Are you trying to figure out which statement describes a VPN accurately? Think of a VPN (Virtual Private Network) as your personal, encrypted tunnel through the vast, often chaotic, public internet – it’s your essential digital shield. In today’s increasingly complex online world, truly understanding how a VPN protects your data isn’t just a “nice-to-have”; it’s fundamental to your digital safety and privacy.
With years immersed in cybersecurity and helping users navigate the digital landscape, I’ve seen firsthand how confusing jargon can obscure the simple power of a VPN. Many get lost trying to find a clear, concise definition. This isn’t just about a definition; it’s about empowerment. A correct understanding is your first step towards smarter online security choices.
In this guide, you’ll discover:
- The single most accurate statement that defines what a VPN truly is.
- Why is grasping this core statement critical for your online security?
- How to easily identify incorrect or misleading statements about VPNs.
- The nuances behind common claims you hear about VPN capabilities.
Don’t let confusion be a barrier to better online protection. Let me walk you through exactly which statement describes a VPN and what that means for you!
1. Pinpointing which statement describes a VPN accurately
So, you’re on a quest to find that one perfect sentence that nails what a VPN is. It’s important because getting the definition right is the first step to understanding its power. Without a clear “statement,” it’s easy to get lost in the tech jargon or, worse, misunderstand what a VPN actually does for you.
1.1. The core statement
From my experience helping people understand cybersecurity, this statement is widely considered the one that describes a VPN most comprehensively and accurately for anyone new to the concept. It truly captures the essence of which statement describes a VPN effectively.
“A VPN (Virtual Private Network) establishes a secure, encrypted connection (a ‘tunnel’) for your device over a public network (like the internet), allowing you to send and receive data as if your device were directly connected to a private network.”
Let’s break that down, piece by piece, because every word matters:
Virtual Private Network
The “virtual” part means it’s not a physical cable running from your device to a secret server room; it’s created by software. “Private” means it’s for your eyes only (or at least, not for the prying eyes on the public network).
Secure, encrypted connection (tunnel)
This is the magic. Imagine your data is a secret message. Encryption scrambles it into an unreadable code. This coded message then travels through a ” VPN tunnel,” a protected pathway that shields it from anyone trying to peek while it’s in transit. We won’t get bogged down in the deep tech of encryption here, just know it’s like a super-strong, digital lockbox.
Over a public network
This is key. A VPN doesn’t replace your internet connection; it works on top of it. Whether you’re on your home Wi-Fi, a coffee shop network, or mobile data, the VPN uses that existing public connection to create its private one.
As if ... directly connected to a private network
This highlights the seamless experience. Once connected, your device behaves as if it’s on a secure, local network, even if you’re miles away. It offers the security and privacy benefits you’d expect from a private setup.

1.2. Alternative accurate statements often encountered
You might hear other definitions, and many are also correct, just focusing on different angles:
“A VPN is a technology that masks your IP address and encrypts your internet traffic, enhancing online privacy and security.”
This statement is great because it zeroes in on two major benefits or outcomes of using a VPN: Hiding your unique internet address (IP address) and protecting your data flow.
“A VPN extends a private network across a public network.”
This one is very concise and is often used in more technical or networking contexts. It focuses on the architectural aspect – how a VPN creates a private ‘space’ using public infrastructure.
While phrased differently, all these valid statements revolve around the core elements of creating a private, encrypted connection over a public network. They’re all pieces of the same puzzle.
As someone who’s explained VPNs countless times, I find the core statement in 1.1 to be the most encompassing and easiest for beginners to grasp initially.
1.3. Where you might hear or read statements describing a VPN
You’ll bump into various “statements describing a VPN” in all sorts of places. You might see them as questions in IT certification quizzes, splashed across the marketing materials of VPN providers, debated in online forums, or even when you’re trying to explain it to a friend.
Knowing the accurate core statement helps you filter the noise and understand if what you’re reading or hearing truly reflects how a VPN works.
