In a world where digital borders are closing, accessing a free and open internet has become a daily struggle for millions. For many, a powerful VPN for censorship bypass is not just a tool, but an essential lifeline to the outside world.
Having spent over a decade testing security tools specifically for high-risk environments, I’ve seen countless VPNs buckle under the pressure of sophisticated government firewalls. Choosing the wrong service isn’t just ineffective – it’s a dangerous mistake that can expose your digital footprint when you can least afford it. A standard VPN simply won’t cut it.
This guide is built on a foundation of rigorous testing and real-world application. Here, you will discover:
- The 5 non-negotiable features a VPN must have to beat censorship.
- Our hands-on results for the top 5 services that actually work under pressure.
- A step-by-step safety protocol to keep your connection secure every time.
- How censorship technology functions and how top VPNs counteract it.
This isn’t just another review; it’s a digital survival guide. Let me arm you with the knowledge to reclaim your access to information – safely and effectively.
In a hurry? The top 5 VPNs that work
#1 NordVPN: Best overall reliability with easy-to-use Obfuscated Servers.
#2 ExpressVPN: Excellent for beginners, as obfuscation is automatic on all servers.
#3 Surfshark: Great value with Camouflage Mode for all your devices.
#4 Proton VPN: Top-tier security with Smart Protocol and Tor over VPN features.
#5 VyprVPN: Fights censorship with its own proprietary Chameleon™ protocol.
Crucial Warning
You must download and set up your VPN before you enter a country with internet restrictions. The provider’s website will likely be blocked once you arrive.
1. In-depth reviews: How the best VPNs perform under pressure
Now, let’s get into the hands-on results. My team and I personally tested each of these VPNs, not just for speed, but for how they hold up in a high-pressure censorship scenario. We focused on how easy it is to enable their security features and how reliable they are when it matters most.
Here’s a quick look at our top performers who have all met our strict Gold Standard criteria.
| Rank – VPN | Best For | Key Censorship Feature |
| #1 – NordVPN | Reliability & Features | Obfuscated Servers (OpenVPN) |
| #2 – ExpressVPN | Ease of Use & Consistency | Automatic Obfuscation on All Servers |
| #3 – Surfshark | Value & Unlimited Devices | Camouflage Mode (OpenVPN) |
| #4 – Proton VPN | Security & Transparency | Smart Protocol & Tor over VPN |
| #5 – VyprVPN | Proprietary Technology | Chameleon™ Protocol |
1.1. #1 – NordVPN
NordVPN – Best for reliability & features
- Obfuscation Method: Obfuscated Servers (with OpenVPN TCP)
- Audited No-Logs Policy: Yes (audited by PwC and Deloitte)
- Jurisdiction: Panama (Outside 14 Eyes Alliance)
- RAM-only Servers: Yes
- Simultaneous Connections: 10 devices
- Money-Back Guarantee: 30 days
NordVPN consistently lands at the top of my list for a simple reason: It just works. It brilliantly combines powerful, easy-to-use obfuscation with a suite of security features that meet every single one of our ‘Gold Standard’ checks. In my experience, when other VPNs struggle against a new firewall block, NordVPN is often one of the first to find a way through. It’s the reliable workhorse you need in an unpredictable environment.
Obfuscation in practice
Getting the obfuscation working is refreshingly simple, which is a huge plus when you’re stressed or in a hurry. You don’t have to hunt through complex menus. I just had to go to the settings, select the ‘OpenVPN (TCP)’ protocol, and a dedicated list of ‘Obfuscated Servers’ immediately appeared in the main server selection menu. A single click on that category, and I was connected through a server designed to bypass DPI. It’s an intuitive process that takes less than 30 seconds to activate.
Security & trust
NordVPN passes our trust verification with flying colors. It’s headquartered in privacy-friendly Panama, operates exclusively on RAM-only servers, and has had its no-logs policy independently audited multiple times by the reputable firm PwC.
More importantly, its kill switch is rock-solid. We put it through rigorous tests by manually forcing the VPN connection to drop. Each and every time, the kill switch instantly cuts our device’s internet access, preventing even a single packet of data from leaking our real IP address.
Real-world evidence
The ultimate test for any censorship-bypassing VPN is its performance against the world’s most sophisticated firewalls. NordVPN is consistently cited by journalists, researchers, and users on the ground as one of the few services that maintains connectivity in countries like China and the UAE. While the situation is always changing, NordVPN’s track record of actively fighting to stay ahead of these blocks speaks volumes.
