from prying eyes.
How to use a VPN safely:
- Choose a reputable VPN provider.
- Install the app and log in.
- Connect to a secure server before browsing on public Wi-Fi.
3.6. Regularly back up your data and set up remote wipe
Backups ensure your files are safe even if your phone is hacked or lost. Remote wipe allows you to erase everything if your phone falls into the wrong hands.
How to enable remote wipe:
- On iPhone: Go to Settings > Apple ID > Find My > Find My iPhone.
- On Android: Go to Settings > Security > Find My Device.
Once enabled, you can locate or erase your phone remotely through your account dashboard.
3.7. Install a reputable mobile security or antivirus app
A good mobile security app provides real-time scanning, phishing protection, and alerts for suspicious activity. Some even offer Wi-Fi protection and device tracking. Popular choices include Bitdefender, Avast, and Norton. While not mandatory, they add valuable protection against evolving threats.
4. Warning signs your phone may be hacked
No phone is completely immune to cyberattacks. Hackers often try to stay hidden, but their activity usually leaves traces. Recognizing these signs early allows you to act before more damage is done. If you notice multiple symptoms at the same time, it’s a strong signal your phone could be compromised.
- Unusual battery drain and overheating: If your phone suddenly loses battery much faster than normal or gets hot even during light use, it could be due to malicious software running in the background. Spyware and hidden apps constantly process data, which consumes power and overheats your device.
- Strange apps or background activity: Unfamiliar apps appearing on your home screen or background processes running without explanation are serious red flags. Hackers often disguise malware as harmless apps, or they may install tools remotely to spy on your activity. If you don’t remember downloading an app, uninstall it immediately.
- Unexpected data usage: A sudden spike in mobile data usage may signal that spyware is secretly sending your information to a hacker’s server. Likewise, constant pop-ups, ads, or redirects in your browser can indicate adware or malicious software infection.
- Slow performance and frequent crashes: When malware infects a phone, it often consumes system resources, making apps freeze, crash, or run unusually slow. If your phone’s operation drops suddenly without a clear reason, it’s worth checking for malicious software.
- Strange messages or calls from your number: If your contacts report receiving suspicious texts, links, or calls from you that you didn’t send, it’s a major warning sign. Hackers may be using your phone to spread malware or phishing attacks.
- Disabled security features: If settings like antivirus, firewall, or device security toggle off by themselves, it may be because malware has taken control. Hackers sometimes disable protective features to keep you from noticing the attack.
- Unauthorized account activity: Receiving alerts about password resets, logins from unknown locations, or purchases you didn’t make can mean your phone has been hacked. Since many accounts are linked to your device, a compromised phone often leads to wider identity theft.
Read more:
5. What to do if you think your phone is hacked
Suspecting a hack can be stressful, but acting quickly helps you limit the damage and regain control. Hackers rely on victims being slow to respond, so the faster you act, the better your chances of stopping them. Follow these steps as soon as you notice signs of compromise.
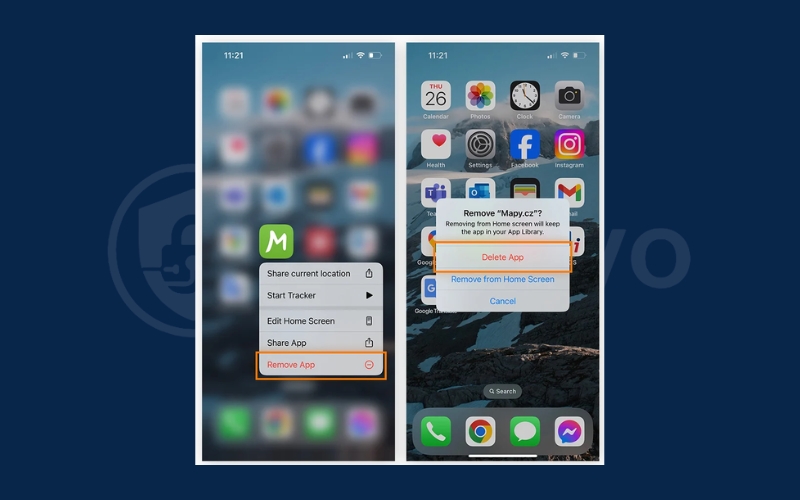
5.1. Remove suspicious apps immediately
Go through your installed apps and uninstall anything you don’t recognize or rarely use. Harmful apps often appear under generic names like “System Update” or “Cleaner,” designed to trick you into ignoring them.