2. Why understanding the correct VPN statement matters
Okay, so we’ve nailed down the core statement that accurately describes a VPN. But why is it so important to really get it? It’s not just about acing a quiz or sounding smart at a (virtual) water cooler. Understanding the correct VPN statement is fundamental to making smart choices about your online life.
2.1. Foundation for informed decisions about online security
When you truly grasp that a VPN “establishes a secure, encrypted connection,” you start to see its practical value. It’s not some vague, magical “internet safety button.” It’s a specific tool with a specific job. This understanding empowers you.
For example, knowing that a VPN creates an encrypted tunnel makes it crystal clear why it’s a lifesaver on public Wi-Fi. You’re not just hoping the coffee shop’s network is secure (hint: it probably isn’t as much as you’d like); you’re actively creating your own secure passage for your data.
This clarity helps you decide when and why to use a VPN, rather than just using it because someone said “it makes you safer.” I’ve seen countless users benefit once this clicks; they start using VPNs more strategically to protect sensitive information during online banking or when handling confidential work files remotely.
2.2. Avoiding misconceptions and unrealistic expectations
The internet is rife with bold claims. If you don’t have a solid grip on the true statement describing a VPN, you’re more susceptible to marketing hype or common myths. You might believe a VPN makes you completely invisible (it doesn’t, as we’ll discuss later) or that any VPN will do the job perfectly (also not true).
Understanding the core definition helps you set realistic expectations. You’ll know what a VPN can achieve – like significantly boosting your privacy and securing your data from common threats – and what it can’t do, like making you immune to all cyber threats or granting you absolute anonymity. This realistic viewpoint is crucial for building a robust, layered security approach.
2.3. Recognizing the value in different VPN features
Once you understand the basic statement – “a secure, encrypted connection over a public network” – the importance of various VPN features becomes much clearer. Suddenly, terms like a “kill switch” (which cuts your internet if the VPN connection drops, preventing data leaks) or a “no-logs policy” (meaning the VPN provider doesn’t store records of your activity) make perfect sense.
You’ll see why these features support the core function of providing a private and secure tunnel. You won’t need to be a tech expert to appreciate them; you’ll understand their value in relation to the primary purpose of the VPN.
While this article focuses on the defining statement, recognizing this connection helps you if you later decide to choose a VPN service. Some industry reports, like those occasionally highlighted by cybersecurity research firms, often point out that users who understand the fundamentals of VPNs are better equipped to select services that genuinely meet their security needs.
3. A simplified example of how a VPN operates
Sometimes, even the clearest statement can benefit from a good analogy. To help you visualize that core “statement describing a VPN” – particularly the “secure, encrypted tunnel over a public network” part.
Now, let’s use a different kind of analogy to illustrate how your actual internet requests are handled when you use a VPN. Imagine you’re in a large library (the internet) and want to request a specific, perhaps sensitive, book (a website or online service).
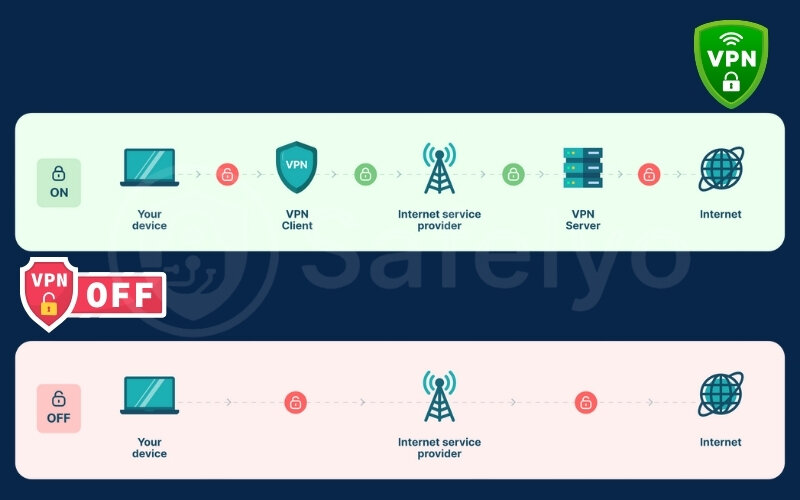
Without a VPN
The Public Librarian
Normally, you walk up to the main librarian’s desk (your Internet Service Provider, or ISP) in the middle of the library. You tell the librarian, out loud, exactly which book you want.
