How to prevent ransomware attacks has become a critical concern in today’s digital world. Unlike traditional viruses that merely slow down or damage systems, ransomware locks your files and demands a ransom for their release. This dangerous form of cyber extortion affects individuals, businesses, and even governments, leading to billions of dollars in losses every year.
In this article, you will learn:
- What ransomware is and how it spreads
- Proven strategies on how to stop ransomware
- The most common types and variants of ransomware
- How ransomware works step by step
- The risks and impacts of falling victim
By the end, you’ll have a clear roadmap to strengthen your cybersecurity and significantly reduce your chances of being targeted. Effective ransomware prevention requires combining technology, user awareness, and regular security practices.
1. What is ransomware
Ransomware is a form of malicious software that restricts access to files, systems, or entire networks until a ransom is paid. Most often, attackers demand payment in cryptocurrencies such as Bitcoin, which makes the transaction harder to trace.
The key features of ransomware include:
- Encryption of data: Victims can no longer access files, documents, or applications.
- Ransom note: A message is displayed, often threatening permanent data loss if payment is not made.
- Psychological pressure: Attackers use time limits, fear of exposure, or fake claims to force quick payment.
Ransomware has evolved significantly over the years, from simple lock screens to sophisticated attacks capable of spreading across global networks within hours.

2. How to prevent ransomware attacks
While no single method can provide 100% protection, applying multiple layers of defense will significantly reduce your risks. Below are the most effective strategies you should follow:
2.1. Avoid clicking on suspicious links
Cybercriminals often hide malicious links inside scam emails, fake pop-ups, or chat messages. Once clicked, these links may lead to unsafe websites or automatically trigger ransomware downloads. Always verify the sender’s email address, hover over links to preview their destination, and avoid clicking on anything that looks unusual.
2.2. Regularly scan emails for malicious attachments
Email remains the number one delivery channel for ransomware. Attackers disguise malware as attachments like invoices, resumes, or shipping confirmations to trick victims. Use spam filters to block suspicious messages and enable antivirus scanning on all email attachments before opening. Use spam filters to block suspicious messages and enable antivirus scanning, including automated scanning of all email attachments, before opening. If an email looks suspicious, it’s safer to delete it. Regular employee training on recognizing fraudulent email messages can further reduce the risk of ransomware infections.
2.3. Enable firewalls and endpoint protection
A firewall helps block unauthorized traffic from entering your system, while endpoint security tools monitor and isolate suspicious behavior in real time. Having both a security wall and endpoint protection enabled provides early detection and stops ransomware before it spreads across your devices or network.
2.4. Download software and files only from trusted sources
Many ransomware infections occur when users download cracked software, fake updates, or media files from shady websites. Only download apps from official vendors or trusted app stores. If you need updates, go directly to the developer’s website instead of clicking pop-up prompts.
2.5. Maintain regular backups of important files
Backups act as your safety net if ransomware locks your files. Store copies of critical data in both the cloud and external drives, and keep at least one backup offline to prevent attackers from encrypting it. Regularly test your backups to ensure they can be restored when needed.
2.6. Use a secure VPN on public networks
Public Wi-Fi is highly vulnerable to IT criminals who can intercept unencrypted traffic. Using a VPN (Virtual Private Network) encrypts your data and protects login credentials from being stolen. Always connect through a VPN when accessing sensitive accounts on public Wi-Fi.
2.7. Keep your security programs up to date
Ransomware evolves quickly, often exploiting known vulnerabilities in outdated software. Regularly update your antivirus, operating system, and applications to close security gaps. Enable automatic updates whenever possible to make sure you always have the latest protections. Investing in advanced security software ensures stronger defenses against evolving ransomware strains.
2.8. Refrain from using unknown USB devices
Attackers sometimes load malware onto infected USB drives. Plugging these into your computer can instantly install ransomware. Only use USB gadgets you own or trust, and disable auto-run features so external drives cannot launch programs automatically.
