If you’ve ever used WhatsApp or Signal, you’ve likely seen a notification pop up mentioning “end-to-end encryption”. But what is end-to-end encryption (E2EE) really, and why is that small message so critical for your digital privacy?
In simple terms, it’s the gold standard for secure communication. Think of it as a digital fortress that ensures only you and the person you’re communicating with can read what’s sent. Nobody in between, not hackers, not your internet provider, and not even the company that runs the app, can access the content.
As a privacy advocate and tech writer, I’ve spent years breaking down complex security topics. One of the most common questions I get from friends and family is, “What does that encryption pop-up on my phone actually mean?” It’s a fantastic question, because understanding this concept is your first step toward having truly private digital conversations in an age of constant data collection.
In this guide, I’ll break it all down for you. You will discover:
- What E2EE is, explained with a simple, easy-to-remember analogy.
- How it works behind the scenes, without the confusing jargon.
- The crucial difference between E2EE and other types of encryption.
- Its real-world benefits and, just as importantly, what it doesn’t protect.
Don’t just see the notification; understand the power behind it. Let me show you how to take control of your digital conversations, starting now.
What is End-to-End Encryption in a Nutshell?
If a service is end-to-end encrypted, only you and the person you’re talking to can ever see the content.
Definition
End-to-end encryption (E2EE) is a secure communication method that prevents anyone, including the service provider, hackers, or governments, from reading private data.
How it Works
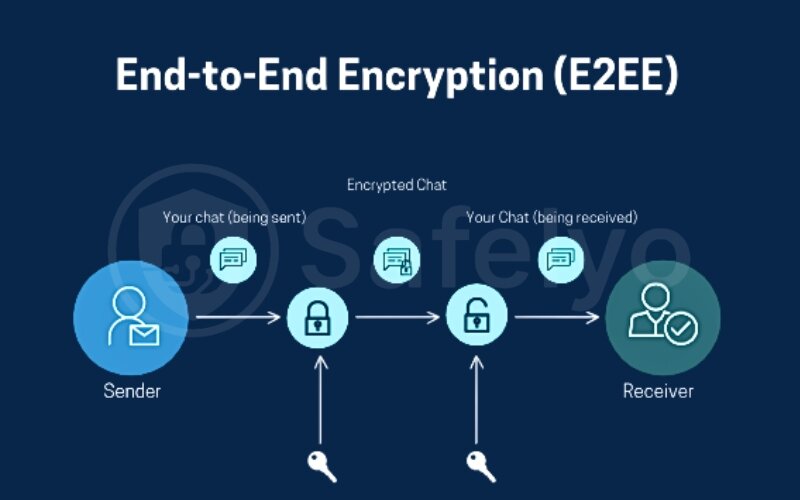
It locks (encrypts) a message on the sender’s device and can only be unlocked (decrypted) by the intended recipient’s device.
1. End-to-end encryption explained with a simple analogy
Forget about complex code and algorithms for a moment. The easiest way to truly grasp end-to-end encryption is with a simple story. We call it The Magic Mailbox Analogy.
Imagine you want to send a highly confidential letter to your friend, Bob.
Instead of a normal mailbox, Bob has given you a special, open padlock. Anyone can snap this padlock shut, but only Bob has the single, unique key that can open it. This open padlock is like Bob’s public key.
You write your secret letter, place it in a sturdy box, and snap Bob’s open padlock onto it. The moment it clicks shut, the box is securely locked. From this point on, no one can open it without Bob’s specific key, not even you.
Now, the mailman comes to pick up the locked box. He can see that the box is from you and that it’s going to Bob, but he has absolutely no way to peek inside. To him, the contents are just a mystery. This mailman is like the service provider (e.g., WhatsApp, your ISP).
Finally, the box arrives at Bob’s house. He takes out his personal, unique key, the only one in the world that can open that padlock. This is Bob’s private key. He unlocks the box and reads your message, exactly as you wrote it.
