Have you ever hit a digital wall, trying to connect your VPN at school, work, or while traveling, only to find it completely blocked? If that sounds familiar, it’s time you learned what is obfuscated VPN. Think of it as the ultimate digital disguise for your connection.
While a standard VPN encrypts your data inside a secure tunnel, its digital “signature” can still scream, “I’m a VPN!” An obfuscated VPN takes it one crucial step further: it camouflages that tunnel, making your VPN usage look like regular, harmless internet traffic. This simple trick is a game-changer for true online freedom.
As a privacy tech analyst, I’ve tested countless VPNs and seen firsthand the frustration users face when their primary tool for security is rendered useless by aggressive network filters. VPN obfuscation isn’t just a niche feature for spies; it’s an essential tool for students, travelers, and anyone who believes their internet access shouldn’t be restricted.
In this guide, I’ll demystify this powerful technology. You’ll discover:
- What VPN obfuscation really is and how it acts as a digital disguise.
- The simple mechanics behind how it hides your VPN traffic.
- The key situations where an obfuscated VPN is a game-changer.
- How to easily enable this feature on your VPN app.
Don’t let VPN blocks dictate what you can and can’t do online. Let Safelyo walk you through everything you need to know to reclaim your digital freedom. Get it now!
1. What is obfuscated VPN? The concept of a digital disguise
At its core, an obfuscated VPN is a feature designed to hide the very fact that you’re using a VPN. Often called a “stealth VPN,” its primary job isn’t just to protect your data, but to conceal your entire protective tunnel from being identified as a VPN connection.
Let’s use a simple analogy. Think of your regular VPN traffic as a securely locked package. The contents are safe, but the package itself is clearly marked with a “VPN” shipping label. Your internet service provider (ISP) or a network firewall can’t see inside the package, but they can easily see the label and know you’re using a VPN.
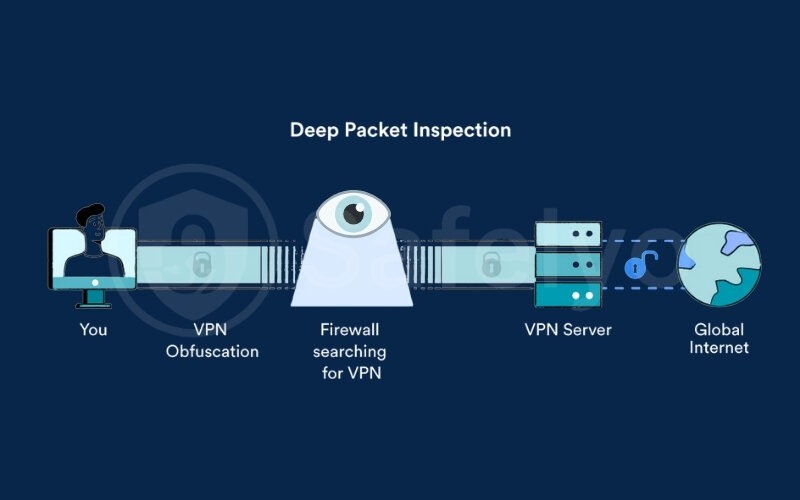
VPN obfuscation is the act of placing that securely locked package inside a bigger, plain-looking box, like an unmarked cardboard shipper or even a pizza box. Your secure data is still inside, but to any outside observer, it just looks like a normal, everyday delivery that doesn’t draw any attention.
This brings us to a crucial point that we at Safelyo find many users misunderstand. It’s the difference between encryption and obfuscation.
- Standard VPN encryption protects the contents of your traffic (the items inside the package).
- Obfuscation disguises the nature of the traffic itself (the package’s outer wrapping).
The ultimate goal? To bypass advanced network filtering systems that use a technology called Deep Packet Inspection (DPI). Think of DPI as a highly vigilant mailroom clerk trained to spot and block any package with a “VPN” label. By making your VPN connection look like something else, obfuscation allows your data to sail right past these checkpoints, completely unnoticed.
2. How does VPN obfuscation work?
So, how does a VPN actually put on its digital disguise? The magic lies in altering the “signature” or “fingerprint” of your data packets. Obfuscation techniques modify your VPN traffic just enough so that automated systems like DPI can no longer recognize it as coming from a VPN protocol like OpenVPN.
