Every day, you see a padlock icon in your browser, a notice that your WhatsApp messages are “end-to-end encrypted,” or hear about “military-grade” security. At the heart of all these is one powerful concept: Encryption. It’s the invisible shield of the digital world, protecting your most sensitive information.
In today’s interconnected society, understanding how this shield works isn’t just for tech experts – it’s essential for everyone. What is encryption? Simply put, it’s the process of turning your readable data into a secret code, ensuring that only the right people can ever read it.
As a security analyst, I’ve seen many explanations of data encryption that are filled with complex jargon, making the topic feel inaccessible. My goal here is to change that by explaining this crucial technology in a way that everyone can understand.
In this comprehensive guide, you’ll discover:
- How encryption works, explained with a simple “secret lockbox” analogy.
- The difference between the two main types of encryption.
- Why is this technology so critical for your daily online safety?
- There are many ways you use it every day without even realizing it.
Your privacy depends on this powerful technology. Let me unlock the secrets of encryption and show you how it works to keep you safe.
What is Encryption in 30 seconds?
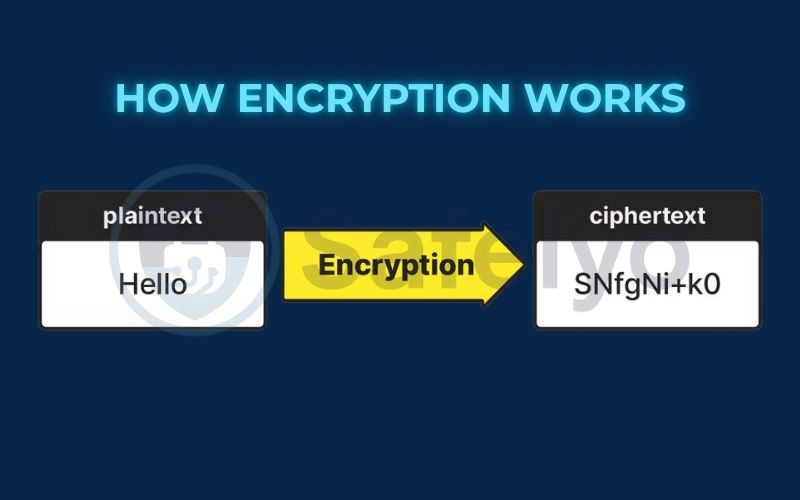
Encryption is the process of scrambling readable data (plaintext) into an unreadable secret code (ciphertext). Think of it as putting a message in a digital lockbox. To lock and unlock this box, you need a special encryption key. This process is the foundation of modern cybersecurity, protecting everything from your online banking to your private messages.
1. What is encryption, and how does it work?
To understand how encryption works, let’s forget about computers and algorithms for a moment. The best way I’ve found to explain this powerful concept is with a simple story about a secret lockbox.
Plaintext (The Secret Message)
Imagine your data – an email, a password, your credit card details – is a secret message written on a piece of paper. This readable, original form is called plaintext. Anyone who finds this piece of paper can read your secret.
Encryption (Locking the Box)
What is encryption? It is the process of transforming your plaintext message into a special, secure lockbox. Once locked, the message inside is scrambled into a secret code. This is the essence of data encryption.
Ciphertext (The Locked Box)
This scrambled, unreadable code is called ciphertext. If a thief intercepts this locked box during delivery, all they’ll see is meaningless gibberish like _@#&%*!_. Your message is completely safe and unreadable to them. The difference between plaintext and ciphertext is the difference between an open letter and a locked safe.
The Encryption Key (The Key to the Lockbox)
To lock the box, you need a unique encryption key. This is a secret piece of information, similar to a long and complex password. It is used by a specific algorithm to scramble data in a precise way.
Decryption (Unlocking the Box)
To read the message, the intended recipient must have the correct key to unlock the box. This process of using the key to turn the ciphertext back into readable plaintext is called decryption. Without that specific key, the lockbox remains permanently sealed.
2. The two main types of encryption: How keys are shared
Our secret lockbox is a great start, but in the digital world, there’s a crucial question: how do you get the key to the recipient safely? The solution to this puzzle leads to the two main types of encryption. From my experience, understanding this difference is the “aha!” moment for most people learning about this topic.
2.1. Symmetric encryption (the identical key)
This is the most straightforward method. In symmetric encryption, both the sender and the receiver use the exact same secret key to both lock and unlock the box. It’s like making a perfect copy of your house key for a trusted friend.
PROS
This method is extremely fast and efficient. Because it uses a single, simpler operation, it’s perfect for encrypting large amounts of data without slowing things down. This is why it’s the workhorse for tasks like streaming a 4K movie over a VPN.
CONS
The biggest challenge is securely sharing that single key in the first place. If you send the key over an insecure channel (like a regular email), an eavesdropper could intercept both the key and the locked box, rendering the encryption useless.
Famous example: AES encryption (Advanced Encryption Standard) is the most famous and widely used symmetric algorithm in the world. It’s the standard for the U.S. government and is used in virtually every top-tier VPN.
