Ever wondered what is P2P VPN and why this term keeps popping up whenever online privacy or file sharing is discussed? In our digital age, knowing how to protect yourself online is crucial. But let’s be honest, ‘P2P VPN’ can be a real head-scratcher because, well, it’s a bit of a shapeshifter – it can mean a couple of different things!
I’ve spent years deep in the world of cybersecurity, and believe me, this term causes more “aha!” (or “huh?”) moments than most. It’s not just tech jargon; understanding it can genuinely impact your online safety. Too often, I’ve seen people either miss out on benefits or misunderstand risks simply because the term “P2P VPN” wasn’t clearly explained.
This guide is here to cut through the confusion. You’ll discover:
- The simple meaning behind “P2P” (peer-to-peer) networks.
- The two main interpretations of “P2P VPN” – and why the difference matters.
- How VPNs optimized for P2P traffic protect you.
- What decentralized P2P VPNs (dVPNs) are and how they aim to work.
- The key benefits and safety points to consider for each.
Don’t let confusing tech terms keep you in the dark. Let me walk you through everything you need to know to make sense of P2P VPNs and take control of your online experience, starting now.
1. What is a P2P (peer-to-peer) network?
Alright, before we dive deeper into the “VPN” part of “P2P VPN,” let’s get a clear picture of what a P2P network actually is. Think of it like a neighborhood potluck where everyone brings a dish to share directly with each other, instead of ordering from a central restaurant.
In technical terms, a P2P network definition refers to a system where individual computers, known as “peers,” connect and share resources (like files or bandwidth) directly with one another. There’s no central big boss computer (server) dictating everything.
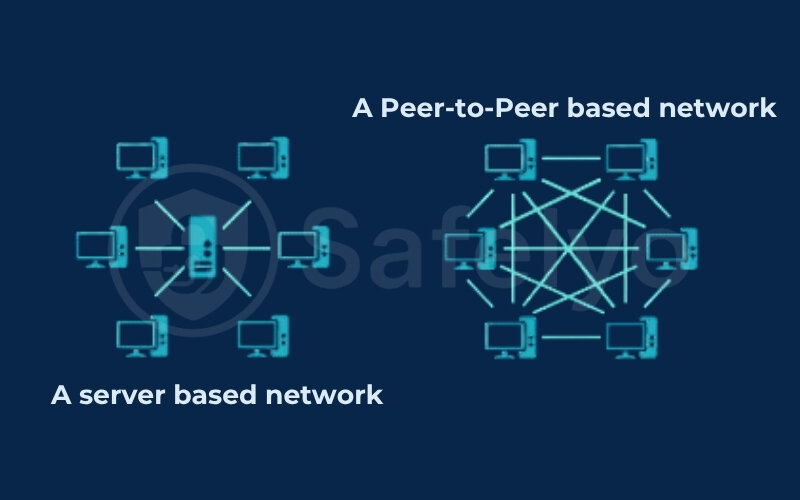
This is quite different from the traditional “client-server” model you might be more familiar with. Imagine browsing a typical website: Your computer (the client) requests information from the website’s main computer (the server). In a P2P setup, each computer can act as both a client and a server. This direct connection model gives P2P networks some cool characteristics:
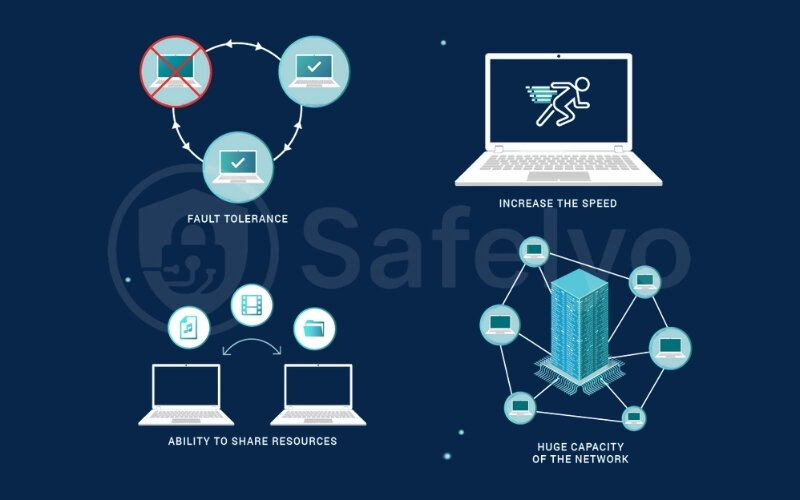
- Decentralized: No single point of control or failure. If one peer goes offline, the network can often still function.
- Scalable: As more peers join and contribute resources, the network can often handle more traffic and data.
- Resilient: They can be harder to shut down because there’s no central hub to target.
You’ve likely encountered P2P technology without even realizing it. The most famous example is BitTorrent, used for sharing large files. Older versions of Skype also used P2P for calls, and many cryptocurrencies like Bitcoin rely on P2P networks to validate transactions and maintain the blockchain.
