Can VPN be hacked? Let’s get straight to the point: The honest answer is yes, but not in the way you might see in a Hollywood movie. Many people view a VPN as an invincible digital cloak, a one-click solution to all online threats. The reality, however, is far more nuanced.
In today’s digital world, understanding a tool’s limits is just as crucial as knowing its strengths. A VPN is an incredibly powerful layer of defense for your privacy, but it isn’t a magic force field. Believing it can ironically leave you more vulnerable.
With over a decade spent analyzing real-world cybersecurity incidents, I’ve seen that the biggest breaches often happen not by breaking the unbreakable, but by finding a loose window or an unlocked door nearby. The same principle applies to VPN security.
In this comprehensive guide, I will break it all down for you. You will learn:
- The common ways VPN services are actually compromised.
- The real-world consequences of your VPN’s security failure.
- The warning signs that your connection might be at risk.
- A practical checklist to choose a truly secure, hack-resistant VPN.
Don’t let the “what-ifs” leave you guessing. It’s time to replace uncertainty with knowledge. Let’s dive in and take control of your online security.
1. Can VPN be hacked?
The direct answer lies in how you define “hack.” If you mean breaking the core encryption of a top-tier VPN, the answer is a resounding no, not with today’s technology. Modern VPNs use military-grade encryption like AES-256, which would take the world’s most powerful supercomputers billions of years to crack by brute force.
However, this is where the crucial distinction comes in. When you hear about a “VPN hack,” the attack almost never targets the encryption tunnel itself. Instead, it exploits weaknesses in the ecosystem surrounding the VPN service.

Let’s use an analogy I often share with my clients. Think of a premium VPN as a modern armored car.
Trying to break its AES-256 encryption is like trying to punch through its reinforced steel plating – it’s a futile effort. But a smart thief doesn’t attack the steel. Instead, they might exploit other vulnerabilities: they could attack the garage where the car is stored (a poorly secured VPN server), find a model with a known faulty lock (an outdated VPN protocol), or simply trick the driver into handing over the keys (a user falling for a phishing scam).
So yes, a VPN system can be compromised, but it’s the surrounding elements, not the core encryption, that are the real targets.
2. How VPNs get hacked?
Since attackers can’t just smash through the front door (the encryption), they start rattling the windows and checking for unlocked back doors. From my years of analyzing security setups, a VPN is only as strong as its weakest link, and these weak links can pop up in surprising places.
To make it crystal clear, here’s a simple table I use to quickly assess a VPN’s risk profile.
| Security Factor | High Risk (Easily Compromised) | High Security (Hard to Compromise) |
|---|---|---|
| Protocol | PPTP, L2TP/IPsec | OpenVPN, WireGuard |
| Logging Policy | Log user activity or connection data | Audited No-Logs Policy |
| Leak Protection | No Kill Switch | Kill Switch & DNS Leak Protection |
| Infrastructure | Standard physical servers | RAM-only servers |
Now, let’s look at how these vulnerabilities play out in the real world.
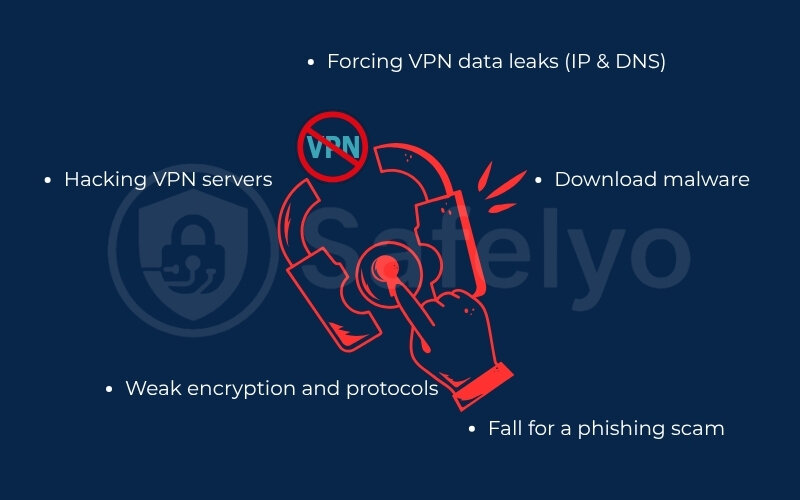
2.1. Exploiting weak VPN encryption and protocols
Whenever I’m asked to review someone’s digital security, the very first thing I check is the VPN protocol they’re using. Using an outdated protocol is like protecting your house with a screen door – it looks like a barrier, but it offers no real resistance.
Protocols like PPTP are from the dial-up era of the Internet. They have well-known flaws that, in the security world, are considered completely broken. A skilled hacker can bypass them with relative ease.