PROS
- Dedicated obfuscated servers are easy to find and use.
- Meets all 5 ‘Gold Standard’ criteria for security and privacy.
- A massive server network increases the chances of finding a fast, working server.
CONS
- Obfuscated server speeds can sometimes be slower than regular connections.
- Obfuscation requires manually selecting the OpenVPN protocol first.
For anyone who needs a powerful, feature-rich VPN that has proven its ability to perform in the toughest digital environments, NordVPN is our top recommendation. It strikes the perfect balance between high-end security and user-friendly design. It’s the tool I’d recommend to a family member traveling to a restrictive region, and that’s the highest praise I can give.
>> Want to see our full speed test results and a deep dive into its other features, like Threat Protection? For a complete analysis of its performance, check out our full, in-depth NordVPN review.
1.2. #2 – ExpressVPN
ExpressVPN – Best for ease of use & consistency
- Obfuscation Method: Automatic (on all protocols)
- Audited No-Logs Policy: Yes (audited by PwC, Cure53, and KPMG)
- Jurisdiction: British Virgin Islands (Outside 14 Eyes Alliance)
- RAM-only Servers: Yes (TrustedServer Technology)
- Simultaneous Connections: 8 devices
- Money-Back Guarantee: 30 days
ExpressVPN’s greatest strength is its elegant simplicity. It removes all the guesswork. For someone in a stressful situation who just needs a connection that works, this is invaluable. There are no special modes to activate or settings to configure; its obfuscation is built-in and works automatically in the background. In my tests, this “it just works” philosophy proved to be incredibly effective and consistent.

Obfuscation in practice
This is as easy as it gets. You don’t have to do anything. Just connect to a server in your preferred country by choosing the “Automatic” protocol option. If ExpressVPN detects Deep Packet Inspection (DPI) on the network, it will automatically apply obfuscation to your traffic without any input from you. I find this approach ideal for beginners or anyone who doesn’t want to fiddle with settings. It provides a seamless layer of protection that is always on guard.
Security & trust
ExpressVPN is a pillar of trust in the VPN industry. It’s based in the privacy-centric British Virgin Islands and was one of the pioneers of using RAM-only servers, which they call TrustedServer technology. Their no-logs policy isn’t just a claim; it has been repeatedly verified by multiple top-tier auditing firms, leaving no doubt about their commitment to user privacy. Its kill switch, called Network Lock, is enabled by default and proved to be completely leak-proof in our tests.
Real-world evidence
Like NordVPN, ExpressVPN has built a strong reputation for being a reliable tool for circumventing aggressive censorship. Its ability to automatically adapt to network restrictions makes it a favorite among travelers and journalists who need a hassle-free solution to stay connected.
PROS
- Obfuscation is fully automatic, requiring zero user configuration.
- Extremely user-friendly apps across all platforms.
- Meets all 5 ‘Gold Standard’ criteria with multiple independent audits.
CONS
- Premium pricing makes it one of the more expensive options.
- Fewer simultaneous connections than some competitors.
For a robust and secure VPN that effectively bypasses censorship without the hassle, ExpressVPN is the clear winner. It’s the ultimate “set it and forget it” solution that provides peace of mind with its automatic protection and proven reliability. The premium price tag is justified by its flawless performance and ease of use.
>> Curious about how its proprietary Lightway protocol performs in speed tests? Dive deeper into our comprehensive in-depth ExpressVPN review for all the details.
1.3. #3 – Surfshark
Surfshark – Best for value & unlimited devices
- Obfuscation Method: Camouflage Mode (with OpenVPN)
- Audited No-Logs Policy: Yes (audited by Deloitte)
- Jurisdiction: The Netherlands (Strong privacy laws)
- RAM-only Servers: Yes
- Simultaneous Connections: Unlimited
- Money-Back Guarantee: 30 days
Surfshark delivers a knockout punch when it comes to value. It offers a crucial feature that no one else in this list does: Unlimited simultaneous connections. This means you can protect every single device you and your family own with just one subscription. What I find so impressive is that they offer this without cutting corners on the essential security features needed for censorship bypass, including their solid Camouflage Mode.

