Mastering how to bypass censorship with a VPN isn’t just a tech hack; it’s a vital skill for reclaiming your digital freedom and accessing an unfiltered internet. For journalists, students, or anyone living in or traveling through restrictive regions, being cut off from global information isn’t just an inconvenience – it’s a critical barrier.
With over a decade in the cybersecurity field, I’ve seen countless users hit a wall when their standard VPN suddenly stops working. This is because modern censorship isn’t a simple block; it’s a sophisticated system designed to detect and shut down VPN traffic itself. But the right VPN, equipped with the right technology, is built for this exact fight.
In this no-nonsense guide, I will show you:
- Why a VPN is your best defense against sophisticated censorship.
- The ‘secret weapon’ technology that makes a VPN invisible to firewalls.
- A step-by-step process to get set up safely and correctly.
- What to do when your connection is blocked or not working.
Don’t let digital borders control your access to information. Let’s get you connected to the open web – securely and effectively.
1. Why do you need a VPN to bypass censorship
When you find your favorite news site or social media app suddenly inaccessible, you’ve likely hit a digital wall. This is internet censorship, and it comes in several forms, from simple IP address blocks and DNS filtering to more advanced methods designed to control the flow of information.
But the most formidable challenge today is deep packet inspection (DPI). Think of DPI as a nosy postman who doesn’t just read the address on your envelope (the website you want to visit). They open the envelope and read the entire letter inside (your actual data and activity). This allows government firewalls not only to block specific destinations but also to identify and block the very pattern of standard VPN traffic itself.
This is where basic tools like free proxy servers fall short. A proxy might change your “address,” but it often leaves your “letter” completely unsealed and easy for the postman to read.
A quality VPN is fundamentally different. It doesn’t just reroute your connection – it wraps your entire internet traffic in a layer of powerful encryption. This means that even if the “postman” (your internet service provider or a government firewall) inspects your data packet, all they see is scrambled, unreadable code. A VPN protects your identity from surveillance while simultaneously granting you access to the open web.
And this fight for access is more critical than ever. According to reports from Freedom House, global internet freedom has declined for more than a decade, with an increasing number of governments deploying sophisticated censorship techniques like DPI. In this environment, a VPN isn’t a luxury – it’s a necessary tool for digital survival.
2. How a VPN works to unblock websites and defeat censorship
So, how does a VPN actually achieve this feat? It relies on a powerful one-two punch that tackles both location-based blocks and direct surveillance.
2.1. The basics: Masking your IP address and encrypting traffic
First, the moment you connect to a VPN server, it instantly hides your real IP address – the unique digital identifier that reveals your physical location. It replaces it with a VPN IP address from the VPN server you’ve chosen. To any website, firewall, or online service, you now appear to be browsing from the server’s location, whether that’s in a different city or halfway across the world. This simple switch is often enough to get around basic regional blocks.
But hiding your location is only half the job. The real security comes from encryption. Reputable VPNs use military-grade AES-256 encryption, the same standard trusted by governments and security experts. This technology scrambles all the data leaving your device, turning your online activity into an unreadable mess for any outsiders.
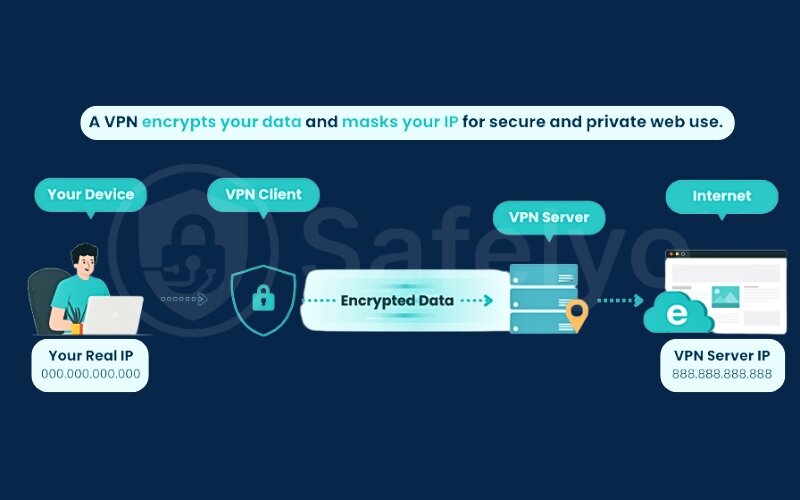
Remember our nosy postman? With VPN encryption, not only is your data in a new envelope (a new IP address), but the letter inside is written in an unbreakable code. Your ISP can see that you’re connected to a VPN, but they have no idea what websites you’re visiting or what you’re doing online. This is the foundation of digital privacy.
