In today’s increasingly interconnected world, understanding how to protect your personal information and navigate the internet privately effectively isn’t just a nice-to-have – it’s becoming essential. Whether you’re a journalist handling sensitive data, an activist in a restrictive region, or simply someone who values their anonymity, knowing about tools like Onion over VPN can be a game-changer.
What is Onion over VPN? Think of it as a powerful, multi-layered shield for your online activities, combining the encryption of a VPN with the anonymizing power of the Tor network to boost your digital privacy significantly.
With many years dedicated to exploring and explaining cybersecurity solutions, I’ve seen firsthand how complex these tools can seem, yet how vital they are for true online freedom. Properly explaining Onion over VPN can empower anyone to take control of their digital footprint. It’s not just for tech-savvy users; it’s a robust privacy measure for anyone who needs extra protection.
In this comprehensive guide, you’ll discover:
- What Onion over VPN (or Tor over VPN) actually is and how this combination works.
- The step-by-step process of how your data travels through this setup.
- The key benefits it offers, such as hiding your Tor usage from your ISP.
- The potential risks and downsides like significantly slower speeds.
- How to set it up safely and when it’s the right choice for you.
- Crucial differences between Onion over VPN, VPN over Tor, and Double VPN.
Don’t let concerns about surveillance or data tracking compromise your online experience. Let me walk you through everything you need to know to master Onion over VPN and fortify your privacy, starting now.
1. Understanding the core components: VPN and The Onion Router (Tor)
Before we can fully unpack what Onion over VPN is, it’s crucial to grasp the individual technologies that come together to make it work. Think of it like understanding the ingredients before you can appreciate the final dish.
Knowing how a Virtual Private Network (VPN) and The Onion Router (Tor) function independently will make it much clearer why combining them can offer such a robust privacy solution. The synergy between an Onion Router and VPN is what gives this method its strength, that making it effective.
1.1. What is a VPN in the context of Onion over VPN?
At its core, a Virtual Private Network (VPN) is a tool that encrypts your internet connection and masks your original IP address. It achieves this by routing your internet traffic through a remote server operated by the VPN provider. When you connect to a VPN, your data is shielded within an encrypted tunnel, making it unreadable to outsiders like your Internet Service Provider (ISP) or potential eavesdroppers on public Wi-Fi.
In an Onion over VPN setup, the VPN plays a critical first-line-of-defense role. It encrypts your data before it even has a chance to reach the Tor network. More importantly, your ISP will only see you connecting to a VPN server, not that you are subsequently accessing Tor. The Tor network’s entry node, in turn, will see the IP address VPN, not your real IP address. This initial layer of obfuscation is key.
1.2. What is the Onion Router (Tor) and its role
Next up is The Onion Router, more commonly known as Tor. Tor is free, open-source software and a global, decentralized network of volunteer-operated servers (called relays). Its primary design goal is to enable anonymous web browsing. The name “Onion” in “Onion over VPN” directly refers to Tor’s signature technique: Onion routing. This is where the magic of its anonymity largely comes from.
So, how does this onion routing work? Imagine your data is an onion. Before it’s sent across the Tor network, it’s wrapped in multiple layers of strong encryption, much like the layers of an actual onion.
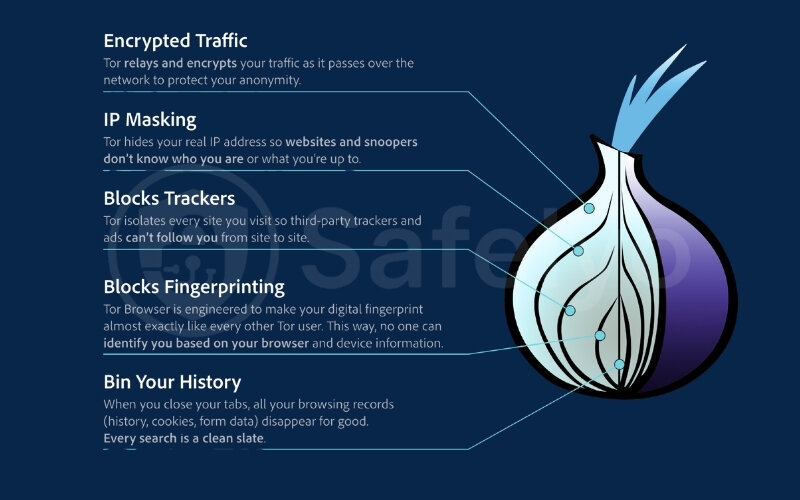
This multi-layered data packet then travels through a series of randomly selected relays within the Tor network. Each relay in the chain only decrypts one layer of encryption, just enough to know where to send the packet next. The relay doesn’t know the full path (origin or final destination), only the previous and next hop. Finally, the last relay in the chain, known as the exit node, sends your data to its ultimate destination on the internet.
The main purpose of Tor is to provide a high degree of anonymity for users by concealing their true IP address and location, making it incredibly difficult to trace internet activity back to them. It also protects users from traffic analysis, a form of network surveillance that can reveal who is talking to whom over a network.
In an Onion over VPN configuration, Tor’s role kicks in after your traffic has passed through the VPN server. Once your VPN-encrypted traffic enters the Tor network, Tor takes over the heavy lifting of deep anonymization.
Tor routes your IP, already masked by the VPN, through random relays. These relays add crucial encryption layers, making the original source nearly impossible to trace. This helps clarify how Onion over VPN is different from Tor used alone; the VPN provides an initial shield before Tor even gets involved.
>> Read more:
2. What is Onion over VPN: Combining the strengths
Now that we’ve covered the basics of VPNs and The Onion Router (Tor) individually, let’s bring them together. What is Onion over VPN?
At its simplest, Onion over VPN (often also referred to as Tor over VPN) is a method where you first establish an encrypted connection to a VPN server. Then, all your internet traffic from that VPN server is routed through the Tor network before it reaches its final online destination.
