In the world of VPNs, the IPsec vs OpenVPN debate is a classic showdown between two of the most trusted and widely used security protocols. Think of them as two different engines for your private connection: One is a standard, built-in system, the other is a flexible, open-source champion.
Choosing between a protocol built into your operating system and a versatile third-party solution can be confusing. However, this choice directly impacts your speed, security, and connection stability.
As a security analyst who has configured everything from corporate networks to personal devices, I know there isn’t one ‘best’ answer. The right choice depends entirely on the task at hand – whether you need raw performance on your phone or unbreakable reliability to bypass censorship.
In this comprehensive guide, you’ll discover:
- The key difference between IPsec and OpenVPN is at a core level.
- Which protocol is generally faster and why?
- The nuances of the security and encryption debate.
- Which one is better for mobile devices versus bypassing firewalls?
Don’t let technical jargon dictate your security settings. Let me demystify these two industry giants and give you the clarity to choose the right protocol for your needs.
1. The built-in standard vs. the open-source champion
Before we dive into a head-to-head comparison, it’s essential to understand the fundamental design and philosophy behind each of these VPN titans. They achieve the same goal – a secure, encrypted VPN tunnel – but they take very different roads to get there.
1.1. What is IPsec? The time-tested framework
IPsec (Internet Protocol Security) is not a single protocol, but a suite of protocols that work at the network layer of the Internet. This is a crucial detail.
From my experience as a network administrator, I view IPsec as a foundational security system. It is built directly into the highways of your operating system, including Windows, macOS, iOS, and Android. Because it’s integrated at this deep, kernel level, it can be incredibly efficient and fast.
However, IPsec itself is just the framework for securing the data packets. It needs a partner to manage the connection and handle the authentication and key exchange. Today, that partner is almost always IKEv2 (Internet Key Exchange version 2).
This powerful duo, IKEv2/IPsec, is the modern standard. IKEv2 acts as the efficient traffic controller that quickly sets up the secure lanes on the highway, and IPsec provides the heavy armor for the vehicles traveling on them. This combination is particularly famous for its stability on mobile devices.
1.2. What is OpenVPN? The flexible open-source solution
OpenVPN, on the other hand, is both a protocol and a piece of software that operates at the application layer. It’s not built into the operating system; it’s an app you install on top of it.
Its greatest strength, and the reason it has been the industry’s gold standard for so long, is its incredible flexibility.
- SSL/TLS Foundation: It uses the widely trusted SSL/TLS library for its security, the same technology that protects HTTPS websites.
- Protocol Duality: It can run over both UDP for speed and TCP for maximum reliability.
- Firewall Traversal: This is its superpower. The ability to run on TCP port 443 – the same port used for all secure web traffic – makes it look like you’re just browsing a regular website. As someone who has tested VPNs in restrictive environments, I can tell you this makes it extremely difficult for firewalls to detect and block.
Think of OpenVPN as a versatile, all-terrain delivery truck. It might not be part of the highway itself, but it can navigate any road. It can also get through almost any roadblock. This makes it a go-to choice for users in countries with heavy internet censorship.
2. IPsec vs OpenVPN: A head-to-head comparison
Now that we understand the core philosophies of the “built-in standard” and the “open-source champion,” let’s put them in the ring together. The difference between IPsec and OpenVPN becomes clear when you analyze them across four key categories: Performance, security, stability, and configuration.
2.1. Performance and speed: Is IPsec faster than OpenVPN?
For users, this is often the bottom line.
The short answer is yes, IKEv2/IPsec is generally faster than OpenVPN.
The reason lies in how they operate. As I mentioned, IPsec processes data deep within the operating system’s kernel, which is a highly efficient, streamlined path. OpenVPN, running in the “user space” as an application, has a slightly longer journey to take, which adds a small amount of processing overhead and latency.
- Real-world impact: While speeds vary depending on the network, server load, and your device, my experience shows some trends. Industry benchmark tests often indicate that IKEv2/IPsec can offer a speed advantage. This advantage can be up to 15-25% over OpenVPN (UDP) under ideal conditions.
- An Important Note: The comparison must be made with OpenVPN’s faster UDP mode. OpenVPN running in TCP mode is significantly slower due to its built-in error checking, making the speed gap with IPsec even wider.
Winner: IKEv2/IPsec
2.2. Security and encryption: Is OpenVPN more secure than IPsec?
This is a much more nuanced debate, and the answer is: Both are considered extremely secure when configured correctly with modern encryption standards like AES-256. The difference is more about transparency and trust.
