You might have noticed that some websites suddenly stop loading or show endless CAPTCHAs the moment you connect through a VPN. I’ve experienced the same issue myself, and out of curiosity, I started researching how these systems detect VPN users. After testing several tools and reading technical resources, here’s what I found.
-
IP reputation databases that list VPN servers
Websites often use commercial or open databases that label IPs belonging to VPN or proxy networks.
-
Suspicious traffic patterns from one shared IP
Hundreds of users sharing a single VPN IP make behavior patterns stand out.
-
DNS and WebRTC leaks exposing real location
Leaks that reveal your true IP or DNS request can expose VPN usage instantly.
-
Browser fingerprint mismatches and cookie trails
Differences in timezone, language, or old cookies can betray that you’re masking your region.
-
GPS and device geolocation not matching IP region
When your phone’s GPS says one place and your IP says another, detection becomes easy.
-
Port or protocol fingerprints seen by servers
Some VPN protocols leave clear technical traces through their handshake or port numbers.
1. How do websites know I’m using a VPN?
Websites use different technical signals to determine whether a visitor is connected through a VPN. None of these signals alone can confirm VPN use, but when several appear together, detection becomes quite accurate. Understanding how these methods work helps you see why some sites block or challenge VPN traffic.
1.1. IP reputation databases that list VPN servers
Many websites use IP reputation databases to detect VPN servers. These systems classify internet addresses based on their origin and past activity. When an IP comes from a data center or hosting company, it is marked as non-residential and considered high-risk.
Once a VPN server’s IP appears in these databases, websites can recognize it almost instantly. They often respond by asking for extra verification or restricting some actions. VPN providers that reuse the same IP range are easier to detect because those addresses show up frequently across multiple users and reports.
1.2. Suspicious traffic patterns from one shared IP
When too many users share the same VPN IP, websites can easily notice unusual traffic patterns. Hundreds of logins, new account creations, or requests from different countries using the same IP make systems suspicious.
Security tools mark these IPs as shared or automated traffic to protect against abuse. This is why popular or free VPN servers often trigger CAPTCHAs, slower logins, or temporary bans, while dedicated IPs remain less noticeable.
Common red flags websites look for:
- One IP logging into many accounts within minutes
- A single IP accessing multiple regions
- High traffic volume inconsistent with normal browsing
1.3. DNS and WebRTC leaks exposing real location
DNS and WebRTC leaks are among the easiest ways for websites to detect VPN use.
- A DNS leak happens when your device still uses your ISP’s DNS server instead of the VPN’s.
- A WebRTC leak occurs when your browser exposes your local IP address during peer-to-peer connections.
If a website sees two different IP addresses at once, one belonging to a VPN and another from your local network, it can tell that a VPN connection is in use.
How to check for leaks:
| Leak type | Detection tool | Fix |
| DNS Leaks | dnsleaktest.com | Use VPN DNS or Cloudflare DNS |
| WebRTC Leaks | browserleaks.com | Disable WebRTC in browser settings |
Tip: Run leak tests regularly and enable “DNS Leak Protection” in your VPN settings.
1.4. Browser fingerprint mismatches and cookie trails
Websites analyze browser fingerprinting and cookies to identify mismatches between your VPN IP and device settings.
A fingerprint includes your timezone, language, screen resolution, and installed fonts. If your browser settings suggest one country but your IP shows another, it raises suspicion.
Typical fingerprint elements websites compare:
- Timezone and language
- Operating system and screen resolution
- Browser plugins and fonts
Old cookies can also reveal your previous region. If you log in after connecting to a VPN, the old cookie data may expose your real location.
Clearing cookies or using a separate browser profile for VPN sessions reduces this type of detection.
1.5. GPS and device geolocation not matching IP region
Websites and mobile apps often cross-check your GPS or Wi-Fi location against your VPN’s IP. If your device shows that you are in one country but your IP is from another, detection becomes instant. Streaming and banking services rely on this method to follow local licensing and security rules.