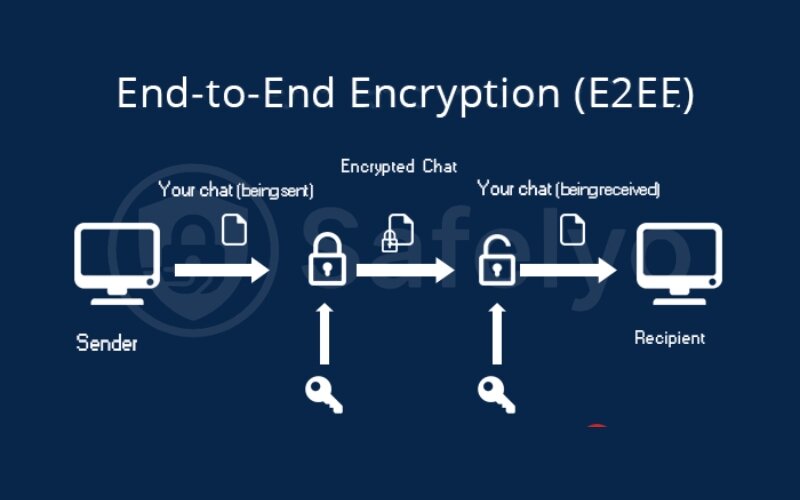
That’s the core idea. End-to-end encryption works just like this. Your message is locked with a recipient’s public key, and only the recipient with the corresponding private key can ever unlock and read it.
2. How does end-to-end encryption work technically?
Now that the magic mailbox analogy is clear, let’s peek under the hood and see how your phone actually pulls this off. It all comes down to a clever concept called asymmetric encryption, which uses a matched pair of keys.
When I first started exploring cybersecurity, this concept of two different keys was the biggest “aha!” moment. It’s the secret sauce that makes the whole system work.
- Public Key: Think of this as your digital mailing address. You can share it with anyone who wants to send you a secure message. It’s public information, and its only job is to lock messages. There’s no risk in sharing it.
- Private Key: This is like the key to your front door. It lives only on your device, and you never, ever share it. Its only job is to unlock messages that were locked with your public key.
These two keys are mathematically linked, but you cannot figure out the private key just by looking at the public key. This is the one-way magic that makes modern encryption possible.
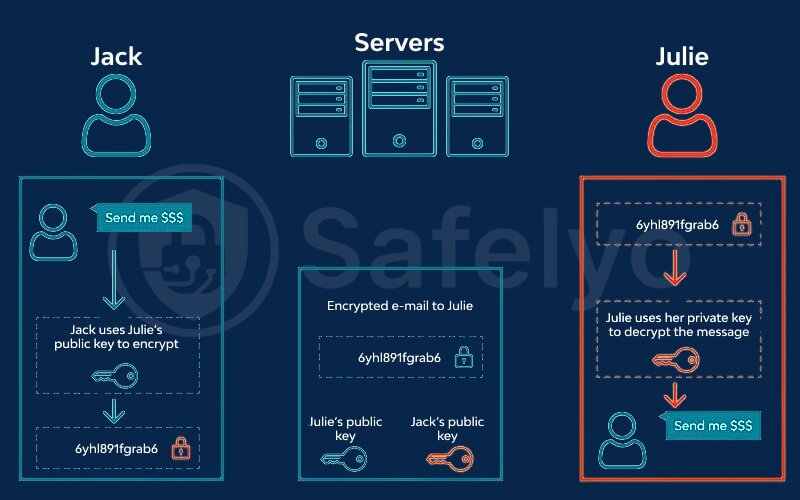
So, how do these keys work together in a real chat? It happens in four seamless steps:
- The Handshake: The moment you start a conversation with a new person, your messaging apps automatically and invisibly exchange public keys. You don’t have to do anything; it happens instantly and automatically in the background. It’s like you and your friend agreeing to use the magic mailbox system before you even write the first word.
- Encryption: You type your message, “See you at 8?”. Before the message leaves your phone, your app uses the recipient’s public key to scramble it into unreadable gibberish. This is the digital version of snapping the padlock shut. The message now looks something like Ag8bZ&k9@vB#x!fPqR$sT.
- Transmission: This scrambled, unreadable data travels across the internet. It passes through the company’s servers (like WhatsApp’s or Signal’s). If a hacker or an employee were to intercept it, all they would see is that meaningless string of characters. It’s completely useless to them.
- Decryption: The message arrives at your friend’s device. Their app then uses their unique private key, the only key in the world that can, to instantly unscramble the message back into “See you at 8?”.
This whole process happens for every single message, in the blink of an eye.
The engine behind modern E2EE: The Signal Protocol
Now, you might be thinking, “That sounds incredibly complicated. Do app developers build this from scratch every time?”
Thankfully, no. Most popular messaging apps you use today, like WhatsApp and Signal itself, don’t reinvent the wheel. They use a highly vetted, open-source technology called the Signal Protocol.
