When a coworker at a small business opened what looked like an invoice attachment, their entire file server was locked within minutes. This was not a hardware failure – it was a ransomware attack. Cases like this highlight why ransomware has become one of the most feared cybersecurity threats today. Ransomware is a type of malware that locks your files or systems until you pay a ransom. Ransomware is evolving constantly, and new ransomware campaigns target both small businesses and large enterprises daily.
In this guide, you’ll learn:
- What ransomware is and what it does to your files
- How ransomware attacks work and the tactics behind them
- The main types of ransomware, from scareware to crypto-lockers
- How to detect, prevent, and respond if your system is compromised
Let’s start by breaking down the basics: What is ransomware, and why does it matter so much?
1. What is ransomware?
What is ransomware? Ransomware is a type of malicious software designed to block access to your computer, files, or systems until a payment (ransom) is made.
Ransomware variants range from scareware to locker ransomware and file-encrypting strains. These ransomware variants are engineered by cybercriminals to monetize access denial at scale.

According to CISA (2024), ransomware remains one of the most disruptive forms of malware, and unlike other malware families, it combines data encryption with financial extortion.
1.1. What does ransomware do to files and systems
Once inside a device, ransomware typically:
- Encrypts files so they cannot be opened without a decryption key
- Locks the operating system, preventing normal access
- Displays ransom notes demanding payment, often in cryptocurrency
This makes personal photos, business documents, or even hospital patient records suddenly inaccessible. In some cases, ransomware also deletes backups or spreads across a network to maximize damage.
In some cases, locker ransomware blocks the desktop entirely, while other strains delete backups or spread across a network to maximize damage.
1.2. Why ransomware attacks are so dangerous
Ransomware is dangerous not only because it disrupts access, but also because it creates financial and reputational risks. Weak user authentication expands the attack surface, enabling follow-on abuse even after the initial breach. Organizations may face:
- Costly downtime, halting productivity or services
- Loss of sensitive or regulated data (leading to fines or lawsuits)
- Pressure to pay attackers who may still refuse to restore files
A ZDNet (2024) report notes that double extortion attacks, where criminals also threaten to leak stolen data, are now a common tactic, making the threat even more severe. For individuals, ransomware can mean losing irreplaceable family memories stored in photos or documents.
>> Read more:
2. How does ransomware work?
Understanding how ransomware works is key to both prevention and response. Attackers usually rely on social engineering, weak system defenses, and automated malware execution to compromise a device or network. Once inside, the malware moves quickly to encrypt files and pressure victims into paying. Unlike other forms of malware, ransomware directly monetizes disruption through extortion.
2.1. What is a ransomware attack?
A ransomware attack is an incident where malware infiltrates a computer or network, encrypts valuable files, and demands payment for decryption. The goal is to deny access to critical data until the victim complies. Unlike other malware, ransomware directly monetizes disruption rather than stealing information quietly.

2.2. Common infection techniques like phishing or RDP
Ransomware spreads through several common entry points:
- Phishing emails with malicious attachments or links
- Remote Desktop Protocol (RDP) exploits, often caused by weak or reused passwords
- Drive-by downloads, where a compromised website automatically installs malware
- Software vulnerabilities that haven’t been patched

These infection vectors are routinely abused by cybercriminals, especially when user authentication policies are weak. A well-documented case happened in 2019–2020, when Ryuk ransomware operators used brute-force attacks against exposed RDP services to compromise several U.S. hospitals.
According to CISA and the FBI (2020), the attackers gained domain-level credentials, deployed Ryuk widely across networks, and encrypted electronic health record systems. Some hospitals were forced to divert ambulances and delay surgeries because their critical systems were locked.
2.3. How ransomware encrypts data and demands payment
Once executed, ransomware uses strong data encryption algorithms (like AES or RSA) to lock files. This data encryption process ensures that victims cannot recover their files without the attacker’s key. Victims typically see:
- A ransom note displayed on the screen
- Instructions to pay in cryptocurrency
- A deadline, after which files may be deleted or permanently locked
According to MITRE ATT&CK (2024), modern ransomware often disables shadow copies and backup processes before encryption to maximize pressure.
