In today’s increasingly distributed workforce, ensuring secure and reliable remote access for employees isn’t just a convenience – it’s a critical business necessity. As the number of remote users grows, so does the challenge of maintaining a secure and manageable network perimeter. This is where the VPN concentrator steps in.
Are you exploring what is a VPN concentrator and how it fits into the complex puzzle of network security? This powerful piece of technology acts as a central command post, expertly managing and securing potentially thousands of simultaneous VPN connections for organizations. It’s a cornerstone for robust remote access.
With years spent navigating the intricacies of network security solutions, I’ve seen firsthand how vital a centralized VPN management system becomes as businesses scale. Overlooking this can lead to a tangled web of individual connections, security gaps, and administrative headaches. A VPN concentrator isn’t just for massive corporations; it’s a strategic asset for any organization serious about secure remote operations.
In this comprehensive guide, you’ll discover:
- A clear definition of a VPN concentrator and its core purpose.
- This device expertly handles numerous secure connections.
- The key benefits it offers from enhanced security to simplified management.
- Important considerations to determine if it’s the right fit for your organization.
Don’t let the complexities of remote access security overwhelm you. Let me guide you through the essentials of VPN concentrators, helping you understand how this technology can fortify your network infrastructure!
1. What is a VPN concentrator?
So, what exactly is this device we’re talking about? At its heart, a VPN concentrator is a specialized piece of hardware or, increasingly, a software-based solution (virtual appliance) designed to handle a large number of Virtual Private Network (VPN) tunnels simultaneously. Think of it as a high-capacity, dedicated gateway built specifically for terminating and managing many secure connections from remote users or sites back to an organization’s private network.
1.1. What does a VPN concentrator do?
Its primary role is to act as a centralized endpoint for numerous VPN connections. While most people are familiar with VPNs for individual use, like securing your connection on public Wi-Fi or accessing geo-restricted content, a VPN concentrator operates on a much larger, organizational scale. You wouldn’t typically find one in a home setup.
The main purpose of a VPN concentrator is to provide secure, encrypted, and centrally managed remote access for many users (employees, contractors, partners) to a company’s internal resources. It ensures that all these remote connections are authenticated, authorized, and that their data is protected as it travels over the public internet. It’s like having a single, heavily guarded checkpoint for all remote traffic trying to enter your corporate network, rather than managing hundreds of individual, less secure entry points.
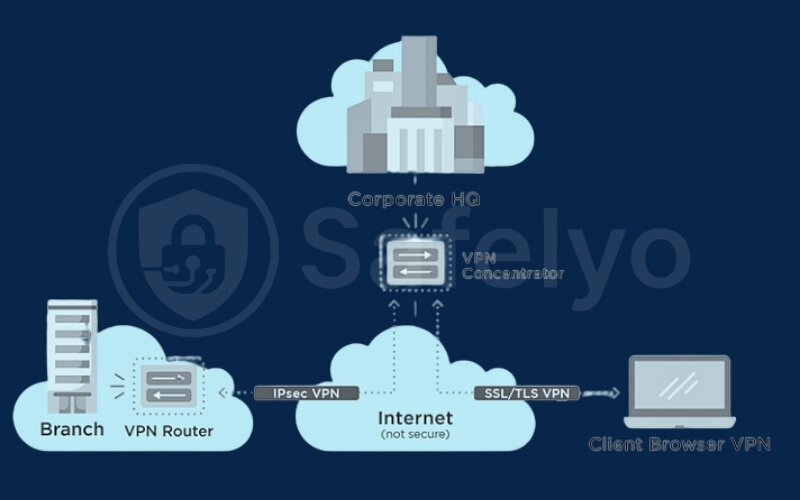
As someone who has helped organizations transition from ad-hoc remote access methods to more structured solutions, I’ve seen the significant improvement a VPN concentrator brings. When your remote workforce grows beyond a handful of users, trying to manage individual VPN accounts or less robust solutions becomes a logistical nightmare and a security risk. A concentrator simplifies this by creating one strong, manageable point of entry.
1.2. Types of VPN concentrators
It’s useful to know that VPN concentrators generally come in two main flavors:
Hardware-based VPN concentrators
These are dedicated physical appliances, often rack-mounted devices, built with specialized processors and interfaces optimized for VPN traffic. They are typically chosen for high performance and reliability in demanding enterprise environments. Cisco, Palo Alto Networks, and Fortinet are well-known names that produce such hardware.
Software-based (or virtual) VPN concentrators
These solutions run as software on standard server hardware or as virtual machines in a cloud environment. They offer more flexibility and can be easier to scale up or down, often integrating well with existing virtualized infrastructure. Many modern enterprise VPN solutions offer software-based options.
