Ever wondered what happens in the split second after you type a website address and hit enter? Traditionally, that request travels across the internet like a postcard, with the address you want to visit written in plain view for anyone to see. So, what is DNS over HTTPS (DoH)? It’s the digital equivalent of putting that postcard inside a sealed, tamper-proof envelope.
In an age where our every click is often tracked and monetized, understanding how your digital footprints are made isn’t just for tech experts – it’s essential for everyone. This simple tweak to how your browser finds websites can make a huge difference in protecting your privacy from your internet service provider (ISP) and other prying eyes.
As a cybersecurity analyst with years of experience demystifying complex tech, I’ve seen how often major privacy leaks happen through the simplest, most overlooked channels. Unencrypted DNS is a massive loophole that has been hiding in plain sight for decades. DoH isn’t a silver bullet for all security threats, but it’s a fundamental, powerful fix that everyone should know about.
In this straightforward guide, you will discover:
- Why your normal internet connection has a built-in privacy risk.
- How DoH works to solve this problem using a simple analogy.
- The key differences between DoH and its sibling, DoT.
- How you can easily enable this feature in just a few clicks.
Don’t let your online activity be an open book. Let me guide you through this crucial step to reclaiming your digital privacy right in this article below.
1. How DNS traditionally works (and why it’s a privacy risk)
Before we can appreciate the brilliance of the solution, we first need to understand the problem. Think of the Domain Name System (DNS) as the internet’s phonebook. It’s a massive, distributed directory that translates human-friendly website names (like safelyo.com) into computer-friendly IP addresses (like 104.21.60.149). Without it, we’d have to memorize long strings of numbers for every site we visit.
Now, let’s use a simple analogy to see how this phonebook lookup traditionally works: the postcard.
When you type a website into your browser, you’re essentially writing the name of that site on a postcard. This postcard is then sent to a DNS resolver – usually operated by your internet service provider (ISP) – with a simple request: “What’s the address for this place?” Here’s what happens next:
- Your computer sends this “postcard” (a plain text DNS query) over the internet.
- It travels on a specific, unencrypted channel (Port 53), visible to anyone on the network path.
- Your ISP’s resolver receives the postcard, reads the website name, and sends another postcard back with the correct IP address.
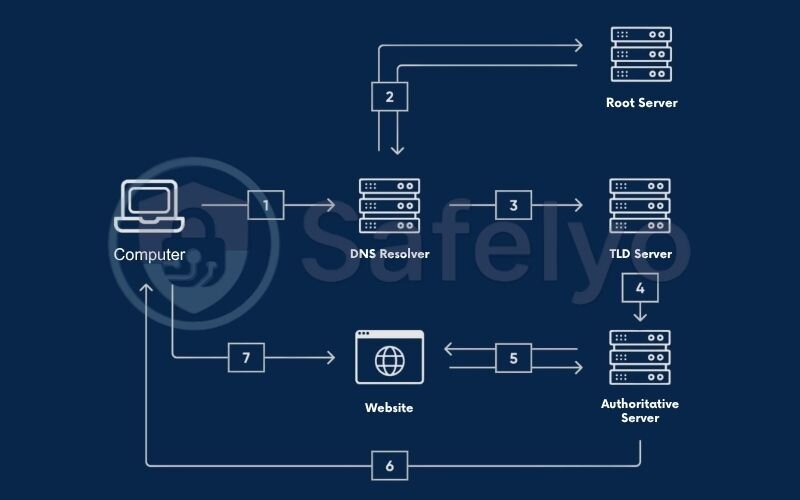
This process has two huge, glaring problems.
First, there is absolutely no privacy. Because the postcard isn’t in an envelope, your ISP can read every single one. They can, and often do, compile a complete history of every website you visit. In my years analyzing network traffic, this is the single most common way people unknowingly broadcast their entire browsing history for their ISP to see, collect, and even monetize.
Second, it’s vulnerable to manipulation. Imagine a malicious postal worker intercepting your postcard and scribbling a different address on it before it reaches its destination. This is essentially what happens in DNS spoofing or “man-in-the-middle” attacks. Attackers can hijack your unencrypted request and redirect you to a fake, malicious website – like a fake banking site – to steal your credentials.
This is the fundamental weakness that DNS over HTTPS was designed to fix.
Read more:
2. What is DNS over HTTPS (DoH), and how does it solve the problem?
If traditional DNS is a postcard, then DNS over HTTPS is its modern, secure counterpart: the sealed, tamper-proof envelope. It fundamentally changes how your DNS requests are sent, directly solving the privacy and security issues we just discussed.
