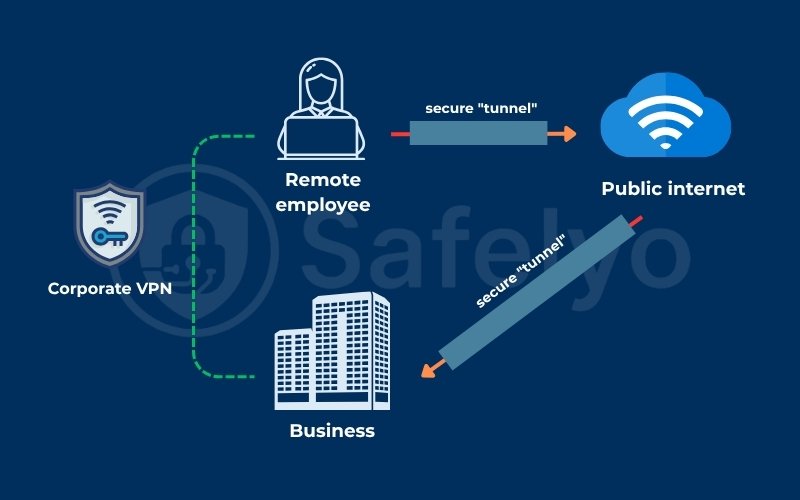
A corporate VPN (Virtual Private Network) is a secure, private network built over the public internet. It allows employees to access a company’s internal data and resources safely from any location.
In today’s business landscape, remote work and distributed teams are the norm. This means remote employees frequently access sensitive company data (or proprietary data) from public Wi-Fi in cafes, airports, and hotels, creating a significant cybersecurity risk.
Understanding “what is a corporate VPN” becomes the first and most critical step in protecting your business data from snooping or being intercepted on these insecure networks.
Key takeaways:
- A corporate VPN creates an encrypted tunnel that protects all business data from hackers, snooping, and on-path attacks.
- It is the standard technology for providing secure remote access to employees.
- It differs from consumer VPNs by focusing on company-controlled access control, user authentication, and network security rather than individual anonymity.
- It is a foundational tool for preventing data breaches and securing connections between office locations.
1. What is a corporate VPN?
At its core, a corporate VPN extends your private company network (the internal network) over the public internet.
You can think of it as a private, encrypted tunnel. When an employee connects to the VPN, all their internet traffic is routed through this secure tunnel directly to the company’s network. This process makes the user’s laptop or mobile device act as if it were physically plugged into the office internal network.
The primary role of a business VPN is twofold: network access control and data confidentiality. While consumer VPNs often focus on hiding a user’s location, a corporate VPN serves a different purpose. Its main functions are:
- Verifying identity: Proving who is trying to connect (authentication).
- Granting access: Deciding what that person is allowed to see and do on the company’s private network.
This leads to the most crucial distinction between corporate and consumer VPNs.
- Consumer VPNs: These services (like NordVPN or ExpressVPN) connect you to a server owned by the VPN provider. The goal is personal privacy, such as hiding your internet activity from your ISP (Internet Service Provider) or bypassing geo-restrictions.
- A corporate VPN: This solution connects you to a “gateway” server owned and managed by your own company. If you’re asking “what is a business VPN?”, the term means the same thing. The goal is to securely access internal company resources like file servers, databases, and intranets from the outside.
2. How corporate VPNs protect business data
Corporate VPNs rely on three core pillars to protect your company’s information. These are secure tunneling, strong traffic encryption, and strict user authentication. Together, they create a private and defended channel for your business data as it travels over the public internet.
A VPN creates a secure “tunnel” for your data. Before any information leaves an employee’s device, the VPN wraps it in an outer layer of encrypted packets. This secure packet travels across the public internet to the company’s VPN gateway. Only at the gateway is the outer packet unwrapped and the data decrypted.
This process effectively shields the data from any eavesdroppers, preventing man-in-the-middle attacks.
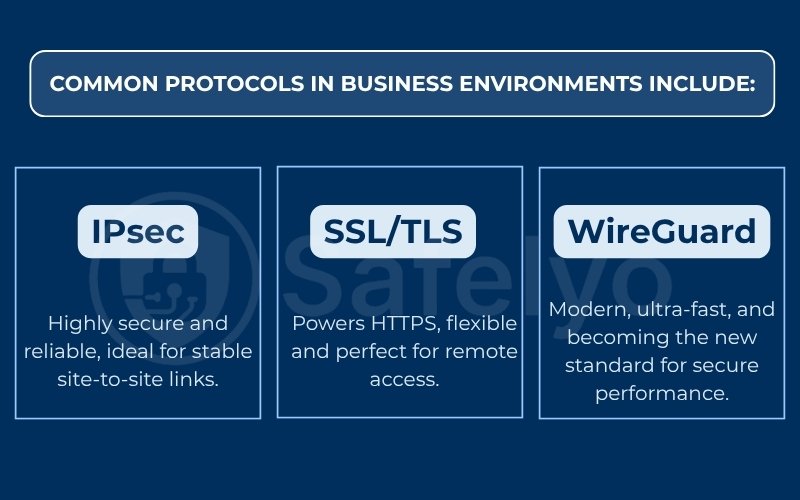
These tunnels are secured using encryption protocols, which are the rules for scrambling and unscrambling the data. Common protocols in business environments include:
- IPsec (Internet Protocol Security): A highly secure and common protocol, often used for stable site-to-site connections.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): This is the same flexible technology that secures ‘HTTPS’ websites, making it ideal for remote access.
