The frantic search for how to remove a hacker from my phone is a moment of pure panic. It’s not just a technical problem; it’s a deep violation of your personal space, putting everything from your private messages to your financial apps at risk.
In today’s world, our phones are our lifelines. Securing them isn’t optional – it’s essential. With years of experience in digital forensics and helping individuals recover from cyber-attacks, I’ve seen how a calm, methodical approach can turn a crisis into a resolved issue. You don’t need to be a tech expert to fight back, but you do need a clear plan.
This guide provides that step-by-step plan to help you:
- Confirm the tell-tale signs that your phone has been compromised.
- Take immediate emergency actions to limit the damage.
- Follow the exact process for removing the threat from your iPhone or Android.
- Secure your accounts and lock down your phone to prevent future attacks.
Don’t let panic take over. Let me guide you through the steps needed to evict the intruder and reclaim your digital life.
QUICK DIAGNOSIS & ACTION PLAN
Here’s a quick summary table. If you spot a sign, understand the likely cause and the first action you should take.
| Sign You’re Seeing | What’s Likely Happening | First Step to Fix It |
| High Battery Drain & Overheating | Malicious software is running constantly in the background, using up your phone’s processor. | Run a security scan with a trusted antivirus app to detect and remove the malware. |
| Sudden Spike in Data Usage | The hacker’s software is sending your personal data from your phone to their server. | Disconnect from Wi-Fi and mobile data immediately to cut off the connection. |
| Unfamiliar Apps Appear | A hacker has installed malware, spyware, or adware onto your device without your consent. | Find the suspicious app and uninstall it. Use Safe Mode on Android if needed. |
| Constant Pop-ups & Slow Speed | Adware or other malware is interfering with your phone’s normal operations and system resources. | Find and delete the responsible app. Also, clear your browser’s history and data. |
| Weird Activity on Online Accounts | Your login credentials have been stolen from your phone and are being used to access your accounts. | Immediately change the passwords for your critical accounts (email, banking) using a different, trusted device. |
| Camera/Mic Activates Randomly | Advanced spyware has been installed, giving a hacker remote control over your device’s hardware. | This is critical. Perform a full factory reset after backing up only your essential photos and contacts. |
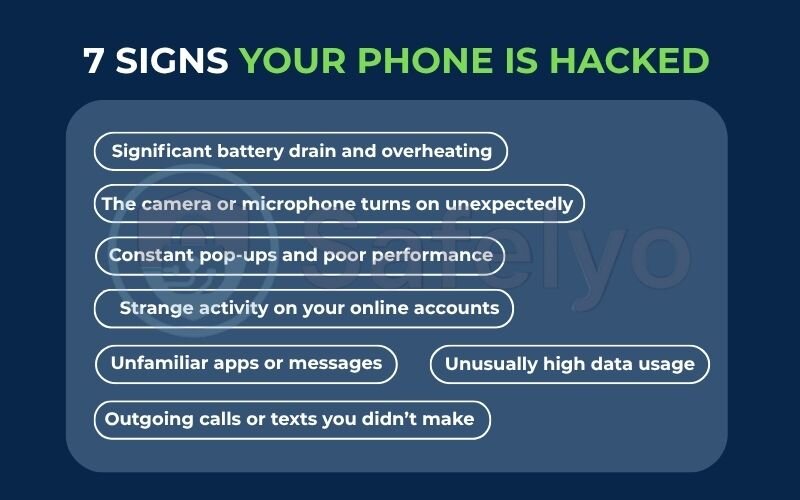
1. Confirm the threat: 7 signs your phone is hacked
Before you take drastic measures like a full reset, it’s important to confirm your suspicions. Sometimes, a poorly written app or an old battery can mimic the signs of a hack. However, if you’re experiencing several of these issues at once, it’s a major red flag.
From my experience helping people diagnose these problems, here are the most common signs that an unwelcome guest is living in your phone:
- Significant battery drain and overheating. Malware and spyware are resource-hungry. If your phone’s battery is suddenly draining much faster than usual and the device feels warm to the touch even when you’re not using it, it’s a classic sign that something is running constantly in the background.