The connection order is crucial and looks like this:
Your Device → VPN Server (encryption & IP change) → Tor Network (anonymization via multiple relays) → Internet
The primary purpose of Onion over VPN is to leverage the distinct strengths of both technologies, creating a more robust setup for privacy with Onion over VPN and enhanced anonymity. Onion VPN configurations aim for a “best of both worlds” scenario.
A key advantage of this specific order is how it appears to outsiders. Your Internet Service Provider (ISP) can only detect that you are connected to a VPN server; they cannot see that you are subsequently using the Tor network. This is a significant benefit if you’re concerned about your ISP flagging or throttling Tor usage.
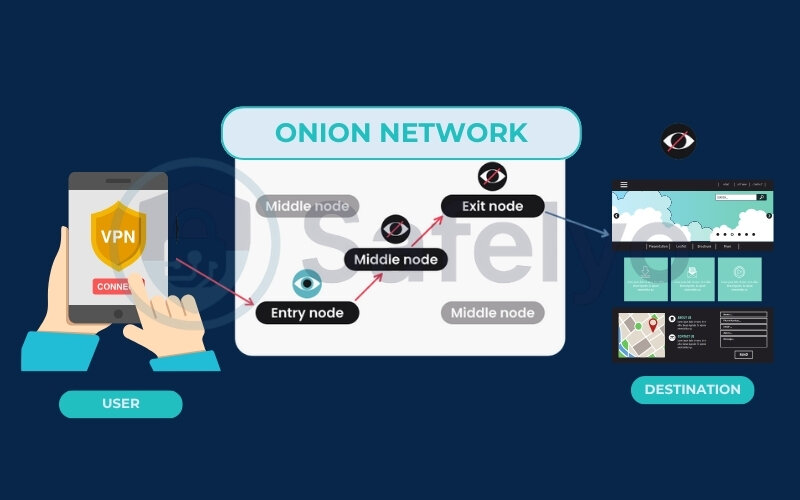
Simultaneously, the entry node (the first relay) of the Tor network will only see the IP address of the VPN server, not your actual, ISP-assigned IP address. This means your real IP address is hidden from the Tor network itself, at least at the entry point. This directly addresses the common question:
- “Can my ISP see I’m using Onion over VPN?”
- Answer: NO, they only see VPN use.
- “Does Onion over VPN hide my IP address?
- Answer: YES, in multiple ways.
As someone who has experimented with various privacy setups, I’ve found that this is the configuration most users gravitate towards when their primary goal is maximizing privacy and anonymity, especially if they have concerns about their ISP monitoring their Tor activity or if they want an extra layer of protection before their traffic even touches the Tor network. It’s a solid approach explained as an Onion over VPN method that offers peace of mind. Some even look for specific Onion network VPN services or use it with the Tor browser VPN setup.
3. How does Onion over VPN work? A step-by-step explanation
Understanding how Onion over VPN works involves following the journey your data takes from your device to the internet. In essence, you’re creating a secure tunnel within another secure environment.
The quick summary of the data flow looks like this:
Your Device → VPN Server → Tor Network Relays → Destination Website
Throughout this entire process, several key things happen to your data that answer the question, “What happens to my data with Onion over VPN?” – It’s encrypted by the VPN, then its source IP is masked by the VPN when entering Tor, then it’s further anonymized and multi-layer encrypted by Tor, and finally, it exits to the internet from a Tor IP address.
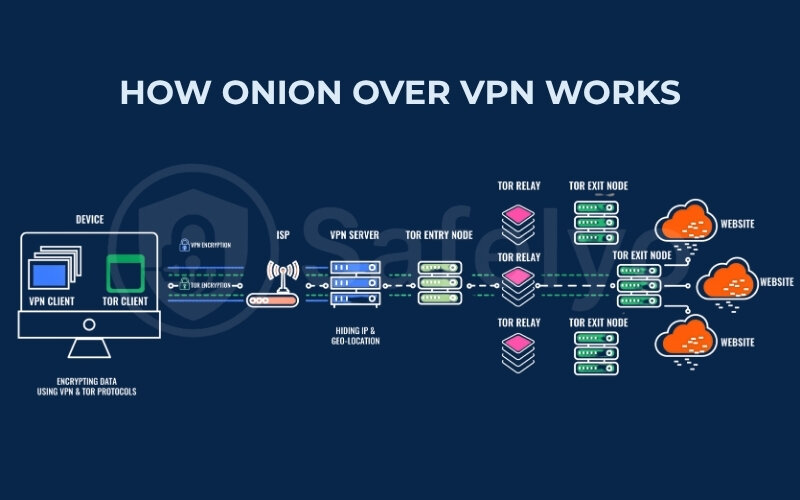
It’s a multi-stage process designed to layer security and anonymity. This sequence ensures your VPN encrypts your connection and masks your Tor usage from your ISP, while the Tor network subsequently adds its powerful layers of anonymity. Here’s a detailed, step-by-step breakdown:
3.1. Step 1: Initiate VPN connection
First, you launch your VPN application on your computer or mobile device and connect to a VPN server of your choice. At this moment, all internet traffic from your device is encrypted and securely routed to this VPN server. Your real IP address is now masked, and your ISP can only see an encrypted connection to the VPN server’s IP address. This is the foundational step.
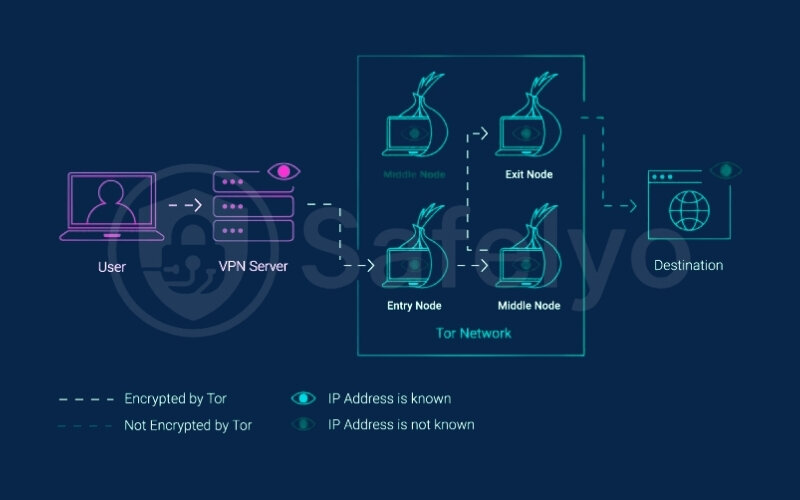
3.2. Step 2: Activate Tor connection
Once your VPN connection is stable and active, you then open the Tor Browser (or another application configured to use the Tor network). It’s important that the VPN is running before you initiate any Tor activity.
