You may have seen the word ‘obfuscate’ in a VPN’s settings or a cybersecurity article and wondered, What does obfuscate mean exactly? In simple terms, it means to deliberately make something confusing. In the world of technology, it’s a powerful technique used to disguise your data, enhancing your security and privacy in ways that standard encryption alone cannot.
As a privacy analyst, I often see this term cause confusion. People wonder if it’s the same as encryption, or just another marketing buzzword. The truth is, it’s a crucial tool, especially for users facing heavy internet censorship. Understanding this concept is key to unlocking a higher level of digital freedom.
In this comprehensive guide, you’ll discover:
- The simple dictionary definition of ‘obfuscate’.
- How it’s used in cybersecurity, especially for VPNs.
- The critical difference between obfuscation and encryption.
- Why is this technique a key to internet freedom?
Don’t let complex terms stand in the way of your security. Let me make this powerful concept clear and show you how it works to protect you.
1. Obfuscation meaning: From the dictionary to your digital life
To truly grasp the concept, we need to start with its basic, everyday meaning before we can apply it to the digital world. This is a word that has a life both inside and outside of technology.
1.1. The general definition
The core obfuscation meaning is simple. According to Merriam-Webster, to obfuscate means “to deliberately make something unclear, confusing, or difficult to understand.”
It’s the act of making something obscure on purpose. You might see obfuscation in a sentence like this:
"The politician's speech seemed designed to obfuscate the real issues, burying the facts under layers of confusing jargon."
The goal is to hide the truth in plain sight by making it hard to comprehend. Keep this core idea of “making something confusing to hide its true nature” in your mind as we move into the tech world.
1.2. What is obfuscation in cybersecurity?
Now, let’s apply that definition to our digital lives. What is obfuscation in cybersecurity? It is the technique of disguising data or code to conceal its true purpose or nature, without actually changing what it does.
The main goal is not to make the data unbreakable (that’s encryption). The goal is to make it look like something else entirely.
As a security analyst, the best way I can describe it is as digital camouflage. Imagine a sniper in a ghillie suit. They are not invisible, but they blend in so well with the surrounding forest that you would never notice them. Obfuscation does the same thing for your data or internet traffic. It makes sensitive information blend in with the normal, harmless data around it to avoid detection. This protection is a clever form of hiding in plain sight.

2. Obfuscate vs. encrypt: The key difference explained
This is the most important distinction to understand. While both techniques are used for security, obfuscation vs encryption describes two fundamentally different goals and methods. I’ve found the easiest way to explain this is by thinking about how you might protect your valuables while traveling.
Encryption (The Locked Safe)
Encryption is about protecting the content of your data.
Imagine you put your valuable documents inside an unbreakable steel safe with a complex combination lock. You then ship this safe. Anyone who sees the package knows immediately that it’s safe and that it contains something valuable. However, no one can get inside to see what is in it without the secret combination (the encryption key).
- The Goal: Confidentiality. The data is scrambled into unreadable ciphertext. It is obviously protected, but its nature as “protected data” is clear.
Obfuscation (The Hidden Compartment)
Obfuscation is about hiding the nature of your data.
Instead of a safe, you take your valuable documents and hide them inside a hollowed-out compartment in a boring-looking book. You then put this book on a shelf with hundreds of other books. Anyone who glances at the shelf just sees a collection of books. They have no idea that one of them contains a hidden secret.
- The Goal: Stealth. The data itself might still be readable if found, but the primary goal is to prevent it from being noticed in the first place. It blends in with its surroundings.