- Unusually high data usage. I once helped a client who discovered a hack because their mobile data bill skyrocketed. Hackers use your data connection to send your information back to their servers. Check your phone’s data usage stats. If you see a massive, unexplainable spike, it’s a strong indicator of foul play.
- Unfamiliar apps or messages. This is one of the most direct clues. Scroll through your apps list. If you see an application you are 100% certain you did not install, it’s a huge warning sign. The same goes for checking your call logs and text messages for any outgoing communication you didn’t send.
- Constant pop-ups and poor performance. If your phone suddenly acts like it’s ten years old – apps crash, it freezes, and you’re bombarded with pop-up ads even when you’re not in a web browser – it could be adware or other malicious software bogging down your system.
- Strange activity on your online accounts. A hacker often uses your phone as a launchpad to access your other accounts. If friends tell you they’re getting weird social media DMs from you, or you see login alerts for your email from strange locations, the breach likely started on your phone.
- Outgoing calls or texts you didn’t make. This is a clear sign that someone else is controlling your device. They might be using your phone to send spam texts or make premium-rate calls that are charged to your bill.
- The camera or microphone turns on unexpectedly. This is the stuff of nightmares, but it happens. If you see the green or orange dot (on newer iPhones and Androids) indicating your camera or mic is active when no app should be using it, your device is almost certainly compromised with advanced spyware.
Recognizing these signs is your first line of defense. According to reports from security firms like Kaspersky, mobile malware attacks are a constant and evolving threat. Trust your gut – if your phone feels “off,” it probably is.
2. Emergency checklist: What to do right now if you think you’ve been hacked
Before you do anything else, take these immediate steps. The goal right now isn’t to fix everything, but to stop any further damage. Think of this as digital first aid.
- Disconnect from the internet. This is your top priority. Turn off your Wi-Fi and your mobile data (cellular data) immediately. This severs the hacker’s connection to your phone, preventing them from stealing more data or controlling it remotely.
- Do not delete anything yet. Don’t delete suspicious text messages, apps, or call logs. As a security analyst who has handled these cases, I can tell you that these items are potential evidence. They can help you or a professional figure out how the hack happened.
- Alert your financial institutions. If you have banking or payment apps on your phone (like PayPal, Cash App, or your bank’s app), call your bank or credit card company. Inform them that your phone may be compromised and ask them to monitor your accounts for fraudulent activity.
- Warn your contacts. Send a brief message from another device (a trusted computer or a friend’s phone) to your close contacts. Let them know your phone might be hacked, and to be wary of any strange messages asking for money or personal information coming from you.
In a moment of panic, your first instinct might be to erase everything. Resist that urge. Your immediate priority is to cut the connection. We’ll handle the removal process methodically in the next steps.

What NOT to do in a panic
Just as important as knowing what to do is knowing what to avoid. Panicked actions can make a bad situation worse.
- Don’t connect to public Wi-Fi to research a solution. Unsecured networks are a hacker’s playground and could expose your device even more.
- Don’t call back unknown numbers or click links from “tech support” texts that suddenly appear. This is often a secondary trap set by the hacker to get even more information from you.
- Don’t rush to delete messages or apps before you understand what they are. As mentioned, they can be crucial evidence for identifying the source of the hack.
- Don’t enter your passwords into any pop-up windows asking you to “verify your account.” Legitimate services will rarely do this. This is a classic phishing trick to steal your credentials.
3. The step-by-step guide to removing a hacker from your phone
Now that you’ve identified the warning signs, it’s time to systematically evict the hacker. We will work through these steps in order, starting with the simplest and moving to the most powerful solution. Follow them carefully for your specific device.
3.1. Run a security scan with a trusted antivirus app
This is always my recommended first step. It’s the least invasive and most automated way to find and remove common malware and spyware. A good security app is designed to hunt for malicious code that you might never find on your own.
- Go to your official app store (Google Play Store for Android, Apple App Store for iPhone).
- Download a mobile security app from a highly reputable provider like Norton, Bitdefender, or McAfee.