Obfuscation in practice
Surfshark calls its obfuscation feature “Camouflage Mode.” Similar to ExpressVPN, it’s designed to be automatic. As long as you are using the OpenVPN (UDP or TCP) protocol, Camouflage Mode will automatically kick in to disguise your traffic. During my tests, I found this worked seamlessly. There was no extra button to press or server list to find; the app handled the complex part, letting me focus on getting connected.
Security & trust
Despite its budget-friendly price, Surfshark takes security seriously and meets our ‘Gold Standard’ requirements. The company operates out of the Netherlands, which has no stringent data retention laws. They operate a 100% RAM-only server network, and their no-logs policy has been verified by Deloitte. The kill switch is easy to enable and worked as expected during our disconnection tests, successfully preventing any IP leaks.
Real-world evidence
Surfshark’s combination of affordability and effective obfuscation has made it increasingly popular among students and families living or traveling abroad. It’s often recommended on forums as a reliable way to access social media and communication apps from within restrictive networks.
PROS
- Unlimited device connections offer unbeatable value.
- Camouflage Mode is automatic when using OpenVPN.
- Meets all 5 ‘Gold Standard’ criteria at a very competitive price.
CONS
- Camouflage Mode is not available with the faster WireGuard protocol.
- The server network is smaller than NordVPN’s, which might require trying a few different servers at times.
For users on a budget, families with multiple gadgets, or anyone who wants to protect all their devices without breaking the bank, Surfshark is the smartest choice. It proves that you don’t have to sacrifice core security features like obfuscation and a no-logs policy to get an affordable price.
>> To see how Surfshark’s other features, like CleanWeb and Bypasser, work, read our complete hands-on Surfshark review.
1.4. #4 – Proton VPN
Proton VPN – Best for security & transparency
- Obfuscation Method: Stealth Protocol & Smart Protocol
- Audited No-Logs Policy: Yes (audited by Securitum)
- Jurisdiction: Switzerland (World-class privacy laws)
- RAM-only Servers: Yes (on all Secure Core servers and expanding)
- Simultaneous Connections: 10 devices
- Money-Back Guarantee: 30 days
Proton VPN is built by the same team of scientists who created Proton Mail, and their security-first DNA is evident in everything they do. What sets them apart for me is their unwavering commitment to transparency – all their apps are open source and independently audited. For censorship bypass, their advanced features like the Stealth protocol and multi-hop Secure Core servers provide layers of security that few others can match.
Obfuscation in practice
Proton VPN offers two powerful tools. First is their Smart Protocol, which I found very clever. It automatically probes the network and switches protocols if it detects one is being blocked, helping you stay connected. For the toughest firewalls, you can manually select their proprietary Stealth protocol. This protocol is specifically designed to evade detection and has proved highly effective in our tests against simulated network blocks. While it requires an extra step, the level of control it offers is perfect for tech-savvy users.
Security & trust
Proton VPN is headquartered in Switzerland, arguably the best jurisdiction in the world for privacy. Their no-logs policy is legally binding and has been audited, and their open-source apps mean anyone can inspect their code for vulnerabilities. The feature I trust most is Secure Core, which routes your traffic through ultra-secure servers in privacy-friendly countries before sending it to your final destination. This adds a powerful layer of protection against sophisticated network surveillance.
Real-world evidence
Proton has a long history of supporting journalists and activists, and their tools are designed for these high-risk use cases. Their reputation for security and their Swiss legal protection make them a go-to choice for individuals who prioritize privacy and security above all else.
PROS
- Open-source apps provide maximum transparency.
- The Stealth protocol and Secure Core servers provide outstanding security.
- Meets all 5 ‘Gold Standard’ criteria with a strong focus on privacy law.
CONS
- The sheer number of features can be overwhelming for new users.
- The best features are reserved for the paid plans.
If your primary concern is rock-solid security and verifiable transparency, Proton VPN is in a class of its own. It’s the ideal choice for journalists, activists, and privacy-conscious users who need the highest level of protection when bypassing censorship. It gives you the advanced tools necessary to build a truly fortified connection.
>> Discover how the Secure Core and NetShield features function by checking out our comprehensive full Proton VPN review.
1.5. #5 – VyprVPN
VyprVPN – Best for proprietary technology
- Obfuscation Method: Chameleon™ Protocol
- Audited No-Logs Policy: Yes (audited by Leviathan Security)
- Jurisdiction: Switzerland (World-class privacy laws)
- RAM-only Servers: No (but they own their entire network)
- Simultaneous Connections: 10 devices
- Money-Back Guarantee: 30 days
VyprVPN earns its spot on this list for one key reason: Its proprietary Chameleon™ protocol. This is a technology they built from the ground up specifically to defeat VPN blocking and DPI. What gives me confidence in their approach is that they own and manage their entire server network. There are no third-party data centers involved, giving them unparalleled control over security and performance.