1.1. How P2P networks function
So, how do these “peers” in a P2P network actually find each other and share stuff without a central coordinator? It’s a bit like trying to find fellow fans of an obscure band in a big city – you need some way to connect.
Typically, P2P networks use a few clever methods:
Discovery mechanisms
When you join a P2P network, your device needs to announce its presence and find other active peers.
In the world of torrents, for example, this often involves a “tracker.” A tracker is a special server (ironically, a bit of a centralized component in an otherwise decentralized system) that keeps a list of peers sharing a particular file. Your torrent client contacts the tracker to get a list of other users (peers) who have the file (or parts of it) you want.
Other P2P systems might use more decentralized discovery methods, like broadcasting messages to nearby nodes or using distributed hash tables (DHTs) where information about peers is spread across the network itself.
Direct data exchange
Once peers find each other, they can establish direct connections. If you’re downloading a file, your device can simultaneously fetch different pieces of that file from multiple peers. This is what makes P2P downloads, like torrents, often very fast – you’re not relying on a single source.
Peers as both clients and servers
This is a core principle. As you download parts of a file, you also typically start sharing (uploading) the pieces you’ve already received with other peers who need them. So, each peer contributes to the network by both taking and giving.
From my experience, many people first encounter P2P through file-sharing applications. The magic of watching a large file download quickly, with bits and pieces flying in from various users across the globe, is a pretty direct demonstration of P2P power. It’s this simultaneous download and upload capability that makes the system efficient.
1.2. Common examples of P2P applications
Now that we know how P2P networks generally operate, let’s look at some common places you’ll find this technology in action. It’s more widespread than you might think.
File sharing
This is the big one. Applications like BitTorrent (with clients such as qBittorrent, uTorrent, Transmission) are prime examples. They allow users to share large files (movies, software, music, documents) by breaking them into small pieces and distributing them among many users.
The efficiency here is key. Distributing a massive operating system update, for instance, is much faster via P2P than from a single server. Older platforms like eMule and Kazaa also used P2P.
Communication platforms
While many modern messaging apps are centralized, some have P2P elements or alternatives that prioritize direct communication. Early versions of Skype famously used P2P for voice calls, reducing reliance on central servers. Some secure messaging apps explore P2P to enhance privacy and resist censorship, though this is less common in mainstream apps today.
Cryptocurrencies
Digital currencies like Bitcoin and Ethereum are built on P2P networks. Transactions are broadcast to the network, verified by multiple participants (miners or validators), and added to a distributed public ledger (the blockchain). This P2P nature is crucial for their decentralization and security, as no single entity controls the currency.
- Decentralized streaming platforms
Though still an emerging area, some platforms are experimenting with P2P to stream video content. The idea is that viewers also help distribute the stream to others, reducing bandwidth costs for the original broadcaster and potentially improving resilience against takedowns.
The reason P2P is so suitable for these applications often boils down to a few core strengths: efficiency for large-scale data distribution (as seen with BitTorrent), potential for censorship resistance in communication, and the ability to operate without a central point of control or trust (vital for cryptocurrencies). It’s a versatile architecture, even if its most well-known use case is file sharing.
2. What is P2P VPN? Unpacking the two common meanings
So, you’ve heard the term, maybe seen it advertised, and now you’re trying to figure out what is a P2P VPN exactly. You’re not alone!
At Safelyo, I understand that tech terms can be seriously confusing, and “P2P VPN” is a prime example because it’s often used to describe two quite different things. It’s like hearing someone talk about a “bat” – are they referring to the flying mammal or the sports equipment? Context is everything.
To clear things up: If you’re searching for ‘P2P VPN’ because you want to download or share files (like torrents) safely and privately, you’re probably thinking about the first meaning we’ll cover. But, there’s also a more technical, architectural meaning involving how the VPN itself is built. Let’s break down both interpretations of P2P VPN meaning so you get the full P2P VPN explained picture.
2.1. Interpretation 1: VPNs optimized for P2P activities
This is by far the most common way people understand “P2P VPN.” When you see a VPN provider advertising “P2P support” or “P2P-friendly servers,” they’re talking about a traditional VPN service that is specifically set up to handle P2P traffic VPN needs, especially for activities like torrenting and other forms of peer-to-peer file sharing.
Why do you need a special kind of VPN for this? Well, when you’re involved in P2P file sharing (like using BitTorrent), your IP address is typically visible to everyone else sharing that same file. This can expose you to potential privacy risks, monitoring by your internet service provider (ISP), or even copyright trolls. A VPN for P2P file sharing is designed to hide your real IP address and encrypt your connection, making these activities much safer.
It’s important to note that these P2P friendly VPN services still use the standard client-server VPN architecture. You connect to a VPN server owned and operated by the VPN company, and that server then handles your P2P traffic.
The “P2P” part refers to the type of internet activity the VPN is good for, not usually how the VPN network itself is built. So, when you ask what does P2P server means in VPN, it typically means a server designated by the VPN provider as suitable and robust for handling P2P connections.
How do these VPNs support P2P traffic?
So, how does a standard VPN that’s “P2P-friendly” actually help you when you’re, say, downloading a torrent?