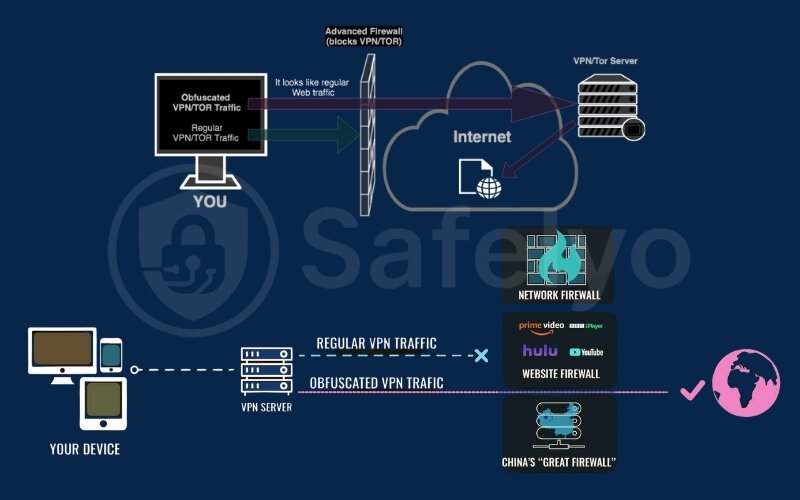
While the engineering behind it is complex, the concepts are quite straightforward. Here are a few of the most common VPN obfuscation techniques that providers use, explained simply:
- OpenVPN Scramble (also called XOR Scramble): Imagine this as “jumbling” the data. This method uses a simple algorithm to scramble the OpenVPN signature, making it unrecognizable to firewalls. It’s a lightweight and fast way to add a basic layer of stealth without significantly slowing down your connection.
- Stunnel (Wrapping in SSL/TLS): This is one of the most effective and popular methods. This technique takes your entire VPN connection and wraps it inside an additional layer of SSL/TLS encryption. Why is this so clever? Because SSL/TLS is the same encryption used by secure HTTPS websites (the little padlock in your browser). As a result, your VPN traffic looks exactly like the regular, secure traffic you’d generate when logging into your bank or shopping online, allowing it to blend in perfectly.
- Shadowsocks: This isn’t technically a VPN protocol but rather an open-source encrypted proxy. It was originally created to bypass the Great Firewall of China. It’s highly effective at disguising traffic and is designed to be lightweight and fast, making it a popular choice for providers offering obfuscation in regions with heavy censorship.
The most important thing to remember is this: you don’t need to be a tech expert to use these. The best VPN services integrate these complex methods seamlessly into their apps. For you, the user, enabling obfuscation is usually as simple as flipping a switch in the settings menu.
3. Key use cases that you might need VPN obfuscation
While a standard VPN is perfect for everyday privacy and security, obfuscation becomes essential in specific situations where your connection itself is under scrutiny. This is where the “why” becomes crystal clear. Here are the most common scenarios where you’ll want to use an obfuscated VPN.
3.1. To bypass internet censorship and government restrictions
This is the primary reason why VPN obfuscation was created. In countries with strict internet censorship, governments actively use Deep Packet Inspection (DPI) to identify and block standard VPN connections. This can cut off access to vital sources of information, including international news sites, social media platforms, and communication apps.
For journalists, activists, researchers, or anyone living in or traveling to these regions, an anti-censorship vpn with obfuscation is not just a tool for convenience—it’s a lifeline. It allows them to bypass these digital barriers, communicate freely, and access the global internet without being detected and blocked.
3.2. To evade VPN blocks on restrictive networks
Have you ever tried to connect to your personal VPN on a school, university, or office Wi-Fi network, only to find it doesn’t work? Many organizations block VPN ports and protocols to control network usage and enforce content filters.
This is a perfect use case for a vpn for restrictive networks. By disguising your VPN connection as regular HTTPS traffic, obfuscation can help you slip past these local network blocks. This allows you to secure your connection on public Wi-Fi and access your personal accounts and services without the network administrator knowing you’re using a VPN.

I once helped a client access restricted services while traveling in the US by setting up obfuscated servers alongside Shadowsocks to bypass strict corporate firewalls and deep packet inspection. This combination restored his internet access seamlessly, even on heavily monitored corporate networks.