2.9. Protect your personal information online
Cybercriminals often collect personal information from social media or forums to launch targeted attacks. Limit the amount of sensitive data you share publicly, such as your birthday, address, or workplace. Adjust your privacy settings to reduce exposure and avoid giving attackers an advantage. Protecting personal data online also reduces the chances of becoming a victim of targeted ransomware campaigns.

3. Types and variants of ransomware
Ransomware is not just one type of malware – it comes in several different forms, each crafted to exploit victims in unique ways. Recognizing these categories can help you detect, prepare for, and respond to attacks more effectively.
- Crypto ransomware: Encrypts files and folders on your device, making them completely inaccessible until a ransom is paid. It is the most widespread and destructive form, often requiring backups for recovery.
- Locker ransomware: Blocks access to your operating system or locks the entire screen, preventing you from reaching your applications or even logging in. While it may not encrypt files, it still paralyzes system use.
- Scareware: Displays fake antivirus alerts, pop-ups, or bogus system warnings to trick victims into purchasing fraudulent software or revealing sensitive details. It often preys on fear and urgency.
- Double extortion ransomware: Takes the attack further by both encrypting data and threatening to publish or sell sensitive files if the ransom is not paid, creating legal and reputational risks for victims.
- Mobile ransomware: Targets smartphones and tablets, locking screens or encrypting mobile data. This can disrupt personal use and compromise sensitive apps like banking or messaging platforms.
- Ryuk: A notorious ransomware strain aimed at large enterprises, hospitals, and government agencies, often demanding multimillion-dollar ransoms. It typically spreads via data spoofing and remote desktop protocol (RDP) attacks.
- LockBit: One of the fastest-growing ransomware families, known for automation and rapid propagation across corporate networks. It has been a top choice for cybercrime groups running ransomware-as-a-service (RaaS).
- REvil (Sodinokibi): A globally infamous variant responsible for high-profile supply chain and business-targeted attacks. It became known for both large-scale data encryption and double extortion tactics.
4. How ransomware works
Ransomware attacks usually follow a predictable cycle, though advanced variants may use more sophisticated techniques.
- Delivery: The ransomware is delivered through scam emails, infected attachments, harmful links, or vulnerabilities in outdated systems.
- Infiltration: Once the victim clicks a link or opens an attachment, the malware silently installs itself. In some cases, attackers exploit network vulnerabilities to spread automatically. Advanced ransomware families may use network discovery techniques to map systems and move laterally.
- Execution and encryption: The malware scans the system, identifies valuable files, and encrypts them. Some strains may also disable antivirus software or delete system backups. They can also connect to remote command and control servers to receive instructions or exfiltrate data. In many cases, exfiltration of sensitive files occurs before encryption, giving attackers extra leverage.
- Ransom note: A message appears, explaining what happened and demanding payment in cryptocurrency. Victims are usually given deadlines, with threats of permanent data loss or data leaks.
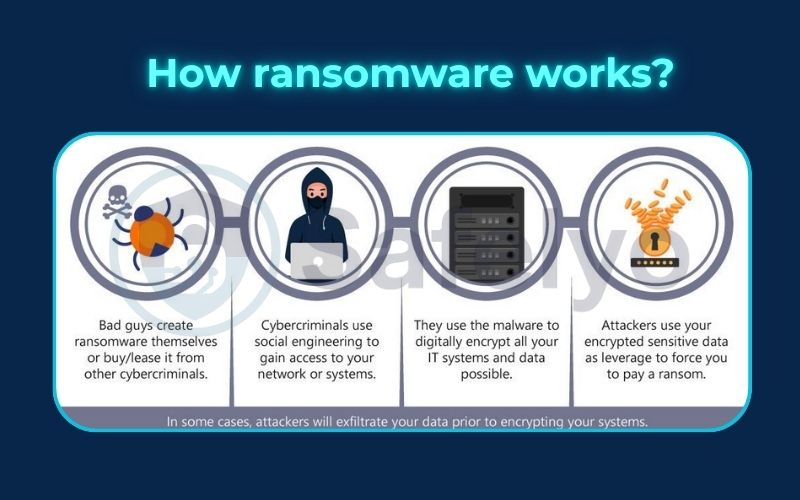
This process can happen within minutes, leaving victims with little time to react once the attack begins.
