Before I ever understood what VPN passthrough was, I spent nearly two hours trying to figure out why my VPN wouldn’t connect through my Asus router. Everything looked fine, my VPN app was configured correctly, the server was online, and my internet connection was stable. Yet, the connection kept failing. It wasn’t until I stumbled into my router’s advanced settings that I realized the problem: VPN passthrough was disabled.
This is a common frustration for anyone trying to set up a VPN through a home or office router. VPN passthrough is a lesser-known but essential feature for anyone using older VPN protocols on home or office networks.
In this article, I’ll walk you through:
- What VPN passthrough is and why it exists
- Why NAT routers block certain VPNs by default
- How VPN passthrough works behind the scenes
- Which VPN protocols require passthrough, and which don’t
- When you actually need to enable it (and when you really don’t)
- Step-by-step instructions to activate it on your router
- Safer and more modern alternatives to using a passthrough today
Whether you’re a remote worker or a small business admin, this guide is for you. It will help you secure your internet traffic. You’ll avoid hours of confusion. Plus, you’ll get your VPN working as it should.
Now let’s start with the basics: What is VPN passthrough, really?
1. What is VPN passthrough?
If you’ve ever tried setting up a VPN at home and couldn’t connect, despite everything seeming correct, it might not be your VPN provider’s fault. The issue could lie with your router’s handling of private IP address assignments. Specifically, it may not have VPN passthrough enabled.
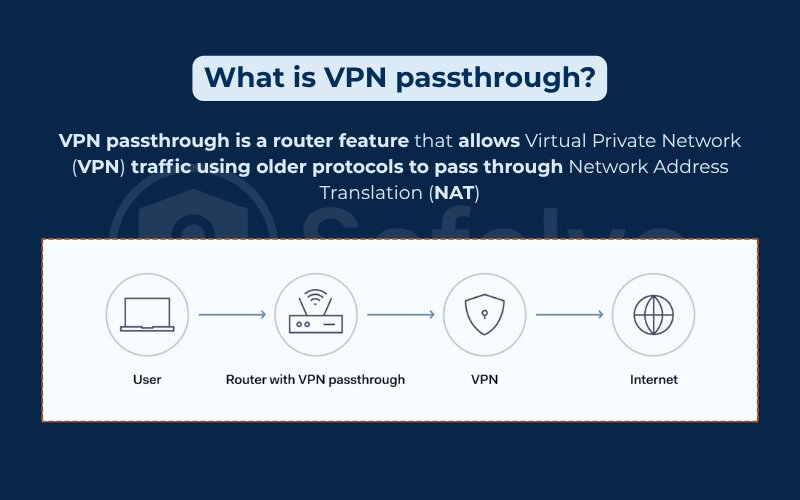
VPN passthrough is a router feature that allows Virtual Private Network (VPN) traffic using older protocols to pass through Network Address Translation (NAT). It’s particularly important for legacy VPN protocols like PPTP, IPsec, and L2TP, which aren’t naturally compatible with NAT environments. When passthrough is not enabled, these protocols often fail to establish secure tunnels. This causes confusion for users who are unaware of this technical barrier. It is especially problematic for those relying on SSL encryption for their connections.
This function was originally developed to address limitations in how VPN traffic is handled by consumer-grade routers. Older VPN protocols rely on specific tunneling methods like ESP (Encapsulating Security Payload) and GRE (Generic Routing Encapsulation), which may require a Session ID for tracking. Because of this, they often get blocked by NAT routers. These routers may not understand these protocols. They may also drop data packets that lack Call ID information.
I used to think VPN passthrough was something found inside the VPN app itself. But when I tried to set up a site-to-site VPN for remote access on a work laptop using my old modem at home, I kept hitting connection errors. After several failed attempts and a deep dive into router settings, I discovered the culprit: VPN passthrough was disabled. Once I enabled it, the connection worked flawlessly, adhering to the established access policies of the network.
Today, VPN passthrough is often misunderstood or overlooked, especially as newer VPN technologies like OpenVPN utilize network segmentation to improve security. Understanding this feature could be crucial to mitigating security vulnerabilities associated with legacy protocols.
In the next section, we’ll look at why routers block VPN traffic in the first place and why older VPN protocols struggle with NAT.
2. Why do NAT routers block legacy VPN protocols?
One of the key reasons people ask “what is VPN passthrough” is that their router blocks VPN traffic without warning.