- Install the app and run a full system scan. Follow its instructions to quarantine or delete any threats it finds.
3.2. Find and delete suspicious apps
If the scan doesn’t solve the problem or you want to be extra thorough, your next step is to manually hunt for suspicious apps.
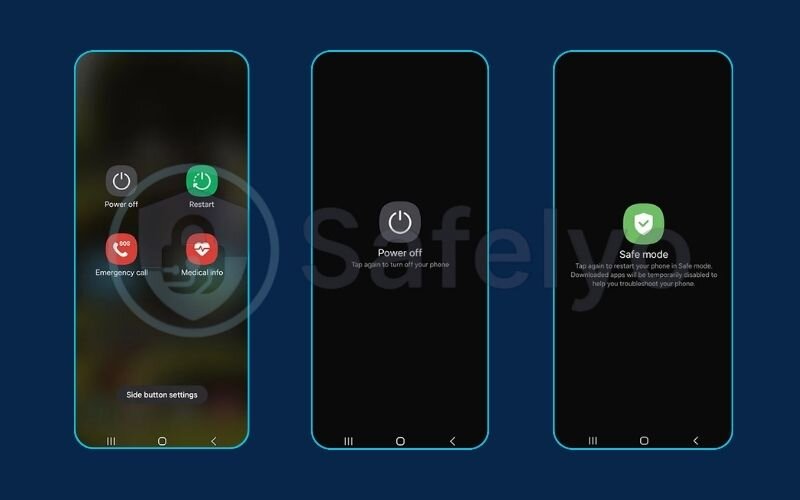
For Android Users
- Enter Safe Mode: This is a crucial diagnostic mode that disables all third-party apps, preventing malware from running.
- Press and hold your phone’s power button until the power menu appears.
- Tap and hold the “Power off” option. A “Reboot to safe mode” prompt will appear. Tap OK.
- Review and Uninstall: Once in Safe Mode, go to Settings > Apps > See all apps. Carefully scroll through the list. If you see any app you don’t recognize or that looks suspicious, tap on it and select Uninstall. Since the malware is inactive in Safe Mode, you should be able to remove it.
- Restart your phone to exit Safe Mode.
For iPhone Users
- Delete Suspicious Apps: Simply look through your home screens and app library for any app you don’t remember installing. To delete it, press and hold the app icon, then tap Remove App > Delete App.
- Check for Malicious Profiles: This is a key hiding spot for advanced spyware. Go to Settings > General > VPN & Device Management. If you see any configuration “Profile” listed here that you didn’t install (e.g., from an employer or school), tap on it and delete it immediately.
3.3. Revoke suspicious app permissions
Hackers want access to your data. They get it by tricking you into giving their malicious app permissions to your camera, microphone, contacts, and location. Let’s review and revoke those permissions. Think of it as taking back the keys to the most private rooms in your house.
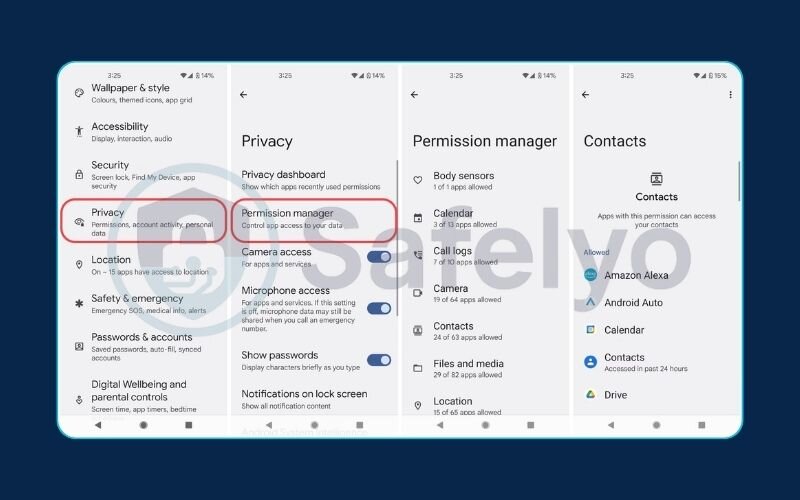
For Android Users
- Go to Settings > Security & privacy > Privacy > Permission manager. Here you can see which apps have access to sensitive permissions like your camera, location, and microphone. If you see an app that has no good reason to access something (e.g., a simple calculator app using your location), revoke its permission.