- You connect to a P2P-optimized VPN server: You launch your VPN app and select a server that the provider has marked as suitable for P2P.
- Your P2P traffic is encrypted: All data from your P2P application (like your torrent client) is encrypted by the VPN before it leaves your device.
- Traffic is routed through the VPN server: This encrypted traffic travels to the VPN server you connected to.
- The VPN server forwards your traffic to the P2P network: The VPN server then sends your P2P requests out to the internet (e.g., to other peers in a torrent swarm) using its own IP address.
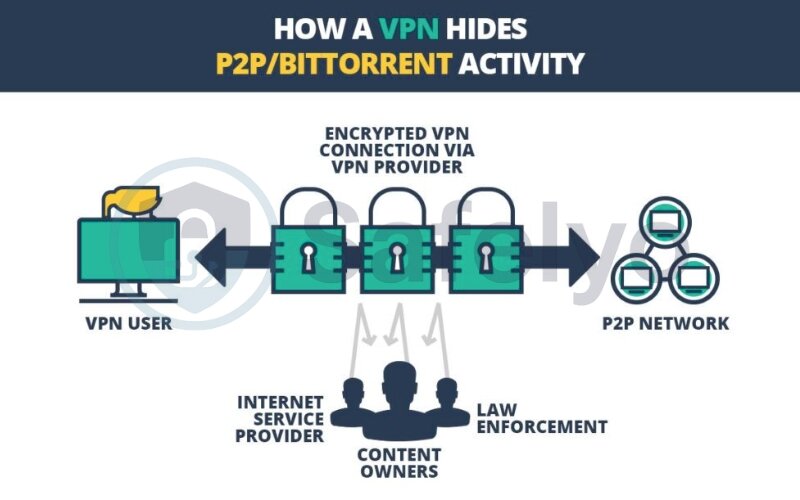
The crucial part here is that your real IP address is hidden from other peers in the P2P network. They only see the IP address VPN of the server. Additionally, your ISP can see that you’re connected to a VPN, but thanks to encryption, they can’t easily tell that you’re specifically engaging in P2P activities or what files you’re sharing. This can help prevent ISP throttling (slowing down your connection) for P2P traffic.
Key features of a P2P-friendly VPN
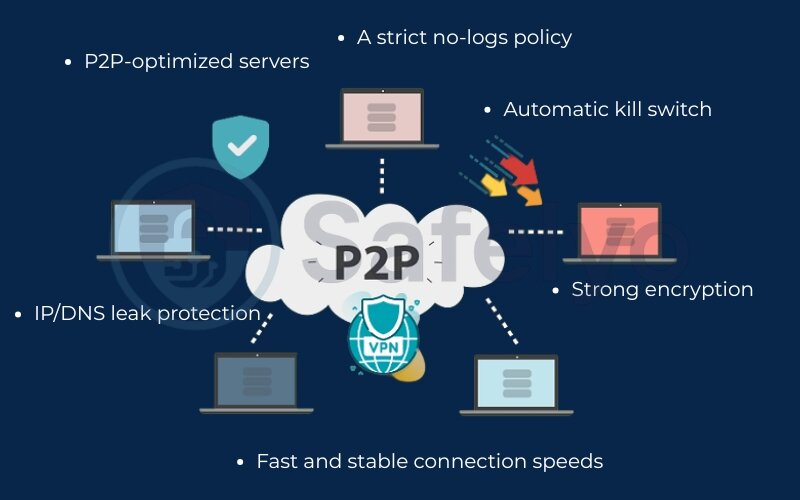
When you’re looking for a VPN to use with P2P activities, certain features are more than just nice-to-haves – they’re essential for your privacy and security. Here’s what a good P2P-friendly VPN should offer:
- P2P-optimized servers: These are servers specifically configured or permitted by the VPN provider to handle the demands of P2P traffic. They often offer better speeds and stability for file sharing. Why it’s important for P2P: Ensures you’re not violating the VPN’s terms of service and usually provides a better experience.
- A strict no-logs policy: The VPN provider should not keep records of your online activity, especially what you download or share. This is critical for privacy. Why it’s important for P2P: If the VPN logs your activity, it defeats a major purpose of using a VPN for P2P privacy.
- Automatic kill switch: This feature blocks your internet access if the VPN connection unexpectedly drops. Why it’s important for P2P: It prevents your real IP address from being accidentally exposed to the P2P network if the VPN disconnects.
- Fast and stable connection speeds: P2P file sharing can be bandwidth-intensive. A fast VPN will minimize slowdowns. Why it’s important for P2P: Slow speeds make downloading and uploading tedious.
- Strong encryption: Robust encryption VPN protocols (like AES-256) are necessary to protect your data from prying eyes. Why it’s important for P2P: Keeps your ISP and other third parties from snooping on your P2P activity.
- IP/DNS leak protection: Ensures that your real IP address or DNS requests don’t leak outside the secure VPN tunnelslow down internet. Why it’s important for P2P: Accidental leaks can expose your identity.