- WireGuard: A modern, extremely fast, and streamlined protocol that is becoming a new standard for performance and security.
Finally, strong encryption works together with authentication.
An employee must first prove their identity to the network. This identity check happens before a secure tunnel is even established. The user provides credentials, such as a username, password, and often a two-factor authentication (2FA) code.
These credentials are verified by the “VPN gateway,” the server that acts as the secure doorway to the network. If the identity is not verified, the gateway will not allow the connection, stopping unauthorized access.
This entire process is a foundational part of a cybersecurity strategy.
3. Benefits of using a corporate VPN
Beyond the technical security, implementing a corporate VPN translates into several critical operational benefits. These advantages support a modern, flexible workforce and form a key part of your data protection strategy.
3.1. Securing remote workers and protecting sensitive data
This is the primary and most urgent benefit. In a hybrid work model, employees regularly use insecure networks. These include public Wi-Fi at cafes, hotels, and airports.
Imagine a sales manager connects to hotel Wi-Fi to access the company’s CRM system. Without a VPN, a hacker on the same network could easily intercept their login credentials. Now, the attacker has full access to your customer database. This scenario is a realistic and common attack vector, one that VPNs are specifically designed to prevent.
According to IBM’s “Cost of a Data Breach Report 2025,” having a remote workforce was a factor that increased the average cost of a data breach by USD 131,212.
A corporate VPN neutralizes these security risks. It allows employees to access confidential files and internal software just as if they were in the office. They can do this without risking a data leak.
This encrypted connection is also essential for regulatory compliance. Many industries must follow strict data protection laws like HIPAA (for healthcare), GDPR (for EU citizen data), or PCI-DSS (for credit card data). For these industries, a VPN is more than just a best practice. It is a mandatory component of a compliant security architecture because it protects sensitive data while in transit.
3.2. Reliable connections between branch offices and cloud services
VPNs are not just for individual users. A Site-to-Site VPN can create a permanent, secure link between two different office locations, such as a headquarters and a branch office.
This allows both sites to share servers and internal data as if they were one single, secure network. This same principle extends to the cloud. A VPN can create a secure, private connection from your office directly to your resources hosted in a private or public cloud, protecting that traffic.
4. Types of corporate VPNs
Not all corporate VPNs are structured the same. The best solution depends on who needs access and what they are connecting to. The types generally fall into these categories.
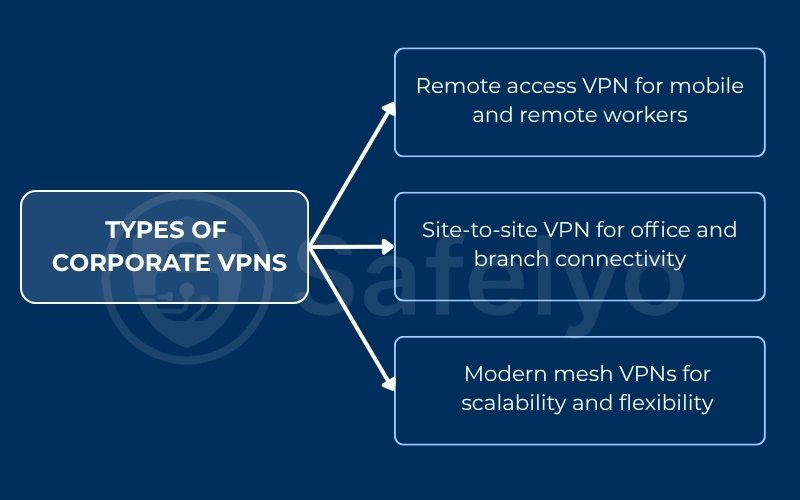
4.1. Remote access VPN for mobile and remote workers
This is a “client-to-site” connection and the most common type for supporting individual employees.
A user (on a laptop or phone) installs a software client, often called a “VPN client“. They use this software to initiate a secure, encrypted tunnel to the central company network. This allows them to work from anywhere as if they were in the office.
4.2. Site-to-site VPN for office and branch connectivity
This is a “network-to-network” connection. It functions as an “always-on” secure link that is managed by network hardware, such as routers or firewalls, at each location.
It is designed to connect an entire office network (like a branch) to another (like headquarters). Employees at the branch office do not have to install any software or manually connect. They are already on the secure, shared network by default.
4.3. Modern mesh VPNs for scalability and flexibility
Newer technologies are evolving how VPNs work, and these solutions are sometimes part of a Zero Trust Network Access (ZTNA) model.
Traditional VPNs funnel all traffic to one central point. This process can be slow. “Mesh” solutions work differently.
They create more direct, secure connections by linking users directly to the specific applications they need. This approach is often faster, more secure, and scales better for modern, cloud-based companies.
