Do you have that unsettling feeling that someone is supervising everything you do on your phone? Stalkerware can turn an ordinary smartphone into a powerful surveillance device without you realizing it. This overwhelming fear is common among victims when they begin to suspect the presence of stalkerware, especially in relationships with controlling partners. If so, you need to know about what is stalkerware – a dangerous type of spyware often used in abusive relationships.
Many survivors report that tech-based control is just one part of broader domestic abuse patterns. Stalkerware operates in complete secrecy, designed to record your text messages, log your calls, track your location, and send all this information back to an abuser without your knowledge. Many advanced tools continuously collect your geolocation data to map your movements in real time. This type of malicious software is intentionally engineered to stay invisible, making it extremely difficult for the victim to detect.
This guide goes beyond a simple definition. Understanding how this hidden software behaves is essential to taking the correct safety steps. More importantly, it provides a safety-first action plan to help you check your device, remove the malicious software, and connect with help if you need it.
If you’re worried your phone is being monitored and need answers fast, start here. This guide will walk you through what stalkerware is and, most importantly, how to deal with it safely.
- What is stalkerware? It’s a type of commercially sold spyware that someone can secretly install on your phone to track your location, read your messages, and monitor all your activity without your consent. This behavior is a form of digital stalking, allowing the abuser to follow every detail of your online and offline life. In many cases, this relentless tracking happens in real time, giving the abuser constant updates about your movements.
- Your safety comes first. Before trying to remove anything, understand that doing so can alert the person to supervision. If you feel you are in any physical danger, contact a domestic violence hotline from a safe device before touching your phone. Technology-facilitated harm frequently overlaps with domestic abuse, making proper support even more critical.
- Look for the warning signs. Common signs of stalkerware include a rapidly draining battery, a spike in data usage, and your phone overheating. The clearest sign, however, is when someone knows things about your private life that they shouldn’t. Such information leaks are a direct result of continuous tracking by a hidden app.
- Follow a safe removal plan. First, use a different, safe device to change your important passwords (email, banking). Using a secondary device prevents the attacker from seeing what changes you are making in real time. Then, use a reputable antivirus app on your phone to scan for and remove the stalkerware. A factory reset is the only way to be 100% sure it’s gone.
Your physical and digital safety is the number one priority. Let’s walk through the steps with me to take back your control and your privacy.
1. What is stalkerware? How does it work?
With the safety precautions in mind, let’s break down what this invasive software really is and how it operates in the shadows.
1.1. A definition: Commercially sold spyware
At its core, stalkerware is a type of commercially available software that someone can buy online and secretly install on another person’s phone. Its sole purpose is to monitor that person’s activity without their consent. Some advanced variants even analyze the victim’s digital activity patterns to predict routines and habits.
How does stalkerware work? Once installed, the app hides itself from the home screen and runs invisibly in the background. This hidden behavior creates a powerful surveillance system operating without the victim’s awareness. It silently collects a vast amount of data – including your location, text messages, photos, call logs, and even conversations happening near the phone – and uploads it to an online dashboard. Some variants even archive your complete call history, giving the abuser insight into who you communicate with most often.
Such constant surveillance allows the abuser to build a complete picture of the victim’s daily life. When combined with access to browser history, the abuser gains an even more detailed understanding of your thoughts, concerns, and online behavior. The stalker can then log into this dashboard from their own device, anywhere in the world, to see everything you’re doing. This remote dashboard essentially turns the phone into a surveillance tool controlled by someone else.
1.2. Spyware vs. stalkerware vs. parental control apps
These terms are often used interchangeably, but the intent behind them is very different. Understanding this distinction is key. I’ve seen many stalkerware apps disguise themselves as “employee monitoring” or “child safety” tools, but their true nature is revealed by their features that promote total secrecy.