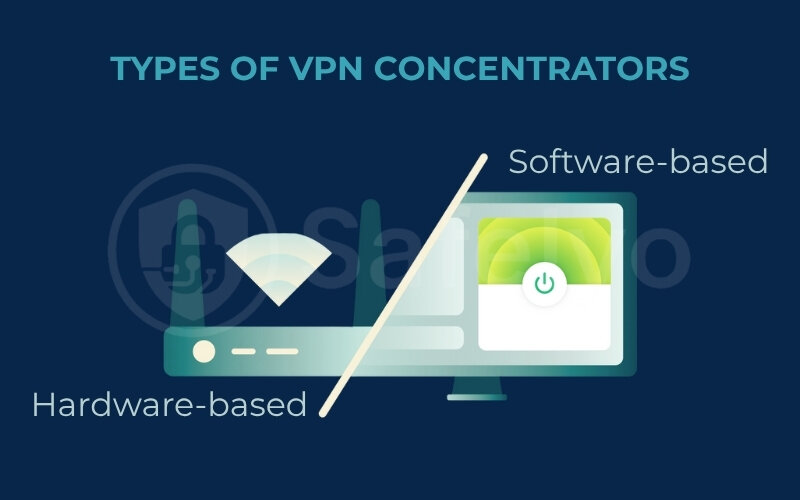
The choice between hardware and software often depends on an organization’s specific needs, existing infrastructure, budget, and scalability requirements.
2. How does a VPN concentrator work its magic?
So, how does a VPN concentrator actually manage to create all these secure connections and keep everything organized? It’s a sophisticated process. In a nutshell, the workflow typically looks like this:
A remote user requests a connection > The concentrator authenticates the user > A secure, encrypted tunnel is established for data transfer.
Now, let’s break down these steps in more detail. Imagine an employee, let’s call her Sarah, working remotely and needing to access files on her company’s internal server. Here’s a simplified look at what happens when Sarah connects via a VPN concentrator:
2.1. Step 1: Connection Initiation
Sarah, using VPN client software on her laptop, initiates a connection request. This request is sent over the Internet to the company’s VPN concentrator. Think of this as Sarah dialing the main security desk of her office building.
2.2. Step 2: Authentication
This is a critical step. The VPN concentrator needs to verify Sarah’s identity before granting any access. This isn’t just a simple password check; it can involve multiple layers:
- User credentials: Her username and password.
- Digital certificates: A unique digital file on her laptop that proves her device is authorized.
- Multi-Factor Authentication (MFA): She might need to enter a one-time code from an authenticator app on her phone or use a hardware token.
The concentrator checks these credentials against its configured user database or an external authentication server (like RADIUS or LDAP).
- If everything matches, Sarah is authenticated.
- If not, access is denied.
From my experience, robust authentication is non-negotiable; it’s the first line of defense.
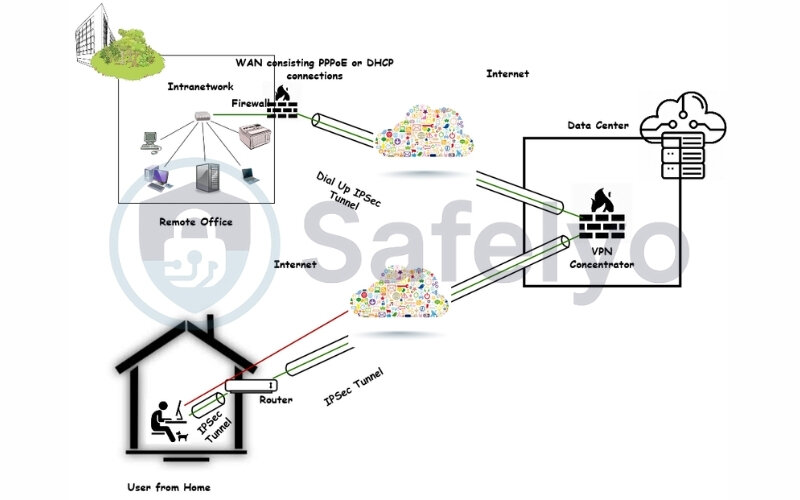
2.3. Step 3: Tunnel Establishment
Once Sarah is authenticated, the VPN concentrator and her VPN client software work together to create a secure, encrypted “tunnel” between her laptop and the concentrator. This tunnel acts like a private, sealed pipe through the public internet. All data passing through this tunnel will be unreadable to anyone trying to intercept it.
2.4. Step 4: Encryption and Decryption
As Sarah accesses files or uses internal applications, all data sent from her laptop is encrypted by her VPN client before it enters the tunnel. When this encrypted data reaches the VPN concentrator, the concentrator decrypts it so it can be forwarded to the correct internal server.
Similarly, data coming from the internal network back to Sarah is encrypted by the concentrator before being sent through the tunnel, and her VPN client decrypts it upon arrival. This end-to-end encryption is what keeps the data confidential.
2.5. Step 5: IP Address Assignment & Session Management
The VPN concentrator typically assigns Sarah’s laptop a temporary IP address from a pool reserved for VPN users. This IP address VPN makes her appear as if she’s part of the internal corporate network. The concentrator also manages her connection session, keeping track of its status, duration, and the resources she’s accessing (based on pre-defined policies). It’s doing this not just for Sarah, but potentially for hundreds or thousands of other users simultaneously, ensuring each session is isolated and secure.
2.6. Step 6: Tunnel Termination
The VPN concentrator is the endpoint where all these individual VPN tunnels from remote clients terminate. Once data is decrypted at the concentrator, it’s then routed to the appropriate destination within the corporate network. When Sarah disconnects, the tunnel is securely torn down.