2.2. Interpretation 2: VPNs with a P2P architecture (decentralized VPNs – dVPNs)
Now for the road less traveled. The second, more technical interpretation of “P2P VPN” refers to a VPN that actually uses a peer-to-peer network architecture for its operation. These are often called decentralized VPNs (dVPNs). So, is a decentralized VPN a P2P VPN? Yes, in this context, it absolutely is.
Instead of connecting to a central server owned by a VPN company, users of a dVPN connect to a network of other users (peers) who are also running the dVPN software. Your internet traffic is then routed through one or more of these other peers’ devices before it reaches its final destination. In essence, other users’ devices act as the “VPN servers” in the network.
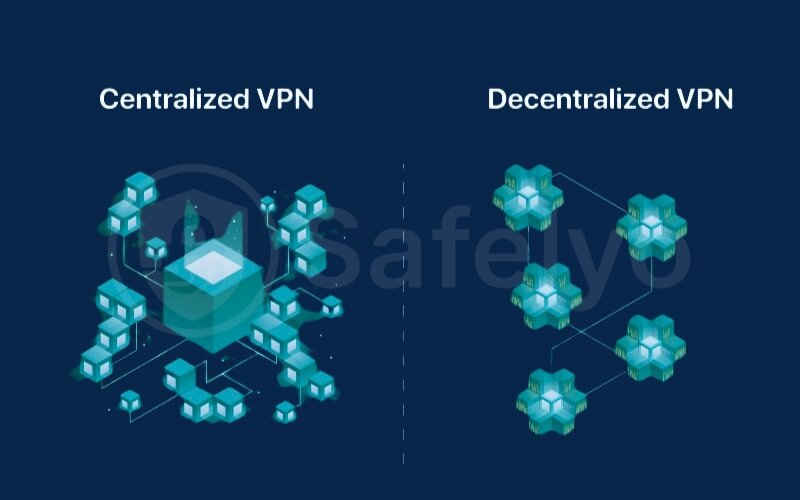
This is a fundamentally different approach compared to traditional VPNs. As some of the more technical resources like Nym.com or Hide.me explain (though we’ll keep it simpler here!), the idea is to distribute the VPN infrastructure across many participants.
This concept is newer and, frankly, less common in mainstream VPN usage, but it’s gaining traction among those particularly focused on censorship resistance and decentralization. I find this area fascinating because it challenges the traditional models of online privacy.
How a decentralized P2P VPN works
It might sound a bit like magic, but the basic idea behind how a decentralized VPN (dVPN) routes your traffic is quite clever:
- Join the network: You install the dVPN software and connect to its network. Your device becomes a “node” or “peer” in this network.
- Share resources (sometimes): In many dVPN models, users contribute resources, like a portion of their bandwidth or their IP address (though this is handled carefully to maintain user privacy), to the network. In return, they get to use the network to route their own traffic.
- Traffic routing through peers: When you want to access a website, your dVPN client encrypts your request and routes it through one or more other peers in the dVPN network. The “exit node” (the last peer your traffic passes through before going to the public internet) then forwards your request to the website.
The key difference here is the absence of a central company controlling the servers. The network is, in theory, run by its users. This means there’s no single entity to compel for user data or to shut down the service by targeting its servers.
The core concept behind dVPNs
So, what’s the big idea driving the development of these decentralized VPNs (dVPNs)? It primarily revolves around a few key goals:
- Enhanced privacy and censorship resistance: By decentralizing the network, dVPNs aim to make it much harder for governments or corporations to block the service or monitor user activity. There’s no single server farm to target.
- Reduced reliance on a single provider: With a traditional VPN, you’re placing a lot of trust in that one company to protect your data and privacy. dVPNs aim to distribute that trust across the network (and often, cryptographic systems) rather than concentrating it in one place.
- Potentially greater anonymity: Routing traffic through multiple, independently operated peer nodes could, in theory, make it more difficult to trace activity back to the original user.
- Community-driven infrastructure: Many dVPNs have a community aspect, where users are not just consumers but also contributors to the network’s operation.
While the ideals are strong, it’s worth noting that dVPN technology is still evolving. Some projects in this space include Orchid, Mysterium Network, and Nym (which offers a mixnet rather than a pure dVPN). The aim is often to create a more resilient and user-controlled alternative to traditional VPNs, though performance and ease of use can sometimes be more variable.
3. How does a P2P VPN work in practice?
We’ve talked about the two main interpretations of “P2P VPN.” Now, let’s get a bit more concrete and look at how does P2P VPN work in terms of the actual user experience and data flow for each type. This should help you visualize what’s happening behind the scenes.
3.1. Mechanism of VPNs supporting P2P traffic
Let’s revisit the first, more common type: A traditional VPN that’s optimized for P2P activities like torrenting.
Here’s a simplified step-by-step of what happens:
- User initiates P2P activity (e.g., starts a torrent download).
- VPN client encrypts P2P data on the user’s device.
- Encrypted data travels to the P2P-optimized VPN server (owned by the VPN provider).
- VPN server forwards P2P traffic to the internet/P2P network using its own IP address, masking the user’s real IP.