Think of it like a car manufacturer. Instead of designing a brand-new, untested engine for every car model, they use a proven, high-performance engine that has been tested for safety and reliability. The Signal Protocol is that pre-built, ultra-secure engine for encryption. Developers can integrate it into their apps to provide best-in-class E2EE, knowing it’s been scrutinized by security experts worldwide.
3. E2EE vs. Encryption in transit
This is where many people get confused, and frankly, it’s the most important distinction to understand. You might be thinking, “Wait, when I visit my bank’s website, I see a little padlock icon. Isn’t that already encrypting my data?”
That’s an excellent question. The answer is yes, that padlock signifies encryption, but it’s a different, less powerful type called encryption in transit. When I explain this to people, I use the analogy of an armored truck versus a magic-locked box.
Encryption in transit (like TLS/HTTPS)
This is the standard security for most of the web – it’s what the padlock icon in your browser represents.
- What it is: It protects your data on its journey between your device and the company’s server. Think of it like an armored truck carrying cash from your local branch to the main bank headquarters. The truck is secure and protected from robbers on the road.
- The weakness: Once the armored truck reaches the bank’s headquarters (the server), the bank guards unlock it, count the money, and see everything inside. Similarly, when your data reaches Google’s or your bank’s server, the company can decrypt and read it. They hold the keys. They need this to process your search query or bank transfer, but it also means they have access to the content.
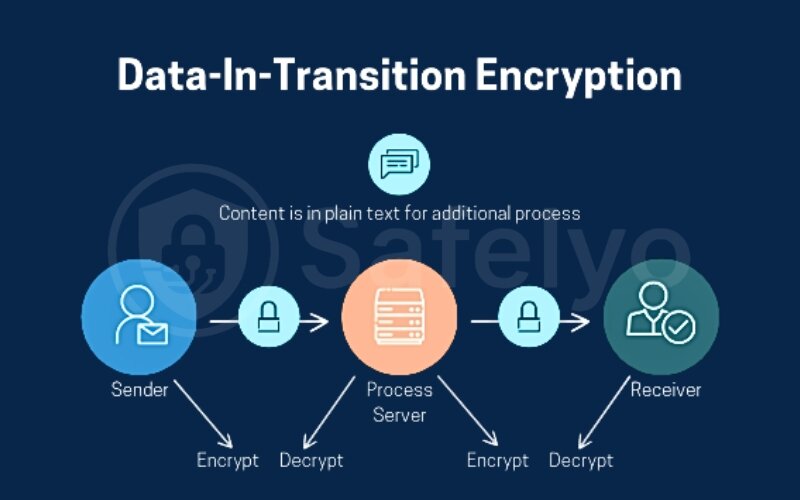
End-to-end encryption (E2EE)
This is where the magic mailbox analogy from before comes back into play. With E2EE, the company providing the service is no longer the bank headquarters; they are just the mailman. They can transport the locked box, but they never, ever get a copy of the key. The data is encrypted on the sender’s device and can only be decrypted on the recipient’s device.
Here’s a simple table to make the difference crystal clear:
| Feature | Encryption in Transit (HTTPS/TLS) |
End-to-End Encryption (E2EE) |
|---|---|---|
| Who can read your data? | You, the service provider (e.g., Google, Facebook), and the recipient. | Only you and the recipient. |
| Protection from server breaches? | No. If the company’s server is hacked, your unencrypted data could be exposed. | Yes. If the server is hacked, thieves only get scrambled, useless data. |
| Common Example | Visiting your bank’s website or browsing Amazon. | Sending a message on Signal or WhatsApp. |
Ultimately, while encryption in transit is good and essential for the modern web, end-to-end encryption provides a far superior level of privacy.
4. The real-world benefits of using E2EE
Okay, so we’ve covered the what and the how. But why does all this technical wizardry matter to you? What are the tangible, everyday benefits of using apps and services with end-to-end encryption?
As someone who writes about digital rights, I see these benefits not as abstract features, but as essential protections for modern life.
Ultimate privacy from prying eyes
This is the most obvious benefit. Your private conversations, photos, and shared documents remain truly private. You can be confident that no one is eavesdropping, not the app developer trying to mine your data for ads, not your internet service provider (ISP), and not government agencies conducting mass surveillance.
It makes a private conversation digital. For instance, a sensitive health discussion with a family member or a confidential business plan shared with a partner remains just between the two of you.