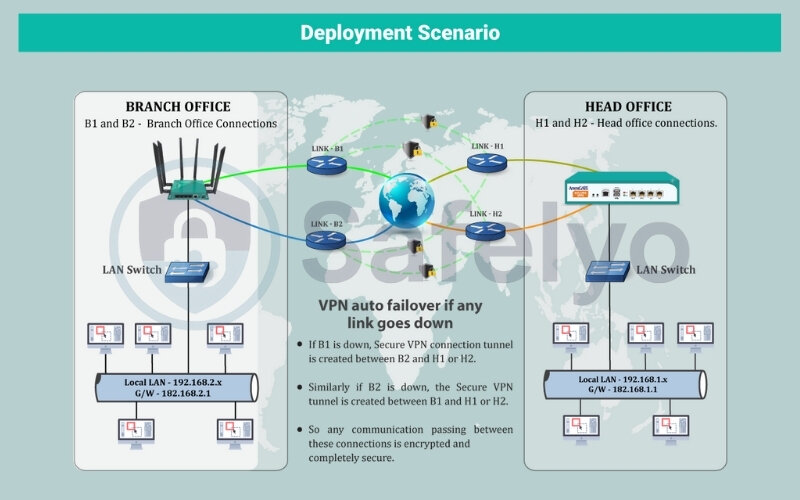
Imagine a busy international airport’s customs and immigration hall. The VPN concentrator is like that hall: Every traveler (remote user) must present valid credentials (authentication). Once verified, they are guided through a secure, private pathway (the VPN tunnel) to their destination within the country (the corporate network). The concentrator manages all these pathways, ensuring only authorized individuals get through and that their passage is secure.
This entire process, from authentication to data transfer, happens seamlessly in the background, allowing users like Sarah to work remotely as if they were physically in the office, but with a robust layer of security.
3. Understanding VPN concentrator encryption protocols and network placement
Two critical aspects that determine the security and effectiveness of a VPN concentrator are the encryption protocols it uses and where it’s strategically placed within the network. Let’s demystify these.
3.1. VPN concentrator encryption protocols
First, let’s talk about encryption protocols (often a key part of what people mean by VPN concentrator encryption protocols). These are the sets of rules and algorithms that scramble your data, making it unreadable to anyone without the decryption key. VPN concentrators typically support several robust protocols:
IPsec (Internet Protocol Security)
This is a very common and highly secure protocol suite. IPsec operates at the network layer (Layer 3 of the OSI model), meaning it can secure all IP traffic passing through it, regardless of the application. It’s widely used for both remote access VPNs (client-to-site) and site-to-site VPNs.
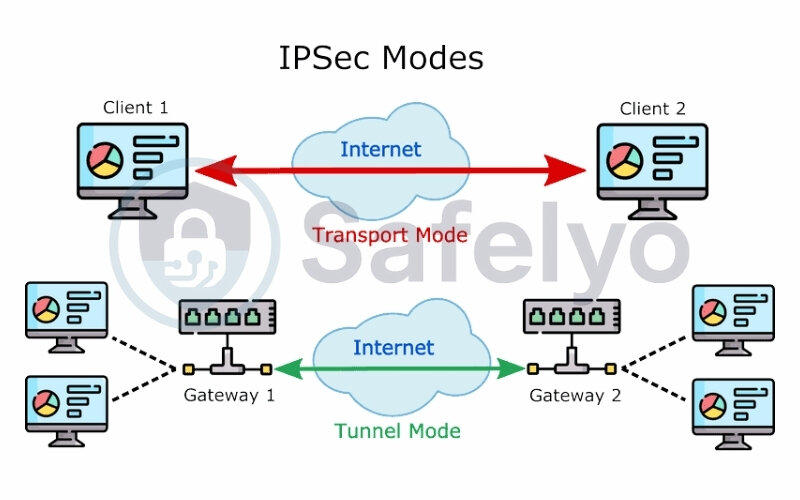
It often involves a combination of protocols like IKE (Internet Key Exchange) for setting up the secure connection and ESP (Encapsulating Security Payload) for encrypting the actual data.
SSL/TLS (Secure Sockets Layer/Transport Layer Security)
You’re probably already familiar with SSL/TLS, as it’s the VPN protocol that secures your web browsing (HTTPS). VPNs can also leverage SSL/TLS, often for clientless web-based VPN access (where users access resources through a web portal) or for some client-based VPNs. SSL/TLS operates at higher layers (Application/Transport) and can be very flexible, often easily traversing firewalls since HTTPS traffic is rarely blocked.