- Return P2P traffic goes to the VPN server, is encrypted, and sent back to the user’s device, where the VPN client decrypts it.
From my perspective as someone who has tested countless VPNs, the beauty of this setup is its relative simplicity for the user. You connect to a server, and the VPN handles the heavy lifting of masking your IP and encrypting your P2P communications. The IP address visible to other peers in the swarm is that of the VPN server, significantly boosting your privacy.
Jump to the details now:
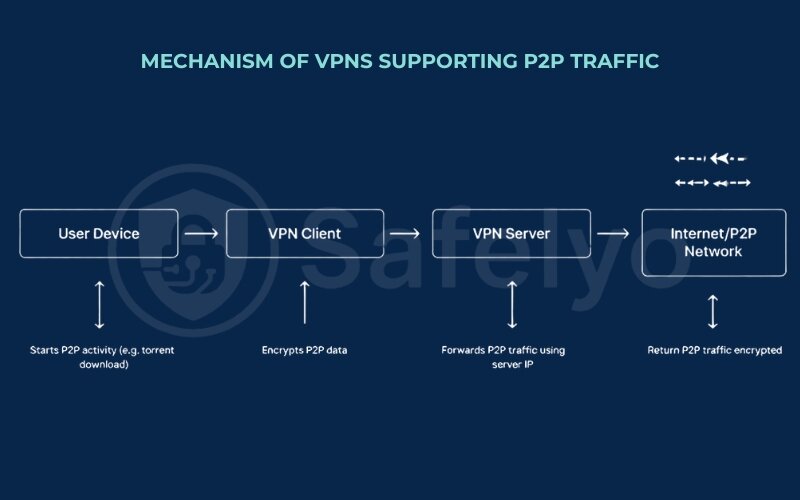
- You start your P2P activity: You fire up your torrent client (like qBittorrent, uTorrent, etc.) and begin downloading or uploading a file.
- The VPN client on your device gets to work: Before any of that P2P data leaves your computer, your installed VPN client (from a provider like NordVPN, ExpressVPN, Surfshark, etc., assuming they offer P2P-friendly servers) encrypts it.
- Encrypted data travels to the VPN server: This encrypted bundle of P2P data is sent through your internet connection to the specific P2P-optimized VPN server you’ve selected in your VPN app. This server is owned and maintained by the VPN company.
- The VPN server decrypts (if necessary for routing) and forwards your traffic: The VPN server receives your encrypted data. It then sends your P2P requests out to the broader P2P network (e.g., connecting to other peers in the torrent swarm). Importantly, it does this using its own IP address, not yours.
- Return traffic is also routed through the VPN: Any data coming back to you from the P2P network first goes to the VPN server, is encrypted, and then sent securely back to your device, where your VPN client decrypts it.
3.2. Mechanism of decentralized P2P VPNs (dVPNs)
Now, let’s switch gears to the more architectural P2P VPN, the decentralized VPN (dVPN). The flow here is quite different because there’s no central company server.
Here’s a general idea:
- User installs dVPN software and connects, becoming a “node” in the peer-to-peer network.
- (Optional) The user’s device may contribute resources (e.g., bandwidth) to the dVPN network.
- The user’s internet traffic is encrypted by the dVPN client and routed through one or more other peer nodes within the dVPN network.
- The “exit node” (final peer in the chain) sends the user’s traffic to its internet destination (e.g., a website), using the exit node’s IP address.
- Return traffic from the internet goes to the exit node, is routed back through the dVPN network (encrypted), and delivered to the user’s device, where the dVPN client decrypts it.
The core idea here is the community-driven or peer-driven nature. The network’s strength, speed, and reliability often depend on the number of active, healthy peers and the specific design of the dVPN.
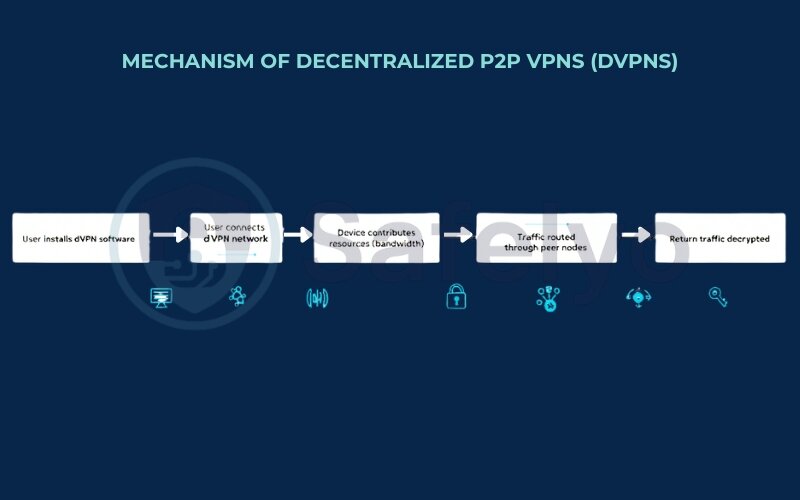
- You install dVPN software and join the network: You download the client software for a specific dVPN service (e.g., Mysterium, Orchid) and connect. Your device now becomes a participant, or “node,” in this distributed network.
