Asking “how to protect your online privacy” isn’t just a search query anymore; it’s a vital question in a world where our digital lives are more exposed than ever. Every click, share, and login leaves a digital footprint that is constantly being tracked, collected, and exploited.
From advertisers who seem to read your mind to the lurking risks on that ‘free’ café Wi-Fi, it’s easy to feel like your personal information is up for grabs. Many feel powerless against it, but here’s the good news: taking back control is not only possible, but it’s also more straightforward than you might think.
With years of experience in the cybersecurity trenches, I’ve seen how often simple oversights can lead to serious privacy invasions. This guide isn’t about becoming a paranoid hermit; it’s about equipping yourself with smart, simple habits. Protecting your online privacy is for everyone, not just tech wizards.
In this definitive guide, you’ll discover how to:
- Build a solid first line of digital defense.
- Browse anonymously and stop trackers in their tracks.
- Lock down your most critical accounts from hackers.
- Spot and sidestep sophisticated phishing traps.
Let’s start the journey to reclaim your digital privacy, one step at a time. I’m here to guide you through it all.
QUICK WINS CHECKLIST
Short on time?
Here are 5 quick privacy wins you can do in 10 minutes
1. Enable Two-Factor Authentication (2FA) on your main email account.
2. Run a privacy checkup on your Facebook or Google account.
3. Install a reputable ad-blocker extension on your browser.
4. Change the password on one critical account (like your bank) to a strong, unique one.
5. Review app permissions on your smartphone and remove unnecessary ones.
1. Why your online privacy matters more than you think
Online privacy isn’t about hiding secrets. It’s about having control over your personal story, who gets to see it, how it’s used, and when it’s shared. The most common argument I hear is, “I have nothing to hide.” But that statement misses the point entirely. Your data, even the bits that seem trivial, can be pieced together to create a startlingly detailed profile of your life, habits, and vulnerabilities.
Let’s move beyond the abstract and look at how this plays out in the real world.
1.1. From personalized ads to price discrimination
Have you ever searched for a flight, only to return an hour later and find the price has mysteriously gone up? That’s not a coincidence. Websites use tracking cookies to gauge your interest. They know you’re likely to buy, so they might inflate the price just for you. This is price discrimination, and it’s a direct financial consequence of your browsing data being used against you.
1.2. The risk of identity theft
What happens when your information falls into the wrong hands? It often starts small. A data breach at an online store you used years ago leaks your email and an old password. It seems harmless, but cybercriminals know that many people reuse passwords. They’ll run that combination on your email, social media, and banking accounts. If they get a match, they suddenly have a key to your financial life, potentially draining accounts or taking out loans in your name before you even realize what’s happened.

1.3. Protecting your reputation
How can public posts affect your real life? Your digital footprint is permanent. That joke you posted on social media ten years ago, or an angry comment made in the heat of the moment, can easily be unearthed by a potential employer, a new landlord, or even a future partner. What seemed like a fleeting post can have lasting real-world consequences, shaping opportunities and perceptions about you in ways you never intended.
I once searched for a specific brand of running shoes, and for the next two weeks, every single website I visited, from news sites to cooking blogs, showed me ads for those exact shoes. It was a stark reminder that your activity is being watched and cataloged. This feeling isn’t unique – according to the Pew Research Center, the vast majority of Americans feel they have little to no control over the data that companies collect about them.
2. Foundational privacy settings: Your first line of defense
Now that you understand the risks, let’s build your fortress. Think of these next steps as the digital equivalent of locking your front door and windows. They are the non-negotiable basics that form the bedrock of your online security. I always tell friends and family to start here, because mastering these habits provides the biggest security return for the least amount of effort.
2.1. Secure your accounts with strong passwords and a password manager
Using the same simple password for everything is like using one key for your house, car, office, and safety deposit box. If a thief gets that one key, they get everything. That’s why “Password123” is a welcome mat for hackers.
A truly strong password has two key ingredients: It’s long and it’s unique. Aim for at least 12 characters with a mix of letters (upper and lower case), numbers, and symbols.

But how do you remember dozens of unique, complex passwords? You don’t. You let a tool do it for you.
This is where a password manager comes in. In my professional life, I manage credentials for hundreds of services – trying to remember them all would be impossible and insecure. Think of a password manager as a highly secure digital vault. You only need to remember one strong master password to unlock it, and the manager handles the rest, creating, saving, and auto-filling unique, complex passwords for every site you use. It’s the single best thing you can do for your account security.