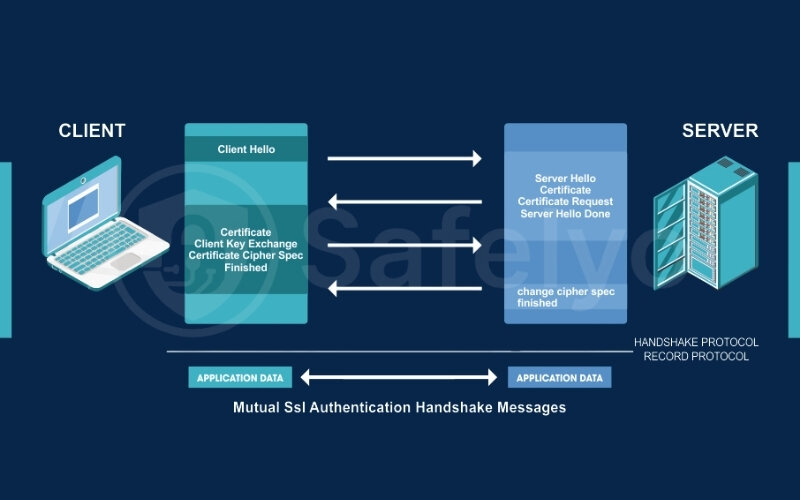
While there are older protocols like PPTP (Point-to-Point Tunneling Protocol) and L2TP (Layer 2 Tunneling Protocol – often paired with IPsec as L2TP/IPsec), PPTP is now considered insecure and should be avoided. L2TP/IPsec is more secure than PPTP, but generally, pure IPsec or SSL/TLS-based VPNs are preferred for modern security needs.
From my experience, organizations usually lean towards IPsec for its robustness or SSL/TLS for its flexibility and ease of use through web browsers.
3.2. VPN concentrator network placement
Now, where does a VPN concentrator typically sit in the network? Its placement is crucial for security and functionality:
- At the network edge: Most commonly, the VPN concentrator is deployed at the perimeter or edge of the corporate network. This means it sits between the untrusted public internet and the trusted internal private network.
- Behind the main firewall or in a DMZ (Demilitarized Zone): Often, it’s placed just behind the primary corporate firewall. The firewall can provide an initial layer of protection, filtering out unwanted traffic before it even reaches the concentrator. Alternatively, it might reside in a DMZ, which is a screened subnetwork that sits between the internal network and the Internet, providing controlled access.
- Requires stable, high-bandwidth internet: Since it handles all incoming remote VPN traffic, the concentrator needs a reliable and high-capacity internet connection to avoid becoming a bottleneck.
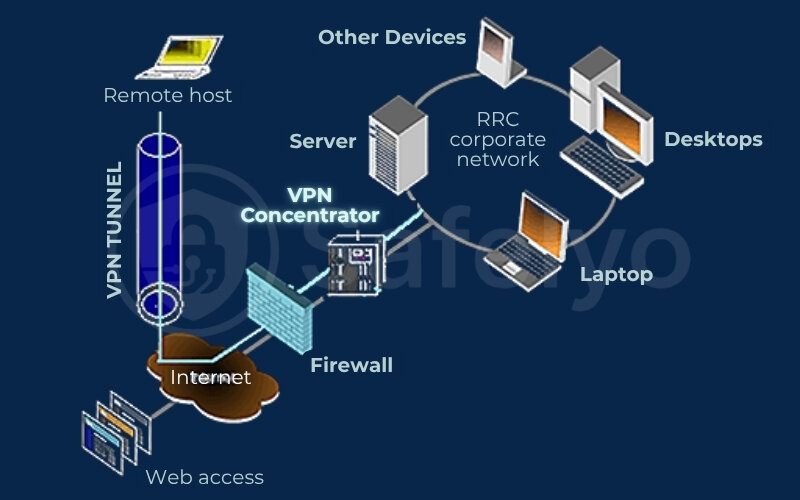
The exact placement can vary based on the organization’s security policies and network architecture, but the goal is always to create a secure, controlled entry point for remote users into the private network. Choosing the right protocols and placing the concentrator strategically are fundamental to a successful VPN deployment.
4. Key functions and purpose of a VPN concentrator
Now that we understand what a VPN concentrator is and how it generally operates, let’s zoom in on its core functions and overarching purpose within an organization’s network.
This device isn’t just a simple passthrough – it’s actively working to manage and secure your remote access. Here are the key functions a VPN concentrator performs:
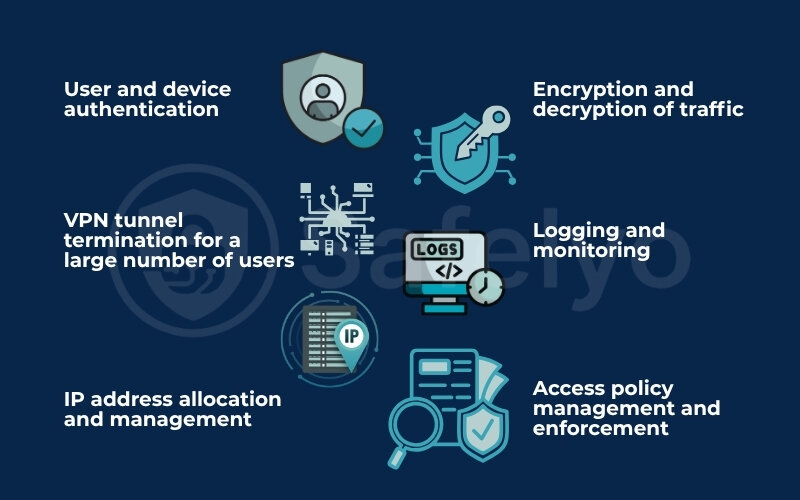
VPN tunnel termination for a large number of users
This is its bread and butter. A concentrator is built to terminate (end) hundreds or even thousands of individual VPN tunnels initiated by remote users or branch offices. It acts as the single, robust destination point for all these encrypted connections.