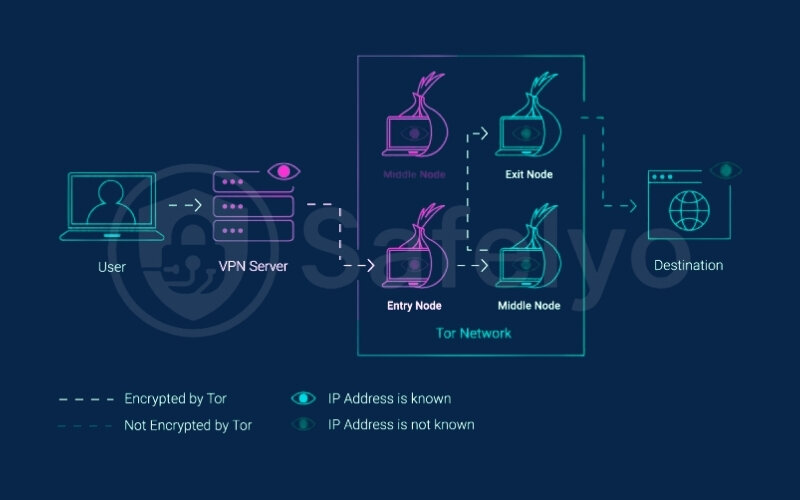
3.3. Step 3: Data from device (via Tor Browser) to VPN server
When you make an internet request through the Tor Browser (like typing a website address), that request first travels through the already established encrypted VPN tunnel. So, the data, which is about to enter the Tor network, is first processed and protected by your VPN.
3.4. Step 4: VPN server forwards traffic to the Tor network
The VPN server receives this encrypted traffic from your Tor Browser. Because it’s the endpoint of that initial VPN tunnel, it decrypts the traffic (only the VPN’s encryption layer). Then, crucially, the VPN server forwards this traffic into the Tor network. The source IP address that the Tor network’s entry node sees is the IP address of your VPN server, not your home IP.
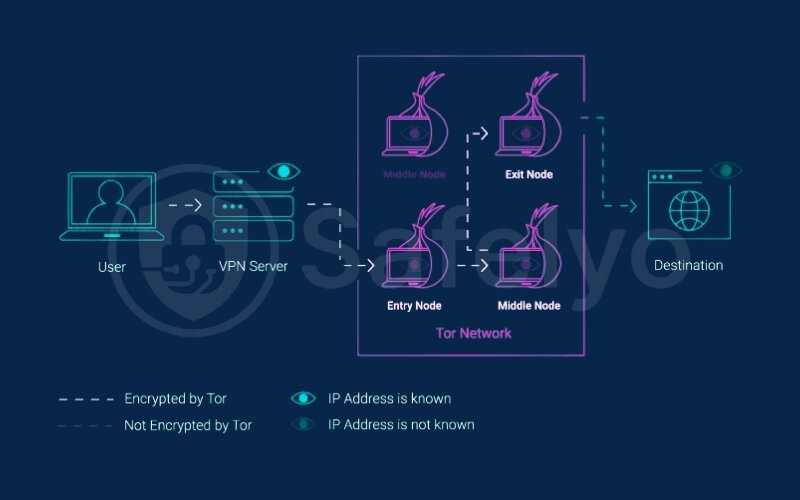
2.5. Step 5: Data travels through the Tor network
Now your traffic is inside the Tor network. It gets wrapped in Tor’s multiple layers of encryption (the “onion”) and begins its journey through a series of randomly selected Tor relays – typically an entry node, one or more middle relays, and an exit node. Each relay only knows the identity of the previous and next relay in the chain, not the full path.
2.6. Step 6: Tor exit node to destination
Finally, the last relay in the chain, the Tor exit node, decrypts the outermost layer of Tor’s encryption and sends your request to the destination website or online service. The website you visit will only see the IP address of this Tor exit node. It has no visibility of your real IP or the VPN server’s IP.
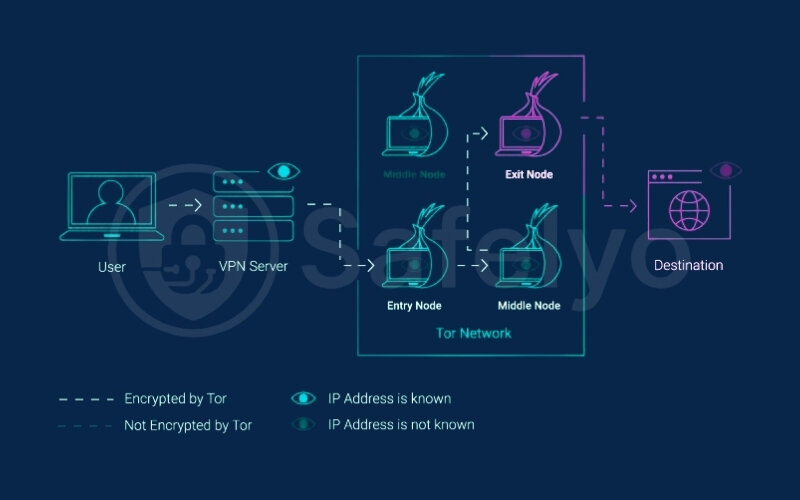
From my experience, this layered approach significantly enhances privacy compared to using either Tor or a VPN alone. With Tor alone, your ISP can see you’re connecting to Tor. With a VPN alone, your VPN provider (if they weren’t trustworthy) could potentially see your activity. Onion over VPN mitigates both these specific concerns by design.