You can reduce detection by disabling GPS access for browsers or restricting location permissions for specific apps. Keeping your physical and VPN locations consistent prevents mismatched data that websites can exploit.
1.6. Port or protocol fingerprints seen by servers
Each VPN protocol communicates in a distinct way, which can leave a recognizable fingerprint. OpenVPN, WireGuard, and IKEv2 use specific ports and handshake patterns that advanced firewalls can analyze. Even though your traffic is encrypted, the packet size, timing, and port number reveal what kind of connection it is.
Some websites block known VPN ports automatically. To avoid this, you can switch to a protocol that looks like normal HTTPS traffic, such as OpenVPN with TCP on port 443. This makes it harder for detection systems to separate VPN traffic from regular browsing.

2. Why websites detect and block VPNs
Websites do not always block VPNs out of hostility. They often do it for legal, commercial, or security reasons. These restrictions protect their business models, ensure regional compliance, and prevent misuse by bad actors. Below are the three main reasons why websites choose to detect and limit VPN connections.
2.1. Enforcing regional content and copyright rules
The most common reason websites block VPNs is to follow licensing or regional content agreements.
Streaming platforms, news sites, and gaming services usually buy distribution rights limited to certain countries. If users access that content from a VPN server located elsewhere, it breaks those agreements.
Examples:
- Netflix and Hulu: Different content libraries per country.
- YouTube and BBC iPlayer: Block content unavailable outside certain regions.
- Game platforms: Restrict in-game purchases or early releases by location.
Read more:
2.2. Preventing fraud and account sharing
Another major reason websites detect VPNs is to reduce fraud and abuse.
When people use VPNs to hide their location, it becomes easier to perform activities such as creating multiple accounts, claiming regional discounts, or sharing subscriptions across countries.
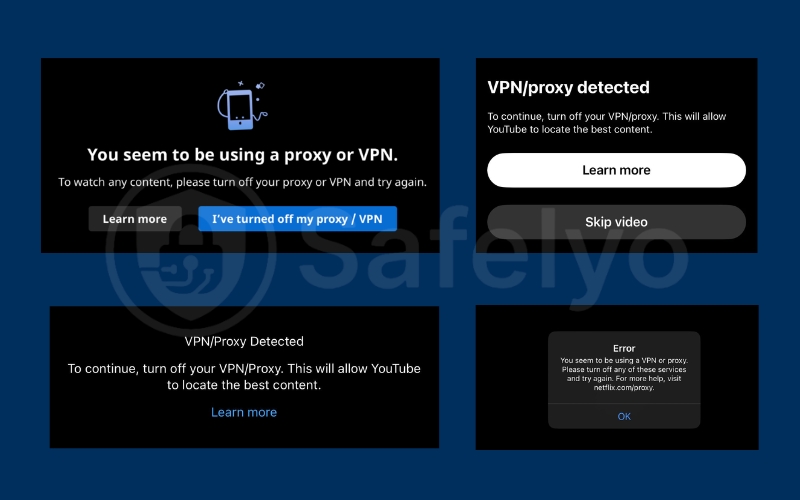
E-commerce platforms and online banks also monitor VPN traffic because it may hide stolen credit cards or suspicious login attempts. Once they detect that multiple users access the same service from one IP, they may trigger verification checks or temporary blocks. These systems help protect both the company and legitimate users from fraud.
2.3. Meeting financial and compliance regulations
Financial and government-related websites are often required by law to know a user’s true location. This is part of Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations. If someone connects from a VPN, the site cannot verify their jurisdiction, which can violate compliance standards.
For example, online trading platforms or gambling sites must confirm whether users are located in approved countries. Using a VPN hides that information and may prevent the site from processing transactions. To stay compliant, these services often block or limit access from known VPN IP ranges.