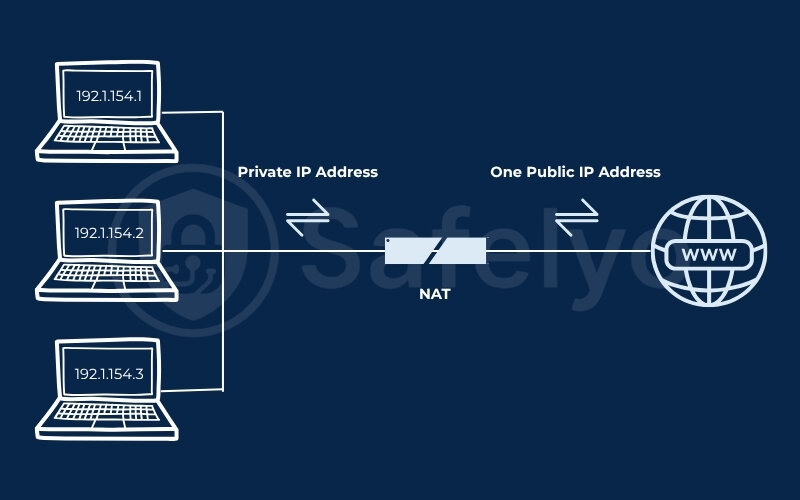
To understand VPN passthrough, you first need to understand why VPN connections sometimes fail. The key factor lies in how home and office routers manage network traffic using something called NAT, or Network Address Translation.
NAT allows multiple devices to share a single public IP address. It modifies packet headers as data enters and exits the local network, making it efficient but problematic for certain types of traffic. Older VPN protocols like IPsec and PPTP use tunneling mechanisms (such as ESP and GRE) that don’t include standard port information. As a result, NAT doesn’t know how to handle them and may discard or block them.
For example:
- PPTP uses GRE, which doesn’t include port numbers, making it hard for NAT to track or forward sessions correctly.
- IPsec uses ESP, which also lacks ports, leading to dropped packets unless specific passthrough settings are enabled.
When I was working from home using a TP-Link router and trying to connect via an IPsec VPN, I spent hours troubleshooting. The VPN client kept failing with generic errors. I tested everything: Credentials, firewall rules, and server reachability. In the end, the issue came down to my router’s NAT engine rejecting ESP packets. Once I enabled IPsec passthrough in the router settings, the VPN connected immediately.
According to Cisco, “Many consumer routers do not support IPsec NAT traversal unless passthrough settings are manually configured. Without this, ESP traffic may be silently dropped.”
These limitations explain why VPN passthrough is still needed in many environments. In the next section, we’ll dive deeper into how VPN passthrough works and what it actually does behind the scenes to keep your connection alive.
3. How VPN passthrough works
At its core, VPN passthrough is a function built into your router that allows legacy VPN traffic to successfully pass through a NAT (Network Address Translation) environment. To understand how it works, we first need to explore what typically goes wrong when passthrough is not enabled.
3.1. Why legacy VPNs get blocked at the router
Older VPN protocols like PPTP and IPsec use tunneling methods that weren’t designed to work with NAT. Specifically:
- PPTP uses a protocol called GRE (Generic Routing Encapsulation), which doesn’t include port numbers.
- IPsec relies on ESP (Encapsulating Security Payload), which also lacks ports.

NAT routers rely heavily on port numbers to route traffic between devices. When they encounter GRE or ESP packets, they often don’t know where to send them. In some cases, they may block these packets entirely for security reasons. This is where VPN passthrough comes in.
3.2. What VPN passthrough actually does
To understand what is VPN passthrough, think of it as the router’s ability to recognize and allow legacy VPN protocols that would otherwise be blocked by NAT.
When you enable passthrough in your router’s settings, you’re telling it to recognize and forward specific VPN traffic types (GRE or ESP) through NAT to your device. In simpler terms, it creates a clear path for outbound traffic through the router’s firewall so that your VPN connection can be established successfully.
Imagine trying to send a package through airport security that looks suspicious because it lacks a label (i.e., port number). Without VPN passthrough, that package gets flagged or rejected. With passthrough enabled, the security checkpoint is trained to recognize it as safe and send it through.