Instead of shouting your request across the open internet, DoH takes your DNS query, wraps it in a strong layer of encryption, and sends it out as regular HTTPS traffic. It uses the very same secure channel (Port 443) that your browser uses for online banking, shopping on Amazon, or logging into your email.
From a network security perspective, I find this part particularly clever. Instead of creating a new, special type of traffic that could be easily identified and blocked, DoH cleverly camouflages your DNS requests to look identical to the millions of other secure connections happening every second.
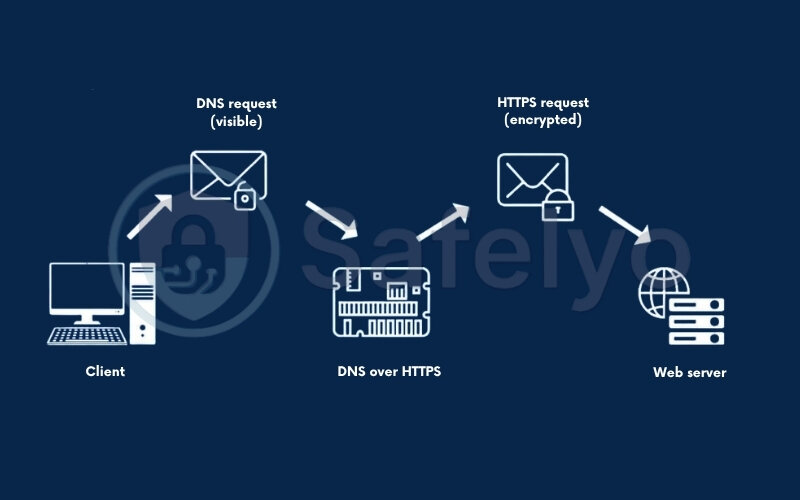
Let’s look at the new, improved workflow:
- Your browser takes your request (“What is the IP for safelyo.com?”), encrypts it, and places it inside that metaphorical “sealed envelope.”
- This encrypted packet travels over Port 443 to a DoH-compatible DNS resolver (like one from Cloudflare, Google, or Quad9). To your ISP, it’s indistinguishable from you simply visiting any other secure https:// website.
- The DoH resolver receives the packet, securely decrypts it, finds the IP address, and sends the answer back to you inside the same secure, encrypted tunnel.
The benefits are immediate and profound:
- Your ISP is blinded. They can see that you’re exchanging encrypted data with a DoH server, but they can no longer read the “postcard” inside. The log of every specific website you visit simply vanishes from their view.
- Your connection is protected from tampering. Since the entire conversation is encrypted, a “man-in-the-middle” attacker can no longer read or alter your request. That digital envelope ensures you land on the real website you intended to visit, not a malicious clone.
3. DNS over HTTPS (DoH) vs. DNS over TLS (DoT): What’s the difference?
As you explore the world of encrypted DNS, you’ll quickly run into another three-letter acronym: DoT, or DNS over TLS. Think of DoT as DoH’s slightly older, more specialized cousin. Both are designed to do the exact same thing – encrypt your DNS queries – but they go about it in a slightly different way.
In my experience, explaining this to users, the main difference boils down to one simple concept: camouflage versus a dedicated channel.
- DoH is the master of camouflage. It sends your encrypted DNS requests through the same crowded highway (Port 443) as all other secure web traffic, making it blend in perfectly.
- DoT, on the other hand, uses its own special, dedicated lane (Port 853). The traffic in this lane is also secure and encrypted, but it’s clearly marked as “DNS traffic.”
This distinction might seem small, but it has significant real-world implications. Here’s a clear breakdown in a comparison table:
| Feature | DNS over HTTPS (DoH) | DNS over TLS (DoT) |
|---|---|---|
| Port Used | 443 (Standard HTTPS port) | 853 (A dedicated port) |
| Traffic Appearance | Blends in with all other secure web traffic | It is a distinct, identifiable type of DNS traffic |
| Ease of Blocking | Very difficult for network admins to block | Easier to block (by simply blocking Port 853) |
| Privacy Level | Excellent | Excellent |
| Performance | May have a tiny, negligible overhead | Potentially slightly faster due to less overhead |
So, which one should you choose?