2.4. Extortion tactics beyond encryption
Encryption is no longer the only threat. Many groups now use double extortion, where they first steal data before locking it. Attackers then threaten to leak sensitive files if payment is not made. Some even escalate to triple extortion, pressuring business partners, customers, or regulators. Modern triple extortion cases combine encryption, data leaks, and public pressure campaigns against victims.
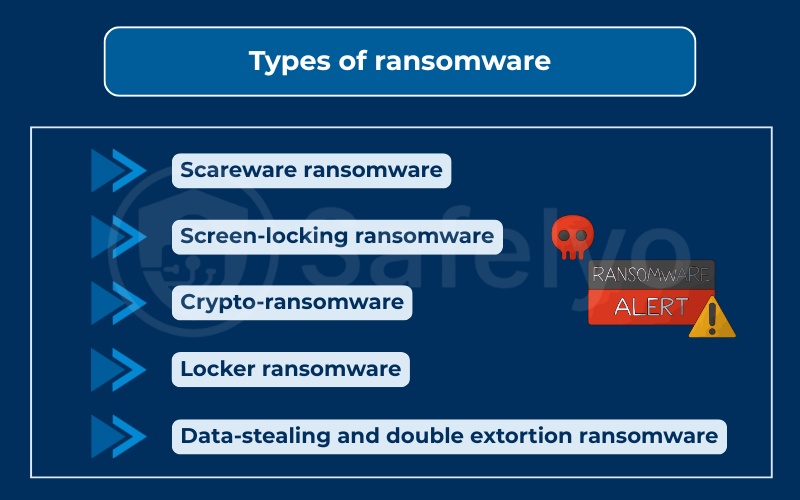
3. Types of ransomware
Ransomware is not a single technique but a family of attack methods. Each type has its own way of pressuring victims into paying. Over the years, countless ransomware variants have been developed, each fine-tuned to exploit specific weaknesses. Among ransomware variants are scareware, locker ransomware, crypto ransomware, and data-stealing models. Below are the main categories you should know.
3.1. Scareware ransomware
Scareware uses psychological tricks rather than encryption. It frightens users into paying by simulating security threats. Typical characteristics include:
- Fake alerts claiming the system is infected
- Pop-ups pretending to be antivirus or cleanup software
- Prompts to buy a “full version” to fix issues
Example: Variants like System Progressive Protection flooded screens with bogus virus warnings around 2012–2014. Victims paid $50–$100 for fake licenses, while no real infection existed.
Impact: While less destructive, scareware can spread panic and lead to financial loss, especially among less tech-savvy users.
3.2. Screen-locking ransomware
This type prevents access to the device by locking the screen. Instead of encrypting files, it blocks normal operations. Common traits include:
- A full-screen message that cannot be closed
- Fake warnings impersonating law enforcement
- Instructions demanding payment via prepaid cards or cryptocurrency
Example: Reveton ransomware (2012–2013) displayed fake FBI or police warnings accusing users of illegal activity. Victims were told to pay a “fine” through Ukash or MoneyPak.
Impact: Although files weren’t encrypted, victims faced downtime and often panicked into paying.
3.3. Crypto-ransomware (file-encrypting attacks)
Crypto-ransomware is the most destructive form because it uses strong encryption. Once inside a system, it usually:
- Scans for common file types such as documents, photos, and databases
- Encrypts them using AES or RSA algorithms
- Replaces file extensions and leaves a ransom note with payment instructions
Example: WannaCry (2017) spread using the EternalBlue exploit in the Windows SMB protocol. It infected over 200,000 computers in 150 countries, crippling the UK’s NHS, Telefónica in Spain, and FedEx operations in the U.S.
Impact: Critical services shut down, surgeries were canceled, and damages were estimated at $4 billion globally.
3.4. Data-stealing and double extortion ransomware
This newer model adds data theft before encryption. Such data theft often exposes trade secrets, customer records, and confidential communications. Attackers pressure victims by combining two tactics:
- Encrypting systems to block access
- Threatening to leak stolen data on public “leak sites” if payment is refused
Example: Maze ransomware (2019) pioneered this double extortion method. Later, groups like REvil and LockBit adopted the same approach, making data leaks common in ransomware attacks.