User and device authentication
Before any tunnel is fully established, the concentrator rigorously authenticates the identity of the user and often the device attempting to connect. As discussed, this can involve usernames/passwords, digital certificates, and multi-factor authentication (MFA) to ensure only authorized individuals gain access.
Encryption and decryption of traffic
The concentrator is responsible for decrypting incoming encrypted data from remote clients so it can be routed to the internal network, and encrypting outgoing data from the internal network before it’s sent back to the remote clients through their secure tunnels.
Access policy management and enforcement
This is a crucial security function. Administrators can configure granular access policies on the VPN concentrator. These policies dictate what resources or network segments a specific user or group of users can access once connected.
For example, the sales team might only access the CRM server, while engineers can access development servers. At Safelyo, we always emphasize that strong policy enforcement is as important as strong encryption.
IP address allocation and management
The concentrator typically assigns a temporary internal IP address to each connected VPN client from a pre-defined pool. This makes the remote device appear as if it’s locally on the company network, simplifying access to internal resources.
Logging and monitoring
To maintain security and troubleshoot issues, VPN concentrators generate detailed logs of connection activity. This includes who connected, when, for how long, and sometimes even the resources accessed (depending on logging levels). These logs are invaluable for security audits and identifying suspicious behavior.
So, what’s the ultimate purpose of a VPN concentrator when you combine all these functions?
- To ensure secure remote access (secure remote access) for a distributed workforce, protecting sensitive company data as it traverses the public internet.
- To simplify the administration and management of numerous VPN connections. Instead of configuring and monitoring countless individual VPN setups, IT teams can manage everything from a central point.
- To bolster the overall security posture of an enterprise network (enterprise VPN solutions) by providing a controlled and monitored gateway for all remote access.
- To enable scalability (VPN concentrator scalability) for remote access solutions. As the number of remote users grows, a well-chosen concentrator can handle the increased load without a proportional increase in administrative complexity.
In essence, a VPN concentrator acts as the dedicated gatekeeper and traffic manager for an organization’s remote workforce, ensuring secure, reliable, and manageable access to vital internal resources.
5. Who really needs a VPN concentrator (and who doesn’t)?
Understanding the capabilities of a VPN concentrator is one thing, but figuring out if your organization actually needs one is another. It’s a significant piece of infrastructure, so it’s not a one-size-fits-all solution.
So, who are the typical candidates for deploying a VPN concentrator, and who can probably manage with simpler alternatives? Here’s a breakdown of common VPN concentrator use cases and scenarios:
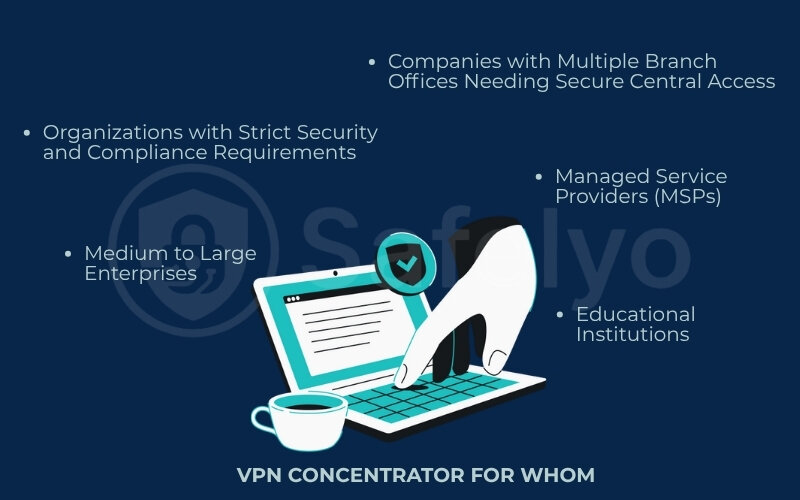
Organizations that typically need a VPN concentrator:
- Medium to Large Enterprises: Companies with a substantial number of employees working remotely (dozens, hundreds, or even thousands) are prime candidates. Managing individual VPN accounts or less robust solutions at this scale becomes unwieldy and a security risk.
- Organizations with Strict Security and Compliance Requirements: Industries like finance, healthcare (HIPAA compliance), and government often handle sensitive data and require highly secure, auditable, and centrally managed remote access. A VPN concentrator, with its strong authentication and policy enforcement, meets these needs.
- Companies with Multiple Branch Offices Needing Secure Central Access: While site-to-site VPNs connect branches, a VPN concentrator can serve as the central hub for remote employees from any location (including those branches or home offices) to access core resources.
- Managed Service Providers (MSPs): MSPs that provide IT services, including secure remote access, to multiple client businesses can leverage VPN concentrators to manage these connections efficiently and securely from a centralized platform.