2.2. Asymmetric encryption (the two-key system)
This is a much more clever solution to the key-sharing problem, and it’s the magic behind much of the internet’s security. In asymmetric encryption, the recipient has two keys that are mathematically linked:
- A public key, which is like an open padlock. They can give this padlock to everyone without any risk.
- A private key, which is the only key in the world that can open that specific padlock. They never, ever share this key.
How it works: You want to send a secret message. The recipient provides their “open padlock” (public key), which you use to secure your message box. Once the padlock is locked, only their unique private key can unlock it. Since you never had to send a secret key, the issue is resolved.
PROS
It’s incredibly secure for establishing communication and verifying identity without prior key sharing.
CONS
This process is more complex and much slower than symmetric encryption.
Famous examples: RSA and ECC are the most common asymmetric algorithms, used for everything from securing HTTPS websites to creating digital signatures.
The key takeaway is that they often work as a team. Asymmetric encryption is used at the start of a secure session to safely exchange the secret symmetric key. Then, the rest of the conversation is encrypted using that fast and efficient symmetric key.
Here’s a quick summary of symmetric vs asymmetric encryption:
| Feature | Symmetric Encryption (One Identical Key) | Asymmetric Encryption (Two-Key System) |
| Number of Keys | One shared secret key for both locking and unlocking. | Two linked keys: a public key to lock, a private key to unlock. |
| Speed | Fast | Slower |
| Best For | Encrypting large amounts of data at rest or data in transit (files, streams). | Securely exchanging keys, digital signatures, and verifying identity. |
| Key Challenge | How to share the single key securely. | Slower performance due to more complex math. |
| Analogy | Using the same key to lock and unlock a box. | Using an open padlock to lock, and a private key to unlock. |
3. Why is encryption important?
So we know what encryption is and the types that exist, but why is encryption important? The simple answer is that it provides the foundation for trust and privacy on the internet. Without it, the digital world as we know it – from online shopping to private messaging – could not exist safely.
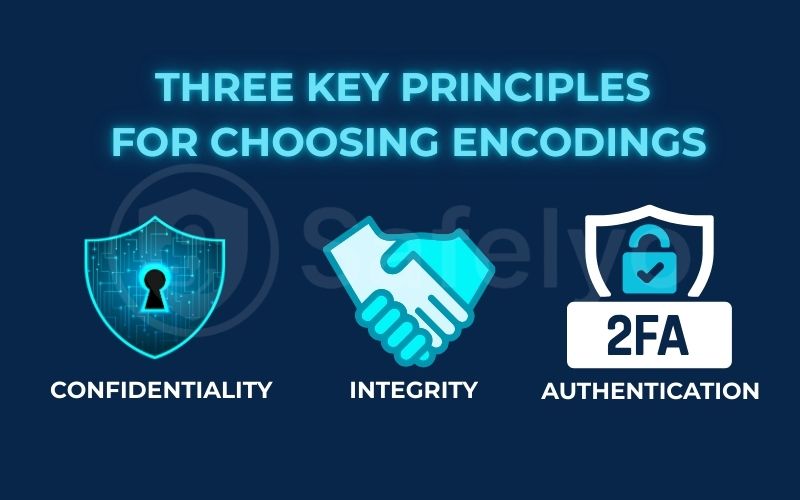
In my work, I see the consequences when data encryption fails or isn’t used. It’s the difference between a private conversation and a public announcement. Think of encryption as your personal digital bodyguard, tirelessly working to ensure three key principles:
1. Confidentiality (Keeping Secrets)
This is the most obvious benefit. Encryption keeps your sensitive data secret from anyone who isn’t supposed to see it – hackers, your Internet Service Provider (ISP), advertisers, or anyone snooping on a public Wi-Fi network. This is how your online banking transactions are protected, how your private photos in cloud storage remain yours, and how your VPN shields your browsing history.
2. Integrity (Preventing Tampering)
How do you know the email you received is exactly what the sender wrote? Encryption can ensure that the data you receive has not been altered in transit. A part of the process, often involving digital signatures, verifies that the message in the “lockbox” that arrives is identical to the one that was sent. It protects against an attacker intercepting and changing your data mid-journey.
3. Authentication (Verifying Identity)
Encryption helps prove that people and websites are who they claim to be. When you see that padlock icon in your browser, asymmetric encryption is working behind the scenes. It verifies that your browser is communicating with the real bankofamerica.com, not a clever fake set up by a phisher. This prevents “man-in-the-middle” attacks, where an attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
Without this silent bodyguard, every email, every purchase, and every password would be an open book for anyone to read.
4. Encryption in your daily life
Encryption isn’t some far-off concept for spies and corporations. You use powerful data encryption dozens of times a day, often without a second thought. I find it incredible how seamlessly this complex technology has been integrated into our lives to protect us.
This simple timeline shows how this invisible shield is with you from the moment you wake up to the moment you go to sleep.