5. The risks and impacts of ransomware
Ransomware is not only financially costly but also deeply disruptive. Victims often face multiple layers of damage that extend beyond the initial attack.
- Financial damage: Paying the ransom can cost thousands or even millions, but even without payment, the costs of recovery, IT support, and downtime can cripple businesses.
- Operational disruption: Hospitals, schools, and companies have been forced to shut down operations for days or weeks due to locked systems. These shutdowns often result from the lateral movement of the ransomware across entire enterprise networks, quickly paralyzing multiple departments at once.
- Data privacy risks: Attackers may leak sensitive data, exposing victims to reputational harm, lawsuits, or compliance penalties. Once personal data is exposed, recovery becomes far more difficult, leading to lasting damage.
- Long-term recovery: Even after systems are restored, organizations may struggle with customer trust, stricter regulations, and the cost of upgrading infrastructure. A clear disaster recovery plan can shorten downtime and limit the impact of ransomware incidents. Building redundancy into the IT infrastructure further reduces the risk of a complete operational shutdown.
- Psychological impact: The fear, stress, and loss of confidence following an attack can affect both individuals and teams within organizations.
6. FAQs
Ransomware raises many concerns, and users often have similar questions when trying to protect their data. Below are some of the most common questions and clear answers to help you understand how to stay safe.
Should I pay the ransom if I get infected?
No. Paying the ransom does not guarantee that attackers will return your files, and many victims never receive a working decryption key. It also funds the cybercriminal industry, making future attacks more likely. Restoring data from backups is always the safer choice.
Can antivirus software stop ransomware?
Yes, antivirus software can block many known ransomware strains before they spread. However, cybercriminals constantly create new versions designed to bypass detection. To stay safe, pair antivirus with firewalls, software updates, and regular backups.
How do I know if my system is infected?
Common signs include encrypted files, unusual file extensions, and a ransom note demanding payment. Some systems may also slow down during encryption. If you see these, disconnect from the internet to stop the malware from spreading. Regular security awareness training helps employees identify early signs of ransomware before major damage occurs.
How can I recover my files after an attack?
The best option is to restore from secure backups that are kept offline or in the cloud. In some cases, free decryption tools are available for specific ransomware families. Avoid unverified recovery tools, as they may install more malware.
Who is most at risk of ransomware?
Businesses, hospitals, financial institutions, and government agencies are frequent targets because attackers know downtime is costly. Still, individuals are also at risk, especially if they use outdated software or download from unsafe sites.
How often should I back up my data?
Experts recommend following the 3-2-1 rule: keep three copies of data, on two different storage types, with one copy kept offline or in the cloud. Backups should be updated regularly and tested to ensure they work during an attack. Storing one copy of backups in secure cloud storage ensures availability even if local systems are compromised.
7. Conclusion
Understanding how to prevent ransomware attacks is essential in today’s digital world, where even a single mistake can lead to data loss or costly downtime. Ransomware continues to evolve, but with the right knowledge and consistent security habits, you can significantly lower your chances of becoming a victim.
Key takeaways:
- Do not click suspicious links or attachments
- Use firewalls, endpoint security, and trusted sources for downloads
- Keep regular backups of critical files
- Stay protected on public Wi-Fi with a VPN
- Update your security software and operating systems regularly
By following these practices, you make yourself a much harder target for cybercriminals. Remember, prevention is always cheaper, safer, and more effective than recovery. Ongoing security awareness programs help organizations stay prepared for new ransomware tactics. To further strengthen your protection, explore the Antivirus section of Safelyo, designed to block ransomware and keep your data safe.