4. Key benefits of using Onion over VPN
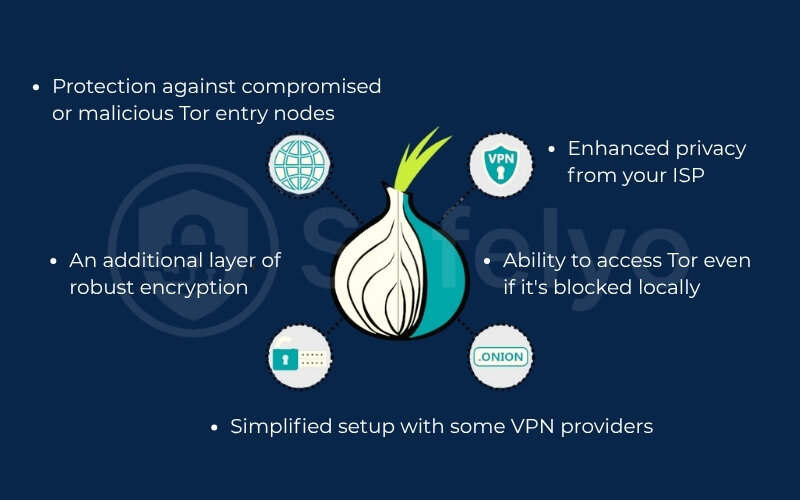
Combining a VPN with the Tor network in an Onion over VPN setup isn’t just a technical exercise; it offers several tangible advantages for users seeking enhanced online privacy and anonymity. Here are the key benefits of using Onion over VPN:
Enhanced privacy from your Internet Service Provider (ISP)
This is often the primary motivator. With Onion over VPN, your ISP cannot detect that you are using the Tor network. They will only see an encrypted connection to a VPN server. This is crucial because some ISPs may monitor, throttle (slow down), or even block direct connections to known Tor relays. By routing through a VPN first, your Tor usage becomes invisible to your ISP, helping you avoid potential surveillance or interference.
>> You may also be interested in: Can my ISP see my browsing history? And how to become invisible
Protection against compromised or malicious Tor entry nodes
The Tor network is run by volunteers, and while most are well-intentioned, there’s always a theoretical risk of an entry node (the first Tor relay your traffic hits) being compromised or operated by an untrustworthy entity. In an Onion over VPN setup, your real IP address is already hidden by the VPN before your traffic enters the Tor network. So, even if an entry node were malicious, it would only be able to log the IP address of your VPN server, not your actual home IP. This adds a significant layer of protection.
Ability to access Tor even if it's blocked locally
In some countries with strict internet censorship, or within certain restrictive networks (like corporate or university networks), direct access to the Tor network might be actively blocked. A VPN can help you bypass these blocks. By first connecting to a VPN server (ideally one in a country with no such restrictions), you can then access the Tor network freely through that encrypted VPN tunnel.
An additional layer of robust encryption
Your data benefits from double encryption. First, it’s encrypted by the VPN between your device and the VPN server. Then, it’s further wrapped in Tor’s multiple layers of encryption as it traverses the Tor network. While Tor’s encryption is strong on its own, this initial VPN encryption ensures your traffic is protected even before it reaches the Tor network.
Simplified setup with some VPN providers
While you can manually set up Onion over VPN, some leading VPN providers (like NordVPN or Proton VPN, for example) have integrated this feature directly into their applications. This often means you can enable Onion over VPN with just a single click, selecting a specialized server that automatically routes your traffic through Tor. This makes a potentially complex setup much more accessible to everyday users.
Note
However, it’s important to remember that not all VPN services offer this convenient feature. Always choose a reputable provider with a clear commitment to user privacy, ideally backed by independent audits.
These benefits collectively answer “Why would someone use Onion over VPN?” and affirm that “Is Onion over VPN good for privacy?” So it’s YES, for many scenarios, it significantly is.
Based on reports from the Tor Project, some ISPs globally do attempt to identify or degrade Tor connections; Onion over VPN is an effective countermeasure.
For instance, imagine a journalist investigating sensitive topics in a country with heavy internet surveillance. Using Onion over VPN helps them hide their Tor usage from local ISPs (avoiding immediate red flags) and protects their true IP from potentially compromised Tor nodes, allowing them to research more safely.
5. When should you use Onion over VPN?
While Onion over VPN offers powerful privacy enhancements, it’s not a one-size-fits-all solution for every online activity. Understanding when to use Onion over VPN is key to leveraging its strengths effectively without unnecessary drawbacks, primarily the significant speed reduction. Here are some scenarios where it truly shines:
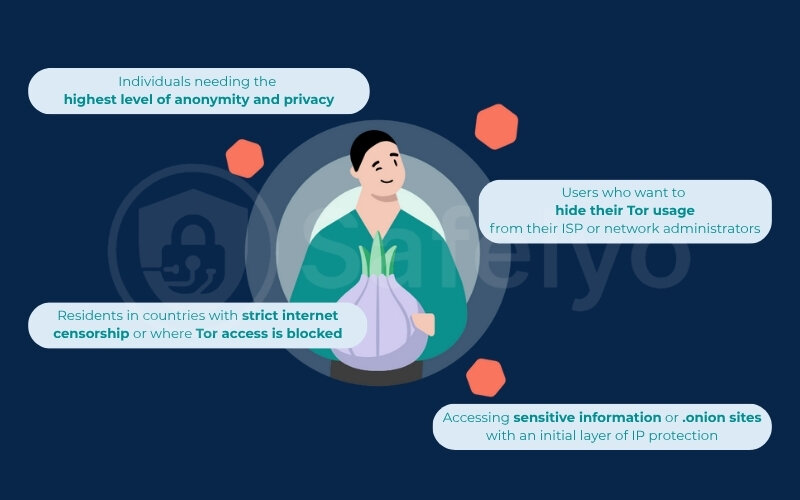
Individuals needing the highest level of anonymity and privacy
This includes journalists working on sensitive investigations, human rights activists operating in oppressive regimes, whistleblowers who need to protect their identity at all costs, or anyone handling highly confidential information where exposure could have severe consequences. For these users, the trade-off in speed is often acceptable for the enhanced anonymity.