This is why I always insist on modern protocols like OpenVPN or WireGuard. They are the industry’s gold standard, paired with powerful AES-256 encryption. Think of this combination as a solid steel door with a complex, unpickable lock.
2.2. Hacking VPN servers
A VPN provider’s servers are its crown jewels and a huge target for attackers. If a hacker gets into a server, they could potentially see the traffic of everyone connected to it.
I often use the NordVPN incident from 2018 to explain this. It’s a perfect real-world case. The attackers didn’t “break” the VPN’s code. Instead, they found a backdoor into a single server at a third-party data center that wasn’t properly secured by the center’s staff. It was a failure of one component in a massive system. This event was a wake-up call for the entire industry and pushed top providers to adopt much stricter security measures, like using RAM-only servers that wipe all data on reboot.
2.3. Forcing VPN data leaks (IP & DNS)
This is a sneaky one that catches many people off guard. Imagine your VPN tunnel is a solid, opaque water pipe. Your data is the water flowing safely inside. A data leak is like a tiny, pinhole leak in that pipe. The pipe itself isn’t broken, but a little bit of water (your real IP address) can spray out, revealing your location.
This happens with:
- DNS Leaks: Your computer might ask for directions (a DNS request) from your regular ISP out of habit, instead of asking from inside the safe VPN pipe.
- WebRTC Leaks: This browser feature, used for video calls, can sometimes shout out your real IP address past the VPN.
This is why I personally consider a Kill Switch to be a non-negotiable feature. It’s my digital seatbelt – I simply don’t go online on public Wi-Fi without knowing it’s enabled. If the VPN connection ever stumbles, the Kill Switch instantly blocks all internet traffic, ensuring not a single drop of data leaks out.
2.4. User error: The weakest link
From my experience in cybersecurity, I can tell you that the most sophisticated security tool in the world can be defeated by a single, simple human mistake. I’ve seen it time and time again: People with premium VPNs getting compromised because the VPN can’t protect you from, well, you.
Think of it this way: A VPN is like having a bodyguard for your car on the highway.
- If you download malware, that’s like willingly rolling down your window and letting a thief jump inside the car. The bodyguard can’t stop that.
- If you fall for a phishing scam, that’s like a con artist tricking you into telling them where you hide your spare key. The bodyguard sees you hand it over willingly.
A VPN secures your internet connection, but it doesn’t make your device or your decisions immune to threats. It’s a vital part of your security toolkit, but it isn’t the entire toolkit.
3. What happens when your VPN security is compromised
Knowing the “how” is important, but what most people really worry about is the “so what?”. If your VPN’s security does fail, what does that actually mean for you? The consequences range from subtle signs to serious privacy violations. Understanding them helps you recognize a problem early and act fast.
3.1. Signs your VPN is hacked or compromised
A compromised VPN connection isn’t always obvious. In my experience, troubleshooting these issues, the signs are often subtle performance changes that are easy to dismiss. Keep an eye out for these red flags:
- Sudden, persistent slowness: If your internet speed drops to a crawl only when the VPN is on, and this is a new, consistent issue, it could be a sign your traffic is being rerouted or monitored.
- Unusual pop-up ads: A reputable VPN should not be injecting ads into your browser. If you start seeing strange pop-ups, specifically when the VPN is active, it’s a major warning sign.
- Frequent, unexplained disconnects: While any VPN can drop occasionally if your client starts disconnecting and reconnecting constantly without reason, it could indicate an issue with the server’s integrity.
- Suspicious login alerts: If you receive an email from your VPN provider about a login from an unknown location, or alerts from other services (like Google or Facebook) about suspicious activity while you are using the VPN, take it very seriously.
>> You may also be interested in:
3.2. The consequences of a hacked VPN
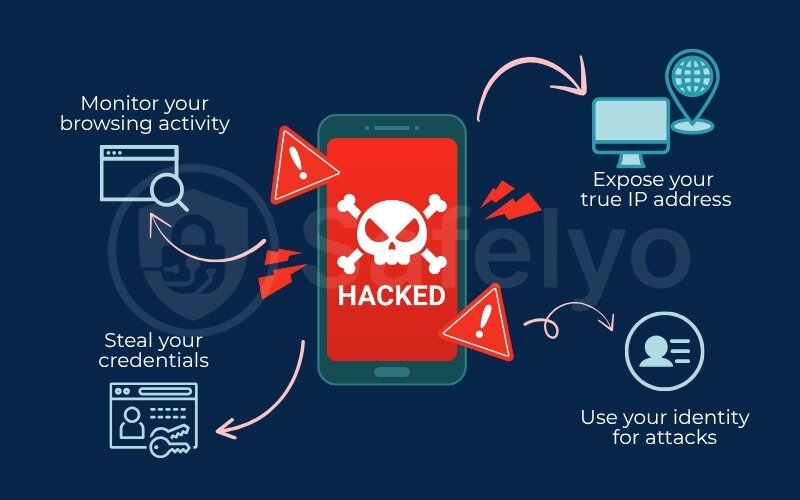
If an attacker successfully compromises your VPN connection or its servers, the protective shield you rely on is gone. Here’s what they could potentially do:
- Monitor your browsing activity: Your web history, the sites you visit, and how long you spend on them could be exposed and logged. The very privacy you sought from your ISP is now in the hands of a malicious actor.