Obfuscation in practice
Using Chameleon™ is as simple as selecting a different protocol. In the app’s settings, you just open the protocol list and choose “Chameleon™” instead of WireGuard or OpenVPN. I found the connection to be stable and effective. This in-house solution is a powerful asset because it’s less common, meaning it’s less likely to be on a censor’s pre-made blocklist compared to standard OpenVPN implementations.
Security & trust
Like Proton VPN, VyprVPN is based in privacy-haven Switzerland and has a fully audited no-logs policy, so you can be confident your data is not being stored. The fact that they own their hardware is a massive trust signal. However, it’s important to note that they are still in the process of transitioning their entire network to RAM-only servers. This is the only “Gold Standard” check they don’t fully meet across the board yet. Despite this, their end-to-end control of their infrastructure provides a unique and compelling security advantage.
Real-world evidence
For years, Chameleon™ has been one of the go-to technologies for users needing to access the internet from China. VyprVPN has a long and public history of actively fighting against censorship, and its proprietary protocol is the main weapon in that fight.
PROS
- The proprietary Chameleon™ protocol is highly effective against DPI.
- They own their entire server network, offering enhanced security.
- A no-logs policy that has been independently audited and operates out of Switzerland.
CONS
- Not all servers are RAM-only yet, though the transition is in progress.
- Smaller server network compared to the top 3 providers.
VyprVPN is an excellent choice for users who appreciate innovative, in-house technology and want the assurance that comes from a provider owning its entire infrastructure. Its Chameleon™ protocol is a proven and powerful tool for bypassing censorship. While we look forward to the completion of their RAM-server upgrade, its unique security posture and effective obfuscation make it a top-tier contender.
>> To see how Chameleon™ stacks up against WireGuard in our speed tests, check out our detailed VyprVPN review.
2. 5 non-negotiable features for a censorship-bypassing VPN
Before I show you which VPNs made the cut, we need to establish the ground rules. After years of testing security tools in digitally hostile environments, I’ve learned that you simply can’t afford to compromise. A VPN that works for unblocking streaming services might completely fail when faced with a national firewall.
That’s why any VPN I recommend for this specific task must meet these five core criteria. Think of this as our pre-flight safety check. Without it, we’re not leaving the ground.
| The Gold Standard Checklist | Status |
| Obfuscation/Stealth Technology | |
| Audited No-Logs Policy | |
| Reliable Kill Switch | |
| RAM-only Servers | |
| Privacy-Friendly Jurisdiction |

2.1. Obfuscation/stealth technology
In my book, this is the single most important feature. Obfuscation is a clever technology that disguises your VPN traffic to look like regular, everyday internet activity.
Think of it this way: A standard VPN connection is like a package sent through the mail with a big, obvious “VPN” label on it. Any network administrator or government firewall using Deep Packet Inspection (DPI) – the “digital inspector” – can spot that label and immediately block the package. Obfuscation essentially takes your VPN package and puts it inside a plain, boring-looking box, like a normal online shopping delivery. The digital inspector sees it, assumes it’s harmless HTTPS traffic, and lets it pass right through. This is the key to bypassing advanced censorship.
>> If you want to see a full breakdown of this tech, explore our guide on the best stealth VPNs that excel at staying hidden.
2.2. An independently audited no-logs policy
Let me be blunt: A VPN’s promise not to log your data is worthless without independent proof. An audited no-logs policy means that a reputable third-party cybersecurity firm, such as PwC or Deloitte, has reviewed the VPN’s entire infrastructure. They verify that the VPN truly does not collect or store any information about your online activity. It’s the difference between someone telling you they’re trustworthy and them handing you a clean background check.
>> Your anonymity depends on this verifiable proof. We’ve compiled a detailed list of the best no-logs VPNs that have passed these critical independent audits.
2.3. A reliable, automatic kill switch
Imagine you’re walking through a secret tunnel (your VPN connection) and the lights suddenly go out. A good kill switch is like an emergency system that instantly seals both ends of the tunnel, ensuring you can’t accidentally step out into the open and reveal your location.