Users who want to hide their Tor usage from their ISP or network administrators
If you’re concerned that your Internet Service Provider (ISP), employer, or school network administrator might be monitoring, logging, or even blocking direct connections to the Tor network, Onion over VPN is an excellent solution. It conceals your Tor activity behind the VPN connection, making it appear as regular VPN traffic.
Accessing sensitive information or .onion sites with an initial layer of IP protection
When you plan to explore websites on the Tor network (often called “dark web” sites, identifiable by their .onion addresses), using Onion over VPN provides an initial shield. Your real IP address is protected by the VPN before your traffic even enters the Tor network, offering an extra safeguard against potentially malicious or poorly configured .onion sites or Tor entry nodes.
Residents in countries with strict internet censorship or where Tor access is blocked
For individuals living in regions where internet access is heavily censored or where using Tor directly is forbidden or technically blocked, Onion over VPN can be a lifeline. The VPN can help bypass these governmental or network-level restrictions, allowing access to the Tor network and the wider, uncensored internet.
It’s crucial to note that for everyday online activities like casual web browsing, streaming videos, online shopping, or gaming, using Onion over VPN is generally overkill. The significant slowdown in connection speed will likely lead to a frustrating experience without providing a proportionate benefit for these common tasks.
As I often advise, it’s about choosing the right tool for the job. For instance, a security researcher on our team might use Onion over VPN when analyzing threats on dark web forums to protect both personal identity and our organization’s network, but they wouldn’t use it for routine email checks.
6. How to set up and use Onion over VPN safely
Setting up and using Onion over VPN can significantly boost your privacy, but it’s essential to do it correctly and follow safety best practices. While this guide focuses on “what is” Onion over VPN, here are the general principles for a safe Onion over VPN setup and how to use Onion over VPN effectively.
Prerequisite: Choose a reputable VPN provider
This is the most critical first step. Your entire Onion over VPN setup hinges on the trustworthiness of your VPN provider. Since they are the first point of contact for your traffic and know your real IP address, you must select a provider with:
- A strict, independently audited no-logs policy: This ensures they don’t keep records of your online activity.
- Strong encryption standards (like AES-256).
- A good reputation within the privacy community.
- Ideally, integrated Onion over VPN support if you prefer a simpler setup.
I always recommend users thoroughly research VPN reviews, consider the company’s jurisdiction, and look for transparency reports before committing to a service.
6.1. Method 1: Using VPNs with a built-in Onion over VPN feature
This is the easiest approach, especially for beginners. This method is the most straightforward, designed for users who want convenience and minimal technical fuss. Several top-tier VPN providers integrate Onion over VPN functionality directly into their applications, making a complex setup accessible with just a few clicks.
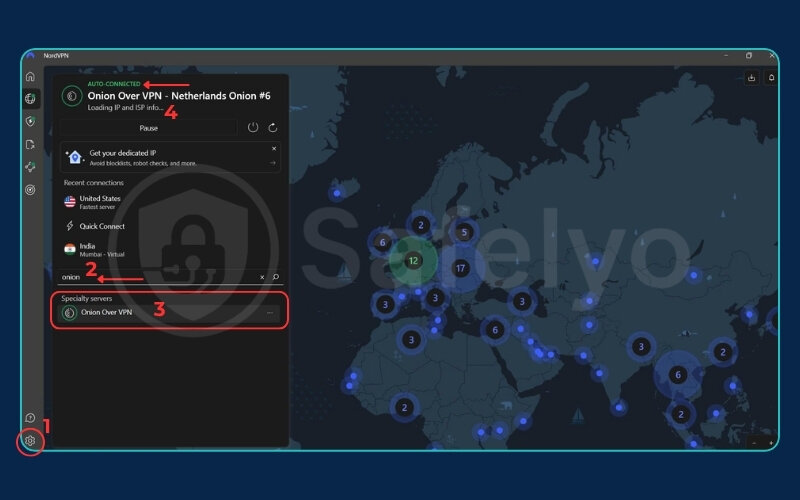
QUICK GUIDE:
Open your VPN application > Locate the “Onion over VPN” or “Tor over VPN” server/feature > Click to connect.
→ Your traffic is now automatically routed.
From my perspective at Safelyo, this built-in method is a game-changer for usability. It removes nearly all the technical barriers. Thế are the detailed steps:
- Launch your VPN client: Ensure you are logged into your account on a VPN service that explicitly offers this feature (e.g., NordVPN’s “Onion Over VPN” servers, Proton VPN’s “Tor over VPN” servers).
- Navigate to server list/features: Within the VPN application, look for a specialized server category or a specific feature toggle for Onion/Tor over VPN. This location varies by provider.
- Select and connect: Choose the Onion over VPN server or enable the feature. The VPN client will then establish a connection to one of its servers, which is pre-configured to route your traffic through the Tor network.
- Verification (Optional but Recommended): Once connected, you can open any browser and visit an IP-checking site (like check.torproject.org) to confirm you are exiting from a Tor IP address.
I’ve tested several VPNs with this feature, and when it works, it’s seamless. The main advantage is simplicity and reduced risk of misconfiguration. However, the downside directly answers part of the question: “Do all VPNs support Onion over VPN?” – NO, so you are limited to the Tor exit nodes chosen by the VPN provider, and not all VPNs offer this. But those that do make it incredibly easy.
6.2. Method 2: Manual configuration (General Steps)
This method offers more control but requires careful execution. You’ll manually establish a VPN connection first, then route your Tor Browser traffic through that VPN tunnel. If your VPN doesn’t have a built-in feature, you can still set it up manually.