Here’s a quick breakdown of the differences between spyware vs. stalkerware vs. parental control apps:
| Feature | Stalkerware | Parental Control Apps | General Spyware |
|---|---|---|---|
| Visibility | Designed to be completely hidden | Visible with icon and notifications | Varies, but often hidden |
| Target | A specific person the user knows (e.g., a partner) | A child, with the parent’s knowledge | A large, anonymous group of victims |
| Consent | No consent from the victim | Implied consent or user awareness | No consent from the victim |
| Purpose | Interpersonal spying and control | Child safety and monitoring | Financial gain or data theft |
In short, while the technology can be similar, the key difference is deception and consent. Legitimate parental control apps operate openly, whereas stalkerware’s entire purpose is to remain a secret. This transparency allows the user to understand exactly what data is being collected and why.
2. Signs of stalkerware to see if your phone is being tracked
If you have a gut feeling that something is wrong, you should trust it. While a single symptom could be a glitch, a pattern of several is a major red flag. Use this checklist to look for common signs of stalkerware on your phone.
| Symptom Category | What to look for |
| Performance Issues | Battery drains unusually fast; device overheats or runs slowly. |
| Data & Connectivity | Sudden spike in mobile data consumption; strange noises during calls. |
| Unexplained Changes | Unknown apps appear; security settings are altered without permission. |
| Real-World Evidence | The person you’re concerned about knows private information they shouldn’t. |
Now, let’s look at each of these warning signs in more detail.
Unusually battery consumption
Is your phone’s battery dying much faster than usual, even when you’re not actively using it? intrusive software runs constantly in the background, using the GPS and uploading your data, which consumes a huge amount of power.
Higher data usage
Have you noticed a sudden, unexplained spike in your mobile data consumption? That’s because the stalkerware app is constantly sending large amounts of information to the stalker’s server. Some variants even monitor activity on your social media, giving the stalker insight into your online interactions.
The device is slow or overheats
Does your phone frequently feel warm to the touch, even when idle? Or does it lag and freeze for no reason? This happens because the hidden app is always working, straining your phone’s processor.
>> You may also be interested in: Does Norton Antivirus slow down the computer? 5 easy ways to fix
Strange background noises during calls
While less common with modern stalkerware, do you sometimes hear faint clicking, static, or echoing sounds during phone calls? This can be a sign that a third-party app is trying to record your conversations.
Unknown apps or files
Have you found an app that you don’t remember installing? Remember to check the full app list in your phone’s settings, not just your home screen, as these apps are designed to be hidden.
Security settings have been changed
This is a big one. For stalkerware to be installed on an Android, a setting called “allow installs from unknown sources” often needs to be enabled. If you find this setting is on, and you didn’t do it, your device has been tampered with.
>> Read to know: How to remove a hacker from my phone? 4-step emergency guide
The person you're worried about knows things they shouldn't
From my experience, this is often the most undeniable sign. They might mention something you only said in a private text message, or know a specific location you visited. Technical glitches can be explained away, but someone knowing your private information is the clearest indicator of how to tell if your phone is being tracked.

3. Before you do anything, consider your personal safety
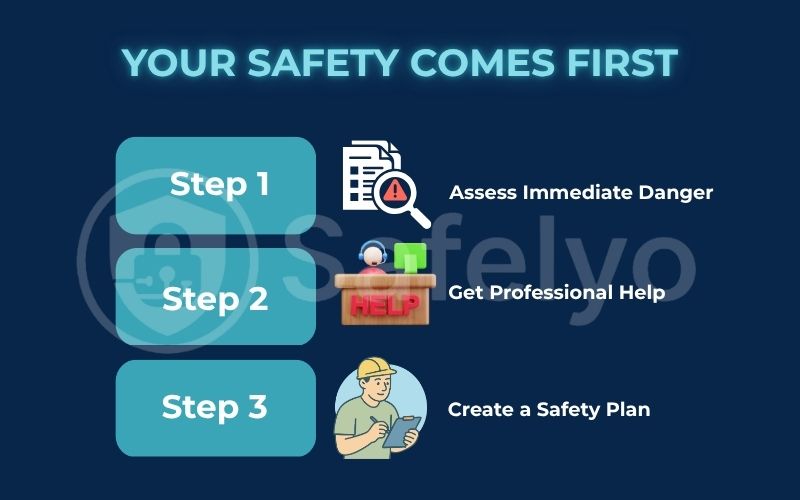
WARNING: YOUR SAFETY COMES FIRST
This is the most important part of this guide. Please read it carefully before taking any action on your phone.