- OpenVPN: Its greatest security asset is that it is fully open-source. The entire codebase can be (and has been) scrutinized by thousands of independent security experts around the world. This transparency makes it very difficult for hidden backdoors or vulnerabilities to exist for long. For this reason, it is often the preferred choice of the privacy and security community.
- IPsec: While IPsec is an open standard, its implementation is built into operating systems, which are closed-source (like Windows and macOS). There have been long-standing, though unproven, concerns stemming from the Edward Snowden leaks that the NSA may have worked to weaken certain aspects of the IPsec standard.
Winner: OpenVPN (by a slight margin for transparency)
From a purely technical standpoint, both are fortresses. However, OpenVPN’s open-source nature gives it a slight edge in verifiable trust.
2.3. Stability and mobility
For users on the move, there is a clear winner in this category.
- IKEv2/IPsec is far superior for mobile devices. It includes a feature called the MOBIKE protocol, which is specifically designed to handle network changes. In my own testing, when I switch my phone from my home Wi-Fi to a 5G cellular network, an IKEv2/IPsec connection re-establishes itself almost instantly.
- OpenVPN, while stable, can take several seconds to detect the network change and re-initiate the handshake process. This can lead to a noticeable pause in your connection.
Winner: IKEv2/IPsec
2.4. Firewall traversal and configuration
This is where OpenVPN’s flexibility gives it a decisive advantage.
- OpenVPN is the champion of bypassing firewalls. Its ability to run over TCP port 443 is its secret weapon. This makes its encrypted traffic look identical to the standard HTTPS traffic used by secure websites, allowing it to slip through most corporate and national firewalls undetected.
- IPsec uses specific, well-known ports (like UDP 500 and 4500) that are much easier for network administrators to identify and block. The initial configuration of IPsec can also be more complex.
Winner: OpenVPN

3. The known issue: IPsec vulnerabilities
If you search online, you’ll inevitably find discussions about IPsec vulnerabilities. It’s a topic that often causes concern, and it’s important to address it head-on with the proper context.
From my experience as a security professional, the key thing to understand is this: The “vulnerabilities” are rarely in the IPsec protocol suite itself, but in how it is configured or implemented. Think of it like a high-quality, complex bank vault. The vault itself is secure, but the danger comes if you set the combination to “1234” or hire an untrustworthy company to install it.
Here are the main points you need to know:
- Avoid IKEv1: The older version of the key exchange protocol, IKEv1, has known, documented vulnerabilities and is considered obsolete. Any modern, secure implementation must use IKEv2. If you ever see a VPN service offering a plain “IPsec” option without specifying IKEv2, I would be very cautious.
- Risk of Misconfiguration: Because IPsec has many moving parts and configuration options, there is a higher risk of human error during a manual setup. A weak authentication method or a poorly chosen encryption setting can create a security hole. This is a major reason why using the pre-configured IKEv2/IPsec option from a trusted, commercial VPN provider is so much safer than trying to set it up yourself.
- The Importance of Updates: Just like any piece of software, specific implementations of IPsec in operating systems or networking gear can have bugs. Keeping your devices and VPN apps updated is crucial for patching any vulnerabilities as they are discovered.
The Bottom Line
When IKEv2/IPsec is implemented by a reputable VPN provider that has done the hard work of configuring it correctly with strong ciphers and authentication, it is an extremely secure protocol. The primary risks come from outdated versions (IKEv1) and incorrect manual configuration, not from an inherent flaw in the modern standard.
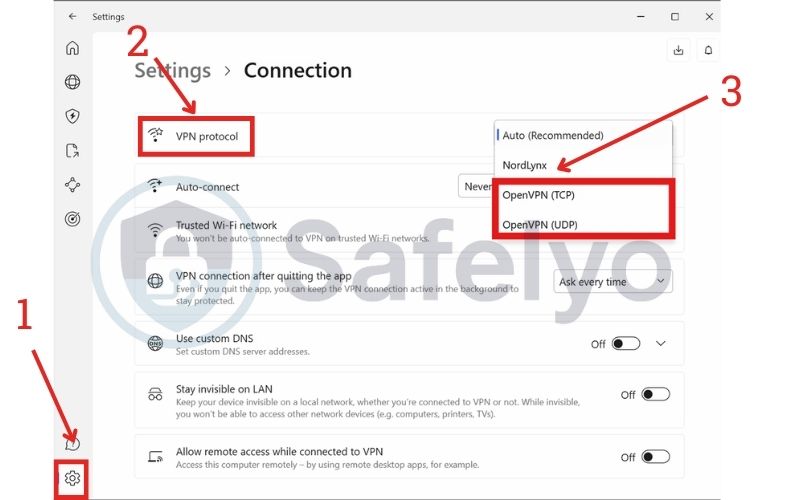
4. How to check what protocol your VPN is using
After learning about the different strengths of IPsec vs OpenVPN, you’re probably wondering, “What protocol does my VPN use?” Fortunately, most modern VPN apps make it very easy to check and even change your VPN protocol.