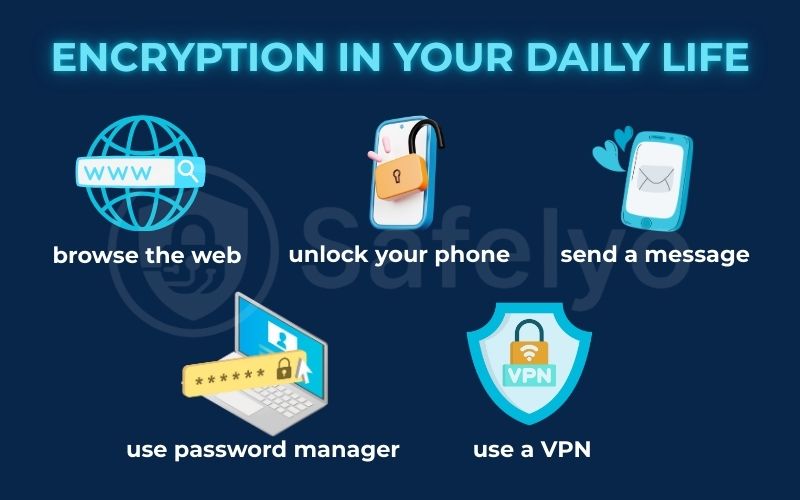
- When you unlock your phone, your smartphone (both iPhone and Android) uses encryption to protect all the data at rest on the device. Your PIN, face, or fingerprint is part of the key that decrypts it.
- When you send a message: Apps like WhatsApp and Signal use end-to-end encryption (E2EE), a powerful form of asymmetric and symmetric encryption working together. This ensures that only you and the recipient can read the messages – not even the company that owns the app can.
- When you browse the web, that little padlock icon next to a website’s URL means your connection is protected by HTTPS (Hypertext Transfer Protocol Secure). This uses encryption to protect the data in transit between your browser and the website, preventing anyone on the network from seeing what you’re doing.
- When you use a VPN: A VPN wraps your entire internet connection in a layer of strong encryption, typically AES encryption. This is especially crucial on public Wi-Fi, as it prevents hackers on the same network from snooping on your activity.
- When you use a password manager, your entire database of passwords is encrypted into ciphertext and locked with your single master password, which acts as the encryption key.
5. FAQ about the encryption
We’ve covered the lockbox analogy and seen encryption in action. Here are some quick, direct answers to the most common questions people have about this foundational security technology.
What is encryption in simple words?
In simple words, encryption is the process of scrambling information so that it can only be read by someone who has the secret key or password. It’s like turning a readable message into a secret code to protect it from prying eyes.
What is data encryption in cybersecurity?
In cybersecurity, data encryption is a fundamental method of protecting digital information. It involves using an algorithm to convert data into ciphertext, rendering it unreadable to unauthorized users. It’s a critical defense against data theft, hacking, and surveillance.
What is encryption in networking?
Encryption in networking refers to protecting data in transit as it moves across a network, like the internet. When you use a VPN or connect to an HTTPS website, encryption creates a secure, private tunnel for your data. This prevents anyone on the network, like on public Wi-Fi, from intercepting and reading it.
Is encryption good or bad?
Encryption is overwhelmingly good. It is a fundamental technology for protecting privacy, securing financial transactions, and ensuring freedom of speech online. While it can be misused by criminals, its benefits for protecting the data of billions of ordinary, law-abiding citizens are essential for a safe and functioning digital society.
What is the difference between encryption and hashing?
Encryption is a two-way process; anything that is encrypted can be decrypted with the correct key. In contrast, hashing is a one-way process; you can create a hash from data, but you cannot reverse the hash to its original form. Hashing is utilized to verify data integrity and securely store passwords, rather than to send secret messages.
What are the main types of encryption?
The two primary types of encryption are symmetric and asymmetric encryption. Symmetric encryption relies on a single shared key for both locking and unlocking, such as AES encryption. In contrast, asymmetric encryption employs a pair of keys: one public key for locking and one private key for unlocking.
Can encryption be broken?
When implemented correctly using modern algorithms like AES encryption, it is practically unbreakable by brute force (guessing the key). However, data can still be compromised if the encryption key is stolen or if there are flaws in the software’s implementation. Additionally, methods like phishing can trick you into giving away your credentials.
6. Conclusion
In a world where our data is constantly traveling, encryption is the essential act of putting our digital messages into a secure, sealed lockbox before sending them on their journey. It is the invisible bodyguard that works silently to protect our most sensitive information every second of every day.
- Encryption turns readable data (plaintext) into a secret code (ciphertext).
- It relies on an encryption key and an algorithm to lock and unlock information.
- The two main types of encryption are symmetric (one key) and asymmetric (two keys).
- You use it constantly every day to protect your messages, browsing, and personal files.
Understanding what is encryption doesn’t just satisfy your curiosity; it helps you appreciate and choose the tools that form the foundation of your digital security.
At Safelyo, we rigorously test and review the tools that use this powerful technology. Explore our guides to the best VPNs and password managers in our Privacy & Security Basics section to see encryption in action.