Powerful protection from data breaches
We hear about major companies getting hacked all the time. If a service you use suffers a data breach, E2EE is your best defense. Hackers might break into the company’s servers, but if your messages are end-to-end encrypted, all they will steal is a mountain of scrambled, useless data.
They can’t read your chats because they don’t have the private keys, which are safe on your device. It’s like a thief breaking into the post office; they can steal the mailbags, but they can’t open any of the magically locked boxes inside.
Defense against man-in-the-middle attacks
A “man-in-the-middle” attack is when an attacker secretly intercepts and relays communication between two parties. Good E2EE systems have a built-in verification mechanism (like comparing security codes or scanning a QR code) that ensures you are talking directly to the person you think you are. This feature confirms that no one is secretly listening in or altering your messages in transit.
Empowering freedom of speech
This benefit is critically important on a global scale. For journalists working on sensitive stories, activists organizing in repressive countries, or simply citizens who want to discuss politics without fear of reprisal, E2E is a lifeline.

It provides a safe digital space for free expression and dissent, which is a cornerstone of a free society. It ensures that the act of communicating cannot be used against you.
5. What end-to-end encryption doesn’t protect
End-to-end encryption is an incredibly powerful tool for privacy, but it’s not a magic invisibility cloak that protects you from everything. In my experience, understanding the limitations is just as crucial as understanding the benefits. A false sense of security can be more dangerous than no security at all.
Let’s look at what E2EE doesn’t do.
It doesn't hide your metadata
This is the most common misconception I have to clear up. E2EE protects the content of your message, but not the context (the metadata).
Think back to our mail analogy. The letter inside the box is secret, but anyone can still look at the outside of the box to see who sent it, who it’s going to, when it was sent, and how big it is.
In the digital world, this means your service provider (like WhatsApp) can’t see what you said, but they can see that you communicated with Bob at 3:15 PM and exchanged five messages. This metadata alone can reveal a lot about you.
Endpoint security is still your responsibility
E2EE protects your message while it’s traveling between devices. But it can’t protect the devices themselves, which we call the “endpoints.”
I like to say that using E2EE on a hacked phone is like putting a massive steel vault door on a house made of cardboard. If an attacker has compromised your or the recipient’s device with malware or spyware, the encryption becomes useless. The attacker can simply read messages as you type them (before encryption) or as you read them (after decryption).
It doesn't make you anonymous
Privacy and anonymity are not the same thing. E2EE gives you privacy by hiding the content of your communication. It does not make you anonymous. Your IP address, a unique identifier for your internet connection, might still be visible to the service provider.
Think of the IP address as the return address on the outside of that locked box. The mailman might not know what’s inside, but he knows where it came from. For true anonymity, you would need to combine E2EE with a tool like a no-logs VPN.
>> To learn more about hiding your IP address, read our complete guide on what a VPN is and how a VPN works.
It doesn't protect against government-mandated "backdoors"
A backdoor is a deliberate weakness built into an encryption system, often at the request of a government agency, to allow them access. Think of it as forcing the locksmith to secretly create a master key that can open all the magic mailboxes. While most secure services publicly resist creating backdoors, the threat remains a contentious political issue.
This leads directly to a major societal debate known as the “Going Dark” problem. Law enforcement agencies argue that strong, unbreakable E2EE allows criminals and terrorists to communicate in secret, hindering investigations. On the other hand, privacy advocates and security experts argue that any backdoor created for the “good guys” will inevitably be found and exploited by the “bad guys,” putting everyone’s security at risk. This is a core conflict of the digital age with no easy answer.
6. End-to-end encrypted apps you’re probably already using
The great news is that you don’t have to be a security expert to use end-to-end encryption. In fact, you’re probably already using it every single day without even thinking about it.
Over the years, I’ve watched E2EE go from a niche feature for cypherpunks to a mainstream standard. Here are some of the most common apps and services where this powerful protection is at work.
Messaging apps
This is where E2EE has become the new normal.
- Signal: Widely considered the gold standard by security researchers (including myself). Everything on Signal is end-to-end encrypted by default, including one-on-one chats, group chats, and voice/video calls. They also pioneer new ways to minimize metadata collection.
- WhatsApp: Owned by Meta (Facebook), WhatsApp is the most popular E2EE app in the world. It uses the excellent Signal Protocol to encrypt all personal messages, group chats, and calls by default.