For iPhone Users
- Go to Settings and scroll down to the bottom to see a list of all your installed apps. Tap on any app to see and manage the permissions it has. Alternatively, go to Settings > Privacy & Security to review permissions by category (e.g., Location Services, Microphone).
3.4. The last resort: perform a factory reset
This is the “nuclear option,” but it is also the most effective way to guarantee you’ve removed the hacker. A factory reset erases everything on your phone – apps, photos, settings, and all malware – and returns it to its original, out-of-the-box state.
Before you proceed, back up your essential data, like photos and contacts, to a cloud service (like Google Photos or iCloud) or your computer. Do not do a full phone backup of apps and settings.
CRITICAL WARNING
After a factory reset, you must set up your phone AS A NEW DEVICE.
DO NOT RESTORE FROM A BACKUP created after you suspected the hack. Restoring from an old backup could simply reinstall the malware you’re trying to get rid of. Manually re-download your trusted apps from the official store and then sync your contacts and photos from the cloud.
For Android Users
- Go to Settings > System > Reset options > Erase all data (factory reset). Follow the on-screen prompts. (The exact path can vary slightly by manufacturer.)
For iPhone Users
- Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. You will be prompted to enter your passcode and Apple ID password.
4. Secure your digital life after the hack
Getting the hacker out of your phone is a huge victory, but the battle isn’t over yet. You must assume that before you kicked them out, they stole the keys to your digital kingdom: your passwords. The next step is to change the locks on every important door.
4.1. Change all your critical passwords immediately
This is not optional. You have to operate under the assumption that every password you’ve ever typed or saved on your phone is now in the hands of a criminal.
Here’s the priority list I give all my clients. Start with your primary email account. Your email is the master key that can be used to reset passwords for all your other accounts.
- Your primary email (Google, Outlook, etc.)
- Banking and financial apps (Bank accounts, PayPal, Wise)
- Your phone’s core account (Apple ID or Google Account)
- Social media accounts (Facebook, Instagram, X/Twitter, LinkedIn)
When you change all your passwords after the hack, don’t make a simple mistake. From my experience, people often just change Password123! to Password124!. This is useless against a hacker. Your new passwords must be strong and unique for every single account. That means a long combination of uppercase and lowercase letters, numbers, and symbols.
Managing this is nearly impossible for a human. For a powerful, long-term solution, I strongly recommend using a password manager. It will create and store incredibly strong passwords for you. Check out Safelyo’s guide to the best password managers of the year to find one that fits your needs.
4.2. Enable two-factor authentication (2FA) everywhere
Think of Two-Factor Authentication (2FA) as a second, deadbolted lock on your door. Even if a hacker manages to steal your password (the key), they still can’t get in without a second piece of information – usually a temporary code from an app on your (now clean) phone.
Enable 2FA on every single service that offers it, especially the critical accounts you just secured. When given the choice, I always advise using an authenticator app (like Google Authenticator, Microsoft Authenticator, or Authy) over receiving codes via SMS text message. SMS messages can be intercepted through advanced techniques like SIM swapping, making authenticator apps a more secure option.
5. How to secure your phone from hackers for good
You’ve done the hard work of removing the threat and securing your accounts. Now, let’s make sure you never have to go through this again. The best way to secure your phone from hackers is to build a digital wall around it through smart habits and powerful tools.
Here are the essential rules I live by and recommend to everyone:
- Only download apps from official stores. Your safest bet is always the Google Play Store for Android and the Apple App Store for iPhone. These stores have security checks in place to weed out most malicious apps. Avoid third-party app stores at all costs.
- Keep your operating system and apps updated. Those update notifications aren’t just for new emojis. They contain critical security patches that close the loopholes hackers use to get in. Always install updates as soon as they are available.