QUICK GUIDE:
Connect to your chosen VPN server > Once VPN is active, open Tor Browser > Verify your IP to ensure correct routing
Manually configuring Onion over VPN gives you flexibility with any VPN provider, which is a big plus. The key is meticulousness, especially with IP verification. Follow the detailed steps below:
- Connect to your VPN: Launch your standard VPN application (any reputable VPN will work for this method). Connect to a server in your preferred location. Crucially, ensure this VPN connection is active and stable before proceeding.
- Open Tor Browser: After your VPN connection is established and running, open the Tor Browser Bundle (TBB). Because the VPN is already routing all your devices’ traffic, the Tor Browser’s traffic will naturally pass through this VPN tunnel first. This is where you need the Tor browser for Onion over VPN to handle the “Onion” part.
- (Crucial) Verify your connection and IP address: This step is non-negotiable for manual setups. Open a tab in Tor Browser and navigate to an IP-checking website (e.g., ipleak.net, check.torproject.org). You are looking for two things:
- The IP address shown should belong to a Tor exit node.
- The IP address should not be your real IP, nor should it (ideally, for maximum confirmation) be the IP of the VPN server you directly connected to (though this is harder to ascertain without knowing all Tor exit IPs). The key is that it is a Tor exit.
It’s slightly more involved, but a solid option if your chosen VPN lacks a built-in feature. You have more control over your VPN server choice, but also more responsibility for the correct setup.
I’ve used this method countless times. The biggest pitfall I’ve seen users encounter is forgetting to connect the VPN first or failing to verify their IP, potentially exposing their real IP to the Tor network if the VPN drops unexpectedly.
Key safety precautions when using Onion over VPN:
- Keep software updated: Always use the latest versions of your VPN client and the Tor Browser to benefit from the newest security patches.
- Be cautious with websites: Exercise extreme caution, especially on .onion sites. They can host malicious content or phishing scams. Avoid clicking suspicious links or downloading unknown files.
- Avoid logging into personal accounts: Unless absolutely necessary and you understand the risks, refrain from logging into critical personal accounts (email, banking, social media) while using this setup. Correlation attacks, though harder, are not impossible.
- Use strong, unique passwords and 2FA: This is standard advice, but even more critical when seeking high anonymity. Enable two-factor authentication wherever possible.
- Consider a dedicated environment (Advanced): For maximum security, some users run Onion over VPN within a virtual machine (VM) or on a privacy-focused operating system like Tails.
A critical tip from my experience!
Always, always verify your IP address after setting up Onion over VPN, especially with a manual configuration. Use a trusted IP checker to ensure your real IP isn’t leaking. It’s a simple step that can prevent a major privacy blunder.
7. Potential risks and downsides of Onion over VPN
While Onion over VPN offers a significant boost in privacy and anonymity, it’s not without its drawbacks and potential Onion over VPN risks. It’s crucial to approach this technology with a clear understanding of its limitations:
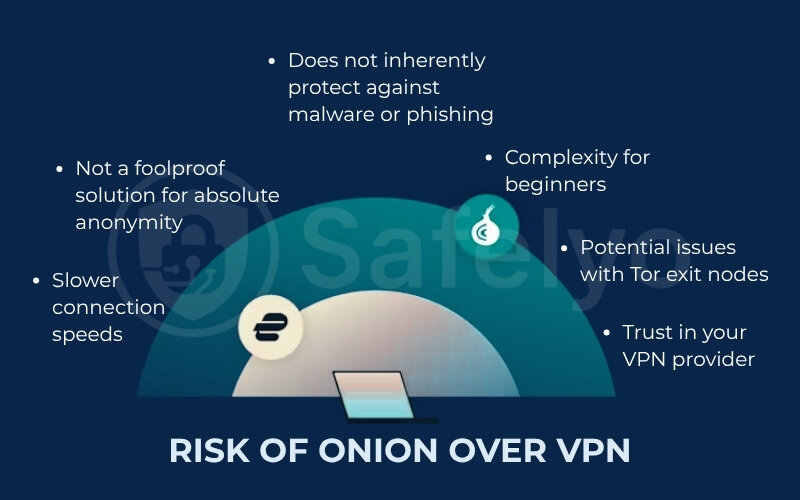
Significantly slower connection speeds
This is almost always the most noticeable downside. Routing your traffic first through a VPN server and then through multiple relays in the Tor network inherently adds latency and reduces bandwidth. Expect a substantial slowdown compared to using just a VPN, just Tor, or no protection at all.
Activities like streaming high-definition video, large file downloads, or online gaming will likely be frustrating or impractical. This directly answers “Does Onion over VPN slow down internet speed?” – Yes, significantly! And the extra hops and encryption layers answer “Why is Onion over VPN slow?”
I’ve personally experienced web pages taking noticeably longer to load, which is the price for the added privacy.
Dependence on and trust in your VPN provider
Although your ISP can’t see your Tor usage, your VPN provider can see your real IP address and knows that you are connecting to the Tor network (even if they can’t see your specific activity within Tor).
This means your anonymity against your VPN provider is not enhanced by this setup. Therefore, choosing a highly reputable VPN provider with a strict, verified no-logs policy is absolutely paramount.
Not a foolproof solution for absolute anonymity
While Onion over VPN makes tracking extremely difficult, no technological solution can guarantee 100% absolute anonymity. Sophisticated adversaries with significant resources (like certain state-level actors) may employ advanced techniques such as traffic correlation attacks (though harder with the VPN layer) or exploit undiscovered vulnerabilities.
User error, like misconfiguration or practicing unsafe browsing habits, can also undermine anonymity. So, to answer “Is Onion over VPN truly anonymous?” – it provides a very high degree of anonymity, but “truly” or “perfectly” is an overstatement for any tech.
Potential issues with Tor exit nodes
This is an inherent characteristic of the Tor network itself. Tor exit nodes are the final relays that send your traffic to the open internet. These nodes can be monitored, or worse, operated by malicious entities.
While Onion over VPN protects your real IP from these exit nodes (they’ll see the VPN’s IP as the entry to Tor, or a Tor internal IP), any unencrypted data (e.g., browsing HTTP sites instead of HTTPS) you send or receive can still be intercepted or modified by a malicious exit node. Always prioritize HTTPS.