After several failed attempts at connecting to a company VPN from home, I finally opened up my router settings and enabled the “IPsec passthrough” option. I had no idea what it did at the time, but the connection worked instantly. That small setting saved me hours of unnecessary troubleshooting and eventually led me to dive deeper into how VPN protocols actually interact with NAT and NAT-Traversal firewall systems.
3.3. Does every VPN need passthrough?
Not anymore. Modern VPN protocols like OpenVPN, WireGuard, and even IKEv2/IPsec with NAT-T (NAT traversal) are built to work naturally with NAT environments, avoiding the need for passthrough entirely. That said, many routers still include passthrough settings because some organizations and users rely on legacy systems that haven’t transitioned yet.
Understanding how VPN passthrough works helps clarify why certain VPNs succeed or fail based on router configuration. In the next section, we’ll explore which protocols rely on passthrough and how compatible they are with modern networks.
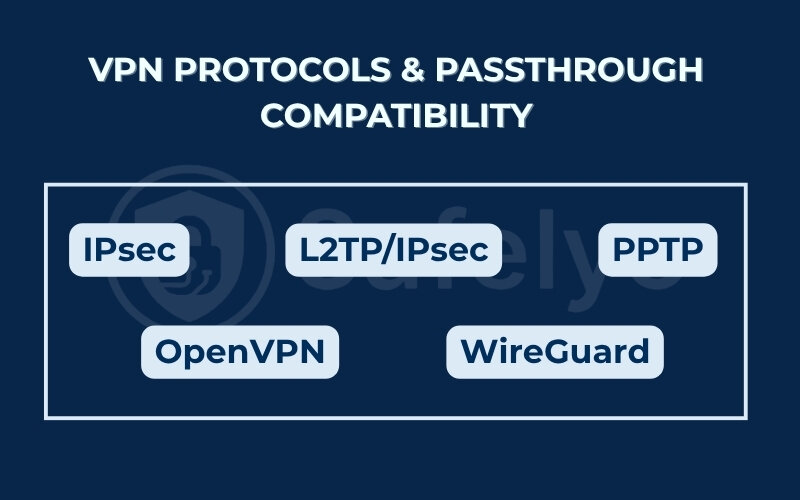
4. VPN protocols & passthrough compatibility
Not all VPN protocols are created equal, especially when it comes to how they interact with NAT routers. Some are heavily dependent on VPN passthrough, while others were designed with NAT traversal in mind. Understanding which protocols require passthrough is key to setting up a stable and secure VPN connection.
That’s why knowing what is VPN passthrough and how it interacts with each protocol is so important for troubleshooting and setup.
4.1. PPTP (Point-to-Point Tunneling Protocol)
PPTP is one of the oldest VPN protocols and uses GRE (Generic Routing Encapsulation) to create its tunnel. Unfortunately, GRE doesn’t use ports, making it difficult for NAT routers to track and forward sessions properly.
- Passthrough requirement: Yes, for GRE
- NAT compatibility: Poor without passthrough
- Security note: PPTP is widely considered insecure and deprecated by most security professionals
I once set up a VPN for a small office that still used PPTP due to its simplicity. However, employees constantly complained that they couldn’t connect from home. After some digging, I found that the office router hadn’t enabled GRE passthrough. Once that was fixed, the connections stabilized. Still, I recommended switching to a more secure protocol shortly after.
4.2. L2TP/IPsec (Layer 2 Tunneling Protocol + IPsec)
L2TP itself doesn’t provide encryption, which is why it’s commonly paired with IPsec for security. This combo uses multiple ports:
- UDP 500 for IKE
- UDP 1701 for L2TP
- UDP 4500 for NAT traversal (if available)
- ESP for ciphered traffic
If NAT-T is not supported or enabled, VPN passthrough is required to forward ESP traffic.
- Passthrough requirement: Yes, for IPsec
- NAT compatibility: Moderate with NAT-T; poor without passthrough
- Security note: More secure than PPTP, but complex to configure manually
4.3. IPsec (Internet Protocol Security)
Used widely in corporate environments, IPsec provides strong encryption and authentication. However, it’s also one of the most problematic protocols when used with NAT.
It uses ESP and AH (Authentication Header) protocols, both of which are incompatible with NAT unless:
- NAT-T (UDP encapsulation) is used
- VPN passthrough is enabled
- Passthrough requirement: Yes, unless NAT-T is implemented
- NAT compatibility: Low without NAT-T or passthrough
- Security note: Very secure, enterprise-grade standard
At one point, I was supporting a client whose VPN kept timing out intermittently. They were using a pure IPsec connection. We found that while their router allowed UDP 500 and 4500, ESP traffic wasn’t making it through. Enabling IPsec passthrough immediately resolved the issue, reinforcing how protocol-layer quirks can break even well-configured systems.