In cybersecurity, these two techniques are often used together. To continue the analogy, the most secure method is to put your documents in a small, locked box (encryption) and then hide that locked box inside the hollowed-out book (obfuscation).
| Feature | Encryption | Obfuscation |
| Main Goal | Protect content (make it unreadable) | Hide nature (make it look like something else) |
| Method | Uses cryptographic keys to scramble data. | Uses cloaking and disguise techniques. |
| Result | Scrambled, obviously protected data (ciphertext). | Data that appears normal, harmless, or nonsensical. |
| Analogy | A locked safe. | A book with a hidden compartment. |
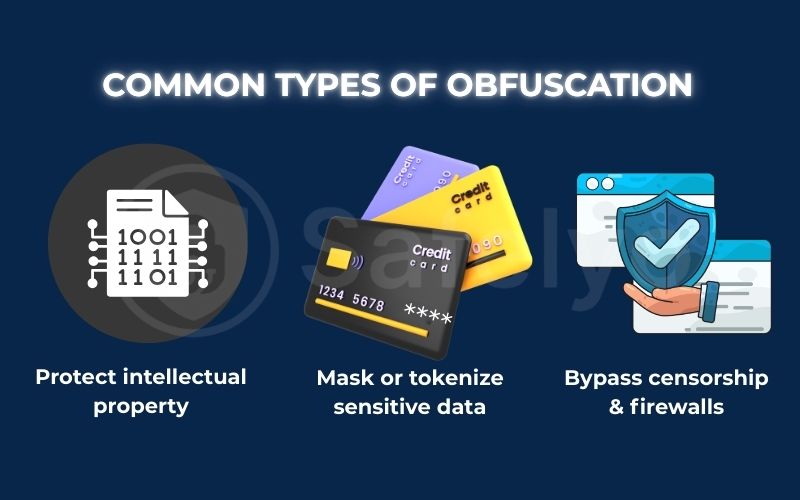
3. Common types of obfuscation: From code to VPN
Obfuscation is not just one technique; it’s a category of techniques applied in different fields for different reasons. While the core idea of “making things confusing” remains the same, the application varies. Here are the most common types you’ll encounter.
3.1. Code obfuscation: Protecting intellectual property
This is a technique used primarily by software developers. When you write a program, the source code is often structured, commented, and easy for a human to read and understand.
- The Goal: Code obfuscation is used to protect that hard work – the company’s intellectual property – from competitors who might try to steal it or analyze it through reverse engineering.
- How it Works: Automated tools take the readable source code and transform it into a functional equivalent that is incredibly difficult for a human to comprehend. They do this by renaming variables to meaningless labels (like a, b, c), inserting junk code that does nothing, and scrambling the logical flow of the program.
- The Result: The software or application runs exactly as it did before. However, trying to read its source code is quite difficult. It’s like reading a novel where all the nouns have been replaced with random numbers.
3.2. Data obfuscation: Securing sensitive information
This technique is all about protecting sensitive data, but in a slightly different way than encryption.
- The Goal: Data obfuscation is employed to protect sensitive information, such as real customer names, addresses, or credit card numbers, when used in non-production environments. This includes scenarios like software testing or developer training.
- How it Works: Instead of just scrambling the data, it’s replaced with realistic but fake data. Common techniques include:
- Data Masking: Replacing real data with fake but correctly formatted data. For example, the name “John Smith” might be replaced with “Adam Jones.” The format is the same, but the real information is protected from unauthorized access.
- Tokenization: Replacing a sensitive piece of data, like a credit card number, with a non-sensitive equivalent called a “token.”
3.3. VPN obfuscation: The key to internet freedom
For the everyday privacy-conscious user, this is the most important application of obfuscation.
- The Problem: In countries with heavy internet censorship, or on restrictive corporate or school networks, administrators don’t just block the IP addresses of known VPN servers. They use a technology called Deep Packet Inspection (DPI) to “look inside” your data packets and identify the characteristic signatures of VPN traffic.
- The Solution: VPN obfuscation is the digital camouflage that solves this problem. It disguises your VPN traffic to make it look like something else – usually, regular, boring HTTPS encryption traffic (the secure traffic used by almost every website today).
- The Result: The DPI system looks at your data, sees what appears to be standard web browsing, and lets it pass. This is the magic behind obfuscated servers and why they are so effective at defeating firewalls and providing access to a free and open internet.
4. The other side of the coin: Deobfuscation
Just as there are techniques to scramble and hide information, there are also techniques to try to reverse the process. The act of trying to make obfuscated data or code understandable again is called deobfuscation. This is a constant cat-and-mouse game in the world of cybersecurity.