- The librarian (your ISP) hears your request clearly. They know who you are (your IP address) and what book you’re asking for (the website you want to visit).
- They then go get the book for you and hand it over.
- Everyone nearby, if they were listening, could also hear what book you requested. The librarian also keeps a log of all the books you’ve checked out.
This is convenient, but not very private. Your ISP sees all your requests, and potentially, so could others on an unsecured network.
With a VPN
Your Private, Discreet Research Assistant
Now, imagine you hire a private research assistant (the VPN). This assistant has their own private, soundproof office within the library (the VPN server).
- Instead of going to the public library, you go into your assistant’s private office. You tell your assistant quietly and privately which book you want. This communication inside the office is encrypted – no one outside can understand it.
- Your assistant then leaves their private office and goes to the main librarian (the internet’s infrastructure) to request the book. Crucially, the assistant requests the book using their own library card (the server’s VPN IP address), not yours.
- The main librarian gives the book to your assistant, thinking the assistant wants it for themselves. The librarian doesn’t know the request originally came from you.
- Your assistant brings the book back to their private office and gives it to you.
So, what happened differently?
- Your request was hidden: Your ISP (the public librarian in this new scenario, or any snoopers in the “public square” of the internet) only sees you communicating with your research assistant’s office (the VPN server). They don’t see the specific book (website) you ultimately requested from that assistant.
- Your identity was masked: The website you visited (the source of the book) only saw the research assistant’s credentials (the VPN server’s IP address), not yours.
This “private research assistant” effectively creates that “secure, encrypted connection (‘tunnel’) for your device over a public network,” just like our core statement says. It fetches what you need from the internet without broadcasting your identity or your specific requests to your ISP or the websites you visit directly. This is much closer to how a VPN reroutes and protects your actual internet traffic.
4. Incorrect statements that misrepresent VPNs
Now that we have a solid understanding of the correct statement describing a VPN, it’s equally important to tackle the misinformation. The digital world is buzzing with claims about VPNs, and frankly, many of them are misleading or flat-out wrong. Recognizing these incorrect statements is key to not falling for hype or, worse, a false sense of security.
Let’s debunk some common misconceptions. For each one, we’ll see why it’s off the mark and compare it to our accurate understanding.
4.1. Misconception 1
This is probably one of the most pervasive myths. While a VPN significantly boosts your online privacy and anonymity, 100% untraceable anonymity is a very high bar that a VPN alone cannot guarantee.
INCORRECT STATEMENT
A VPN makes all your internet activity 100% anonymous and untraceable.
Why is it wrong? A VPN hides your IP address and encrypts your traffic, which is a huge step. However, other factors can still potentially reveal who you are. These include:
- VPN provider logging: Some VPNs (especially free ones) might keep logs of your activity. If they do, they could theoretically link activity back to you.
- Website cookies and trackers: Websites use cookies and other tracking technologies that can identify you even if your IP is hidden.
- Your own actions: If you log into your Google account or Facebook while using a VPN, well, Google and Facebook know it’s you.
- Malware or browser vulnerabilities: If your device is compromised, a VPN won’t stop that.

The correct perspective
Our core statement says a VPN “establishes a secure, encrypted connection” and allows you to act “as if your device were directly connected to a private network.” It’s about creating a private and secure channel.
Instead of “100% anonymous,” a more accurate statement is: “A VPN significantly enhances your online privacy and anonymity by masking your IP address and encrypting your data.” As I’ve often explained to users, think of it as wearing a very good disguise at a party, not becoming invisible.