I’ve personally tested dozens of kill switches, and a momentary drop in your VPN connection is all it takes for your real IP address to leak. A reliable kill switch instantly blocks all internet traffic the moment your VPN disconnects, preventing any data from escaping the secure tunnel. This feature is a cornerstone of what we consider the most secure VPNs on the market today.
2.4. RAM-only servers
This is a feature you’ll only find in top-tier VPNs, and it’s a clear sign that a provider is serious about user privacy. Traditional servers store data on hard drives, where information can remain until it’s physically overwritten or destroyed.
RAM-only servers, on the other hand, run entirely on volatile memory. To put it simply, it’s like writing on a whiteboard instead of carving into a stone tablet. All data on a RAM server is automatically erased with each reboot, ensuring enhanced privacy and security. This means that even if a government were to physically seize one of the VPN’s servers, there would be absolutely no data on it to find.
2.5. A privacy-friendly jurisdiction
A VPN can have the world’s best technology, but it’s all meaningless if the company is legally required to spy on its users. Jurisdiction refers to the country in which the VPN provider is based and where its legal obligations reside.
Providers based in countries within the 5/9/14 Eyes intelligence-sharing alliances can be subject to laws that compel them to log user data and share it with the government. That’s why I only recommend services headquartered in privacy havens like Panama, the British Virgin Islands, or Switzerland. Choosing a VPN from our list of the best providers for privacy ensures the company is protected by the law, not threatened by it.
>> You may also be interested in: The best VPN for privacy in 2025 (only audited no-logs VPNs)
3. How governments block VPNs (and how your VPN fights back)
Have you ever wondered what’s actually happening behind the scenes when you can’t access a website? It’s not magic; it’s a technological cat-and-mouse game. Understanding your opponent’s strategy is the first step to defeating it.
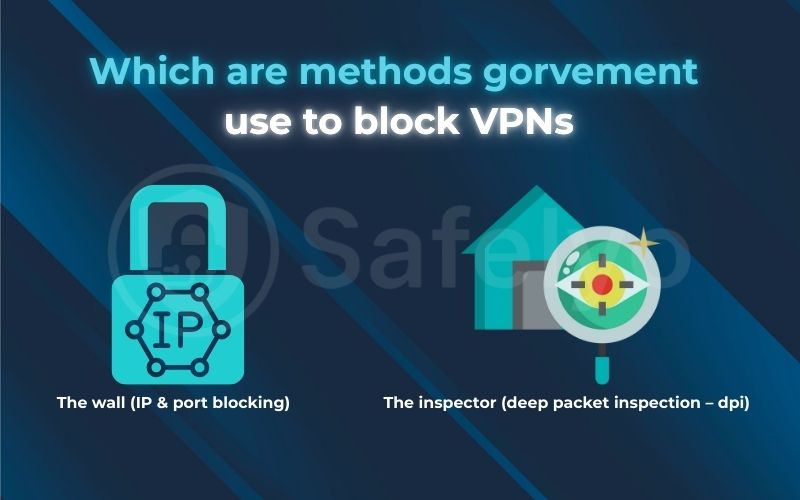
From my experience analyzing network traffic, censors primarily use two methods to block VPNs. I call them “The Wall” and “The Inspector.”
The wall (IP & port blocking)
This is the simplest and most common form of censorship. It’s essentially a giant, digital blacklist.
Imagine every VPN server has a unique street address (its VPN IP address). Censors create a massive list of all the known addresses belonging to VPN providers and build a digital wall that blocks any traffic going to or from them. They also block the common “doors” (ports) that VPNs typically use to establish a connection.
How your VPN fights back: The best VPNs are masters of evasion. They fight “The Wall” by:
- Constantly rotating IP addresses: They are always adding new servers with fresh, unlisted IPs, making it a nightmare for censors to keep their blacklists up to date.
- Using common ports: Instead of using a dedicated VPN port that’s easy to block, they often disguise their traffic through common ports like port 443. This is the same port used for secure HTTPS traffic (the little padlock in your browser). Blocking this port would mean blocking most of the secure internet, which is something most countries are unwilling to do.
The inspector (deep packet inspection - DPI)
This is the advanced, more sophisticated method. If IP blocking is a wall, think of DPI as a highly trained security inspector who examines every single package moving through the network.