- Educational Institutions: Universities and large school districts often need to provide secure remote access to resources for students, faculty, and staff, making a VPN concentrator a viable option.
Essentially, if your organization is asking “Do I need a VPN concentrator?” and you’re dealing with a large, distributed workforce that requires regular, secure access to internal networks and data, the answer is likely leaning towards “yes.”
Organizations that likely don't need a VPN concentrator:
- Individual Users or Freelancers: If you’re an individual looking to secure your internet connection or bypass geo-restrictions, a standard personal VPN client software is perfectly adequate. A VPN concentrator would be massive overkill.
- Very Small Businesses (Micro-Businesses): Companies with only a handful of employees (e.g., fewer than 5-10) who occasionally work remotely might find a VPN concentrator too complex and costly for their needs.
- Alternatives for them: A good quality VPN router (a router with built-in VPN server capabilities) or setting up a software-based VPN server on an existing office server can often provide sufficient secure remote access for a small team. I’ve often advised startups in this category to explore these more agile options first.
- Organizations with Minimal Remote Access Needs: If remote work is rare and only involves non-sensitive data, the investment in a VPN concentrator might not be justified.
My advice is always to carefully assess your current and future remote access needs, security requirements, and budget. Don’t over-invest in a solution that’s far more powerful than you require, but also don’t under-invest if your organization’s security and productivity depend on robust remote access for a significant number of users. It’s about finding the right fit.
6. Unpacking the 5+ benefits the VPN concentrator brings to businesses
When an organization decides to implement a VPN concentrator, it’s typically looking to gain some significant advantages, especially as its remote workforce or need for secure connections grows. Let’s unpack the key VPN concentrator benefits that make it an attractive solution for many businesses.
6.1. Enhanced security
This is often the paramount benefit. A VPN concentrator provides a robust, encrypted pathway for all remote access traffic, shielding sensitive company data from interception as it travels over the public internet.
By centralizing connections, it ensures consistent application of security protocols and reduces the attack surface compared to managing disparate, potentially less secure remote access methods.
6.2. Centralized management and control
Imagine trying to manage security policies, user accounts, and software updates for hundreds of individual VPN setups. It’s a nightmare. A VPN concentrator brings all remote access management under one roof.
IT administrators can configure, monitor, update, and enforce security policies for all users from a single interface. This simplifies administration, reduces errors, and saves significant time.
6.3. Scalability to support growth
Businesses evolve, and so do their remote access needs. VPN concentrators are designed with scalability in mind (VPN concentrator scalability). Whether you’re adding a few dozen new remote employees or expanding to support hundreds or thousands more, a properly sized concentrator (or a cluster of them) can handle the increased load without a linear increase in management overhead.
This is crucial for growing organizations. I’ve seen companies seamlessly scale their remote operations thanks to the foresight of implementing a scalable VPN solution like a concentrator.
6.4. Improved productivity for remote employees
When remote employees can securely and reliably access the same internal applications, files, and resources they would in the office, their productivity naturally increases. A stable and performant VPN connection, managed by a concentrator, minimizes frustration from dropped connections or slow access, allowing them to focus on their work.
6.5. Cost-Effectiveness (especially at scale)
While the initial investment in a VPN concentrator (hardware and setup) can seem high, it can be more cost-effective in the long run for larger organizations. Consider the alternatives:
- Managing numerous individual commercial VPN licenses can become expensive and administratively burdensome.
- The cost of a security breach resulting from inadequate remote access security can be astronomical, far outweighing the cost of a robust solution.
- Reduced IT overhead due to centralized management also contributes to long-term savings. According to recent data from Gartner, remote work is here to stay, with many organizations adopting hybrid models. This ongoing trend underscores the need for scalable and secure remote access solutions, where VPN concentrators can offer good long-term value.
6.6. Consistent policy enforcement
With a centralized system, it’s much easier to define and consistently apply security and access policies across all remote users. This ensures that everyone adheres to the same standards, regardless of their location or device, reducing the risk of policy violations or inconsistent security postures.
6.7. Detailed logging and auditing
VPN concentrators provide comprehensive logging capabilities, tracking connection attempts, session durations, bandwidth usage, and more. These logs are vital for security audits, compliance reporting, and troubleshooting network issues.
These benefits combine to create a more secure, manageable, and efficient remote access environment, enabling businesses to support their distributed workforce effectively.
7. Potential drawbacks and considerations of a VPN concentrator
While VPN concentrators offer substantial benefits, especially for larger organizations, they aren’t without their challenges and considerations. It’s crucial to weigh these potential VPN concentrator disadvantages before making an investment.
Here are some key drawbacks and points to keep in mind:
High initial cost and complexity
- Cost
Dedicated VPN concentrator hardware can represent a significant upfront investment, especially for high-capacity models from top-tier vendors. Software-based solutions might have lower initial hardware costs if you have existing servers, but licensing can still be substantial.
- Complexity
Setting up, configuring, and maintaining a VPN concentrator properly requires specialized IT knowledge and expertise. This isn’t typically a plug-and-play device. Misconfiguration can lead to security vulnerabilities or performance issues.
Single Point Of Failure (SPOF)
Because all remote VPN traffic funnels through the concentrator, if that single device (or software instance) fails, all remote access can be instantly cut off. This can be a major disruption.
