Does Tor have a built-in VPN? No, Tor Browser does not have a built-in VPN. This is a common question. Many users seek all-in-one privacy tools and often group Tor and VPNs together. Both relate to privacy, but they are separate technologies with different goals.
Key takeaways:
- Tor Browser and VPNs are two separate privacy tools.
- Tor provides anonymity by routing traffic through a 3-node volunteer network.
- A VPN provides privacy by encrypting your connection to a private server.
- You can use both together, most commonly as “Tor over VPN” for layered security.
1. Does Tor have a built-in VPN?
No, Tor Browser does not have a built-in VPN. You will not find a “connect to VPN” button or any integrated VPN service within the browser’s settings.
This is a very common point of confusion. Many users ask “Does Tor Browser have a built in VPN?” because both tools are powerful and famous for protecting online privacy. It is easy to group them together.
The key is understanding their different goals:
- A VPN’s main job is privacy. It creates a secure, encrypted tunnel between your device and a single server run by a company. This hides your online activity from your Internet Service Provider (ISP). Your ISP only sees you connecting to the VPN, not the websites you visit.
- Tor Browser’s main job is anonymity. It hides who you are from the websites you visit. It does this by routing your connection through a decentralized, three-layer network run by volunteers. The website sees the IP address of the final volunteer node, not your real IP.
They are built to solve two different problems.
2. Why Tor Browser doesn’t include a VPN
The entire philosophy behind Tor is decentralization. Its power comes from a global network of thousands of volunteer-run servers, called nodes. No single person, company, or government controls this network.
If Tor included a “built-in VPN,” it would break this entire model. A VPN is a centralized service. You must trust the single company that runs the VPN servers. You trust them not to log your activity and to protect your data.
This creates a direct conflict. Tor is designed to be trustless. You do not need to trust the volunteers because of its 3-layer encryption. A VPN is a trusted system where you place your full trust in the VPN provider.
By not including a VPN, the Tor Project keeps the browser focused on anonymity. It gives you, the user, the choice to use a separate VPN provider if you wish.
3. What privacy features does Tor Browser have?
So, if Tor doesn’t have a VPN, what does it have? It includes a powerful, multi-layered defense system focused entirely on anonymity. These features work together to make your identity harder to trace.
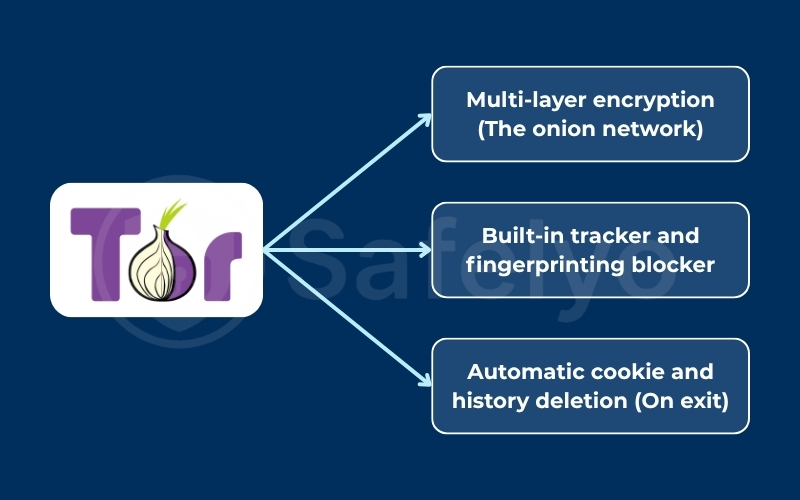
3.1. Multi-layer encryption (The onion network)
Tor’s name comes from “The Onion Router”. This is a perfect analogy. Your data is wrapped in three layers of encryption, like the layers of an onion.
It then travels to the network. The first “Guard” node peels off the first layer. This node only knows where you came from, but not your final destination.
The “Middle” node peels off the second layer, only knowing the Guard and Exit nodes.
The final “Exit” node peels off the last layer. It sees the website you are visiting, but has no idea who or where you are.
This 3-step process means no single point in the network knows your full path.
3.2. Built-in tracker and fingerprinting blocker
Tor Browser actively fights against online tracking. It automatically blocks many of the third-party scripts, ads, and trackers that follow you across the internet.
More importantly, it prevents browser fingerprinting. This is a technique where sites build a unique profile of you. They use details like your screen size, installed fonts, and browser version. Tor Browser makes every user look the same by standardizing these settings.