4.4. Do modern VPNs need passthrough?
Not typically. VPNs like OpenVPN, WireGuard, and IKEv2/IPsec with NAT-T are designed to function efficiently in NAT environments without needing passthrough settings.
Here’s a quick compatibility summary:
| VPN Protocol | Needs Passthrough? | NAT Compatibility | Notes |
|---|---|---|---|
| PPTP | Yes (GRE) | Poor | Deprecated/insecure |
| L2TP/IPsec | Yes (ESP) | Moderate | Better with NAT-T |
| IPsec | Yes (ESP) | Low | Requires passthrough or NAT-T |
| OpenVPN | No | High | Uses standard ports (UDP/TCP) |
| WireGuard | No | High | Modern, fast, NAT-friendly |
Understanding these differences can save hours of confusion during setup. Next, we’ll explore whether VPN passthrough is still necessary in today’s modern internet environment, or if it’s just a relic of outdated systems.
5. Do you still need VPN passthrough today?
With the rise of modern VPN protocols and smarter router firmware, many users wonder: Is VPN passthrough still relevant in 2026? The short answer is: It depends on your setup.
VPN passthrough was once essential for anyone using older protocols like PPTP or IPsec, especially when routers had limited support for encrypted traffic. But things have changed.

5.1. When passthrough is still needed
There are a few scenarios where VPN passthrough remains useful:
- Older routers or modems: If your router is several years old, it may not support NAT traversal techniques automatically.
- Legacy VPN clients: Some organizations still rely on IPsec or PPTP-based VPNs for compatibility reasons.
- Business environments: In some enterprise setups, VPN passthrough may be required to allow remote workers to connect to an on-premises VPN concentrator using legacy configurations.
In these cases, if passthrough isn’t enabled, the VPN may fail to establish or will drop unexpectedly, even if everything else is set up correctly.
Just recently, I helped a friend who couldn’t connect to his company’s IPsec VPN while working from home. After ruling out firewall issues and confirming the VPN server was reachable, we checked his router. As it turned out, the IPsec passthrough setting was disabled by default. Once we toggled it on, the VPN connected immediately.
5.2. When it’s no longer necessary
Most modern VPN services (like NordVPN, Surfshark, or ExpressVPN) now use protocols that handle NAT traversal internally:
- OpenVPN uses standard UDP or TCP ports and works seamlessly through most NAT setups.
- WireGuard is lightweight, efficient, and NAT-friendly.
- IKEv2/IPsec with NAT-T encapsulates ESP inside UDP, bypassing NAT-related issues.
These protocols do not need VPN passthrough to work properly, and enabling it won’t offer any benefit. If you:
- Use a modern VPN provider
- Have a relatively new router
- Don’t manually configure VPN settings
…then chances are, you don’t need passthrough at all.
5.3. How to determine if you need passthrough
If you’re still wondering what is VPN passthrough and whether your system needs it, this checklist can help clarify your situation:
- Are you using PPTP, L2TP/IPsec, or raw IPsec? → You might need VPN passthrough
- Does your VPN connect fine on mobile data, but fail on your home Wi-Fi? → Router passthrough might be the issue
- Are you using OpenVPN or WireGuard? → Passthrough likely not required
Understanding whether VPN passthrough is necessary can help you avoid unnecessary troubleshooting, or worse, abandoning a perfectly working VPN due to simple router settings.
In the next section, I’ll walk you through how to enable VPN passthrough step-by-step on most home routers.
6. How to enable VPN passthrough on a router
If your VPN isn’t connecting and you suspect passthrough is the culprit, don’t worry, enabling VPN passthrough is usually quick and safe, as long as you know what to look for.
Most consumer-grade routers come with passthrough options for PPTP, IPsec, and sometimes L2TP. However, these settings are often buried in advanced menus or labeled differently depending on the brand.