Mitigation: Organizations often address this by implementing redundant concentrators in a high-availability (HA) cluster, but this, of course, adds to the cost and complexity. From my experience, planning for failover is critical for any business relying heavily on a concentrator.
Potential performance bottleneck
If the VPN concentrator isn’t sized correctly for the number of users and the volume of traffic, or if the underlying internet connection isn’t robust enough, it can become a bottleneck, leading to slow speeds and a poor user experience for remote employees. The encryption/decryption process itself also consumes processing power.
Significant bandwidth requirements
A VPN concentrator needs a high-bandwidth, reliable internet connection at the corporate site where it’s located. If the uplink is insufficient, it will cripple the performance for all connected users, regardless of how powerful the concentrator itself is.
Resource intensive
Handling hundreds or thousands of encrypted tunnels, authenticating users, and enforcing policies means VPN concentrators (especially hardware ones) can be demanding in terms of processing power (CPU) and memory. This is factored into their design but contributes to their cost.
Ongoing maintenance and management
Like any critical network infrastructure, VPN concentrators require regular maintenance, security patching, firmware/software updates, and monitoring to ensure they remain secure and perform optimally. This requires ongoing IT staff time and expertise.
User awareness and compliance are still key.
This is a crucial consideration I always highlight. While a VPN concentrator provides a strong technical security layer, its effectiveness also depends on the security hygiene of the end-users.
If employees use weak passwords, fall for phishing attacks that compromise their VPN credentials, or use unsecured personal devices to connect, the concentrator’s protection can be undermined. Therefore, ongoing user training and awareness programs are still essential.
Understanding these potential downsides allows organizations to plan more effectively, allocate appropriate resources, and implement mitigating strategies to ensure their VPN concentrator deployment is successful and resilient.
8. VPN concentrator vs. other VPN solutions
The term “VPN” is broad, and a VPN concentrator is just one type of solution within that landscape. To truly understand its place, it’s helpful to compare it directly with other common VPN technologies and terms. This will clarify when a concentrator is the right tool for the job.
Here’s how a VPN concentrator stacks up against other VPN solutions:
8.1. VPN concentrator vs VPN router
In essence, a VPN router is a jack-of-all-trades for small networks, offering basic routing plus some VPN capability. A VPN concentrator is a specialist, built for the heavy lifting of managing a large volume of secure remote connections.
This is a common point of confusion, especially for smaller businesses.
| FEATURE | VPN CONCENTRATOR | VPN ROUTER |
| Primary Role | A dedicated device for terminating many VPN tunnels | Router with added VPN server/client functionality |
| Scale | Handles hundreds to thousands of users | Typically tens of users, sometimes up to 50-100 |
| Performance | High, optimized for VPN processing | Moderate, shared with routing tasks |
| Management | Advanced, centralized | Simpler, often basic VPN settings |
| Target User | Medium to large enterprises | Home users, small offices, micro-businesses |
| Cost | Higher | Lower to moderate |
| Complexity | Higher to set up and manage | Simpler |
| Typical Use Case | Secure remote access for a large workforce | Secure home network, basic remote access for SOHO |
As I often tell clients, if you have more than a couple of dozen regular remote users, a VPN router will likely start to struggle, and a concentrator becomes a more viable option.
8.2. VPN concentrator vs VPN server (software-based)
This comparison can be a bit nuanced because a VPN concentrator can be a software-based solution. The distinction often lies in dedication and optimization.
| Feature | VPN Concentrator (Hardware or Dedicated Software) | General VPN Server (Software on standard OS) |
| Optimization | Highly optimized for VPN performance & scale | Performance depends on server hardware & OS overhead |
| Hardware | Often, specialized hardware (VPN concentrator hardware) or a dedicated virtual appliance | Runs on general-purpose server hardware |
| Throughput | Typically higher, designed for many tunnels | Can vary widely, may be limited by other server tasks |
| Management UI | Usually robust, enterprise-grade features | Can range from basic to advanced (e.g., OpenVPN) |
| Integration | Often integrates with enterprise auth systems | May require more manual integration |
| Scalability | Designed for high scalability | Scalability depends on the underlying server capabilities |
Key takeaway
While you can set up VPN server software (like OpenVPN or StrongSwan) on a standard Linux or Windows server to handle remote connections, a VPN concentrator (even if software-based) is typically a more purpose-built, hardened, and performance-tuned solution specifically for managing a high volume of VPN tunnels. It often comes with more enterprise-focused management features out of the box.
8.3. VPN concentrator vs site-to-site VPN
A VPN concentrator facilitates remote access VPNs (also known as client-to-site VPNs). A site-to-site VPN is designed to permanently link two or more office networks together as if they were one, for example, connecting a head office with a branch office.