Removing stalkerware can alert the abuser.
These apps are designed to notify the person who installed them if the app is removed or the phone is tampered with. If you suddenly delete the software, the stalker will know they’ve been discovered. From my experience in handling these cases, this can cause the situation to escalate and potentially put you in physical danger.
If you are in immediate danger, seek help first.
Before you change anything on your device, your priority is to ensure you are safe. Contact a domestic violence support organization. They are trained to help you create a safety plan.
Create a safety plan before acting.
- Use a safe, different device – like a computer at a public library or a trusted friend’s phone – to research your options and contact help. Do not use the suspected device for these activities.
- Consider documenting evidence. If it is safe for you to do so, take screenshots of any suspicious apps you find before deleting them. This could be useful later.
- Trust your instincts. You know your situation best.
I cannot stress this enough: Your personal safety is more important than your phone’s security. Please prioritize it above all else.
4. How to check for and remove stalkerware
If you’ve identified several warning signs, it’s time to take action. Follow these steps in order. Remember the safety warning from the beginning of this article: Proceed only if you feel it is safe to do so.
Here’s a quick overview of the action plan:
- Step 1 (Safe Device): Use a different, trusted device to change all your important passwords first.
- Step 2 (Antivirus Scan): Install a reputable mobile security app on the suspected phone and run a full scan.
- Step 3 (Manual Check): Manually inspect your phone’s app lists and security settings for anything suspicious.
- Step 4 (Factory Reset): For 100% certainty, perform a factory reset to completely wipe the device clean.
Now, let’s look at each step in more detail.
4.1. Step 1: Secure your critical accounts on a safe device
This is the most crucial first step, and it must be done before you touch the suspected phone.
Why? Because the moment you remove the stalkerware, the abuser may be alerted. In my experience, their first move is often retaliation, which can include using the passwords they’ve stolen to lock you out of your email or bank accounts.
Using a computer at a library, a new device, or a trusted friend’s phone, immediately change the passwords for your most important accounts. This includes:
- Your primary email account (like Gmail or Outlook).
- Your Apple ID or Google Account.
- Your online banking and financial apps.
By doing this first, you cut off their access and protect your digital life before they know they’ve been discovered.
4.2. Step 2: Run a scan with a reputable mobile antivirus
Now, you can turn your attention to the phone. The easiest way to find stalkerware is to use a tool designed for the job.
Go to the official Google Play Store or Apple App Store and install a trusted mobile security app. From a professional perspective, I recommend using apps from reputable cybersecurity companies like Malwarebytes, Avast, or Bitdefender. Their threat detection engines are specifically designed to recognize the signatures of common stalkerware apps.
Once installed, run a full system scan. The app will check all your files and installed applications against its database of known threats and alert you if it finds anything suspicious.
>> You may also be interested in: How to add a website to Avast Antivirus in 6 quick easy steps
4.3. Step 3: Manually inspect your phone
An antivirus scan is powerful, but sometimes a manual check can uncover things it might miss.
For Android users:
- Go to Settings > Apps > See all apps. Look through the entire list for any app names you don’t recognize. Some stalkerware uses generic names like “Sync” or “Device Health” to avoid suspicion. These hidden apps may also quietly sync your browser history, exposing sensitive searches or websites you’ve visited.