2.2. The secret weapon: Obfuscated servers and stealth VPN technology
The foundation of IP masking and encryption works well against basic blocks. But what happens when you’re up against a highly restrictive firewall that uses deep packet inspection (DPI)? This is where standard VPNs fail. Even though the DPI can’t read your encrypted data, it can recognize the shape and structure of the VPN packets themselves. It detects the “VPN signature” and blocks the connection on sight.
This is where the real game-changer comes in: Stealth VPN technology, often deployed through what are called obfuscated servers.
Obfuscation is the art of disguise. This technology takes your already-encrypted VPN traffic and wraps it in an additional layer, making it look like regular, everyday HTTPS traffic – the same kind of secure traffic you generate when logging into your bank or shopping online. The firewall’s DPI scans your connection, sees what appears to be normal browsing, and simply lets it pass through. It effectively hides the fact that you are using a VPN at all.
Many leading providers have their own names for this feature, such as “StealthVPN,” “Chameleon Protocol,” or simply an “Obfuscated” server option in their app. But the principle is the same: it’s designed to be undetectable.
From my experience helping users in heavily restricted environments, this is the single most important feature. Many users get frustrated when their standard VPN connection stops working after a few days or weeks. This is almost always because the government’s DPI has identified and blacklisted the standard VPN protocol. Switching to an obfuscated VPN is no longer an advanced trick – it is the essential next step for maintaining a stable and secure connection.
3. Step-by-step guide: How to bypass censorship with a VPN safely
Having the right tool is only half the battle. How you use it is what truly determines your success and safety. I’ve seen many people subscribe to a fantastic VPN but fail to bypass censorship because they missed these crucial setup steps. Follow this guide precisely to build a robust defense.
Quick Guide: Your 4 Steps to Freedom
- Choose the Right Tool: Select a VPN proven to have obfuscated servers and a kill switch.
- Prepare in Advance: Download and install the app before entering a restricted area.
- Activate Defenses: Go into the settings and enable the kill switch and leak protection.
- Connect Smartly: Always connect to a designated “obfuscated” or “stealth” server.
Now, let’s break down exactly why each of these steps is so important.
3.1. Step 1: Choose a reliable anti-censorship VPN
This is the most critical decision you’ll make. Not all VPNs are created equal, and most standard services are simply not built for this high-stakes task. Over the years, I’ve developed a non-negotiable checklist for anyone venturing into a censored digital space.
Here’s what you absolutely must look for:
| Feature | Why It’s Non-Negotiable |
| Verified No-Logs Policy | A VPN’s promise not to record your activity is good. A policy verified by an independent audit is better. Think of it as the difference between a restaurant saying its kitchen is clean versus having an official health inspector’s certificate on the wall. |
| Obfuscated Servers / Stealth VPN | As we discussed, this is the technology that hides your VPN usage. Without it, your connection is an easy target for advanced firewalls. |
| VPN Kill Switch | This is your digital safety net. If your VPN connection unexpectedly drops, the kill switch instantly cuts off all internet access. It’s like an emergency brake that stops your car from rolling into traffic if the engine stalls. This prevents your real IP address from being exposed, even for a second. |
| DNS Leak Protection | When you type a website name, your device asks a digital “phonebook” (a DNS server) for its real address. This feature ensures you are only using the VPN’s private, secure phonebook, not your ISP’s public one, which logs every website you look up. |
| Servers in Nearby, Free Countries | Connecting to a server closer to your physical location almost always results in better speeds and a more stable connection. It’s like making a local call instead of an international one – the signal is just clearer and stronger. |
Expert’s Note: The One Thing You Must Not Overlook
Before subscribing to any VPN, use their free trial or money-back guarantee to test an obfuscated server connection from your location. A VPN that works flawlessly for someone in one country might be blocked in yours. As a cybersecurity consultant, I can’t stress this enough: real-world testing is non-negotiable.
3.2. Step 2: Download and install the VPN before you need it
This might sound obvious, but it’s the most common mistake I see. I get frantic messages from people who’ve just landed in a country with heavy censorship, only to find the VPN provider’s website is already blocked. They are locked out before they can even get the key.