- Be skeptical of public Wi-Fi. Think of public Wi-Fi at cafes, airports, or hotels as a public park. You wouldn’t leave your wallet unattended there. Hackers can use these unsecured networks to snoop on your traffic. If you must use public Wi-Fi, always protect your connection with a reputable VPN.
- Don’t click on suspicious links. This is how most hacks begin. Be wary of urgent or “too good to be true” messages in emails or texts, even if they seem to be from a friend or a trusted company. A simple example is a text saying “Your package has a delivery issue, click here to resolve,” which leads to a fake site designed to install malware.
- Install and run a reputable mobile security app continuously. This is your 24/7 digital bodyguard. It actively scans for threats, blocks dangerous websites, and alerts you to suspicious activity in real-time.
Manually removing a hacker is a stressful, one-time fix. For continuous, real-time protection that lets you sleep at night, a powerful security app is non-negotiable. See Safelyo’s expert picks for the best mobile antivirus software to keep you safe 24/7.
Read more:
6. FAQ about how to remove a hacker from my phone
Even with a detailed plan, it’s normal to have some lingering questions during a stressful time like this. Here are direct answers to some of the most common queries I encounter.
Can you remove hackers from your phone?
Yes, absolutely. You can remove a hacker by following the systematic steps in this guide, which include running security scans, deleting malicious apps, and, if necessary, performing a factory reset to completely wipe the device clean.
What should I do if my phone has been hacked?
The very first thing you should do is follow the Emergency Checklist at the beginning of this article: disconnect from the internet, alert your financial institutions, and warn your contacts. This immediately limits the damage while you prepare to remove the threat.
Where can I check if my phone is hacked?
You can check for signs of a hack in several places on your phone: check your battery usage for unusual drain, your mobile data stats for unexplained spikes, your apps list for any you don’t recognize, and your online accounts (like email and social media) for strange activity.
Can I block a hacker?
You can’t “block” a hacker in the same way you block a phone number. Instead, you block their access. You do this by removing their malicious software from your phone, changing all your passwords, and enabling two-factor authentication (2FA). This effectively locks them out.
Will a factory reset definitely remove a hacker?
In almost all cases, yes. A factory reset erases everything on the phone, including most types of malware and spyware. However, you must remember to set up your phone as new and not restore from a potentially infected backup.
Can someone hack your phone just by knowing your number?
Directly hacking your phone with just a number is extremely difficult for a typical hacker. However, your number can be used for sophisticated attacks like SIM swapping or targeted phishing messages designed to trick you into installing malware.
Can a hacker see you through your phone’s camera?
Yes. If your phone is infected with advanced spyware, a hacker can potentially gain remote access to your camera and microphone without your knowledge. This is a serious privacy invasion and a key reason to act fast if you suspect you’ve been hacked.
What is the best way to scan your phone for hackers?
The most reliable method is to install and run a full system scan using a reputable mobile antivirus application from a trusted provider. These apps are specifically designed to detect and remove malicious code that is often hidden from view.
How can I stop someone from mirroring or remotely controlling my phone?
“Phone mirroring” is usually a symptom of malware or spyware already on your device. By following the steps in this guide – especially running an antivirus scan, deleting suspicious apps, and performing a factory reset – you will remove the malicious software that enables a hacker to mirror or control your device.
7. Conclusion
Knowing how to remove a hacker from my phone is a vital skill in today’s digital world, transforming you from a potential victim into an empowered user who can take back control. The feeling of violation is real, but so is the solution.
To summarize, here are the key points to remember:
- First, identify the signs and take immediate emergency action to isolate your device and prevent further damage.
- Second, follow the systematic removal steps, from running a security scan to performing a factory reset if necessary.
- Finally, secure your accounts and adopt preventative habits to build a strong defense for the future.
Proactive protection is always better than reactive recovery. Don’t leave your security to chance. Explore comprehensive guides in the Antivirus section of Safelyo to stay one step ahead of the threats and keep your digital life secure.