- Steal your credentials: Through a Man-in-the-Middle (MitM) attack, hackers can intercept unencrypted data. If you log into a non-secure (HTTP) website, they could potentially steal your username and password.
- Expose your true IP address: The most basic function of a VPN is to mask your IP. A compromised connection can leak your real IP, stripping away your anonymity and exposing your physical location to websites and third parties.
- Use your identity for attacks: In some cases, your compromised connection could be used as a springboard to launch other attacks, making it appear as if the malicious activity is coming from you.
3.3. What to do immediately after a VPN hack
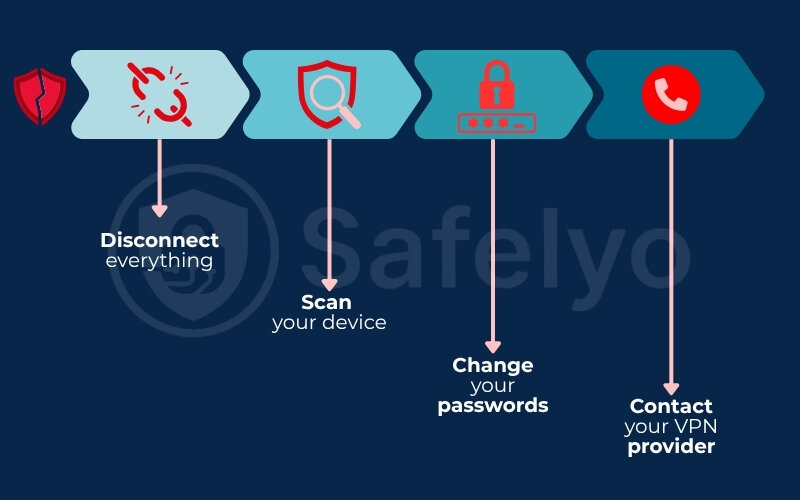
If you suspect your VPN has been compromised, don’t panic. Take a deep breath and follow these steps methodically. The goal is to contain the potential damage and secure your accounts. I recommend this exact sequence:
- Disconnect everything. The first and most critical step. Disconnect from the VPN and then turn off your Wi-Fi or unplug your Ethernet cable. Isolate the device from the internet immediately.
- Scan your device. Run a full, comprehensive scan with a reputable antivirus and anti-malware program. This will help find and remove any malicious software that might have been the root cause.
- Change your passwords. Start with your VPN account password. Then, move on to your most critical accounts: email, banking, and any social media accounts you may have used while the VPN was active. Use unique, strong passwords for each.
- Contact your VPN provider. Reach out to their support team. Inform them of the situation and the server you were connected to. A good provider will take this report seriously and investigate immediately.
4. A security checklist on how to choose a hack-proof VPN
The best defense is a proactive offense. Instead of worrying about a potential hack, you can drastically minimize your risk by choosing a VPN that is built with security as its core foundation. After years of testing and reviewing services, I’ve found that the most secure providers consistently excel in a few key areas.
Use this quick checklist from Safelyo when evaluating any VPN service. If a provider doesn’t get a tick on all of these, I strongly advise you to keep looking.
| Security Feature | What to look for | Status |
| Modern Protocols | Offers OpenVPN and WireGuard as default options. | ☐ |
| No-Logs Policy | Has been independently audited by a top firm (e.g., PwC, Deloitte). | ☐ |
| Kill Switch | Built-in feature to block the internet if the VPN disconnects. | ☐ |
| Leak Protection | Explicitly protects against DNS, IP, and WebRTC leaks. | ☐ |
| Server Infrastructure | Utilizes RAM-only servers for data protection. | ☐ |
| Jurisdiction | Based in a country outside the 5/9/14 Eyes Alliance. | ☐ |
Use this checklist from Safelyo as your guide. If a VPN you’re considering can’t tick all these boxes, you should look elsewhere. Now, let’s explore why each of these checklist items is so critical for your security.