3. Can ISPs and local networks tell I’m using a VPN?
Internet service providers (ISPs) and local networks cannot see what you do inside a VPN tunnel, but they can recognize that you are using one. VPNs encrypt your traffic, hiding websites, apps, and data transfers.
However, the pattern of encrypted packets still reveals that a VPN protocol is active. The sections below explain how they detect it and in which environments this usually happens.
3.1. Recognizing encrypted traffic patterns
Even though VPNs hide the content of your data, they still produce a unique type of encrypted traffic. Normal browsing traffic contains many short requests to different domains, while VPN traffic forms a steady stream of large, uniform packets going to one destination.
ISPs or network administrators can identify these patterns easily. They may not know what websites you visit, but they can see that your device is continuously connected to a specific remote server using a single protocol. This consistent behavior makes VPN traffic stand out from ordinary web activity.
3.2. Deep packet inspection (DPI) explained simply
Deep Packet Inspection, or DPI, is a method used by advanced networks to analyze the structure of internet traffic. Instead of just reading the destination of a packet, DPI checks parts of the packet header and handshake data to identify the type of connection being used.
For example, the handshake used by OpenVPN or WireGuard looks different from a normal HTTPS request. Even without decrypting the content, DPI can spot that signature. Many corporate networks and national firewalls use DPI to detect and sometimes block VPN connections, especially in countries with strict internet controls.
3.3. Countries and networks that often use DPI
Some countries and private networks apply DPI more aggressively than others. Places with strict online regulations, such as China, Russia, or Iran, use DPI systems to detect and limit VPN connections on a large scale. These systems can block specific ports, throttle encrypted traffic, or cut connections that do not match approved protocols.
On a smaller scale, corporate or university networks may also use DPI to enforce local security policies. They can restrict VPNs to prevent employees or students from bypassing internal firewalls. In most cases, home ISPs only log that a VPN connection exists but do not block it, unless required by local laws.
4. Practical ways to reduce detection (use responsibly)
You cannot completely hide VPN usage, but you can make it harder for websites or networks to detect it. The following methods help reduce detection signals by disguising your traffic and keeping your setup consistent. Always apply these techniques responsibly and within the terms of service of each website or network.
4.1. Use obfuscated or stealth VPN modes
Most premium VPNs include an obfuscation or stealth mode that makes VPN traffic look like regular HTTPS traffic. This works by changing the packet headers and encrypting the handshake so that deep inspection tools cannot identify the protocol type.
If you often connect from places like offices, schools, or travel networks where VPNs are restricted, this feature can help maintain access without breaking security policies. Activating stealth mode adds a thin disguise layer over your VPN connection, reducing the chance of detection by basic filters.
4.2. Connect via common ports like 443 or 80
Using ports 443 or 80 helps your VPN blend in with normal web traffic.
- Port 443 is the same port HTTPS uses for secure websites.
- Port 80 is used for standard web connections.
Because these ports are essential for web browsing, most firewalls and networks cannot block them without breaking other services.
Quick configuration steps:
- Open your VPN app settings.
- Select TCP instead of UDP protocol.
- Change the port number to 443.
4.3. Prevent DNS and WebRTC leaks with proper setup
Even a strong VPN connection can fail if DNS or WebRTC leaks expose your real IP. Make sure your VPN uses its own DNS servers or trusted third-party ones such as Cloudflare or Google DNS. You can also disable WebRTC in your browser settings or use privacy-focused extensions that block leak requests.
After adjusting the settings, test your connection using DNS leak test tools. If your real IP or DNS server appears in the results, your VPN is leaking information and needs reconfiguration.
4.4. Keep browser settings and time zone consistent
Websites compare browser fingerprints to find inconsistencies between your VPN IP and your device settings.
If your browser shows one timezone while your VPN IP belongs to another, this mismatch signals possible VPN use. To avoid it, adjust your device’s timezone and language to match your VPN server’s location.
Old cookies can also reveal past sessions tied to your real IP. Clear them before connecting or use a separate browser profile for VPN browsing. Keeping these small details consistent helps prevent easy fingerprint-based detection.