Here’s a quick comparison of some top choices:
Comparison of Popular Password Managers
| Feature | NordPass | 1Password | Bitwarden |
|---|---|---|---|
| Free Version | Yes, with limitations (e.g., active on 1 device at a time) | No, free trial only | Yes, a very generous free version for personal use |
| Pricing | Affordable paid plans | Premium pricing with family options | Very low-cost premium options |
| Compatibility | Windows, macOS, Linux, Android, iOS, most browsers | Windows, macOS, Linux, Android, iOS, most browsers | Windows, macOS, Linux, Android, iOS, most browsers |
2.2. Enable two-factor authentication (2FA) everywhere possible
If a password is your front door lock, then two-factor authentication (2FA) is the security guard who asks for ID. It’s a second layer of protection that proves it’s really you trying to log in.
The concept is simple. 2FA is like needing your ATM card and your PIN to get cash. One without the other is useless. Online, it usually means that after you enter your password (something you know), you must provide a one-time code from your phone (something you have).
Why is this so critical? Because even if a hacker steals your password, they can’t get into your account without that second piece of verification.
In my cybersecurity circles, not using 2FA on critical accounts is a major red flag. You should enable it immediately on these accounts at a minimum:
- Your primary email
- All banking and financial accounts
- Your main social media accounts (Facebook, Instagram, X)
- Cloud storage accounts (Google Drive, iCloud, Dropbox)
2.3. Review and lock down your social media privacy settings
Social media platforms are designed to encourage sharing, so their default settings are often far more public than you’d like. It’s your job to go in and tighten the screws.
A friend of mine once posted excitedly, “Counting down the days until our two-week vacation in Hawaii!” While it seemed harmless, he was essentially broadcasting to the world that his home would be empty for two weeks. It’s a simple mistake, but it highlights how public information can create real-world risks.
Take 15 minutes and go through your settings.
Here's a quick checklist:
- Who can see your posts? Change this from ‘Public’ to ‘Friends’.
- Who can find you? Limit who can look you up using your email or phone number.
- Photo tagging: Set this to require your approval before a tagged photo appears on your profile.
- Third-party apps: Review the list of apps you’ve given access to your account and remove any you don’t recognize or no longer use.
3. Intermediate steps: Taking control of your digital footprint
You’ve secured your accounts, which is a fantastic start. Now, it’s time to reduce the amount of data you leave behind as you navigate the web. Think of this as learning to walk through the digital world without leaving deep footprints for trackers to follow. These intermediate steps involve using specific tools to actively shield your activity.
3.1. Master your browser for private browsing
Everyone knows about “Private Browsing” or “Incognito Mode.” But what does it actually do?
Here’s a simple truth: Incognito mode only erases your browsing history on your local device. It’s like tidying up a room after a meeting. The people in the room forget the conversation happened, but the building’s security cameras (your internet provider, your employer, and the websites you visited) still have a full recording. It does not make you anonymous online.
To truly prevent online tracking, you need more powerful tools:
- Ad and tracker blockers: I personally use extensions like uBlock Origin. These tools do more than just hide annoying ads – they block the invisible trackers embedded within those ads, which are the primary way companies follow you from site to site.
- Privacy-focused browsers: Instead of adding extensions to Chrome, you can switch to a browser like Brave or DuckDuckGo. These come with strong, built-in privacy protections from the start, blocking trackers and third-party cookies by default.
- Manage your cookies: Cookies are small data files that websites leave on your browser. While some are useful (like keeping you logged in), others are used for tracking. Set your browser to block third-party cookies and to clear all cookies when you close it.
>> Read more:
3.2. Use a VPN to truly protect your connection and online privacy
A Virtual Private Network (VPN) is one of the most powerful tools in your privacy arsenal. Here’s a simple way to understand it: A VPN creates a secure, encrypted VPN tunnel for your internet traffic. Instead of your data traveling in the open, it’s locked in a private armored car that no one can peer into.
I travel often for work, and my number one rule is to never, ever connect to public Wi-Fi at an airport, hotel, or café without first activating my VPN. That network named “FREE_AIRPORT_WIFI” could easily be a trap set by a hacker trying to intercept data. By using a VPN, I know my connection is scrambled, making my information unreadable and useless to any eavesdroppers.