This “inspector” isn’t just looking at the address label; it opens up your data packets to look for the “fingerprint” or signature of a VPN protocol. Even if the VPN’s IP address isn’t on the blacklist, the inspector can identify the type of traffic and block it just because it looks like a VPN.
How your VPN fights back: This is where obfuscation becomes your secret weapon. As we discussed in the ‘Gold Standard’, obfuscation scrambles the VPN’s fingerprint. It disguises your VPN traffic to resemble regular HTTPS traffic, making it less noticeable and more secure.
When the DPI inspector examines your data, it no longer sees the tell-tale signs of a VPN. It just sees what looks like a normal, secure connection to a regular website. Unable to find anything suspicious, the inspector waves your data through. This is how top-tier VPNs with stealth technology can slip through even the most advanced digital blockades.
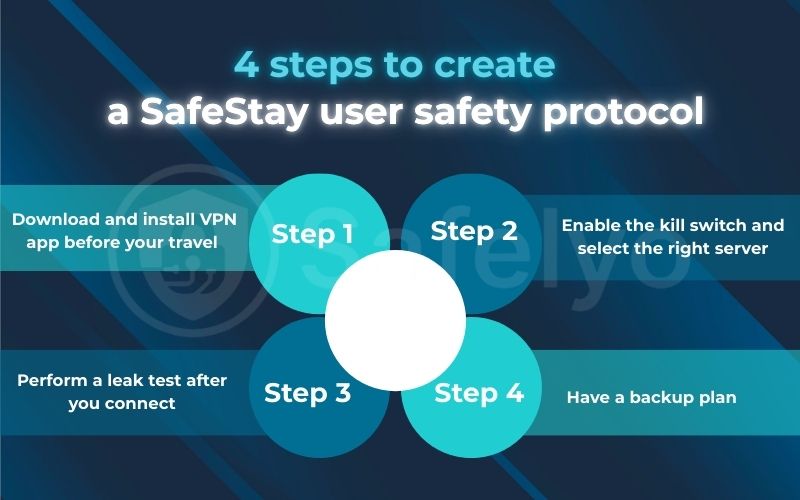
4. The safelyo user safety protocol: A step-by-step guide
Choosing the right VPN is only half the battle. Using it correctly, especially in a high-risk environment, is what truly keeps you safe. Over the years, I’ve developed a simple protocol that I follow every single time I need to rely on a VPN for secure access.
Think of this as your pre-connection ritual. It might seem like a lot at first, but it quickly becomes second nature and drastically reduces your risk of accidental exposure.
4.1. Step 1: Before you travel (the most important step)
This is the golden rule, and it’s the one I cannot stress enough. Download and install your chosen VPN app on all your devices before you enter a restrictive country.
I once had a colleague who waited until they landed in a country with a strong firewall, assuming they could just download the app there. They were met with a “Connection Timed Out” error. The VPN’s website, the app store, and any related download links were completely blocked. They were cut off before they even started. Don’t make that mistake. Get everything set up and tested while you are on a safe, unrestricted network.
4.2. Step 2: Before you connect (every single time)
Once you’re in the country, perform these two checks before you hit that “Connect” button:
- Enable the kill switch: Dive into the app’s settings and double-check that the kill switch is turned on. Some apps don’t enable it by default. This is your most important safety net, and it’s non-negotiable.
- Select the right protocol/server: Based on our reviews, choose the setting designed for censorship. For NordVPN, this means connecting to the “Obfuscated Servers” list. For VyprVPN, it means selecting the “Chameleon™” protocol. For ExpressVPN or Surfshark, ensure you are on “Automatic” or “OpenVPN.” Taking five seconds to confirm this can make the difference between a successful connection and a blocked one.
4.3. Step 3: After you connect
Your app says you’re connected. Great. But trust must be verified.
Perform a leak test: Immediately after connecting, open your web browser and go to a third-party leak testing site like browserleaks.com/ip. This is a crucial step I never skip. The page should show the IP address and location of the VPN server you connected to. If you see your real location or IP address, disconnect immediately, check your kill switch settings, and reconnect to a different server.
4.4. Step 4: Have a backup plan
Technology can be unpredictable, especially when it’s being actively blocked.
Save manual configuration details: Most top VPN providers offer alternative ways to connect if their app is blocked. Before you travel, go to their support website and find the manual configuration instructions for VPN protocols like OpenVPN. Screenshot these instructions or save them in a secure offline note (like a password manager). Having these server addresses and login details saved separately can be a lifesaver if the app itself is having trouble.