- iMessage: When you see those “blue bubbles” on your iPhone, you’re using E2EE. Apple automatically enables it for all conversations between Apple devices. (Note: The “green bubbles” are standard SMS messages, which are not encrypted.)
Email services
Traditional email (like standard Gmail or Outlook) is a classic example of “encryption in transit,” not E2EE. The providers can and do scan your emails. However, some services are built from the ground up for privacy.
- ProtonMail & Tutanota: These are the two biggest names in secure email. They are designed with E2EE as a core, non-negotiable feature. Emails between users on the same service are automatically end-to-end encrypted.
Video conferencing
The shift to remote work brought E2EE to the forefront for video calls.
- Zoom, Google Meet, & Microsoft Teams: After some initial privacy concerns, all the major players now offer E2EE for meetings. However, there’s a catch: in most cases, it’s an optional feature that you must manually turn on, and it might disable other features like live transcription or cloud recording.
Knowing which apps use E2EE by default versus which ones require you to flip a switch is a key part of making informed privacy choices.
>> Want to find the most secure option? Check out our detailed comparison of the Best Encrypted Messaging Apps.
7. FAQ about E2EE – End-to-end encryption
Here are the answers to some of the most common questions we get about end-to-end encryption.
What is meant by end-to-end encryption?
End-to-end encryption (E2EE) is a communication method that secures a message so that only the sender and the intended recipient can read it. No one in between, including the app provider or your internet service provider, can access the content.
Is it good to turn on end-to-end encryption?
Yes, it is highly recommended. Turning on E2EE is one of the best steps you can take to ensure your digital conversations, photos, and files remain truly private and secure from hackers, corporations, and other third parties.
What are the disadvantages of end-to-end encryption?
The main disadvantages are that it doesn’t hide metadata (who you talked to and when), and it cannot protect your messages if your device is compromised with malware. Some also argue it presents challenges for law enforcement investigations.
What will happen if you turn off the end-to-end encryption?
If you turn off E2EE, your messages revert to a lower level of security, likely “encryption in transit.” This means the service provider will have the ability to read, scan, or turn over your message content because they hold the encryption keys on their servers.
If an app is end-to-end encrypted, is it 100% safe?
Not necessarily. While the message content is extremely secure during transit, your security is only as strong as your weakest link. If your phone has malware (a compromised “endpoint”), an attacker could read messages before they are encrypted or after they are decrypted on your device.
Can police read my end-to-end encrypted messages?
No, they cannot read the message content directly from the service provider. By design, the company doesn’t have the keys to decrypt the data. However, authorities can request metadata or attempt to gain access to the physical device to read the messages there.
Since Meta owns WhatsApp, can Facebook read my WhatsApp messages?
No. This is a key benefit of E2EE. Because WhatsApp uses strong end-to-end encryption, the content of your personal messages is scrambled in a way that even its parent company, Meta (Facebook), cannot access or read.
What is the difference between E2EE and a VPN?
They protect different things. E2EE protects the content of a specific message, like a letter in a sealed envelope. A VPN protects your entire internet connection, hiding your online activity from your ISP and changing your IP address, like making the entire mail truck’s route private.
8. Conclusion
So, what is end-to-end encryption? In the simplest terms, it is your personal digital privacy shield. It’s the modern-day equivalent of a sealed letter, ensuring that your private conversations remain exactly that, private. By converting your messages into a scrambled code that only your recipient’s device can unlock, E2EE stands as a powerful defense against the prying eyes of hackers, corporations, and even the service providers themselves.
To make sure the most important ideas stick, here are the key points to remember from this guide:
- For Your Eyes Only: The core principle of E2EE is that only the sender and the intended recipient can read the message content.
- The Provider is Blind: Unlike other forms of encryption, the company that runs the service (like WhatsApp or Signal) cannot decrypt and see your messages.
- Content vs. Context: E2EE protects the content of your messages but does not hide the metadata (like who you talked to and when).
- Endpoint Security is Key: Your encryption is useless if your or the recipient’s device has been compromised with malware.
- It’s Already in Your Pocket: You use E2EE every day in popular apps like WhatsApp, Signal, and iMessage.
Understanding this technology is a fundamental step toward taking control of your digital life. Here at Safelyo, we believe that knowledge is the best tool for self-defense in the online world. Continue building your expertise and stay secure by exploring more topics in our Privacy & Security Basics category.