Always download and install the VPN application on all your devices before you travel or before an anticipated internet crackdown. Think of it like this: Trying to download a VPN after censorship is in place is like trying to buy a fire extinguisher when the store is already on fire.
3.3. Step 3: Enable critical security features
Once the VPN is installed, don’t just hit “Connect.” You need to perform a quick pre-flight check. Open the app’s settings or preferences menu. I never go online in a sensitive area without first ensuring these two options are turned on:
- Activate the Kill Switch: Find the setting labeled “Kill Switch” or “Network Lock” and turn it on.

- Enable DNS Leak Protection: This is usually on by default with good VPNs, but it costs nothing to double-check.
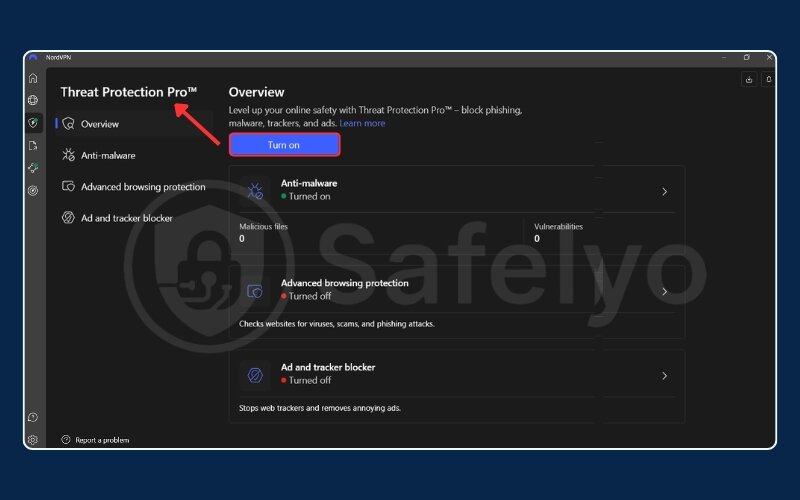
This ten-second check is one of the simplest and most effective things you can do to protect your real identity.
3.4. Step 4: Connect to an obfuscated server
Now you’re ready to connect. Don’t just pick the first server on the list. You need to specifically choose one that uses stealth technology.
Look for a server list labeled “Obfuscated,” or “Stealth,” or you may need to go into your settings and change the connection “Protocol” to an option like “OpenVPN (TCP)” or one explicitly named after their stealth feature. If you can’t find it, check the VPN provider’s support page.
For the best performance, try connecting to a server in a geographically close country that respects internet freedom. For example, if you’re in a restricted part of Asia, connecting to a server in Japan or South Korea might be faster than connecting to one in the USA.
4. What to do when your VPN is blocked or not working
It’s the moment every user in a restricted region dreads: you open your VPN, hit “Connect,” and nothing happens. Or worse, it connects for a moment and then drops. This is a sign that the firewall has detected and blocked your attempt.
Don’t panic. In my experience, this is rarely a permanent problem. It’s a cat-and-mouse game. The firewall learns to block a server or method, and you just have to switch your approach. Here is a troubleshooting sequence I always follow:
Play musical servers.
This is your first and easiest move. Disconnect and try connecting to a few different servers in the same country you were using. If that fails, expand your search and try connecting to servers in a different nearby country. Often, a firewall has only blacklisted a specific range of IP addresses, and switching to a new one is all it takes.
Change the communication protocol.
Think of VPN protocols as different languages your VPN app can use to “talk” to the server. If the firewall is blocking the default language (like OpenVPN UDP), switching to another one (like OpenVPN TCP, WireGuard, or IKEv2) can often sneak the connection through. You can find this setting in your app’s preferences menu.
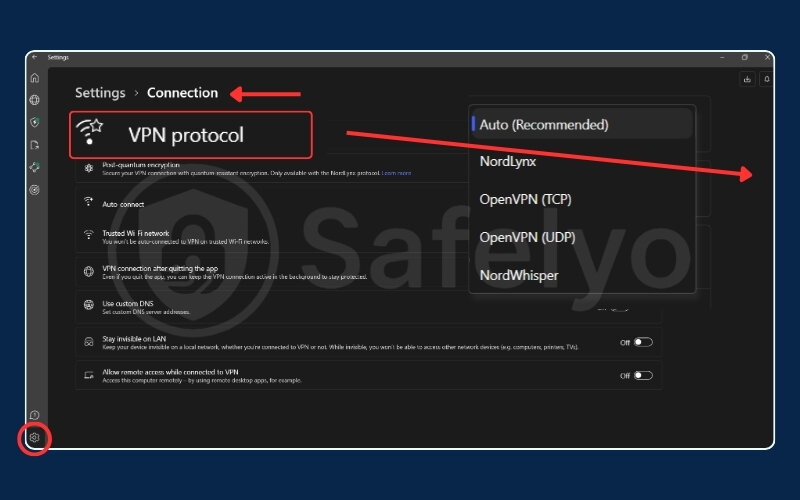
Double-check that stealth mode is active.