These serve very different primary purposes, though both use VPN technology.
| FEATURE | VPN CONCENTRATOR | SITE-TO-SITE VPN |
| Connection Type | Remote Access VPN (individual users to the network) | Network-to-Network VPN (connects entire networks) |
| Endpoints | Many individual clients connect to one central point | Typically, two or more fixed network gateways (routers/firewalls) |
| Primary Goal | Secure access for remote employees/devices | Securely link geographically separate office LANs |
| User Interaction | Users initiate connections via VPN client software | Usually “always-on,” transparent to end-users |
| Hardware Used | VPN concentrator at corporate; client software on user devices | VPN-capable routers or firewalls at each site |
They are not mutually exclusive; an organization might use site-to-site VPNs for its branches and a VPN concentrator for its remote individual workers.
8.4. VPN concentrator vs VPN gateway
This is where terminology can get a bit blurry, as these terms are sometimes used interchangeably, or one can be a component of the other.
VPN Gateway
This is a broader term that generally refers to any device or software that sits at the edge of a network and provides VPN connectivity. This could be a VPN-capable router, a firewall with VPN functions, or a dedicated VPN server. Its job is to encrypt and decrypt traffic for VPN tunnels.
VPN Concentrator
As we’ve discussed, a VPN concentrator is a specialized type of VPN gateway. Its defining characteristic is its ability to terminate and manage a large number of simultaneous VPN tunnels from many individual remote clients. It’s optimized for high-density client connections.
Think of it this way: All VPN concentrators are VPN gateways, but not all VPN gateways are VPN concentrators. A simple VPN router acts as a VPN gateway for a few connections, but it lacks the scale, performance, and advanced management features of a true VPN concentrator. When you need to handle hundreds or thousands of remote users, you’re looking for the specialized capabilities of a VPN concentrator.
Understanding these distinctions helps in choosing the right VPN architecture for specific organizational needs.
9. FAQ about VPN concentrators
Here are answers to some of the most common questions people have about VPN concentrators.
What is the difference between a VPN and a VPN concentrator?
A VPN (Virtual Private Network) is a general technology for creating secure, encrypted connections over a public network. A VPN concentrator is a specific type of hardware or software device designed to handle and manage a large number of these VPN connections simultaneously, typically for an organization’s remote users connecting to its private network.
What is the difference between a VPN gateway and a concentrator?
A VPN gateway is a broad term for any device that provides VPN connectivity at the network edge. A VPN concentrator is a specialized, high-capacity VPN gateway optimized to terminate and manage hundreds or thousands of VPN tunnels from individual remote clients. Think of a concentrator as a heavy-duty VPN gateway.
How much does a VPN concentrator cost?
The cost varies widely based on whether it’s hardware or software, the vendor, supported user capacity, features, and performance. Hardware units can range from a few thousand to tens of thousands of dollars. Software solutions might involve licensing fees. It’s best to get quotes based on specific organizational needs.
What is the purpose of a VPN tunnel?
The purpose of a VPN tunnel is to create a secure, private, and encrypted communication channel between two points (e.g., a remote user’s device and a VPN concentrator) across an untrusted public network like the internet. This protects the data transmitted through it from being intercepted or viewed.
Do I need a VPN concentrator for my small business?
Probably not, if your business is very small (e.g., fewer than 10-20 regular remote users). A VPN router or a software VPN server on existing hardware might be more cost-effective. VPN concentrators are better suited for medium to large organizations with significant remote access demands.
Where is a VPN concentrator typically placed in a network?
A VPN concentrator is usually placed at the edge of the corporate network, often behind the main firewall or within a DMZ (Demilitarized Zone). This allows it to securely manage connections from the public internet to the private internal network.
Can a VPN concentrator slow down internet speed?
While the encryption/decryption process can introduce some overhead, modern VPN concentrators are designed for high performance. Significant slowdowns are more often due to insufficient internet bandwidth at the corporate site, an undersized concentrator for the user load, or misconfiguration, rather than the concentrator technology itself.
What are some common examples of VPN concentrators?
Many established networking vendors offer VPN concentrator solutions. Well-known examples include hardware appliances from companies like Cisco, Palo Alto Networks, Juniper Networks, and Fortinet. There are also robust software-based VPN server solutions that can function as concentrators when deployed with sufficient resources.
10. Conclusion
Understanding what is a VPN concentrator is a key step for any organization looking to provide secure, scalable, and manageable remote access for its workforce. It’s more than just a piece of hardware or software; it’s a strategic component of modern network security architecture, especially in an era of increasing remote and hybrid work models.
To sum up the main points we’ve covered:
- A VPN concentrator is a dedicated solution designed to terminate and manage a large number of simultaneous VPN connections.
- It provides crucial benefits like enhanced security, centralized management, robust scalability, and consistent policy enforcement for remote access.
- The ideal candidates are typically medium to large organizations with a significant number of remote users and strong security requirements.
- Important considerations include initial cost, complexity, potential as a single point of failure, and the need for adequate bandwidth and IT expertise.
- It differs from VPN routers, general VPN server software, and site-to-site VPNs in its scale, primary purpose, and performance capabilities.
Choosing whether to implement a VPN concentrator requires a careful evaluation of your organization’s specific needs, existing infrastructure, budget, and future growth plans. It’s about finding the right balance between security, functionality, and cost.
At Safelyo, we break down complex tech so you can make confident, informed choices. To learn more about VPN solutions, concentrators, and secure network setups, explore more articles in our VPN Guides category.