4.2. Misconception 2
This is a harmful stereotype that, unfortunately, still lingers. While some people might misuse VPNs, their primary and legitimate purpose is security and privacy.
INCORRECT STATEMENT
VPNs are primarily tools for illegal activities or bypassing copyright.
So, why is it wrong? The vast majority of VPN users are everyday people and businesses seeking to protect themselves online. Legitimate uses abound:
- Securing data on public Wi-Fi (a massive one!).
- Protecting sensitive financial transactions.
- Allowing employees to securely access company networks when working remotely.
- Guarding against ISP tracking and data collection.
- Maintaining privacy from excessive advertiser surveillance.

The correct perspective
From my years in tech, I can assure you that VPNs are essential tools for digital self-defense for law-abiding citizens and responsible organizations. The statement describing a VPN focuses on creating a “secure, encrypted connection,” which is a fundamentally protective measure. Attaching a stigma of illegality misses the entire point of their design.
4.3. Misconception 3
This is a dangerous assumption. While the concept of how a VPN works (as per our definition) is universal, the quality of implementation, features, and trustworthiness varies wildly.
INCORRECT STATEMENT
Any VPN, especially free ones, provides the same level of security as paid ones.
It’s wrong because:
- Security protocols and encryption strength: Not all VPNs use the latest, most secure VPN protocols. Free VPNs might cut corners.
- Logging policies: This is huge. Many free VPNs make money by logging your data and selling it to third parties – the exact opposite of what you want for privacy! Reputable paid VPNs often have strict, audited no-logs policies.
- Server infrastructure: Paid VPNs invest in a robust, fast, and secure server network. Free ones might have overcrowded, slow, or less secure servers.
- Data leaks: Cheaper or poorly configured VPNs can suffer from IP leaks or DNS leaks, exposing your real information.

The correct perspective
Our core statement describes the ideal function of a VPN. A more accurate real-world understanding is: “While all VPNs aim to create a private tunnel, the reliability, security, and privacy assurances differ significantly between providers, with reputable paid services generally offering stronger protections than free alternatives.” Don’t assume all “tunnels” are built equally.
4.4. Misconception 4
These two are often mentioned in the context of online security, but they do entirely different jobs.
INCORRECT STATEMENT
A VPN is a type of antivirus software.
It’s wrong at:
- A VPN secures your internet connection. It encrypts the data traveling between your device and the internet, masking your IP address. It protects data in transit.
- Antivirus software protects your device from malware like viruses, ransomware, and spyware. It deals with threats that are already on or trying to get onto your computer or phone.

The correct perspective
They are complementary, not interchangeable. You really need both for comprehensive security. A better statement is: “A VPN protects your data in transit over the network, while antivirus software protects your device from malicious software; they are distinct but equally important security tools.”
4.5. Misconception 5
It’s true that routing your traffic through an extra server and encrypting/decrypting data can introduce some overhead, potentially slowing things down. However, “always significantly slower” is an overstatement.
INCORRECT STATEMENT
Using a VPN means your internet speed will always be significantly slower.
Let’s pinpoint the wrong sides:
- Quality VPNs: Good paid VPNs invest heavily in high-speed servers and optimized networks. The speed drop can often be minimal, sometimes unnoticeable for everyday browsing.
- Server proximity: Connecting to a VPN server geographically close to you usually results in better speeds.
- ISP throttling: Ironically, in some cases, a VPN can improve speeds if your ISP is throttling (deliberately slowing down certain types of traffic, like streaming or torrents). A VPN encrypts your traffic, so your ISP can’t “see” what you’re doing to throttle it.

The correct perspective
Our core statement about VPNs doesn’t mention speed because it’s a performance factor, not a defining characteristic of the technology itself. A more nuanced statement is: “While a VPN can introduce some latency due to encryption and server routing, modern premium VPNs often minimize speed loss, and in specific scenarios like ISP throttling, may even offer a perceived speed improvement.” Don’t let outdated fears about speed deter you from crucial security.