3.3. To prevent ISP throttling and snooping
Even in countries with a free and open internet, your own Internet Service Provider (ISP) might be watching. Some ISPs monitor for VPN usage and may deliberately slow down—or “throttle”—your connection speed if they detect it, especially during high-bandwidth activities like P2P file sharing or HD streaming.

By hiding your VPN usage, obfuscation can help you avoid this targeted throttling. It ensures your ISP only sees regular encrypted traffic, giving them no reason to interfere with your connection. This adds an extra layer of privacy, keeping your online activities hidden even from the company that provides your internet.
Read more:
4. The trade-offs: Benefits vs. potential drawbacks of obfuscation
Like any technology, VPN obfuscation comes with its own set of pros and cons. Understanding these trade-offs is key to deciding if it’s the right tool for your specific needs. It’s a powerful feature, but not one you necessarily need to have enabled all the time.
Here’s a quick summary of the main points to consider:
| Benefits of VPN Obfuscation | Potential Drawbacks of VPN Obfuscation |
| Bypasses strict censorship & VPN blocks. | It can slightly reduce connection speeds. |
| Hides your VPN usage from ISPs & networks. | Not offered by all VPN providers or on all servers. |
| Helps avoid targeted speed throttling. | May require using a specific protocol (like OpenVPN). |
Now, let’s look at these points in more detail.
4.1. The key benefits
To put it simply, the advantages of using an obfuscated VPN are significant for those who truly need it. The main benefits are:
- Bypasses advanced censorship: It is the most reliable way to bypass VPN blocks enforced by national firewalls and restrictive regimes.
- Enhances privacy and anonymity: It prevents your ISP, school, or work network from knowing you are using a VPN, adding another layer of secrecy to your online activity.
- Prevents targeted throttling: It can help you avoid having your connection speed intentionally slowed down by an ISP that disapproves of VPN usage.
4.2. Potential drawbacks to consider
While incredibly useful, obfuscation isn’t without its compromises. Here are a few potential downsides to keep in mind:
- Slower speeds: This is the most common trade-off. The extra process of disguising your VPN traffic requires more processing power and adds a layer of data overhead. As a result, an obfuscated connection is almost always slightly slower than a standard VPN connection. The performance hit is usually minor, but it’s something to be aware of.
- Limited availability: Not all VPN providers offer obfuscation. Among those that do, the feature might only be available on specific servers or when using a particular VPN protocol (most commonly OpenVPN). This can limit your choice of connection locations.
- Slightly more complex setup: While the best providers make it a one-click process, some may require you to dig into the settings menu to find and enable the feature. It’s not difficult, but it’s one extra step compared to a standard connection.

5. How to enable and use an obfuscated VPN
You don’t need to be a network engineer to use obfuscation. Reputable VPN providers have made the process incredibly simple.
Here’s the process in a nutshell:
Pick a VPN with Obfuscation > Enable the ‘Stealth’ feature in Settings > Connect to an Obfuscated Server.
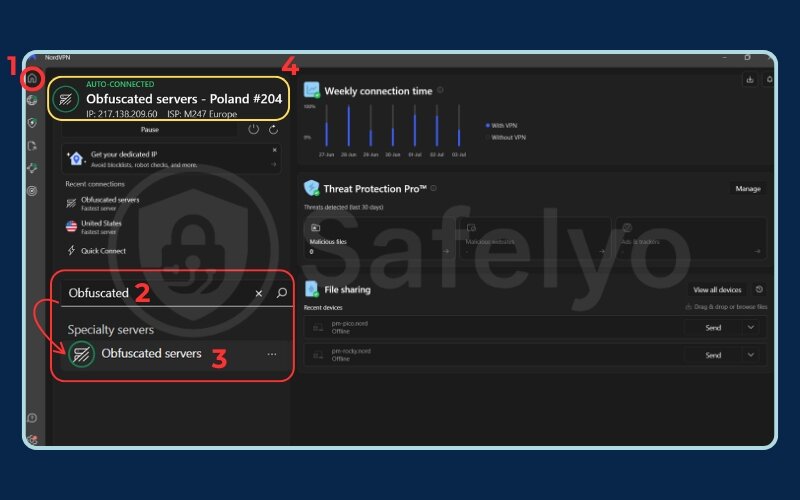
Now, let’s break down those steps with a bit more detail.
- Step 1: Choose a VPN that offers obfuscation. The most critical step is to subscribe to a trusted VPN service that explicitly lists “obfuscation,” “stealth VPN,” or “obfuscated servers” as a feature. Not all VPNs have this capability, so check their feature list before you commit.