- You may contribute resources (optional/varies by dVPN): Some dVPNs operate on a “give-and-take” model. You might share a small portion of your bandwidth or, in some designs, allow your device (with strict privacy safeguards) to act as a relay or exit node for other users’ traffic. In return, you get to use the network. Other dVPNs might involve micropayments for bandwidth usage.
- Your internet traffic is encrypted and routed through other peers: When you browse the web or use an application, your dVPN client encrypts your traffic. This traffic is then “hopped” through one or more other user nodes within the dVPN network.
- The “exit node” sends your traffic to its destination: The final peer in the chain (the exit node) sends your (now typically unencrypted, if it’s standard HTTPS traffic to a website) request to the destination server (e.g., the website you want to visit). The website sees the IP address of this exit node, not your original IP.
- Return traffic follows a similar path back: Responses from the internet come back to the exit node, then get routed back through the dVPN network to your device, being encrypted along the way.
I’ve experimented with a few dVPNs, and while the concept is powerful for decentralization, the user experience can sometimes be less predictable than with traditional VPNs due to this reliance on other users’ connections.
4. Key benefits of using different types of P2P VPNs
So, why go through the trouble of using a P2P VPN, whichever type we’re talking about? Well, there are some significant advantages. Let’s break down the benefits of P2P VPN depending on whether it’s a VPN for P2P traffic or a decentralized P2P VPN.
4.1. Advantages of using a VPN for P2P file sharing
When you’re using a traditional VPN that’s optimized for P2P activities like torrenting, the benefits are primarily focused on enhancing your privacy and security during these specific operations. I’ve seen firsthand how these benefits can make a real difference for users.
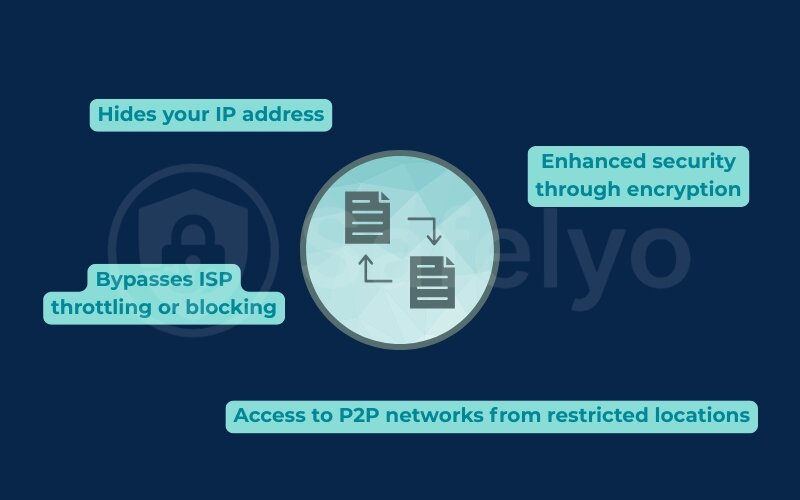
Hides your IP address
This is a big one. Your real IP address is masked from other peers in the torrent swarm, as well as from your ISP and any potential copyright monitors. Instead, they see the IP address of the VPN server. This significantly boosts your anonymity.
Enhanced security through encryption
The VPN encrypts all your P2P traffic. This means your ISP can’t easily see what you’re downloading or sharing, nor can hackers on public Wi-Fi (if you happen to be torrenting there, though generally not recommended without a VPN). It adds a strong layer of protection against snooping.
Bypasses ISP throttling or blocking
Some ISPs don’t like P2P traffic because it can be bandwidth-intensive. They might slow down (throttle) your connection or even block P2P activities altogether. Since a VPN encrypts your traffic, your ISP can’t easily identify it as P2P, allowing you to bypass these restrictions. I’ve heard from many users that their download speeds actually improved with a VPN when their ISP was previously throttling them.
Access to P2P networks from restricted locations
If your school, workplace, or even your country restricts access to P2P networks or torrent sites, a VPN can help you overcome geoblocking by making it appear as if you’re connecting from a different location where these activities are allowed.
For many users, especially those concerned about receiving warning notices from their ISPs or simply wanting to keep their file-sharing activities private, these benefits make using a P2P-friendly VPN a no-brainer.
4.2. Potential advantages of decentralized P2P VPNs (dVPNs)
The potential benefits of dVPNs (the architectural P2P VPNs) are more focused on the principles of decentralization and censorship resistance, though they are often more theoretical or still in development compared to the established benefits of traditional VPNs.
Higher theoretical censorship resistance
Because dVPNs don’t rely on centralized servers owned by a single company, it’s much harder for governments or organizations to block or shut them down. There isn’t one single point of failure or control to target.
Potentially enhanced anonymity and privacy
By routing traffic through multiple, independently operated peer nodes, dVPNs aim to make it more difficult to trace online activity back to the original user. The trust is distributed, not concentrated.