From a practical standpoint, the performance difference is so minimal that most people will never notice it. The real deciding factor is the “ease of blocking.” Because DoH traffic is hidden among a sea of essential web traffic, it’s extremely difficult for a restrictive network (like at a school, office, or in a country with censorship) to block it without also breaking huge parts of the internet.
For this reason, my advice for the vast majority of users is simple: stick with DoH. Its ability to blend in provides a more resilient form of privacy. DoT is an excellent and secure standard, but its use of a dedicated port makes it an easier target for anyone looking to control or monitor DNS traffic.
4. The benefits and controversies of DoH
Like any powerful technology, DoH isn’t without its debates. While it offers clear advantages for individual users, it also creates challenges for network administrators and raises valid questions about the structure of the internet itself. As a security professional, I believe it’s crucial to understand both sides of the coin to appreciate the full picture.
4.1 The benefits (for the end-user)
For the everyday internet user, the advantages of enabling DoH are straightforward and significant.
- Enhanced privacy
This is the number one benefit. By encrypting your DNS queries, you effectively stop your ISP from building a detailed profile of your browsing habits. They can no longer see the list of websites you visit, which is a massive win for personal privacy.
- Improved security
DoH acts as a shield against common redirection attacks like DNS spoofing. Because the connection is encrypted and authenticated, you can be much more confident that you’re connecting to the legitimate website you intended to visit, not a malicious imposter.
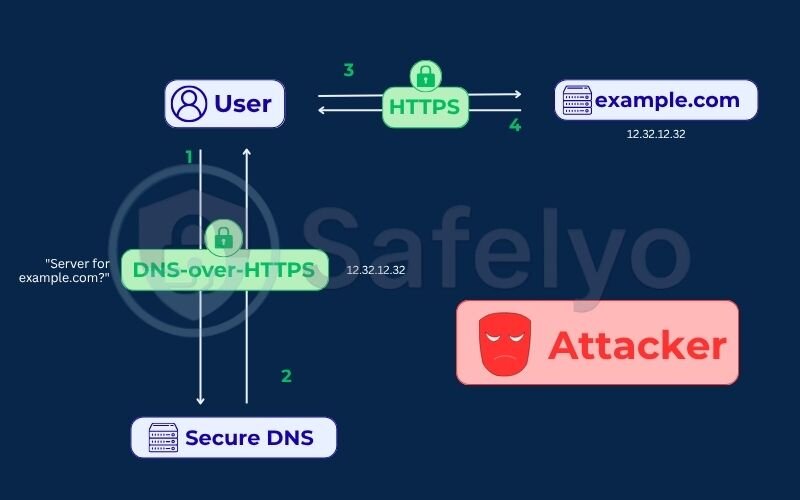
- Bypasses some censorship
In many places, the simplest way to block a website is at the DNS level. When you try to visit the site, the ISP’s DNS server simply refuses to give you the IP address. Since DoH bypasses your ISP’s DNS, it can often circumvent these basic forms of content blocking.
See also:
4.2 The controversies (the enterprise and ISP perspective)
On the other side of the argument, many network administrators and security experts have raised important concerns.
- Centralization of DNS
This is perhaps the most significant philosophical debate around DoH. Traditionally, DNS requests are distributed across thousands of different ISPs all over the world. With DoH, we’re encouraged to route our requests to a handful of massive, global tech companies like Google and Cloudflare.
Instead of your DNS data being spread across thousands of different ISPs, DoH effectively funnels a large portion of it to a small number of global tech giants who provide DoH services. This raises questions about giving these few companies even more insight into global internet traffic. It’s a classic trade-off: do you trust your local ISP or a global tech giant more with your data?
- Bypasses network security and filtering
Many organizations, from corporations to schools, rely on monitoring DNS traffic to enforce security policies. They use it to block access to malicious websites, filter inappropriate content, and monitor for signs of malware infections.
When a user’s device uses DoH, its DNS traffic becomes invisible to these security tools, essentially creating a blind spot that can be exploited by both malicious actors and employees bypassing company policy. From a sysadmin’s point of view, it can feel like trying to secure a building when someone has just opened a back door they can’t monitor.
5. How to enable DNS over HTTPS (DoH)
Now for the best part: Turning this privacy feature on is incredibly easy.
For most people, the simplest way is directly within your web browser. This ensures that any browsing you do in that application is protected. It’s one of those rare “set it and forget it” security wins that I always recommend people take advantage of.
Here’s how to do it in the most popular browsers.
5.1 In your web browser (the easiest way)
Most modern browsers now have a built-in setting for “Secure DNS”, which uses DoH. The process is very similar across all of them.