Complexity for beginners (if not using integrated VPN solutions)
If your chosen VPN doesn’t offer a simple, one-click Onion over VPN feature, the manual setup, while straightforward with guidance, can still be a bit complex for complete beginners. Ensuring the VPN is connected before Tor and verifying the IP address correctly requires attention to detail.
Does not inherently protect against malware or phishing
It’s important to understand that Onion over VPN is a privacy and anonymity tool, not an antivirus or anti-phishing solution. This answers the very common question: “Does Onion over VPN protect against malware?” – not directly.
While it might indirectly reduce risks from IP-targeted attacks, you can still download malware or fall for phishing scams if you’re not careful. Always use robust security software alongside it.
One common mistake I’ve seen is users becoming complacent. They enable Onion over VPN and assume they’re invincible, then neglect basic security hygiene like using strong, unique passwords, keeping software updated, or being wary of suspicious links. Technology is a powerful tool, but it’s not a substitute for cautious online behavior.
8. Onion over VPN vs. VPN over Tor
When discussing combining VPNs and Tor, you’ll inevitably encounter two main configurations: Onion over VPN (which we’ve been focusing on, also called Tor over VPN) and its counterpart, VPN over Tor.
Understanding the distinction is crucial, as they offer different security models and are suited for different purposes. So, what is the difference between Onion over VPN and VPN over Tor? Let’s break them down side-by-side:
| FEATURE | TOR OVER VPN | VPN OVER TOR |
| Connection Order | Your Device → VPN Server → Tor Network → Internet | Your Device → Tor Network → VPN Server → Internet |
| What ISP Sees | Encrypted connection to VPN server (Tor uses a hidden service) | Connection to the Tor network (VPN uses hidden) |
| What VPN Sees | Your real IP address reveals that you’re connecting to Tor | Connection from a Tor exit node IP (real IP hidden) |
| What Tor Entry Sees | VPN server’s IP address (real IP hidden) | Your real IP address (Major Risk!) |
| Main Advantage | Hides Tor use from ISP; protects real IP from Tor entry | Hides real IP from VPN provider |
| Main Disadvantage | Must trust the VPN provider | ISP sees Tor use; real IP exposed to Tor entry |
| Setup Complexity | Low to Moderate | High |
| Speed Impact | Significant slowdown | Potentially even slower |
| Primary Use Case | General enhanced privacy, hiding Tor use from the ISP | Niche: Hiding real IP from VPN, bypassing Tor blocks |
As I’ve observed in my work, the vast majority of inquiries and practical applications lean towards Onion over VPN due to its more balanced approach to privacy, security, and usability. VPN over Tor introduces complexities and risks that often outweigh its benefits for the average user.
Which is better at the end, Onion over VPN or VPN over Tor?
There’s no single “better” option; it depends entirely on your specific threat model and goals.
- For most users seeking enhanced privacy and to hide their Tor usage from their ISP, Onion over VPN is generally the recommended, safer, and easier-to-implement choice.
- VPN over Tor is a more specialized setup with significant risks (IP exposure to Tor entry nodes) and greater complexity. It’s typically only considered by advanced users with very specific needs who understand and can mitigate the risks.
9. Onion over VPN vs. Double VPN
Another common question when exploring advanced privacy setups is how Onion over VPN vs Double VPN compares. Both aim to provide more security than a standard single-VPN connection, but they achieve it through very different mechanisms and cater to slightly different needs.
First, let’s briefly define Double VPN (also known as Multi-hop VPN). This is a feature offered by some VPN services where your internet traffic is routed through two different VPN servers (often in different geographical locations) instead of just one. The traffic is encrypted at your device, sent to the first VPN server, re-encrypted (or passed through another encrypted tunnel), sent to the second VPN server, and then out to the internet.
It’s important to clarify that Is Onion over VPN the same as Double VPN? No, they are distinct. Now, let’s compare them:
| Feature | Onion over VPN | Double VPN (Multi-hop VPN) |
| Core Technology | VPN + Tor Network (decentralized relays) | VPN + Another VPN Server (centralized, same provider) |
| Connection Flow | Device → VPN Server 1 → Tor Relays → Internet | Device → VPN Server 1 → VPN Server 2 → Internet |
| Primary Goal | Maximize anonymity, hide Tor usage from ISP | Enhance IP obfuscation & add encryption layer |
| Anonymity Level | Generally higher (due to Tor’s nature) | Good, but relies on a single VPN provider’s trust |
| Security/Trust | Relies on VPN + Tor network (exit node risk) | Relies entirely on the single VPN provider |
| Speed Impact | Significant slowdown (Tor is slow) | Moderate slowdown (faster than Onion over VPN) |
| ISP Visibility | Sees connection to VPN Server 1 | Sees connection to VPN Server 1 |
| Complexity | Moderate (easy if VPN has built-in feature) | Very Easy (usually a one-click feature in VPN app) |
| Use Cases | High-risk anonymity needs, accessing Tor discreetly | Enhanced IP protection, added security layer |
And after all, Onion over VPN vs Double VPN: Which is more secure?
This is a nuanced question. “More secure” depends on what threats you’re prioritizing:
- For Anonymity: Onion over VPN generally offers a higher potential for anonymity due to the decentralized nature of Tor and its complex routing. It’s designed to make it extremely difficult to trace activity back to the source.
- For Trust & Control (Potentially): If you deeply trust your VPN provider (verified no-logs, strong reputation), Double VPN might feel more “controlled” because the entire chain is managed by one entity. You don’t have the “wild card” element of unknown Tor volunteers. However, this is also its single point of failure.
- Against ISP Snooping: Both hide your ultimate destination, but Onion over VPN specifically hides your use of Tor.
- Against VPN Provider Compromise: Neither protects you if your primary VPN provider (in Onion over VPN) or the sole provider (in Double VPN) is untrustworthy or compromised regarding your initial connection.
From my experience, the choice often comes down to this:
- If your absolute top priority is the highest possible level of anonymity and accessing the Tor network discreetly, and you can tolerate very slow speeds, Onion over VPN is the stronger candidate.