>> Read more:
5. Other common statements about VPNs
Beyond the outright incorrect statements, there are many common claims about VPNs that aren’t necessarily false, but they require a bit more context or understanding of their nuances.
These statements often highlight a specific benefit or use case, but it’s important to see how they fit into the bigger picture of what a VPN is, as described by our core statement.
Let’s explore some of these.
STATEMENT
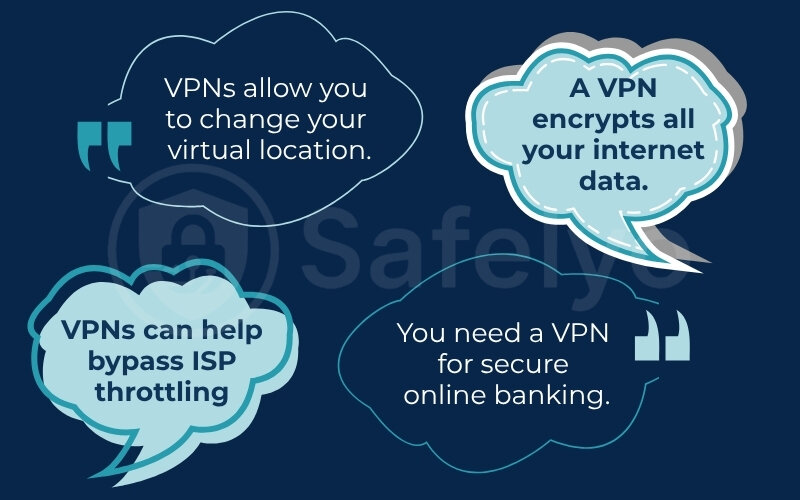
VPNs allow you to change your virtual location.
This is a very popular reason people use VPNs, and technically, it’s true. When you connect to a VPN server in another country, websites and online services will typically see the IP address VPN of that server, making it appear as if you’re browsing from that location.
While accurate, the ability to change your virtual location is a consequence or a feature derived from how VPNs work (routing your traffic through a server elsewhere), rather than its primary defining purpose. The core statement emphasizes creating a “secure, encrypted connection.”
This statement reflects a popular application of VPN technology, directly linked to the core function of routing traffic through a remote server, which inherently masks your original IP and presents the server’s IP. It’s a powerful benefit, especially for accessing geo-restricted content or enhancing privacy, but it’s one outcome of the underlying security architecture.
STATEMENT
You need a VPN for secure online banking.
This is often advised, and for good reason, especially in certain situations. Modern banking websites already use HTTPS, which encrypts the connection between your browser and the bank’s server. So, is a VPN redundant? Not quite.
While HTTPS is crucial, a VPN adds an additional layer of security, particularly if you’re conducting banking on a network you don’t fully trust, like public Wi-Fi. The VPN encrypts all your device’s traffic, not just the browser-to-bank connection, and it hides your IP address from the bank (though they know who you are from your login).
It’s less about “needing” it in the absolute sense on a secure home network, and more about “strongly recommended for enhanced protection” in potentially insecure environments. This statement highlights a key security application of a VPN, reinforcing the “secure, encrypted connection” aspect of our core definition, especially valuable when the underlying public network’s integrity is questionable.
STATEMENT
VPNs can help bypass ISP throttling.
This can be a welcome side effect for some users. ISP throttling is when your Internet Service Provider deliberately slows down certain types of internet traffic (like streaming, gaming, or file-sharing).
A VPN can indeed help with this if the throttling is based on your ISP identifying and targeting specific types of traffic. Since a VPN encrypts your data, your ISP can’t easily see what you’re doing online; they only see encrypted traffic going to a VPN server. This can sometimes make it harder for them to selectively throttle you.