Reduced reliance on a single provider
With a traditional VPN, you’re placing your trust in that one company not to log your data and to maintain good security. dVPNs aim to remove this single point of trust. No single entity has complete control over the network or user data (in theory).
Possibly lower costs (in some models)
Some dVPNs operate on a model where users contribute resources (like bandwidth) to the network and, in return, can use the service for free or at a lower cost than traditional VPN subscriptions. Other models might involve micropayments for bandwidth, which could still be cheaper for light users.
It’s important to remember that dVPN technology is still evolving. While the potential benefits are compelling, particularly for those in heavily censored regions or strong advocates for decentralization, practical aspects like performance, ease of use, and the maturity of the security models are still being refined. I see dVPNs as a very promising frontier, but one that still has some way to go to match the user-friendliness of top-tier traditional VPNs.
5. Are P2P VPNs safe and legal to use?
This is often the million-dollar question, especially since “P2P” is so closely associated with torrenting, which sometimes treads into legally gray areas. So, is P2P VPN safe, and is it legal? The short answer is: It depends on how you use it and the type of P2P VPN we’re discussing. Let’s untangle this.
5.1. Safety considerations for P2P file sharing with a VPN
When we’re talking about using a traditional VPN (Interpretation 1) for P2P file sharing, the VPN itself significantly increases your safety. Here’s why and what to watch out for:
- IP address protection: A good P2P-friendly VPN hides your real IP address from other peers in the swarm. This is a major safety boost, protecting you from direct targeting or identification.
- Encryption: Your P2P traffic is encrypted, making it unreadable to your ISP or anyone else trying to snoop on your connection.
- The VPN’s quality matters: Your safety heavily relies on the VPN provider.
- No-logs policy: Essential. If the VPN logs your activity, it compromises your privacy.
- Kill switch: Crucial. If the VPN connection drops, a kill switch cuts your internet to prevent your real IP from leaking.
- Leak protection (IP/DNS leak): Prevents accidental exposure of your identifying information.
- Beware of the files themselves: This is a big one. A VPN protects your connection, not your computer, from malicious files. If you download a file containing malware or a virus via P2P, the VPN won’t stop that infection. While a good VPN significantly boosts your safety during P2P activities, Safelyo always advises users to also practice caution with the files they download and use reliable antivirus software.
So, is torrenting with a VPN safe? Yes, much safer than without one, provided you choose the best VPN for torrenting, which is reputable with the right features, and remain cautious about what you download.
5.2. Security aspects of decentralized P2P VPNs (dVPNs)
For decentralized VPNs (dVPNs – Interpretation 2), the security model is different, bringing its own set of potential advantages and risks:
- Potential for enhanced privacy (in theory): The decentralized nature, with traffic routed through multiple peers, can make it harder to trace activity back to a single user. No central point has all the information.
- Risk from exit nodes: This is a significant concern. The “exit node” is the peer whose internet connection your traffic uses to access the public internet. If this traffic isn’t encrypted (e.g., if you’re visiting an HTTP site instead of HTTPS), the operator of that exit node could potentially see your unencrypted data. Reputable dVPN designs try to mitigate this, but it’s an inherent challenge.
- Network reliability and peer integrity: The security and performance can depend on the other users in the network. A malicious peer could theoretically try to disrupt traffic or, in poorly designed systems, compromise data.
- Maturity and audits: Many dVPN projects are newer and may not have undergone the same rigorous independent security audits as established commercial VPNs. This isn’t always true, but it’s a factor to consider.
I find that the security model of dVPNs is fascinating because it distributes trust. However, this also means users need to be aware that the “links” in the chain are other users’ devices, which introduces different security considerations than relying on a professional company’s dedicated servers.
5.3. Legality of P2P activities and VPN usage
Now for the legal side. This is where it gets nuanced:
- VPNs themselves are legal in most countries: Using a VPN to protect your privacy online is perfectly legal in the vast majority of places around the world. There are a few countries that restrict or ban VPN use, so it’s wise to be aware of your local laws.
- P2P technology itself is legal: Peer-to-peer networking is just a way for computers to communicate. There’s nothing inherently illegal about the technology.
- The content matters: The legal issues arise from what you’re sharing or downloading via P2P. Sharing or downloading copyrighted material (movies, music, software, games) without permission from the copyright holder is illegal in most countries.
- A VPN does not make illegal activities legal: This is a critical point. While a VPN can hide your IP address and encrypt your traffic, making it harder for copyright holders or authorities to track you, it doesn’t change the legal status of copyright infringement. If you use a P2P VPN to download copyrighted material illegally, you are still breaking the law.
Safelyo encourages responsible and legal use of P2P technology and VPNs. While a VPN is an excellent tool for privacy and security, it should be used in compliance with the laws of your jurisdiction and with respect for intellectual property rights. Always be mindful of what you are sharing and downloading.
6. P2P VPN vs. traditional VPN
By now, you’ve probably got a good sense that “P2P VPN” isn’t a single, simple thing. So, how does it stack up against what we typically call a “traditional VPN”? The traditional VPN vs P2P VPN comparison largely depends on which interpretation of “P2P VPN” we’re focusing on.