6.1. Where to find VPN passthrough settings
Here’s where you can typically locate the passthrough options on popular router brands:
| Router Brand | Navigation Path to VPN Passthrough |
| TP-Link | Advanced > NAT Forwarding > VPN Passthrough |
| Asus | Advanced Settings > WAN > NAT Passthrough |
| Netgear | Advanced > Setup > WAN Setup |
| Linksys | Security > VPN Passthrough |
| D-Link | Advanced > Firewall Settings or VPN Settings |
The naming may vary slightly, so look for terms like “IPSec Passthrough”, “PPTP Passthrough”, or “L2TP Passthrough”.
Before changing anything, it’s a good idea to back up your router configuration. Most routers offer this feature in the Administration or System Tools section.
I once spent nearly an hour clicking through my Asus router settings just to find the passthrough menu. The labels weren’t intuitive, and I only found them under the WAN section after some trial and error. Since then, I have always taken a screenshot of the full menu path after setup, which saves time if I need to reconfigure or explain it to someone else.
6.2. What to enable (and what not to)
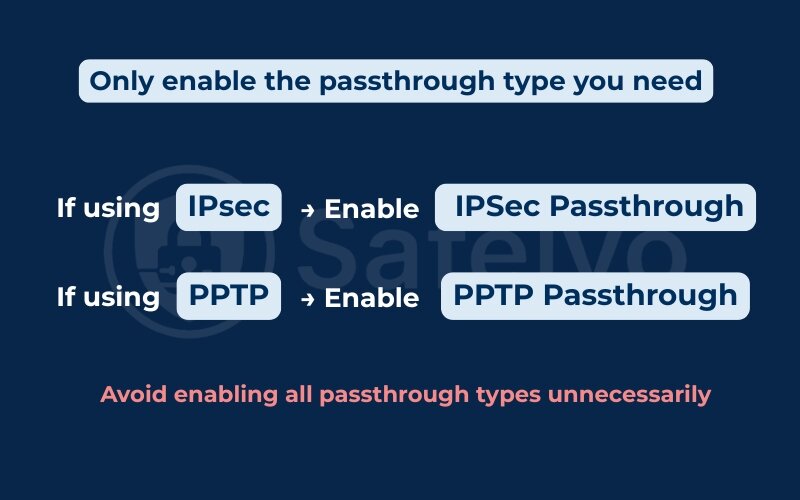
If you know which VPN protocol you’re using, only enable the passthrough type you need. For example:
- If using IPsec → Enable IPSec Passthrough
- If using PPTP → Enable PPTP Passthrough
Avoid enabling all passthrough types unnecessarily, as this can open up vulnerabilities or create configuration conflicts.
6.3. Additional tips and cautions
- Restart your router after enabling passthrough to ensure the settings take effect.
- If your VPN still doesn’t work, double-check your firewall settings, port forwarding rules, and VPN client configuration.
- For enterprise users, consult your network admin before changing any router settings that might impact overall security policies.
Once VPN passthrough is properly enabled, most legacy VPN connections should establish without further issues. But as you’ll see in the next section, there’s a difference between passthrough and true VPN router functionality, and it’s important to know which one you actually need.
7. VPN passthrough vs VPN router
It’s easy to assume that if your router supports VPN passthrough, it’s fully “VPN-ready.” But in reality, VPN passthrough and VPN routers serve very different roles, and knowing the difference can save you from a lot of misconfigured setups.

7.1. What is VPN passthrough?
VPN passthrough means your router can recognize and allow VPN traffic (like GRE or ESP) to pass through its firewall and NAT system. This enables a device behind the router, such as your laptop or phone, to connect to a VPN server located on the internet.
The router itself is not running the VPN client or encrypting the traffic. It’s simply acting as a gatekeeper that lets the VPN data through.
7.2. What is a VPN router?
A VPN router, on the other hand, has built-in VPN client (and sometimes server) capabilities. This means:
- The router itself connects to the VPN on behalf of all devices on the network
- Every connected device: phones, laptops, smart TVs, benefits from encrypted VPN protection without installing apps individually
- It’s ideal for households or offices wanting an “always-on” VPN at the network level
VPN routers support protocols like OpenVPN, WireGuard, or even IPsec, and often include advanced settings for custom VPN profiles.
When I bought my first router labeled “VPN supported,” I assumed it would protect all my devices by default. After setting it up, I realized it only offered passthrough, meaning the router wasn’t actually running the VPN. I had to upgrade to a model with OpenVPN client support to get the true “whole-network VPN” experience I was looking for.