However, it’s not a guaranteed fix. ISPs can also throttle all VPN traffic if they choose, or the bottleneck might be elsewhere. This statement points to a specific benefit derived from the encryption and traffic obfuscation provided by a VPN, which aligns with the “secure, encrypted connection” that masks the nature of your data from your ISP.
STATEMENT
A VPN encrypts all your internet data.
This is generally what a VPN is designed to do, and it’s a cornerstone of its security benefits. When active, it aims to route all internet traffic from your device through its encrypted tunnel.
While this statement is fundamentally true for the traffic passing through the VPN tunnel, there are a few caveats:
- Proper Configuration: The VPN must be correctly configured and working without issues like DNS leaks or WebRTC leaks, which could inadvertently expose some of your data or your real IP address.
- Split Tunneling: Some VPNs offer a feature called “split tunneling.” This allows you to choose which apps or websites use the VPN tunnel and which connect directly to the internet. If split tunneling is active, then not all your data is being encrypted by the VPN.
This statement is very close to the core truth, emphasizing the “encrypted connection” part of the main VPN definition. The nuance lies in ensuring the VPN is functioning optimally and understanding features like split tunneling that might create exceptions. It underscores the importance of the data encryption VPNs provide for overall online privacy.
6. FAQ focusing on VPN statements
Here are some common questions people ask when trying to pin down exactly which statement describes a VPN.
What is the single most important “statement” that accurately describes a VPN for a beginner?
The most important statement is: “A VPN creates a secure, private tunnel for your internet connection over a public network, protecting your data and privacy.” Safelyo believes this captures the essence simply and effectively for anyone starting out.
If a statement says “VPNs use dedicated physical connections,” is it correct?
No, that statement is incorrect. A key part of the correct VPN description is “virtual” connections. VPNs use software to create logical connections over existing public physical infrastructure, not dedicated physical lines for each user.
Why are there so many different “statements” trying to describe a VPN?
VPNs have multiple benefits and technical aspects. Different statements might emphasize different facets like privacy, security, IP masking, or network architecture. However, the core concept of a secure, virtual tunnel over a public network remains central to understanding which statement describes a VPN accurately.
Is the “statement describing a VPN” different for mobile VPNs vs. desktop VPNs?
Yes. For example, a statement like “VPNs make you invisible online” is misleading because while they significantly enhance privacy, true invisibility is nearly impossible. It’s crucial to understand the nuances and what a VPN realistically achieves, which Safelyo aims to clarify.
Can a statement about VPNs be true but still misleading?
Yes. For example, a statement like “VPNs make you invisible online” is misleading because while they significantly enhance privacy, true invisibility is nearly impossible. It’s crucial to understand the nuances and what a VPN realistically achieves, which Safelyo aims to clarify.
7. Conclusion
Hopefully, after journeying through these analyses with Safelyo, you can now confidently identify which statement describes a VPN most accurately and, just as importantly, spot the common misunderstandings. Grasping this core definition isn’t just academic; it’s the bedrock for using VPNs effectively to safeguard your digital life and make informed choices about your online privacy.
Here’s a quick recap of the main takeaways:
- The most precise statement about a VPN emphasizes its role in creating a secure, private, and encrypted connection (a ‘tunnel’) over a public network.
- Many popular “statements” about VPNs can be incorrect or misleading, potentially giving a false sense of security or misrepresenting their capabilities (e.g., claiming 100% anonymity).
- Understanding the correct statement empowers you to appreciate a VPN’s true benefits, set realistic expectations, and recognize the value of its security features.
- Even statements that are technically true often have nuances that are important to understand in the broader context of VPN functionality.
At Safelyo, we’re committed to demystifying technology and empowering you with clear, actionable knowledge. Understanding the fundamental statement that describes a VPN is your first step. To dive deeper into how VPNs work, their benefits, and how to choose the right one for your needs, explore more articles in our VPN Guides category. Take control of your online privacy today!