- Check your App list in Settings for anything you didn’t download yourself.
- Sort apps by installation date to spot recent additions that may have caused the problem.
- If an app refuses to uninstall, reboot your phone into Safe Mode and try again.
5.2. Change passwords and enable stronger authentication
Once your phone is compromised, your accounts are at risk too. Hackers may have stolen login details for your email, banking, or social media.
- Start with your email account, since it’s often the recovery point for other logins.
- Update your banking and payment app credentials immediately.
- Create strong, unique passwords and avoid reusing them across multiple accounts.
- Turn on two-factor authentication (2FA) wherever possible. This ensures that even if hackers know your password, they can’t log in without the extra code.
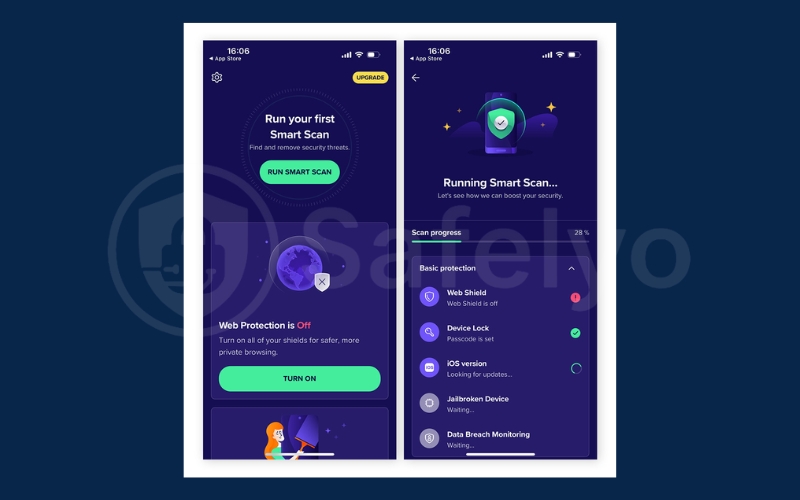
5.3. Run a full scan with mobile antivirus or security software
A reputable mobile antivirus app can detect hidden threats and remove them automatically. Many also protect against phishing and unsafe Wi-Fi networks.
- Download a trusted app such as Bitdefender, Avast, Norton, or Kaspersky.
- Run a full system scan instead of a quick scan to check every file and app.
- Follow the antivirus recommendations to quarantine or delete malicious files.
- Keep the app installed to provide ongoing protection against future threats.
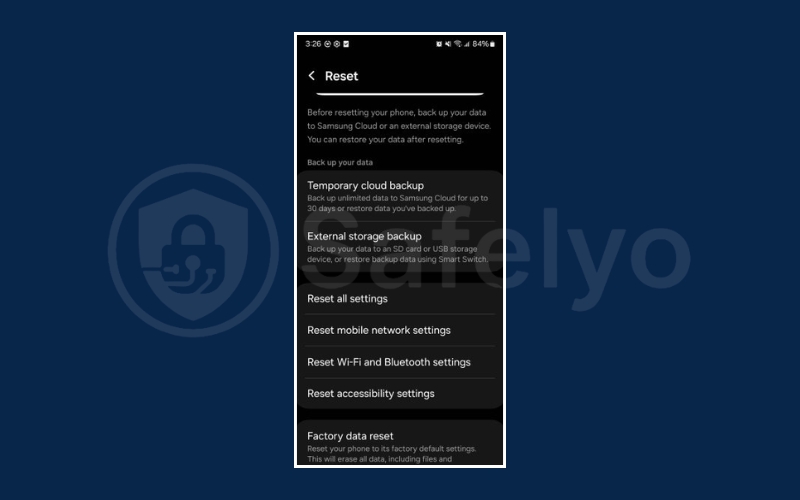
5.4. Perform a factory reset if necessary
If problems persist after trying the above steps, a factory reset may be the only option. This completely erases all data and apps from your device, returning it to its original state.