Impact: Beyond downtime, victims face lawsuits, regulatory fines, and reputational damage due to sensitive data exposure.
3.5. Locker ransomware
Locker ransomware prevents victims from accessing their entire system by blocking applications, desktop functions, and settings. Unlike crypto ransomware, it does not encrypt files, but it completely locks the user out of the device.
Example: Android locker ransomware families like SimplLocker spread in the mid-2010s, locking users’ mobile screens and demanding payment through prepaid cards.
Impact: Users lose access to all system functions, forcing many to pay even though their files remain intact.
>> Read more:
4. Real-world ransomware examples
Several high-profile cases illustrate how different ransomware types have evolved and spread:
- WannaCry (2017): A crypto-ransomware worm that spread automatically across networks using the EternalBlue exploit.
- Ryuk (2018–2020): Deployed via TrickBot and exposed RDP services, it disrupted hospitals and municipalities; one Florida city paid $600,000 in Bitcoin to restore access.
- LockBit (2022–2023): A professionalized Ransomware-as-a-Service group, leasing tools to affiliates and leaking stolen data when victims refused to pay.
Beyond these, other ransomware families have also left a lasting mark on cybersecurity. Security researchers track new ransomware variants every year, noting how quickly techniques evolve to bypass defenses. The table below summarizes some of the most notable examples, their type, core traits, and when they first appeared.
| Name | Type | Key characteristics | Year emerged |
|---|---|---|---|
| WannaCry | Encrypting | Spread via the EternalBlue exploit in Windows SMB; infected 200,000+ devices | 2017 |
| Cerber | RaaS | Early ransomware-as-a-service; affiliates shared profits | 2016 |
| Locky | Encrypting | Spread through phishing emails with Word macros; encrypted 160+ file types | 2016 |
| Ryuk | Encrypting | Targeted enterprises via phishing and TrickBot; spread laterally in networks | 2018 |
| GandCrab | RaaS | Large-scale affiliate program with frequent variants; mainly Windows systems | 2018 |
5. Ransomware-as-a-Service (RaaS)
Ransomware is no longer limited to skilled hackers. Today, many groups operate like businesses by offering Ransomware-as-a-Service (RaaS). This model allows affiliates with little technical knowledge to launch attacks using ready-made ransomware kits.
Here’s how RaaS typically works:
- Developers create the ransomware code and manage infrastructure (like payment portals and leak sites).
- Affiliates rent or buy access, then distribute the ransomware through phishing campaigns or exploited systems.
- Revenue sharing is arranged, with affiliates keeping a large share (often 60–80%) while developers take a cut.
Example: The LockBit gang is one of the most active RaaS operators. In 2022–2023, affiliates using LockBit’s platform targeted government agencies, schools, and corporations worldwide. Their leak site on the dark web publicly shamed victims who refused to pay.
Impact: RaaS lowers the barrier to entry for cybercrime. According to Dark Reading (2023), it has fueled an explosion in global ransomware incidents by enabling almost anyone with malicious intent to become an attacker.
6. Detecting and responding to ransomware
The faster ransomware is detected, the more damage can be avoided. Early warning signs, quick response steps, and proper communication can make the difference between a minor disruption and a complete shutdown.
6.1. Early warning signs you should not ignore
Ransomware often shows hints before the full attack executes. Common indicators include:
- Unusual system slowdown without a clear cause
- Files suddenly changing extensions or becoming inaccessible
- Antivirus or security tools are being disabled unexpectedly
- Strange network traffic, especially large outbound transfers
- Suspicious ransom note files appearing in folders
According to MITRE ATT&CK (2024), lateral movement and privilege escalation are often observed before full-scale encryption. This indicates that IT teams can take action if alerts are investigated quickly and threat detection signals are not ignored.
6.2. What to do in the first 24 hours
If ransomware is detected, fast action is critical. Recommended steps are:
- Isolate the affected system by disconnecting it from the network.
- Preserve evidence such as ransom notes, log files, and malicious binaries.
- Notify internal security or IT teams immediately.
- Avoid rebooting unless instructed by professionals, since this can trigger further encryption.