>> You may also be interested in this 5 best VPN for public Wi-Fi security in 2026 (tested)
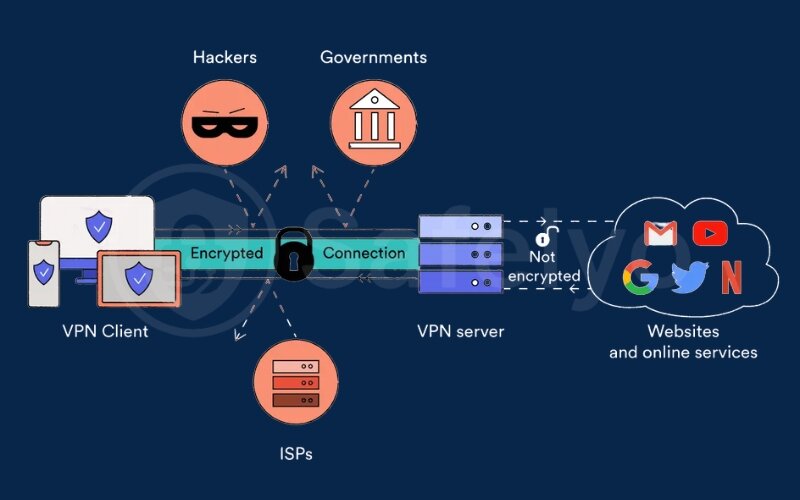
The main benefits you get when you use a VPN for privacy are:
- It encrypts your data: This is crucial on public Wi-Fi, protecting you from hackers who might be on the same network.
- It hides your real IP address: Your IP address is like your home address online. A VPN gives you a different one – a VPN IP address, making it much harder for websites and advertisers to track your location and activity. This is a key step in learning how to be anonymous online.
- It bypasses censorship: By connecting to a VPN server in another country, you can access content that might be blocked in your region.
Choosing the right service is key. A reliable VPN is crucial for your privacy. Explore Safelyo’s ranking of the Best VPN to find the perfect fit for your needs.
3.3. Secure your home Wi-Fi network
Your home Wi-Fi router is the main gateway to every internet-connected device you own. If it’s not secure, none of your devices are truly safe. Securing it is easier than you think.
Here are the essential steps to secure your Wi-Fi network:
- Change the default admin password: Every router comes with a default username and password (like “admin” and “password”). Hackers have lists of these and will try them first. Change it to something unique immediately.
- Use strong encryption: In your router settings, make sure you’re using WPA3 or, at a minimum, WPA2 encryption. This scrambles your Wi-Fi signal, preventing neighbors or others from snooping on your activity.
- Create a guest network: Most modern routers allow this. Think of it as giving visitors a key to a guest room, not the key to your entire house. It keeps their devices (and any potential malware on them) completely separate from your main network, where your important computers and files reside.
>> Read more: How to VPN into home network with this 4 simple methods
4. Advanced tactics for maximum privacy
You’ve built a strong defense and learned to navigate the web with care. These final tactics are for those who want to go the extra mile to truly secure their digital footprint. This is about being proactively minimalist and vigilant with your data.
4.1. Minimize your data exposure
The safest data is the data that you never share in the first place. This is the core of the “data diet.” Before you give away any piece of personal information, ask yourself: “Is this absolutely necessary?”
I was recently setting up a new smart light bulb, and its companion app asked for permission to access my phone’s contact list. I stopped and thought, “Why would a light bulb need to know who my friends are?” It doesn’t. I denied the permission. This is the kind of critical thinking the data diet encourages.
Here are some practical ways to put it into practice:
- Use email aliases: Services like SimpleLogin or the built-in features of iCloud Mail allow you to create unique email addresses (aliases) for every service you sign up for. If one of those services gets breached or starts sending spam, you can just delete the alias without affecting your real email address.
- Avoid online quizzes and surveys: Those fun “Which Disney character are you?” quizzes are often data harvesting tools in disguise. They collect personal preferences and answers to security-like questions (“What was the name of your first pet?”) that can be used against you.
- Think before you grant app permissions: Always question why an app needs certain access. A photo editing app doesn’t need your location, and a game doesn’t need access to your microphone. If the request doesn’t make sense, deny it.
4.2. Regularly check for data breaches and know how to respond
It’s no longer a question of if your data will be exposed in a breach, but when. Being prepared is essential.