- Backup your data first using Google Drive, iCloud, or another secure cloud service.
- On Android: Go to Settings > System > Reset > Factory data reset.
- On iPhone: Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
After the reset, restore only essential apps and files from backup to avoid reintroducing malware.
6. Advanced mobile security measures
Once you’ve secured the basics, you can strengthen your phone further with advanced techniques. These steps are particularly valuable for professionals, frequent travelers, and anyone dealing with confidential information.
- Use a VPN for safer browsing: A Virtual Private Network (VPN) encrypts your internet traffic, preventing hackers from intercepting data on public Wi-Fi. This is essential when traveling or working remotely in cafes, airports, or hotels.
- Encrypt sensitive data on your phone: Encryption makes your files unreadable without the correct password or key. Even if hackers gain access to your phone, they won’t be able to read your private documents, messages, or emails.
- Limit app permissions and background access: Many apps request permissions they don’t need, such as access to your location, microphone, or contacts. Review your app permissions regularly and disable unnecessary ones to minimize data exposure.
- Enable device tracking and remote wipe: Most smartphones have built-in tools like Find My iPhone or Find My Device on Android. These allow you to locate, lock, or wipe your phone if it’s lost or stolen, protecting sensitive data from falling into the wrong hands.
- Consider secure messaging apps: If you share confidential information, use apps with end-to-end encryption like Signal or WhatsApp. This ensures that only you and the recipient can read the messages, not even the service provider.
7. FAQs about how to protect your phone from hackers
Many smartphone users still have questions about mobile security. Here are clear answers to the most common concerns.
Can someone hack my phone through a text message?
Yes. Malicious text messages containing links or attachments can install spyware or malware on your device if you click on them. Always avoid opening links from unknown senders and delete suspicious messages immediately.
Is it safe to use public Wi-Fi with a VPN?
A VPN encrypts your data, making public Wi-Fi much safer by preventing hackers from intercepting your traffic. However, it’s still best to avoid online banking or sensitive transactions on public networks whenever possible.
Does turning off my phone stop hackers?
Turning off your device disconnects it from the internet, so hackers cannot access it while it’s powered down. But the malware remains on the phone and will reactivate once it’s turned back on, unless you remove it.
Can my phone’s camera or microphone be hacked?
Yes. Some advanced malware can gain control of your camera or microphone without your knowledge, allowing hackers to spy on you. This is why limiting app permissions and installing a reputable mobile security app is critical.
How do I know if an app is safe to install?
Stick to official app stores like Google Play or the Apple App Store. Before downloading, check reviews, developer information, and requested permissions. Avoid apps asking for unnecessary access, like a calculator app requesting microphone or location data.
8. Conclusion
Learning how to protect your phone from hackers requires more than just installing security apps. It’s about building a mix of awareness, safe digital habits, and the right tools to reduce risks. By securing your lock screen, enabling two-factor authentication, you cover the basics that block most common attacks. Going further with advanced steps like using a VPN, encrypting files, and limiting app permissions provides extra protection for those who handle sensitive data or travel frequently.
Quick recap of essential steps to protect your phone from hackers:
- Use strong authentication methods like PIN, fingerprint, or facial recognition to block unauthorized access.
- Keep your phone updated with the latest security patches to fix vulnerabilities.
- Download apps only from trusted sources and carefully review app permissions before installing.
- Secure your connections with VPNs and avoid using risky public Wi-Fi for sensitive activities.
- Monitor your device for suspicious behavior and remove any detected threats immediately.
By applying these strategies, you can reduce your risks, secure your personal information, and enjoy peace of mind when using your smartphone. For more practical guides, explore the Tech How-To Simplified category on Safelyo and stay one step ahead of cyber threats.