5. Why does your business need a corporate VPN?
A corporate VPN is no longer just an optional IT upgrade. It has become a foundational component for modern business security and continuity
The simple answer is to protect your two most valuable assets: your data and your people.
- It secures your data in transit, preventing breaches, stopping eavesdroppers, and helping you meet critical compliance regulations like GDPR and HIPAA.
- It empowers your people by giving remote employees a secure, encrypted connection to access internal resources from any location, neutralizing the risks of public Wi-Fi.
As I explained in detail in “Benefits of using a corporate VPN” section, these functions are the primary drivers for adoption. They are essential for enabling a secure, productive, and flexible modern workforce.
6. Choosing the right corporate VPN solution
When you start evaluating vendors for a business VPN, it is easy to get lost in technical jargon. To find the right solution, businesses should focus the decision on a few key factors.
First, consider the most important factors for your daily operations:
- Security: Does the solution support strong, modern protocols (like WireGuard or OpenVPN)? Critically, does it support Multi-Factor Authentication (MFA) to prevent credential theft?
- Speed: A slow VPN kills productivity. Look for solutions known for high-performance servers and efficient protocols that will not frustrate your employees.
- Scalability: How easy is it to add new users or new office sites? You need a solution that can grow with your business.
- Compatibility: Does the vendor provide easy-to-use client apps for all the devices your team uses (Windows, macOS, iOS, Android)?
Next, understand that a VPN is just one layer of security. The best solutions integrate with other tools. Does it work with your existing firewall? Does the vendor offer a “suite” (sometimes called SASE) that bundles the VPN with endpoint protection (antivirus) and web filtering?
Finally, evaluate the vendor’s reputation and support. For a business-critical tool, you need 24/7 business-class support, not just a consumer helpdesk. Look for vendors with a proven track record of reliability and uptime.
7. Challenges and limitations of corporate VPNs
While a corporate VPN is essential, it is not a silver bullet for cybersecurity. It is crucial to understand its challenges and limitations.
Challenges (Implementation & use)
- Performance bottlenecks: Traditional VPNs route all traffic through a central gateway. This can create significant latency penalties, slowing down access to cloud apps.
- High overheads and complexity: Setting up, configuring, and managing VPN access for hundreds of users requires significant management time from IT management staff. Furthermore, traditional hardware-based solutions often have high mounting costs and require dedicated maintenance.
- Modern infrastructure challenges: VPNs were not designed for the modern hybrid cloud. Forcing all cloud traffic back through a central data center creates cloud complexities, bottlenecks, and performance issues.
- User experience issues: If the VPN client is slow or hard to use, employees may be tempted to work around it. This creates a new security risk (shadow IT).
Limitations (Security gaps)
- No malware protection: A VPN encrypts traffic, but it does not scan for or block viruses, malware, or phishing links. It will securely deliver a virus right to your network.
- “All-or-nothing” access: Once authenticated, a user often gets broad access to the entire internal network. This is a classic weakness of the outdated perimeter security model. If credentials are stolen, an attacker has free rein.
- Doesn’t stop phishing: A VPN cannot prevent an employee from clicking a malicious link in an email and giving away their credentials.
8. FAQs about What is a Corporate VPN
To round out our understanding, here are quick answers to some of the most frequently asked questions about business VPNs.
Is a corporate VPN necessary for all businesses?
If your business has any employees who work remotely, travel, or access company data from personal devices, a corporate VPN is a non-negotiable, foundational security tool.
Can a corporate VPN protect against all cyber threats?
No. A VPN’s primary job is to secure your internet connection and access. It does not protect against malware, viruses, or phishing attacks. You must use it alongside strong antivirus software and employee security training.
How does a corporate VPN differ from a proxy server?
A proxy server typically only routes traffic from a single application (like your web browser) and may not offer encryption. A VPN secures and encrypts all internet traffic from your entire device (all apps, all services) at the operating system level, making it far more secure.
What devices and operating systems support corporate VPNs?
All major business platforms are supported. This includes Windows, macOS, and Linux for computers, as well as iOS and Android for mobile devices. Any reputable VPN solution will provide client apps for all of them.
Can employees use personal devices with corporate VPNs securely?
Yes, this is a core function and part of a “Bring Your Own Device” (BYOD) strategy. The VPN client creates a secure, encrypted container for business web traffic and data, isolating it from the employee’s personal activity on their device.
9. Conclusion
Understanding “what is a corporate VPN” makes it clear that this technology is no longer an optional IT upgrade but a core component of modern business security and continuity.
To summarize, here are the main takeaways:
- A corporate VPN is the essential tool for securing remote work, protecting company data from data breaches on insecure networks.
- It verifies user identity and encrypts all traffic between the employee and the company network.
- Key types include Remote Access (for individuals) and Site-to-Site (for offices).
- A VPN is not a complete solution; it must be part of a layered cybersecurity strategy that includes antivirus, firewalls, and user training.
Ultimately, implementing a corporate VPN is the single most effective preventative step to close the high-risk vulnerability created by an unprotected remote workforce.
For more guides like this, explore the VPN Guides section on Safelyo.