7.3. Which one should you use?
Here’s a quick breakdown to help you decide:
| Feature | VPN Passthrough | VPN Router |
|---|---|---|
| Handles VPN traffic? | Yes (passes it through) | Yes (routes and encrypts it directly) |
| Requires VPN app on device? | Yes | No |
| Best for | Legacy protocol support | Always-on protection for all devices |
| Technical complexity | Low | Medium to high |
If your goal is simply to use a VPN on one device, passthrough may be enough. But if you want network-wide protection without configuring each device separately, investing in a true VPN router is the way to go.
Next, we’ll explore an important consideration: Should you disable VPN passthrough when it’s not in use? Let’s take a closer look.
8. Should you disable VPN passthrough?
If you’re not using a VPN that requires passthrough, disabling it is generally a smart move, especially from a security and network stability perspective. While passthrough itself isn’t inherently dangerous, it can introduce unnecessary exposure when left enabled without purpose.
8.1. Why it’s safer to disable passthrough when unused
Once you understand what is VPN passthrough, it’s easier to evaluate whether leaving it enabled poses any security risks in your current setup.
Here are a few good reasons to turn off VPN passthrough if you’re not actively using an older VPN protocol:
- Reduces attack surface: Legacy protocols like PPTP and IPsec (especially without NAT-T) have known vulnerabilities. Leaving passthrough enabled may open up unnecessary paths into your network if exploited.
- Improves network performance and clarity: Having all passthrough options enabled at once can sometimes confuse the router’s NAT engine, leading to intermittent drops or failed VPN handshakes.
- Prevents misconfiguration: On networks with multiple users or devices, an active passthrough setting could allow unauthorized VPN access, bypassing monitoring tools or parental controls.

After switching to WireGuard for personal VPN use, I decided to revisit my router settings and disable all passthrough options. I didn’t notice any drop in performance; in fact, file transfers between devices on my LAN became slightly more stable. It made me realize how often we forget to clean up outdated settings once they’re no longer needed.
8.2. When you might keep it enabled
There are a few cases where it still makes sense to leave passthrough enabled:
- You’re using an older work VPN that relies on IPsec or PPTP.
- A legacy device (e.g., Windows XP-era laptop or corporate scanner) needs it.
- You’re troubleshooting a VPN connection and want to rule out NAT issues.
In these scenarios, make sure:
- You only enable the specific passthrough type you need (e.g., just IPsec).
- You disable it again once you’re done, especially on shared or public-facing networks.
8.3. How to check if passthrough is active
To verify:
- Log in to your router’s admin panel.
- Navigate to sections like “VPN Settings,” “Security,” or “Advanced WAN.”
- Check for options labeled “IPSec Passthrough”, “PPTP Passthrough”, or “L2TP Passthrough”.
If they’re enabled but unused, it’s a good idea to switch them off, just as you would with any service port or protocol you’re no longer using.
Coming up next, we’ll look at modern alternatives to VPN passthrough that offer better performance, easier setup, and stronger security.
9. Alternatives to VPN passthrough
As networking technology advances, VPN passthrough is increasingly being replaced by smarter, more secure solutions. If you’re looking for better performance, easier setup, and enhanced privacy, there are several modern alternatives that don’t rely on legacy passthrough functionality.

9.1. Use VPN protocols with built-in NAT traversal
Modern protocols are designed to work seamlessly through NAT routers without needing any special passthrough settings. These include:
- OpenVPN: A widely supported, open-source protocol that uses standard ports (UDP 1194 or TCP 443), making it highly NAT-friendly and firewall-compatible.
- WireGuard: A lightweight, fast, and secure protocol that uses a single UDP port. Its simplicity means fewer compatibility issues with routers.
- IKEv2/IPsec with NAT-T: Unlike raw IPsec, IKEv2 includes NAT Traversal (NAT-T), which encapsulates traffic in UDP packets, allowing it to pass through NAT effortlessly.
If your VPN provider offers these protocols (as most top-tier services like NordVPN, Mullvad, and Proton VPN do), there’s no need to worry about enabling passthrough on your router.
In recent years, I’ve completely stopped enabling VPN passthrough when setting up VPNs for friends or clients. With services like Mullvad and ProtonVPN offering WireGuard by default, connections work right out of the box, even behind basic home routers. It’s a huge improvement over the finicky, port-based issues of the past.