- Engage incident response experts to assess the scope of compromise.
6.3. Who to notify and how to recover
Responding effectively means coordinating with the right parties:
- Law enforcement: In the U.S., incidents should be reported to CISA or the FBI Internet Crime Complaint Center (IC3).
- Cyber insurance providers: If insured, claims should be initiated immediately.
- Vendors and partners: Notify stakeholders if data leaks are possible.
Recovery often involves:
- Wiping infected systems and reinstalling clean software
- Restoring files from offline or immutable backups
- Reviewing vulnerabilities (e.g., patching RDP or updating software)
According to CISA (2024), organizations with offline backups often recover without paying, while those without backups face weeks or months of downtime.
7. How to prevent ransomware attacks
Prevention is always cheaper and safer than recovery. By combining strong technical controls with user awareness, businesses and individuals can significantly reduce risk and strengthen cyber defenses.
7.1. Patch systems and secure configurations
Most ransomware exploits known vulnerabilities. To minimize exposure, organizations should:
- Apply operating system and software updates promptly.
- Disable unnecessary services and close unused ports. Reducing the attack surface makes it harder for ransomware operators to find a way in.
- Use endpoint protection with behavioral detection. Use endpoint detection and response systems with advanced behavioral analysis.
Example: WannaCry spread globally in 2017 because many systems had not applied Microsoft’s security patch MS17-010. Machines that were patched were immune.
7.2. Use MFA and least privilege access
Stolen or brute-forced passwords are a common entry point. Strong identity security includes:
- Enabling multi-factor authentication (MFA) for remote access and admin accounts
- Applying the principle of least privilege, granting only the access users truly need
- Regularly reviewing accounts for dormant or high-risk permissions
According to NIST (2023), MFA can block over 99% of common credential-based attacks.
7.3. Keep offline or immutable backups
Backups are the most effective safeguard against ransomware encryption. Best practices are:
- Maintain at least one offline backup disconnected from the network
- Consider immutable storage that cannot be altered by malware
- Test restoration regularly to ensure backups are usable
Safelyo’s analysis shows that companies with offline backups can restore operations in hours, while those without face weeks of downtime.
7.4. Train employees and run incident drills
Human error remains the top infection vector. To reduce risk:
- Provide phishing awareness training at least quarterly
- Run simulated phishing campaigns to measure resilience
- Conduct incident response drills so staff know what to do during an attack

A study cited by ENISA (2023) found that organizations running regular phishing simulations reduced successful attacks by 60%.
8. Business impact and costs
Ransomware attacks can cripple organizations financially and operationally. Large-scale ransomware attacks in recent years have shown how quickly entire industries can be disrupted. The costs extend far beyond the ransom payment itself, often reaching millions in hidden losses.
The main categories of impact include:
- Downtime and lost productivity: Systems may be offline for days or weeks, halting customer service, manufacturing, or healthcare operations.
- Direct financial loss: Ransom payments can range from thousands to millions of dollars, with no guarantee of file recovery.
- Data breach consequences: If attackers leak stolen data, organizations may face lawsuits, regulatory fines, and reputational damage.
- Recovery expenses: Hiring incident response teams, forensic investigators, and deploying new infrastructure adds significant costs.
- Insurance premiums: Cyber insurance claims often lead to higher premiums or reduced coverage in future contracts.
Example: In 2021, the Colonial Pipeline ransomware attack disrupted fuel supply across the U.S. East Coast. The company paid nearly $4.4 million in ransom, but the broader economic impact from fuel shortages and panic buying was estimated in the hundreds of millions.
According to IBM’s Cost of a Data Breach Report (2023), the average total cost of a ransomware incident now exceeds $5 million, including downtime, legal fees, and regulatory penalties.
9. Latest ransomware trends and threats (2026)
Ransomware in 2026 continues to grow more dangerous, targeting both individuals and organizations. The U.S. is among the most heavily affected regions. These are the key developments to watch.
9.1. Ransomware-as-a-Service (RaaS) growth
Criminals increasingly operate ransomware as a service. Affiliates can rent ready-made tools and launch attacks with little technical skill. In 2024, researchers identified more than 75 active groups, nearly double the previous year. This affiliate model has created a fragmented ecosystem where new groups quickly appear after old ones are disrupted.