Knowing how to find this setting is a powerful tool. It allows you to troubleshoot connection issues or optimize your performance for specific tasks. Here’s a simple, universal guide.
- Open Your VPN App: Launch the VPN client on your computer or smartphone.
- Navigate to Settings: Look for a menu icon, often a gear (⚙️) or three horizontal lines (☰). Click it to open the settings panel.
- Locate the “Protocol” or “Connection” menu: In the settings, search for a tab or section labeled “Protocol,” “Connection,” or occasionally “Advanced.”
This is where you’ll find a dropdown menu or a list of options. It will show you the currently selected protocol.
Understanding the "Automatic" Setting
In my experience testing dozens of VPNs, I’ve found that most top-tier providers now default to an “Automatic” setting. This is usually the best choice for most users. The app is smart enough to analyze your network and select the best protocol for you. It will typically:
- Default to a fast protocol like WireGuard or IKEv2/IPsec for the best performance.
- Automatically switch to OpenVPN (TCP) if it detects that you’re on a restrictive network that is blocking other protocols.
Knowing this VPN protocols comparison, however, means you are no longer just relying on the automatic setting. You can now manually switch to OpenVPN to bypass a firewall or choose IKEv2/IPsec for maximum stability on your phone, making you a more empowered VPN user.
5. FAQ about the IPsec vs OpenVPN showdown
We’ve covered the head-to-head battle, but you might still have some specific questions. Here are direct answers to the most common queries in the IPsec vs OpenVPN debate.
IPsec vs OpenVPN: Which VPN protocol should you choose?
Choose IKEv2/IPsec if your priority is speed and stability, especially on mobile devices. Choose OpenVPN if you need maximum flexibility, the ability to bypass strict firewalls, or the verifiable trust of a fully open-source project. For most users, the “Automatic” setting in a quality VPN app, which often defaults to IKEv2/IPsec, is a great choice.
What is the difference between IPsec and SSL VPN?
The primary difference between IPsec and an SSL VPN lies in the network layer where they function. IPsec works at the lower network layer, securing all IP traffic. In contrast, an SSL VPN, with OpenVPN as the most popular example, operates at the application layer and offers greater flexibility in bypassing firewalls by mimicking standard HTTPS traffic.
Is IKEv2 the same as IPsec?
No, but they work as a team. IPsec is the suite of protocols that provides the actual encryption and authentication for the data. IKEv2 is the modern protocol used to manage the key exchange and establish the secure tunneling connection for IPsec. You will almost always see them used together as IKEv2/IPsec.
Which protocol is better for overcoming censorship in countries like China?
OpenVPN, especially when configured to run on TCP port 443, is generally more effective at bypassing strict firewalls and deep packet inspection. This is due to its ability to “disguise” its traffic as standard, secure web browsing (HTTPS), making it much harder for censors to detect and block.
6. Conclusion
The showdown between IPsec vs OpenVPN doesn’t have a single knockout winner. Instead, it reveals two powerful champions, each mastering a different aspect of VPN security and performance. One is a highly efficient, integrated standard perfect for speed and mobility, while the other is a flexible, transparent workhorse that can navigate any digital obstacle.
- Choose IKEv2/IPsec: When your top priority is speed and stability, especially on mobile devices that frequently switch networks.
- Choose OpenVPN: When you need maximum flexibility, the ability to bypass strict firewalls, or the verifiable trust of a fully open-source solution.
- Both are highly secure: When implemented correctly by a reputable VPN provider, both protocols offer robust, military-grade encryption.
- Trust “Automatic”: For most users, the “Automatic” setting in a top-tier VPN app is the smartest choice, as it will select the best protocol for your current network conditions.
Understanding the core differences between these protocols empowers you to move beyond the default settings and actively optimize your VPN connection for any situation. You now know how to troubleshoot issues and choose the right tool for the job.
To continue enhancing your cybersecurity knowledge, explore the other in-depth comparisons and guides in our Privacy & Security Basics section of Safelyo.