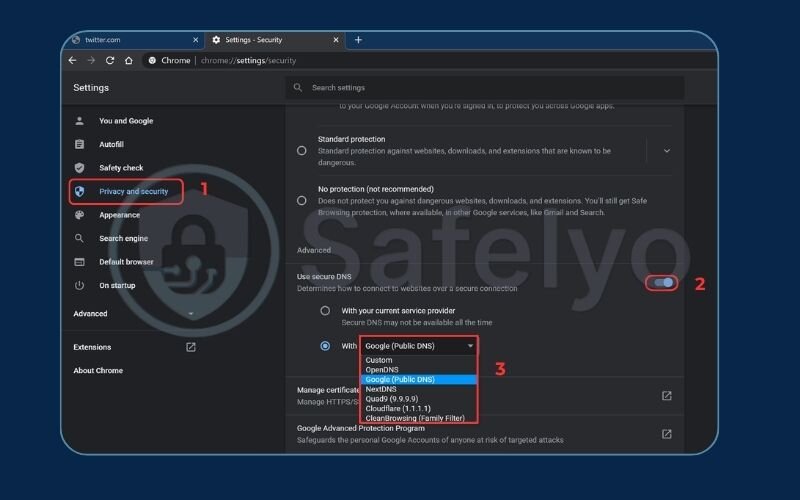
For Google Chrome:
- Go to Settings > Privacy and security.
- Click on Security.
- Scroll down and enable the Use secure DNS option. It will usually default to your current service provider if they support it, or you can choose a specific one like Cloudflare or Google from the list.
For Mozilla Firefox:
- Go to Settings > Privacy & Security.
- Scroll all the way down to the DNS over HTTPS section.
- Select an option from the dropdown. “Max Protection” is a great choice as it ensures all your DNS requests use DoH.
For Microsoft Edge:
- Go to Settings > Privacy, search, and services.
- Scroll down to the Security section.
- Enable the toggle for Use secure DNS. Just like Chrome, you can let it choose automatically or pick a specific provider.
5.2 In your operating system
For more comprehensive protection that covers all applications on your device (not just the browser), you can enable DoH at the operating system level. This is slightly more advanced but provides broader coverage.
On Windows 11: Microsoft has integrated DoH support directly.
- Go to Settings > Network & internet.
- Click on your current connection (e.g., Wi-Fi or Ethernet).
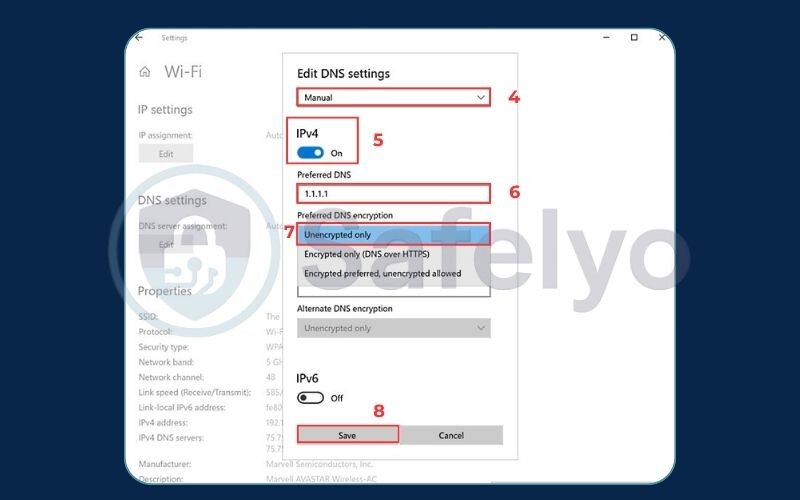
- Find the DNS server assignment and click Edit.
- Switch from “Automatic (DHCP)” to “Manual”, turn on IPv4, and enter the IP addresses of a DoH provider (e.g., 1.1.1.1 and 1.0.0.1 for Cloudflare).
- Under Preferred DNS encryption, select “Encrypted only (DNS over HTTPS)”. Windows will handle the rest.
On macOS, iOS, and Android:
The most straightforward method is to use a dedicated app. For example, installing the 1.1.1.1 app from Cloudflare will configure your entire device to use their secure DoH service with a single tap. It’s a method I often use myself when on public Wi-Fi for a quick and simple layer of protection.
Enabling DoH is a quick win. But for a list of the best providers, you can explore our guide to the best private DNS servers to find one that fits your needs.