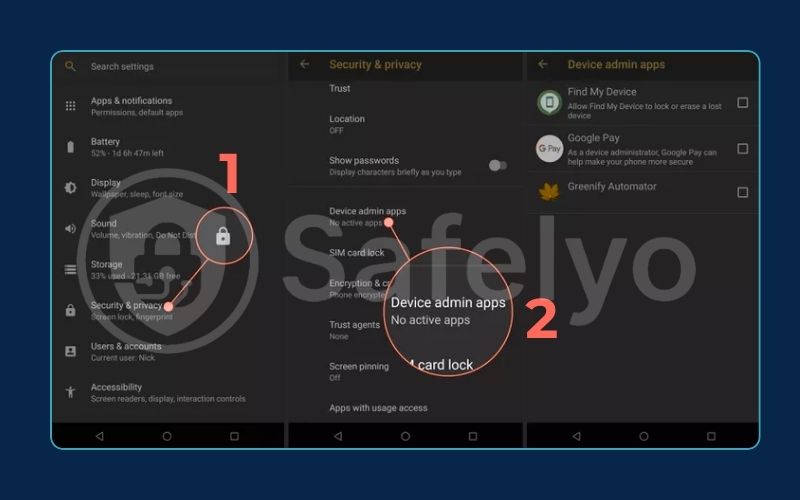
- Check your admin permissions. Go to Settings > Security & privacy > Other security settings > Device admin apps. Stalkerware often abuses elevated permissions to maintain control and hide from normal app lists. No app should have this level of control unless you specifically granted it (like for a work email). Reviewing which permissions each app has requested can immediately reveal red flags. If you see an unknown app here, deactivate it. Revoking dangerous permissions limits what the stalkerware can access even before you fully remove it.
>> More for Android Antivirus:
For iPhone users:
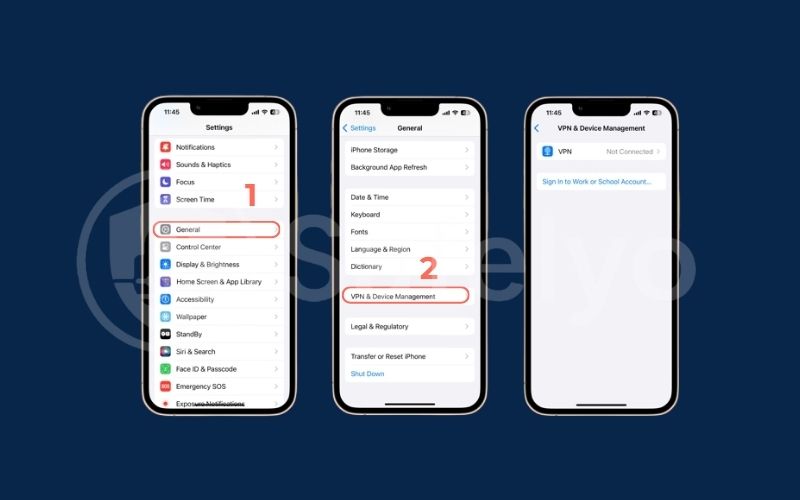
- Stalkerware on an iPhone is much harder to install unless the phone has been jailbroken. Look for apps on your home screen that you didn’t install, specifically “Cydia” or “Sileo“. The presence of these apps is a near-certain sign of a jailbreak.
- Check for suspicious profiles. Go to Settings > General > VPN & Device Management. If you see any “Configuration Profiles” that you don’t recognize (especially if they are not from your employer or school), it’s a major red flag.
>> More for iPhone Antivirus:
4.4. Step 4: The ultimate solution – a factory reset
If you’ve found suspicious apps or simply want absolute certainty, there is only one foolproof method for how to remove stalkerware: a factory reset. Does a factory reset get rid of viruses?
A factory reset will completely erase everything on your phone – all apps, images, data, and settings – and restore it to its original, out-of-the-box state. This process eliminates any hidden software, including any trace of intrusive software.
Warning: Before you do this, make sure you back up only your essential personal files, like photos and contacts, to a cloud service. Do not perform a full backup and restore, as this could potentially bring the stalkerware back onto your clean device.
5. How to protect yourself from stalkerware in the future
Once your device is clean, the next step is to ensure this never happens again. Long-term prevention requires forming strong digital habits that reduce opportunities for someone to tamper with your phone. Protecting yourself from stalkerware is about practicing good digital hygiene. Here are the most effective habits to adopt.