Who uses deobfuscation?
- Security Researchers and Malware Analysts: This is the “good guy” use case. When a new piece of malware is discovered, it is almost always heavily obfuscated by its creators to hide its malicious purpose and evade detection by antivirus software. My colleagues in malware analysis spend their days using specialized tools and techniques to deobfuscate this code. By peeling back the layers of camouflage, they can understand what the virus is trying to do and develop ways to stop it.
- Competitors and Hackers: This is the “bad guy” use case. A rival company might try to deobfuscate a competitor’s software to perform reverse engineering and steal their trade secrets. Similarly, a hacker might try to find vulnerabilities in a piece of obfuscated code.
How hard is it?
Deobfuscating well-protected code is extremely difficult and time-consuming. While there are automated tools that can help reverse some of the simpler techniques, a multi-layered obfuscation strategy creates an incredibly complex puzzle. It often requires a significant amount of manual effort and expertise.
The goal of obfuscation isn’t to be impossible to crack, but to make the process so difficult and expensive that it’s not worth the attacker’s time or resources.
5. FAQ about the obfuscation
We’ve covered the core concepts of obfuscation, but you might still have a few specific questions. Here are direct answers to the most common queries we see about this powerful security technique.
What does obfuscate mean?
The correct spelling is “obfuscate.” The term means to deliberately make something confusing, unclear, or difficult to understand. It’s the act of making something obscure on purpose to conceal its true meaning or nature.
What is obfuscation in cybersecurity?
What is obfuscation in cybersecurity? It is a security technique used to disguise code or data to hide its true purpose. Unlike encryption, which makes data unreadable, obfuscation makes data look like something else entirely, helping it to evade detection by security systems or analysis by humans.
What does obfuscated mean on NordVPN?
When you see “Obfuscated Servers” in NordVPN, it refers to a special feature that uses VPN obfuscation. This feature disguises your VPN traffic to look like regular, secure HTTPS traffic. This is a powerful tool for bypassing firewalls and internet censorship in restrictive countries or on networks (like at school or work) that block standard VPN connections.
What does obfuscate mean? How it hides your VPN traffic
When you see “Obfuscated Servers” in NordVPN, it refers to a special feature that uses VPN obfuscation. This feature disguises your VPN traffic to look like regular, secure HTTPS traffic. This is a powerful tool for bypassing firewalls and internet censorship in restrictive countries or on networks (like at school or work) that block standard VPN connections.
What is an example of obfuscation?
A great example of obfuscation in action is code obfuscation. A software developer might take their human-readable source code (function calculate_salary) and use a tool to change it into something nonsensical (function aB1x()) before releasing the application. The program still works perfectly, but it becomes extremely difficult for a competitor to reverse engineer it.
What is the difference between obfuscation and encryption?
The fundamental difference lies in their purpose. Encryption secures data content by scrambling it with a key, while obfuscation conceals the data’s nature by disguising it to appear as something else. Encryption resembles a locked safe, whereas obfuscation is akin to a book with a hidden compartment.
6. Conclusion
So, what does obfuscate mean? It’s the art of smart camouflage – a technique of making things intentionally confusing to enhance security and privacy. It’s a powerful layer of defense that moves beyond simply locking data to actively hiding it in plain sight.
- Obfuscation makes data confusing to hide its nature, while encryption scrambles data to protect its content.
- It has many applications, from protecting source code (code obfuscation) to securing test data (data obfuscation).
- For internet users, the most important application is VPN obfuscation, which helps defeat sophisticated firewalls and censorship by making VPN traffic look like normal web traffic.
- Deobfuscation is the reverse process, used by security experts to analyze malicious code.
The next time you see the “obfuscated server” option in your VPN app, you’ll know exactly what it is: a powerful tool designed to give you true internet freedom, no matter where you are. To learn more about the technologies that protect your privacy, explore other in-depth guides in the Privacy & Security Basics section from Safelyo.