You can use a free service like “Have I Been Pwned” to check for data breaches. You simply enter your email address, and it will tell you if your credentials have appeared in any known public data leaks. I recommend setting a calendar reminder to do this every few months.
If you discover your information has been compromised, don’t panic. Follow this simple action plan:
- Change the password immediately on the affected account.
- If you’ve reused that password anywhere else (which you shouldn’t, thanks to your password manager!), change it on all those accounts too.
- Enable 2FA on the account if you haven’t already.
4.3. Staying ahead of emerging threats
The privacy landscape is always changing. Staying informed about new risks is key to staying protected. Here are a few things to keep on your radar:
- AI and data privacy: Large AI models are trained on vast amounts of public data from the internet. Be mindful that what you post publicly today could become part of an AI’s knowledge base tomorrow.
- Biometric data: Your fingerprint and face are becoming the new passwords. While convenient, this data is irreplaceable if stolen. Be cautious about which services you trust with your biometric information.
- Internet of Things (IoT) privacy: Smart speakers, TVs, and even refrigerators are constantly connected to the internet. These devices can be vulnerable entry points into your home network if not properly secured. Always change default passwords and keep your software updated.
5. FAQ about how to protect your online privacy
Navigating online privacy can bring up a lot of questions. Here are clear, straightforward answers to some of the most common ones we hear at Safelyo.
Does private or incognito mode truly protect my privacy?
Not completely. It only prevents your browsing history and cookies from being saved on your device. Your internet service provider (ISP), your employer or school, and the websites you visit can still see your activity. For true privacy from prying eyes, a tool like a VPN is necessary.
Is it safe to use a free VPN?
Generally, no. Most free VPNs have significant speed and data limits. More importantly, if a service is free, you are often the product. Many free providers make money by collecting and selling your browsing data to advertisers, which completely defeats the purpose of using a VPN for privacy. Always invest in a reputable, paid VPN with a strict no-logs policy.
How often should I review my privacy settings?
A good rule of thumb is to review the privacy settings on your most important accounts (like your main email and social media profiles) at least every six months. Platforms frequently update their policies and introduce new settings, so a regular check-up ensures your protection doesn’t become outdated.
What are the best ways to protect my privacy online?
The best strategy is a layered one. Start with the fundamentals: use a password manager for unique, strong passwords and enable 2FA on all important accounts. Then, use a reliable VPN to encrypt your connection, a privacy-focused browser to block trackers, and be mindful of what you share on social media.
How do I keep my information private online?
You can keep your info private by minimizing how much you share (the “data diet” principle). Use email aliases for sign-ups, deny unnecessary app permissions, and think twice before taking online quizzes. The less information you put out there, the less there is to be compromised.
What can I do to protect my online identity?
Protecting your online identity involves securing your core accounts. Your primary email is the key to your digital kingdom – protect it fiercely with a strong password and 2FA. Regularly check for data breaches using services like “Have I Been Pwned” so you can react quickly if your credentials have been exposed.
What are 8 ways to stay safe online?
Here are eight essential safety habits:
- Use a password manager.
- Enable 2FA everywhere.
- Use a VPN, especially on public Wi-Fi.
- Keep your software and apps updated.
- Lock down your social media privacy settings.
- Be skeptical of phishing emails and suspicious links.
- Regularly back up your important data.
- Secure your home Wi-Fi network.
6. Conclusion
Learning how to protect your online privacy is an ongoing journey, not a one-time destination. By implementing the steps laid out in this guide, you’ve built a powerful foundation for taking back control of your personal data and navigating the digital world with confidence. It’s about creating smart, sustainable habits that become second nature.
Remember these key takeaways to stay secure:
- Start with the basics: Strong, unique passwords managed by a password manager and two-factor authentication are your non-negotiable first line of defense.
- Use powerful tools: A reputable VPN and a privacy-respecting browser are your best allies for staying anonymous and preventing online tracking.
- Stay vigilant: Regularly check for data breaches, be critical of app permissions, and always think before you share your personal information.
Be proactive. Don’t wait for a privacy scare to take your security seriously. Your digital privacy is a valuable asset – protect it.
To continue building your knowledge and find in-depth reviews of the best security tools, explore the Privacy & Security Basics category on Safelyo. We’re always here to help you navigate the digital world safely.