9.2. AI-enhanced phishing and social engineering
Generative AI is now widely used by attackers. They create realistic phishing emails, forged invoices, and even deepfake voices to trick users. Because phishing remains the most common entry point, AI-powered campaigns are more convincing and harder to detect than traditional scams.
9.3. Cloud and SaaS platforms under attack
With more data stored online, ransomware groups are shifting toward cloud services and SaaS applications. A major campaign in 2024 exploited vulnerabilities in Snowflake accounts, compromising hundreds of organizations. Malware is also being tailored specifically to infiltrate collaboration platforms and cloud storage.
9.4. More aggressive extortion tactics
Modern ransomware goes beyond locking files. Many groups now:
- Steal sensitive data and threaten to leak it
- Launch DDoS attacks against public services
- Contact customers, regulators, or media to increase pressure
These strategies raise the stakes. Even with backups available, nearly half of victims still pay ransoms to avoid reputational damage.
9.5. Critical sectors remain vulnerable
Healthcare, education, and infrastructure continue to face the greatest impact. Hospitals experience delayed treatments, schools suspend classes, and municipalities lose access to essential systems. In 2024, one ransomware campaign crippled hundreds of U.S. clinics and pharmacies, underscoring the risks to critical services. The risks are amplified in an era of remote work, where employees access corporate resources from outside secured networks.
9.6. Shifts in payments and government response
Although attacks remain widespread, total ransom payments declined to 814 million dollars in 2024, a 35 percent drop from the year before. Law enforcement crackdowns, crypto seizures, and new regulations are key factors. The United Kingdom banned ransom payments in the public sector in 2026, while U.S. authorities sanctioned several ransomware operators. These measures reduce profits but also push criminals to focus on smaller, less regulated victims.
10. FAQs about what is ransomware
Ransomware raises many common questions for both individuals and businesses. Here are clear answers to the most frequent ones.
Should you pay the ransom?
Security agencies like CISA (2024) and the FBI strongly advise against paying. Payment encourages further attacks and does not guarantee data recovery. Some victims who paid still never received working decryption keys.
Can ransomware be removed without paying?
Yes, but success depends on the variant. In some cases:
- Free decryption tools are available from projects like No More Ransom.
- Security experts can wipe infected systems and restore from clean backups.
- For advanced strains, if no decryptor exists, only backups or full system rebuilds can restore functionality.
Who should I report a ransomware attack to?
Reporting helps authorities track and disrupt ransomware groups. Depending on your country:
- United States: Report to CISA or the FBI’s Internet Crime Complaint Center (IC3).
- European Union: Report to ENISA or national cyber agencies.
Other regions: Contact local Computer Emergency Response Teams (CERTs).
How fast can ransomware spread?
Ransomware can spread within minutes once executed. Worm-like variants such as WannaCry propagated automatically across networks in under an hour. Modern strains also move laterally, encrypting connected drives and cloud shares quickly.
11. Conclusion
Ransomware is one of the most damaging forms of cybercrime because it locks access to vital files, disrupts operations, and pressures victims into paying money. Understanding “what is ransomware”, how it works, and the main types helps both individuals and organizations stay prepared.
Key takeaways from this guide:
- Ransomware encrypts or locks files and systems, demanding payment for release.
- Infection usually happens through phishing, weak RDP, or unpatched software.
- Common types include scareware, screen lockers, crypto-ransomware, and double extortion attacks.
- Prevention relies on patches, MFA, offline backups, and employee training.
- The financial and reputational costs of an attack often far exceed the ransom itself. With preparation, businesses can limit the damage even if ransomware attacks occur.
From personal experience, I once saw a friend lose access to years of family photos after accidentally clicking a phishing link. They didn’t have backups, and the files were gone for good. That moment taught me that something as simple as keeping an external hard drive backup could save priceless memories from ransomware.
Staying vigilant and building resilience is the best defense. For more practical internet safety tutorials and protection strategies, explore the Antivirus section at Safelyo.