- Step 2: Find the feature in the settings. Once you’ve installed the VPN app, open it and navigate to the settings or preferences menu. You’re looking for a toggle switch or a menu option. It might be labeled differently depending on the provider:
- Common names include “Obfuscated Servers,” “Stealth Mode,” “Scramble,” or “Make VPN undetectable.”
- In some cases, you may need to switch your VPN protocol to OpenVPN (TCP) first, as this protocol is most commonly associated with obfuscation features.
- Step 3: Enable the feature and connect. Simply flip the switch to turn the feature on. If your provider uses dedicated obfuscated servers, you may need to select one from the server list. Once enabled, connect to a server location as you normally would. Your traffic will now be automatically disguised.
Safelyo’s Expert Tip: If you connect and find the speed is too slow or the connection is unstable, don’t give up. Try connecting to a different obfuscated server. Sometimes, one server may be more congested than another, and switching can make a significant difference in performance.
6. FAQ about obfuscated VPN
Here are some of the most common questions we get about VPN obfuscation, answered directly.
Should I always use an obfuscated VPN?
Not necessarily. You should enable obfuscation when you’re in a country with heavy internet censorship, or if your school or workplace network actively blocks standard VPNs. For everyday activities like securing your connection on public Wi-Fi or unblocking streaming sites in a free country, a standard VPN connection is usually faster and perfectly sufficient.
Is a stealth VPN the same as an obfuscated VPN?
Yes, “stealth VPN” is another common term for an obfuscated VPN. They both refer to the same technology used to disguise your VPN traffic and make it undetectable. The goal is to put your VPN connection into “stealth mode” to avoid detection and blocking.
Can an obfuscated VPN be detected?
It’s a constant cat-and-mouse game. While advanced obfuscation is highly effective against most current detection methods like Deep Packet Inspection (DPI), no method is 100% foolproof forever. However, for the vast majority of users facing blocks, it remains a highly effective solution.
Is an obfuscated VPN slower?
Yes, typically an obfuscated VPN is slightly slower than a standard VPN connection. The extra process of disguising the VPN traffic requires additional processing power, which can lead to a minor reduction in your overall internet speed.
What is the difference between obfuscated and Double VPN?
They solve different problems. Obfuscation disguises your VPN traffic to hide the fact you are using a VPN. Double VPN (or Multi-Hop) routes your traffic through two different VPN servers for an extra layer of encryption and security. Use obfuscation to bypass blocks; use Double VPN when your top priority is maximizing anonymity.
Is VPN obfuscation legal?
The technology itself is legal in most parts of the world. However, using it to bypass local laws in countries that restrict or ban VPNs can put you in a legal gray area or may be explicitly against the law. Always be aware of and respect local regulations.
How do you obfuscate VPN traffic?
You don’t need to do anything manually. A good VPN provider will have this feature built directly into their app. You simply enable it in the settings, often by selecting “Obfuscated Servers” or a specific “Stealth” protocol, and the application handles all the technical work for you.
7. Conclusion
In the end, what is obfuscated VPN – It’s a powerful and essential tool for anyone facing aggressive internet censorship or restrictive network blocks. By acting as a digital disguise, it restores your ability to access information freely and privately, even in the most challenging online environments. It’s the key that unlocks the open internet when digital walls are built around you.
To quickly recap, here are the most important things to remember:
- It disguises your connection: Its main job is to hide the fact you’re using a VPN, making your traffic look like regular, everyday internet activity.
- It’s for specific situations: Obfuscation is crucial for bypassing censorship, evading school/work network blocks, and preventing ISP throttling.
- It involves a minor trade-off: The extra layer of stealth usually results in a slight decrease in connection speed, which is a small price to pay for online freedom.
- Ease of use is key: The best providers integrate this feature seamlessly, allowing you to enable it with a single click in the app’s settings.
While the slight drop in speed is a valid consideration, the immense benefit of bypassing censorship and enhancing your privacy often far outweighs this minor drawback.
Choosing a provider with a reliable and easy-to-use obfuscation feature is crucial. To help you make an informed decision, Safelyo has tested and reviewed the industry’s leading VPN services. Explore our Privacy & Security Basics to find the best security solution for your needs.