4.1. Choose modern VPN protocols (WireGuard & OpenVPN)
This is the technical foundation of your security. As we’ve discussed, outdated protocols are a non-starter. Look for a provider that not only offers WireGuard and OpenVPN but also sets them as the default options. This shows they prioritize your security over compatibility with ancient devices.
4.2. Demand an audited no-logs policy
A VPN provider can claim they don’t log your data, but words are cheap. A true no-logs policy must be verified by a reputable, independent third-party auditor like PricewaterhouseCoopers (PwC), Deloitte, or Cure53. These audits are expensive and rigorous, so when a provider invests in them, it’s a powerful signal that they are serious about your privacy. I always look for a recent audit (within the last 2-3 years).
4.3. Verify essential features: kill switch & leak protection
These aren’t fancy add-ons; they are fundamental safety nets. A Kill Switch prevents your real IP from being exposed if the VPN connection drops. DNS and IP leak protection ensures that all of your traffic stays inside the encrypted tunnel, with no exceptions. Before you subscribe, check that these features are present and enabled by default in the VPN’s app.
4.4. Prioritize RAM-only servers for data privacy
This is a more advanced feature, but it’s becoming the new security standard. Traditional servers write data to hard drives, where it can remain until it’s manually overwritten. RAM-only servers, by contrast, are completely wiped clean every time they are rebooted. This makes it physically impossible for any data to be stored on them long-term, providing a powerful layer of protection against both remote hackers and physical server seizure.
4.5. Check the company’s jurisdiction and transparency
Where is the VPN company legally based? This matters immensely. A provider located in a country that’s part of the 5/9/14 Eyes Alliances (intelligence-sharing agreements between nations like the US, UK, Canada, and Australia) can be legally compelled to log user data. For maximum privacy, I recommend choosing a VPN based in a privacy-friendly jurisdiction like Panama or the British Virgin Islands.
SAFELYO’S EXPERT TAKE
At Safelyo, we believe the single most non-negotiable factor when choosing a VPN is a recently audited no-logs policy. A company’s promise means nothing without proof. An independent audit from a top firm like PwC or Deloitte is the only way to truly verify that a provider is honoring their commitment to your privacy. If there’s no audit, there’s no trust.
5. FAQ about hacked VPN
Can a VPN be broken?
Theoretically, yes, but practically, no. Breaking the AES-256 encryption used by top VPNs would require computational power that doesn’t exist today. However, the VPN system can be “broken” or compromised through weaker points like outdated software, insecure servers, or user error, as we’ve discussed in this guide.
Can a VPN be intercepted?
Yes, your internet traffic can always be intercepted by your ISP or a hacker on public Wi-Fi. The key difference is that when you use a secure VPN, the intercepted data is fully encrypted. To the snooper, it’s just a stream of unreadable, jumbled code with no meaning.
Can police hack a VPN?
Law enforcement agencies typically don’t “hack” VPN encryption directly. Their primary method is legal: serving warrants to the VPN provider demanding user data. This is precisely why choosing a VPN with a strict, audited no-logs policy and a privacy-friendly jurisdiction is absolutely critical. If there is no data to hand over, the warrant is useless.
Which VPN has been hacked?
There have been a few publicly disclosed security incidents. The most notable examples include the 2018 NordVPN server breach and vulnerabilities found in Pulse Secure VPN. These incidents highlight that even major providers face risks and underscore the importance of how transparently a company responds to and rectifies such issues.
Can free VPNs be trusted?
In my professional opinion, almost never. If you aren’t paying for the product, you are the product. Free VPNs often make money by logging and selling your browsing data, injecting intrusive ads, or, in the worst cases, bundling malware with their software. When it comes to your security, you truly get what you pay for.
6. Conclusion
Ultimately, answering the question can VPN be hacked reveals that true online security is a partnership between the tools you choose and the habits you practice. A VPN is not an impenetrable shield on its own, but it is an essential component of a robust digital defense strategy. The key is to approach it with awareness, not blind faith.
To secure your digital life, remember these key takeaways:
- VPNs can be compromised, but this usually happens by exploiting system vulnerabilities or user error, not by breaking the core encryption.
- Recognizing the warning signs of a compromised connection and knowing how to react quickly is crucial for damage control.
- The best defense is proactive prevention. Choosing a secure VPN based on a strict security checklist is your most effective strategy.
Don’t let the fear of potential risks paralyze you. Using a reputable, high-quality VPN is still a massive security upgrade over using nothing at all. Now that you know what to look for, you’re equipped to make an informed choice.
Let Safelyo help you build a complete digital defense. Understanding these risks is the first step. To continue strengthening your online fortress, explore more essential guides and foundational knowledge in our Privacy & Security Basics category.