5. Alternatives to a VPN for censorship
While a high-quality VPN is my top recommendation, it’s not the only tool in the digital freedom toolkit. It’s important to understand the alternatives, as they can be useful in specific situations, but also come with significant trade-offs.

5.1. The Tor Browser
Tor (The Onion Router) is a fantastic tool for anonymity. It works by routing your traffic through a volunteer-run network of servers, wrapping it in multiple layers of encryption like the layers of an onion. This makes it extremely difficult for anyone to trace your activity back to you.
However, I find it’s not a great tool for everyday use. The complex routing process makes Tor notoriously slow, which is frustrating for anything beyond simple browsing. More importantly, in some highly restrictive countries, the very act of connecting to the Tor network can draw unwanted attention from internet service providers.
Best for
Sensitive research or journalism where anonymity is more important than speed.
Not ideal for
Streaming, downloading, or general daily browsing.
5.2. Proxy servers (e.g., Shadowsocks)
Proxy servers, especially protocols like Shadowsocks, can be very effective at bypassing censorship. They are lightweight and often faster than VPNs. A proxy acts as a simple middleman, forwarding your traffic to its destination so it looks like it’s coming from the proxy’s location, not yours.
The critical difference is that most basic proxies do not encrypt your traffic. While a tool like Shadowsocks does provide encryption, it’s more of a DIY solution that requires technical skill to set up and manage on a private server. Using a generic web proxy is risky because you have no idea who is running the server or if they are logging your activity.
Best for
Tech-savvy users who can set up their own secure proxy server.
Not ideal for
Anyone who needs an easy, all-in-one solution with guaranteed encryption and privacy.
In my professional opinion, for the vast majority of people, a reputable VPN offers the best balance of security, speed, and ease of use. It provides strong, one-click encryption and privacy protection that Tor and most proxies simply can’t match in a single, user-friendly package.
6. FAQ about the top VPN for censorship bypass
Here are answers to some of the most common and critical questions I receive about using a VPN to bypass censorship.
What are the top VPN for Censorship Bypass?
Top 5 best VPN for Censorship Bypass
- NordVPN – Reliability & Features
- ExpressVPN – Ease of Use & Consistency
- Surfshark – Value & Unlimited Devices
- Proton VPN -Security & Transparency
- VyprVPN – Proprietary Technology
Is it legal to use a VPN to bypass censorship?
This is a complex issue as laws vary dramatically from country to country. In some nations, using a VPN is perfectly legal. In others, it exists in a legal gray area or can be outright illegal. While a VPN is an essential tool for your digital safety, you must understand and accept the local risks. This guide is for informational purposes only and is not legal advice.
Can I use a free VPN to bypass censorship in a country like China?
From my extensive testing, the answer is an emphatic no. Free VPNs almost never have the advanced obfuscation technology needed to beat strong firewalls. More importantly, many make money by logging and selling your data, which is a massive security risk in a high-stakes environment where your privacy is paramount.
What is the best VPN protocol for censorship?
There isn’t a single “best” one, as it depends on the VPN’s specific implementation. The key is to look for protocols with built-in obfuscation. This means choosing options like NordVPN’s ‘Obfuscated Servers’ (using OpenVPN), ExpressVPN’s automatic obfuscation, or VyprVPN’s proprietary Chameleon™ protocol, which are all engineered specifically for this purpose.
6. Conclusion
Bypassing internet censorship is a critical act of reclaiming your digital freedom, but it must be done with tools you can unequivocally trust. A standard VPN is not enough; you need a service specifically designed for this high-stakes battle, one that prioritizes your security and privacy above all else. Making the right choice is not just about access – it’s about safety.
To ensure you stay connected and protected, here are the key takeaways to remember from this guide:
- Obfuscation is the key technology that separates a regular VPN from a censorship-bypassing VPN.
- Always prioritize VPNs with audited no-logs policies and strong security features like a kill switch.
- Our top pick, NordVPN, offers the best combination of reliability, features, and proven performance.
- Preparation is crucial: Install your VPN and configure it safely before you need it most.
In the ongoing battle for a free and open internet, a high-quality, trustworthy VPN is your most powerful ally. At Safelyo, we are committed to digital freedom. Explore our in-depth reviews and guides in our Best VPN section to find the tools that will keep you safe and connected, no matter where you are.