Sometimes, an app update or settings change can disable your obfuscation feature. Go back into the settings and make absolutely sure you are trying to connect to a server specifically labeled as “Obfuscated” or “Stealth“. You’d be surprised how often this simple check solves the problem.
Contact customer support.
If you’ve tried the steps above and are still blocked, it’s time to use one of the best resources of a paid VPN: Its support team. Think of them as your on-the-ground intelligence. They have real-time information on which servers and protocols are currently working in your specific region and can often provide you with manual configuration files that are much harder to block.
The best way to solve a problem, however, is to prevent it from happening.
PRE-TRAVEL CHECKLIST FOR GUARANTEED ACCESS
For journalists, activists, or any serious traveler who cannot afford to lose their connection, preparation is everything. This is my essential pre-departure checklist.
| Checklist | Action Item | Why It’s Crucial (Your Failsafe) |
|---|---|---|
| ☐ | Install at least two different VPNs | This is your primary and your backup parachute. If one service is completely blocked, your second one might work. |
| ☐ | Download offline installers | This is your spare key. Save the setup files to a USB drive so you can install the software even if the VPN website is blocked. |
| ☐ | Screenshot manual instructions | This is your emergency map. If the app fails, these instructions let you set up a connection manually through your device’s settings. |
| ☐ | Confirm your subscription is active | Don’t let your access expire at a critical moment. Ensure auto-renewal is enabled if possible. |
| ☐ | Test the obfuscated connection | Practice connecting to a stealth server before you leave. This ensures you know how it works and that your account is ready to go. |
5. FAQ about bypassing censorship with a VPN
Can I use a free VPN to bypass censorship?
It is highly discouraged. Free VPNs almost never offer the advanced features like obfuscated servers that are necessary to defeat modern censorship. Furthermore, they often have cripplingly slow speeds, weak security, and some have even been caught selling user data. For a high-stakes task like bypassing censorship, a reputable, paid VPN is a necessary investment in your safety and success.
What’s the difference between a VPN and Tor for censorship?
Think of it this way: a VPN is like a secure, private car – it’s fast, reliable, and encrypts everything for your entire journey (all your device’s traffic), making it great for everyday use. Tor is like a public bus that takes a very long, winding route through many stops (volunteer-run nodes) to make you anonymous. Tor provides stronger anonymity but is much slower, making it difficult for activities like streaming. A stealth VPN is often the better balance of speed and security for bypassing censorship.
Which VPN protocol is best for bypassing deep packet inspection (DPI)?
There isn’t one single “best” protocol because it’s less about the protocol itself and more about how it’s disguised. Any protocol (like OpenVPN TCP) that is wrapped inside a stealth or obfuscation layer is specifically designed for this purpose. While modern protocols like WireGuard are very fast and secure, they can be easier for firewalls to identify and block if they are not hidden by obfuscation technology.
6. Conclusion
In summary, learning how to bypass censorship with a VPN is a powerful step toward protecting yourself and reclaiming your access to the open world of information. While modern firewalls are sophisticated, the right tools and knowledge can reliably get you through. The key isn’t just having a VPN; it’s about using a smart VPN correctly.
To ensure you stay connected and safe, always remember these key points:
- Stealth is everything: Always choose a VPN that offers obfuscated servers to hide your connection.
- Activate your defenses: Your VPN’s kill switch and DNS leak protection are non-negotiable safety features.
- Prepare before you’re blocked: Install your VPN and download offline files before you travel or anticipate restrictions.
- Test and adapt: If one server or protocol is blocked, switch to another. Don’t be afraid to experiment.
In the ongoing fight against censorship, knowledge, and the right tools are your strongest defense. Always prioritize your personal safety and choose a service you can trust. To find a VPN that meets these critical standards, explore the expert-vetted lists and in-depth reviews in the Privacy & Security Basics section on Safelyo.