- If you want an extra layer of IP obfuscation and encryption with better performance than Onion over VPN, and you have high trust in your VPN provider, Double VPN is a more practical choice for everyday enhanced security.
It’s not about one being definitively “better” in all aspects, but which one aligns best with your individual needs and risk assessment.
10. FAQ about Onion over VPN
Here are some common questions people ask about Onion over VPN, along with concise answers.
Is Onion over VPN safe to use?
Onion over VPN significantly enhances privacy and anonymity compared to using just a VPN or Tor alone, making it “safer” in that regard. It protects you from your ISP seeing your Tor usage and hides your real IP from Tor entry nodes. However, no solution is 100% foolproof. Its overall safety depends on choosing a reputable VPN provider, correct configuration, and your own cautious online behavior. Remember, it doesn’t protect against all threats like malware or phishing if you’re not careful.
Is using an Onion over a VPN illegal?
In most countries, using Tor and VPNs for legitimate purposes is perfectly legal. However, any illegal activities performed while using these tools remain illegal. Some countries may have restrictions or outright bans on VPNs or Tor, so it’s always wise to be aware of your local laws. Safelyo emphasizes that these tools should be used responsibly and in compliance with applicable regulations. Using Tor with a VPN is not accurate phrasing for most democratic nations; the tools themselves are not illegal, but how you use them can be.
Can Onion over VPN be tracked or traced?
Onion over VPN is designed to make tracking and tracing extremely difficult. Your ISP can’t see that you’re using Tor, and your real IP is hidden from the Tor network. However, highly resourceful adversaries (like some government agencies) might employ sophisticated traffic analysis or other de-anonymization techniques in specific, targeted scenarios. Also, if your traffic is unencrypted (HTTP) after leaving the Tor exit node, that specific data could be visible to the exit node operator or others on that path. So, while very hard, it’s not impossible to be tracked with Onion over VPN in all circumstances.
Can I use Onion over VPN for torrenting?
Technically, you might be able to, but it’s generally not recommended for torrenting. Connection speeds with Onion over VPN are usually very slow, which is unsuitable for downloading large files, typically of torrents. Furthermore, heavy P2P traffic can strain the volunteer-run Tor network, which is primarily intended for anonymity and censorship circumvention, not bulk file sharing. Many VPNs offer dedicated P2P servers that are a much better choice.
Can I use Onion over VPN for streaming?
Similar to torrenting, using Onion over VPN for streaming is usually not a good idea. The very slow connection speeds will likely result in a poor viewing experience with frequent buffering and low video quality. A standard VPN with fast servers optimized for streaming will provide a far better experience.
How is Onion over VPN different from a regular VPN?
A regular VPN creates an encrypted tunnel between your device and a single VPN server, masking your IP and encrypting your traffic. Onion over VPN takes this a step further: after your traffic goes through that initial VPN server, it’s then routed through the multi-layered, multi-hop Tor network for an additional, deeper level of anonymity.
Do all VPNs support Onion over VPN?
No, not all VPN providers offer built-in, direct support for Onion over VPN in their applications. Some leading VPNs provide specialized servers for this, making it a one-click setup. For other VPNs, you’d need to configure it manually by connecting to your VPN first, then launching the Tor Browser.
Does Onion over VPN hide my IP address?
Yes, Onion over VPN effectively hides your real IP address at multiple points. The website you visit sees the IP of a Tor exit node. The Tor entry node sees the IP of your VPN server. Your ISP only sees you connecting to a VPN server, not your ultimate destination or Tor usage.
How is Onion over VPN different from Tor?
Tor (The Onion Router) is a standalone network and software designed for anonymous internet communication. Onion over VPN is a specific setup method where you use a VPN before connecting to the Tor network. The VPN’s role here is to hide your Tor usage from your ISP and provide an initial layer of IP protection before your traffic enters the Tor network.
What is the purpose of Onion over VPN?
The primary purpose of Onion over VPN is to provide a significantly enhanced level of online privacy and anonymity by combining the strengths of both VPNs and the Tor network. It helps hide your Tor usage from your ISP, protects your real IP from Tor entry nodes, and adds an extra layer of encryption via the VPN.
11. Conclusion
Understanding what is Onion over VPN is a crucial first step towards potentially leveraging its power to protect your online privacy and bolster your anonymity. By intelligently combining the security layer of a VPN with the multi-layered anonymization of the Tor network, this method offers a robust solution for those seeking a high degree of protection in the digital realm.
Here’s a quick recap of the key takeaways from our discussion:
- Definition & Flow: Onion over VPN (or Tor over VPN) first encrypts your traffic via a VPN server, then routes it through the Tor network, effectively hiding your Tor usage from your ISP and your real IP from Tor’s entry points. This is a core part of any Onion over VPN explained guide.
- Key Benefits: Enhanced privacy from ISP, protection from malicious Tor entry nodes, ability to access blocked Tor networks, and an added layer of encryption.
- Primary Downsides: Significantly slower speeds are the most notable, along with reliance on your VPN provider’s trustworthiness and the fact that it’s not a foolproof anonymity solution. Be aware of Onion over VPN risks.
- Use Cases: Best suited for individuals needing maximum anonymity (journalists, activists), those wanting to hide Tor usage, or accessing .onion sites with an extra IP shield. Not for everyday browsing or streaming.
- Key Distinctions: It’s vital to differentiate Onion over VPN from VPN over Tor (different connection order and security implications) and Double VPN (uses two VPN servers from the same provider).
- Safe Setup: Always choose a reputable VPN, keep software updated, and verify your connection, especially with manual setups.
Ultimately, the decision to use Onion over VPN should be a careful one. Safelyo advises you to always weigh your specific security and anonymity needs against the potential performance trade-offs and inherent risks. While it’s a powerful tool, it’s not always the necessary or most appropriate solution for everyone or every situation.
Continue to follow and read articles in the VPN Guides category. Don’t hesitate to leave a comment below this article to share or ask a question to explore more in-depth knowledge, reviews, and detailed guides on online security tools.