6. Is DNS over HTTPS a VPN?
This is a question I get all the time, and the answer is clear and simple: No, they are very different tools for different jobs. Confusing the two can leave you with a false sense of security, so it’s vital to understand the distinction.
DoH is a scalpel, designed to do one specific thing very well: it only encrypts your DNS queries. It hides the names of the websites you are trying to visit from your ISP. However, it does not hide your IP address, nor does it encrypt any of the actual data you exchange with those websites once you connect. Your ISP can still see which IP addresses you are connecting to, how much data you’re sending, and for how long.
A VPN (Virtual Private Network), on the other hand, is a full-body shield. A VPN encrypts your entire internet connection. It creates a secure, private tunnel for all your traffic – not just DNS, but also your web browsing, streaming, gaming, and app data. Crucially, it also hides your real IP address, replacing it with the IP address of the VPN server.
Let’s go back to our mail analogy to make it perfectly clear:
Think of DoH as securing only the address written on the outside of your envelope. Your mail carrier (ISP) can’t read the destination address, but they still know the letter came from your house (your IP address) and can see the envelope itself.
A VPN secures the envelope, its entire contents, and sends it via a private courier who doesn’t know your home address. The courier takes it to a different location (the VPN server) before sending it to its final destination. No one can see where it came from, where it’s going, or what’s inside.
While DoH is a fantastic and necessary step for privacy, it only protects one piece of the puzzle.
For complete privacy and security that DoH alone cannot provide, a VPN is essential. Learn more about how a VPN works to protect your entire digital life.
Read more:
7. FAQ about DNS over HTTPS
Here are some of the most common questions I hear about DNS over HTTPS. Getting these quick answers will help solidify your understanding of this important technology.
Should you use DNS over HTTPS?
Yes, for the vast majority of people. Enabling DoH is a simple, free, and effective way to significantly boost your online privacy by hiding your browsing history from your internet service provider.
Does DoH make my internet slower?
The impact is usually negligible and often completely unnoticeable. While there’s a tiny bit of processing overhead from encryption, I’ve found that using a fast DoH provider like Cloudflare can sometimes be even quicker than a slow default ISP DNS.
Which DoH provider should I use?
Popular and trusted choices include Cloudflare (1.1.1.1), Google (8.8.8.8), and Quad9 (9.9.9.9). Quad9 is particularly noteworthy because it also actively blocks access to known malicious domains, adding an extra layer of security.
What is 1.1.1.1 DNS over HTTPS?
This refers to Cloudflare’s specific implementation of the DoH protocol. 1.1.1.1 is the IP address for their public DNS resolver, which is one of the most popular and fastest DoH services available, focusing heavily on user privacy and speed.
Why is DNS over HTTPS controversial?
The main controversies stem from two points: it centralizes DNS data to a few large tech companies, and it can bypass network security tools used by businesses and schools for content filtering and malware protection.
Why disable DNS over HTTPS?
You might disable DoH if you are on a corporate or school network that requires DNS-level monitoring for security, or if you are a parent using a router-based content filter to protect your children. For most users on a home network, there is little reason to disable it.
Is DoH enabled by default?
It is increasingly being enabled by default in major browsers like Firefox and Chrome, but this can depend on your region and existing settings. It’s always best to check your browser’s security settings to be sure it’s active.
How can I check if DoH is working?
An easy way is to visit Cloudflare’s security check tool at 1.1.1.1/help. This page will run several tests and explicitly tell you if you are connected using “DNS over HTTPS.”
8. Conclusion
Understanding what is DNS over HTTPS gives you the power to take a simple yet incredibly significant step in reclaiming your online privacy. It’s no longer an obscure feature for tech enthusiasts but a foundational privacy tool for the modern internet user. By sealing your digital “postcards” inside an encrypted envelope, you take back control over who gets to see where you go online.
To recap the most important points to remember:
- DoH encrypts your DNS requests, effectively hiding your list of visited websites from your ISP.
- It cleverly blends in with regular HTTPS traffic, making it very difficult to block, unlike its cousin DoT.
- It is a fantastic privacy tool, but it is not a replacement for the comprehensive protection of a VPN, which secures your entire internet connection.
Enabling DoH in your browser is a quick win for your digital hygiene and a great first step on the path to better security. To continue building a complete digital defense, explore more expert articles and guides in the Privacy & Security Basics library, and let’s Safelyo become your own security expert.