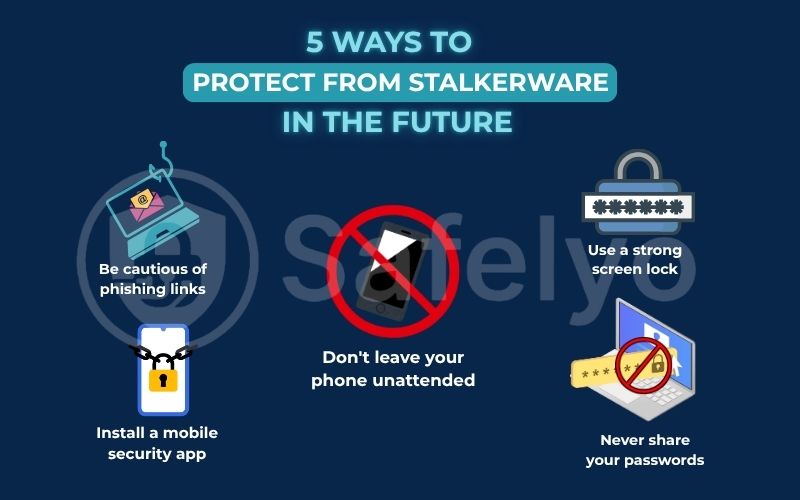
Use a strong screen lock
This is your most basic and essential defense. Always secure your phone with a strong passcode, PIN, fingerprint, or Face ID. This step is essential for blocking unauthorized access, which is the most common doorway for stalkerware attacks. A simple “swipe to unlock” is not enough. In my experience, the vast majority of stalkerware installations happen because the abuser had easy, physical access to an unlocked phone.
Never share your passwords
Treat your phone’s passcode and your Apple/Google account passwords like your toothbrush – don’t share them with anyone. Giving someone your iCloud or Google password can allow them to access your backups, photos, and location without ever touching your phone.
Don't leave your phone unattended
It only takes a few minutes for someone to physically install stalkerware on an unlocked device. Be mindful of where you leave your phone, especially around people you may not fully trust.
Install a mobile security app
Don’t just use an antivirus for a one-time scan. Keep a reputable mobile security app installed on your phone for real-time protection. It can warn you if you attempt to install a suspicious app and can regularly scan for new threats.
Be cautious of phishing links
While less common, some advanced stalkerware can be installed remotely if you are tricked into clicking a malicious link sent via text or email. Be wary of any unexpected links, even if they seem to come from someone you know.
You may also be interested in this article: What is a Trojan virus: 6 warning signs to watch out
6. FAQs about stalkerware
It’s natural to have more questions about such a serious topic. Here are direct answers to some of the most common queries we receive about stalkerware.
What is stalkerware?
Stalkerware is commercially available software designed to be secretly installed on someone’s phone to monitor their activity without consent. It can track location, record calls, read messages, and more, all while remaining hidden from the user.
Can stalkerware be installed remotely without physical access?
In most cases, no. The majority of stalkerware apps require the abuser to have physical access to an unlocked phone to install them. However, some can be installed remotely if the victim is tricked into clicking a malicious phishing link.
Can an antivirus detect all stalkerware?
Reputable antivirus and mobile security apps are very effective at detecting most known stalkerware. However, early detection also depends on noticing unusual behavior from your phone before the threat escalates. However, new variants are always being created, so it’s possible a brand-new or custom-built app might go undetected. This is why a factory reset is the only 100% guaranteed elimination method.
What’s the difference between stalkerware and parental control apps?
The key difference is consent and transparency. Legitimate parental control apps are visible on the device, often with notifications, and are used with at least the implied consent of the child. Stalkerware is designed to be completely hidden and operates without the victim’s knowledge or permission.
7. Conclusion
Ultimately, what is stalkerware is not just a technology issue – it is a profound violation of privacy and a tool of abuse. Recognizing its signs and knowing how to act is a critical step in reclaiming your digital and personal safety.
You deserve to feel safe, both online and off. If you or someone you know is in this situation, please remember that help is available. To learn more about protecting yourself from digital threats, explore the other guides from Safelyo in our Antivirus category.