9.2. Enterprise-grade alternatives to traditional VPNs
For businesses, there’s also a shift away from legacy VPNs toward more modern, scalable solutions such as:
- SASE (Secure Access Service Edge): Combines networking and security functions into a cloud-delivered service. It replaces VPNs with identity-based access and better control over remote traffic.
- ZTNA (Zero Trust Network Access): Offers granular access to apps based on user/device identity and context, not network location. This eliminates the need for full-tunnel VPN access.
- SD-WAN (Software-Defined Wide Area Network): Optimizes traffic across multiple locations and ISPs while maintaining encrypted connectivity without traditional VPN complexity.
These solutions are built with cloud-first, remote-first environments in mind, offering stronger security models than traditional VPNs.
9.3. Why move away from passthrough-based setups?
Here are the key benefits of upgrading to passthrough-free VPN architectures:
- Better security: Modern protocols avoid the vulnerabilities found in legacy tunneling methods.
- Faster performance: WireGuard, for example, is known for superior speed and lower overhead.
- Smoother compatibility: No need to tweak router settings or worry about port conflicts.
- Scalability: Especially for businesses, SASE and ZTNA scale far better than traditional VPNs.
If you’re still relying on VPN passthrough, it’s likely a sign your setup could use an upgrade.
In the next section, we’ll answer some of the most common questions users have about VPN passthrough, based on real-world troubleshooting experience.
10. FAQ about VPN passthrough
If you’re still unsure about what is VPN passthrough or whether you actually need it, the following answers address some of the most common questions people ask during setup and troubleshooting.
Does VPN passthrough slow down my internet?
Not directly. VPN passthrough is simply a router feature that allows VPN traffic to pass through. It doesn’t encrypt or route the data itself. However, if your router is underpowered and handling legacy VPN protocols inefficiently, you might experience slower speeds. Upgrading to a VPN protocol like WireGuard or OpenVPN can improve performance significantly.
Should I enable all passthrough options?
No. You should only enable the passthrough setting for the protocol you’re actively using. For example, if your VPN uses IPsec, only enable IPsec Passthrough. Enabling all forwarding types can cause unnecessary exposure and possible configuration conflicts.
I once enabled all passthrough settings at once, thinking it would “cover all my bases.” The result? My VPN couldn’t connect at all. Disabling unused transmission types fixed the issue.
Is VPN passthrough required for OpenVPN or WireGuard?
No. Both OpenVPN and WireGuard are designed to work well with NAT and firewalls without needing passthrough. In fact, many routers don’t even offer passthrough settings for these protocols, and that’s perfectly fine.
Can I use VPN passthrough for torrenting?
VPN passthrough is unrelated to torrent support. Torrenting depends on your VPN provider’s policies, P2P support, and bandwidth, not whether passthrough is enabled. Still, if you’re using an older VPN protocol that needs passthrough and it’s not enabled, your VPN may not connect at all.
What if my VPN works on mobile data but not on home Wi-Fi?
This could indicate that your home router is blocking VPN traffic. If you’re using a legacy VPN protocol like PPTP or IPsec, try enabling the appropriate passthrough setting in your router. If that doesn’t help, switching to a NAT-friendly protocol like WireGuard may resolve the issue.
11. Conclusion
VPN passthrough played an essential role in making legacy VPNs work over NAT networks. If you’re using protocols like PPTP or IPsec without NAT-T, enabling passthrough can mean the difference between a working connection and a frustrating failure.
But in today’s modern internet landscape, its relevance is fading. Most current VPN services support NAT-friendly protocols like OpenVPN and WireGuard, which work out of the box without the need for router tweaks. That means for most users, especially those relying on apps from top providers. You may never need to touch this setting at all.
That said, having a solid understanding of what is VPN passthrough and how it works can still be incredibly useful. Whether you’re helping a coworker troubleshoot a connection issue or maintaining legacy equipment in a small office, this knowledge can save you hours of unnecessary guesswork.
After nearly a decade of working with VPNs, both personally and professionally, I rarely rely on passthrough anymore. But when connection issues arise, it’s one of the first things I check. Knowing how it works has helped me support others more effectively, especially in remote environments where every minute counts.
If you’re ready to go deeper, I highly recommend checking out the beginner-friendly breakdown on the Privacy & Security Basics section at Safelyo – a great starting point to understand how modern VPN technologies are shaping online privacy and security.