If “P2P VPN” means a traditional VPN that allows or is optimized for P2P traffic (Interpretation 1), then the core technology is the same as any other traditional VPN. The “difference” is merely in its permitted use cases and potentially some server optimizations.
However, the more significant differences emerge when we compare a traditional VPN to a decentralized P2P VPN (dVPN), which has a P2P architecture (Interpretation 2). This is where the what is the difference between P2P and VPN question (or rather, dVPN and traditional VPN) becomes more distinct.
Let’s break down the key distinctions, primarily focusing on Traditional VPN vs. dVPN (P2P Architecture VPN):
| It can be more variable, depending on peer availability and network health. | Traditional VPN (Client-Server Architecture) | Decentralized P2P VPN (dVPN – P2P Architecture) |
| Server Architecture | Centralized: Relies on servers owned and managed by the VPN provider. | Decentralized: Relies on a network of user-operated peer nodes. |
| Data Routing | User -> VPN Server -> Internet Destination | User -> Peer Node(s) -> (Exit Node) -> Internet Destination |
| Trust Model | Trust is placed in the VPN provider (their policies, infrastructure, etc.). | Trust is distributed across the network participants and/or cryptographic design. |
| Control | The VPN provider has full control over the servers and network. | Control is ideally decentralized among users or governed by protocol rules. |
| Primary Goal | Privacy, security, and bypassing geo-restrictions via the provider’s servers. | Extreme censorship resistance, decentralization, user-controlled network. |
| Performance Stability | Generally, more stable and predictable. | Typically, very user-friendly with dedicated apps. |
| Ease of Use | Typically very user-friendly with dedicated apps. | It can be more complex to set up and use; technology is still evolving. |
| Cost Model | Usually subscription-based. | Can be subscription, pay-per-use (bandwidth), or free (by contributing resources). |
Understanding these differences is crucial for choosing the right tool for your needs. If your main goal is safe torrenting with good speeds, a P2P-friendly traditional VPN is likely your best bet. If your priority is exploring decentralized technologies for maximum censorship resistance, a dVPN might be more appealing, despite potential performance trade-offs.
7. FAQ about P2P VPNs
Here are some common questions people ask about P2P VPNs, with concise answers to help you quickly understand the key points.
Do I need a P2P VPN for torrenting?
Yes, it’s highly recommended. Using a VPN that supports P2P traffic (Interpretation 1) hides your IP address from other users in the torrent network and encrypts your data, significantly boosting your privacy and security.
Is P2P VPN good?
It depends on the type and your needs. VPNs that support P2P traffic (Interpretation 1) are very good for safe and private file sharing. VPNs with a P2P architecture (dVPNs – Interpretation 2) are an emerging technology with strong potential for censorship resistance, but may have variable performance and are generally more technical.
What is the difference between P2P and VPN? (Is P2P itself a VPN?)
P2P (Peer-to-Peer) is a network architecture where devices connect directly. A VPN (Virtual Private Network) is a technology that creates a private, encrypted connection over the internet. P2P itself is not a VPN. However, a “P2P VPN” can refer to a traditional VPN that allows P2P traffic, or a dVPN that uses a P2P architecture to function.
Are P2P VPNs free?
Some free VPNs might allow P2P traffic, but they often come with significant limitations (speed, data caps, weaker security, logging). Some VPNs may offer free tiers if you contribute resources. However, for reliable P2P activity, I generally advise caution with free VPN services and recommend considering reputable paid options.
What does a P2P server mean in VPN?
A “P2P server” in a VPN context (referring to Interpretation 1) is a server owned by the VPN provider that is specifically configured or designated to handle peer-to-peer traffic like torrenting. These servers are typically optimized for better speed, stability, and security for such activities.
8. Conclusion
Understanding what is a P2P VPN is a vital first step towards navigating the online world with greater safety and confidence. As we’ve explored, this term isn’t one-size-fits-all; it can describe a traditional VPN service fine-tuned for P2P activities like torrenting, or it can refer to an innovative decentralized VPN (dVPN) built on a peer-to-peer architecture. Both have distinct characteristics and use cases.
To quickly recap the essentials:
- “P2P VPN” most commonly means a standard VPN that allows and optimizes for P2P traffic (e.g., torrenting), hiding your IP and encrypting data.
- It can also refer to a decentralized VPN (dVPN), which uses a P2P network structure for its operation, aiming for greater censorship resistance.
- VPNs for P2P traffic (Interpretation 1) are crucial for private and secure file sharing.
- dVPNs (Interpretation 2) are an emerging technology with unique benefits like decentralization, but also potential drawbacks in performance and complexity.
- Regardless of the type, always consider the safety features of the VPN service and the legality of your online activities.
Ultimately, whether you’re looking to secure your torrent downloads or explore the frontiers of decentralized networking, a clear understanding of what P2P VPNs are and how they function will empower you to make informed choices. To dive deeper into fundamental VPN concepts and choose the best solution for your needs, explore more articles in the VPN Guides category on Safelyo and check out our other comprehensive guides.