This makes it very difficult for a website to single you out from the crowd of other Tor users.
3.3. Automatic cookie and history deletion (On exit)
The Tor Browser is designed to be stateless. This means it has no memory of your session once you are done.
When you click the “X” to close the browser, everything is instantly wiped. This includes all your browsing history, any cookies from websites, and your cache (stored images or files). It leaves no trace of your activity on your computer. The next time you open Tor Browser, it is a completely fresh, clean session.
4. How to combine a VPN with Tor Browser
Since Tor doesn’t have a built-in option, it’s natural to ask if you can combine them manually.
Advanced users layer these tools for maximum privacy. The main goal is to hide the fact that you are using Tor from your Internet Service Provider (ISP).
There are two ways to do this: one is safe and recommended, the other is not.
4.1. Method 1: Tor over VPN (Recommended)
This is the simplest, safest, and most common method. “Tor over VPN” means you route your Tor traffic through an active VPN connection. Your computer connects to the VPN server first, and only then does your Tor traffic pass through that encrypted tunnel.
Here are the steps to do it:
- Step 1: Open your standalone VPN application and connect to a server. Your entire internet connection is now encrypted.
- Step 2: After your VPN is connected, open the Tor Browser and use it normally.
The primary benefit of this method is that your ISP cannot see you are using Tor. It only sees a block of encrypted traffic going to your VPN server, which looks like normal VPN use.
This setup also protects you in other ways. Your VPN provider knows your real IP address, but it cannot see what you are doing on Tor. It only knows you connected to the Tor network.
Meanwhile, the Tor network never sees your real IP; it only sees the IP address of your VPN server. This creates a powerful extra layer of anonymity.
I personally use the “Tor over VPN” method. I first launch my VPN app and connect to a server. Only then do I open Tor Browser. This setup ensures my ISP doesn’t flag my account for using Tor, giving me an essential extra layer of privacy.
4.2. Method 2: VPN over Tor (Not recommended)
This method reverses the process and is not recommended for most people. It means you try to route your VPN connection through the Tor network.
This involves:
- Step 1: Open the Tor Browser first.
- Step 2: Try to configure your VPN application to route its own connection through the Tor network.
This setup is extremely difficult, as most VPN apps do not support this configuration. Even if you succeed, the connection will be incredibly slow. Tor is already slow due to its 3-node design, and forcing heavy VPN encryption through that slow network makes the internet almost unusable.
The most important reason to avoid this is the security risk. The final “Exit Node” in the Tor network can see your internet traffic. This means the volunteer running that node could potentially see your unencrypted traffic on its way to your VPN, which might include your VPN login credentials. It exposes sensitive information to the most vulnerable part of the Tor network.
5. FAQs about Does Tor have a built-in VPN
Let’s answer a few other common questions about using Tor and VPNs.
Is Tor Browser safer than a VPN?
They are different. Tor is better for anonymity (hiding who you are). A VPN is better for privacy (hiding what you do from your ISP). For daily browsing, a VPN is faster and more practical.
Can my ISP see me using Tor Browser?
Yes. If you use Tor without a VPN, your ISP can see that you are connecting to the Tor network. They cannot see what you are browsing, but they know you are using Tor.
Will a separate VPN slow down Tor Browser?
Yes. Tor is already slow because it routes your traffic through three nodes. Adding a VPN (Tor over VPN) adds another step. This will slow your connection further. This is the trade-off for increased security.
Can I use Tor Browser instead of a VPN for daily use?
It is not recommended. Tor is often too slow for streaming or large downloads. Many websites also block users coming from Tor exit nodes. A VPN is much more suitable for everyday internet use.
6. Conclusion
So, does Tor have a built-in VPN? No, it doesn’t. Tor’s goal is anonymous, decentralized browsing. While a VPN’s goal is private, encrypted browsing from a central provider.
- Tor provides anonymity through its decentralized, multi-layered “onion network.”
- A VPN provides privacy by creating a single, encrypted tunnel to a private server.
- For daily privacy from your ISP, a VPN is the best choice.
- For maximum anonymity, Tor is the best choice.
- To hide your Tor use, connect to your VPN before opening Tor Browser.
For more simple and practical tech tutorials, explore the Privacy & Security Basics section at Safelyo.