4.5. Try a dedicated or residential IP
A shared VPN IP is the easiest to detect because many users access the same sites through it. Some VPN providers offer dedicated or residential IPs that belong only to one user. These addresses appear like normal home connections instead of data center IPs.
This approach reduces block rates on streaming or e-commerce platforms. However, dedicated IPs may cost more and require identity verification, so use them only if you need reliable access to sensitive services.
5. How to test whether a site is flagging your VPN
Websites do not always block VPNs directly. Sometimes they only flag your connection as suspicious, which leads to extra login steps, repeated CAPTCHAs, or access delays. These are signs that your VPN IP has been detected or labeled as high risk. The following steps show you how to confirm it and find out why.
5.1. Check your IP reputation
Your IP reputation score reveals whether a website sees your VPN server as trustworthy or risky.
Visit tools such as Project Honey Pot, IPQualityScore, or AbuseIPDB and enter your VPN IP address. These databases show if the IP belongs to a hosting provider or has a history of suspicious activity.
If your VPN IP appears in the “proxy,” “hosting,” or “VPN” category, websites are likely recognizing it as a shared address. Changing to a new VPN server or using a dedicated IP can fix this quickly.
5.2. Run DNS and WebRTC leak tests
DNS and WebRTC leaks can expose your real IP address even when your VPN is connected.
Go to a trusted leak test site while using your VPN. Check if the DNS server or public IP displayed matches your real location. If your actual IP or ISP name shows up, it means the VPN is leaking network information.
Websites use these leaks to confirm that a VPN tunnel is active. You can fix this by enabling DNS leak protection in your VPN settings and disabling WebRTC in your browser.
5.3. Compare results using mobile data
Testing your connection on mobile data helps you identify if the VPN server is causing the block.
Disconnect from your VPN and try to access the same website using your phone’s mobile network or hotspot. If the page loads normally without CAPTCHAs or region errors, the VPN IP is almost certainly being flagged.
This method isolates the problem. If mobile data works but the VPN does not, you know the issue is with the VPN server or its IP reputation.
5.4. Test a different VPN protocol or port
Websites sometimes detect VPN traffic based on the port or protocol being used.
Switch from UDP to TCP or change the connection port to 443, which mimics normal HTTPS web traffic. Some sites block OpenVPN or WireGuard when they appear on nonstandard ports but allow them when using port 443.
Changing the port and protocol can help your VPN blend in with ordinary web connections, reducing the chance of detection.
5.5. Watch for repeated CAPTCHA or login errors
Frequent CAPTCHAs, region warnings, or login resets are strong signs of VPN detection.
If you see these problems only when using your VPN, the site’s system is challenging your session because the IP looks unusual or shared. Try switching servers, clearing cookies, or using a new IP to verify whether the problem disappears.
These repeated verification steps confirm that the website’s security filters have identified your VPN connection.
Running these five checks helps you pinpoint where the detection is happening. Once you find the weak spot, you can adjust your VPN settings, fix leaks, or switch servers to avoid unnecessary blocks.
6. FAQs about How do websites know I’m using a VPN
These common questions explain how websites detect VPN usage and what you can do to reduce false flags. Each answer is simple and beginner-friendly so readers can quickly find what applies to their situation.
Can websites see my real IP when I use a VPN?
Websites cannot see your real IP address if your VPN is configured correctly. The VPN replaces your real IP with its own server IP, keeping your actual address hidden. However, leaks through DNS, WebRTC, or old browser cookies can still expose it. Always test for leaks after connecting to ensure your VPN is working as intended.
Is deep packet inspection common on home ISPs?
Most home ISPs do not use deep packet inspection (DPI) extensively. They can see that you are using encrypted traffic but usually do not inspect it in detail. DPI is more common in corporate networks, schools, or countries with strict internet controls. In normal conditions, home ISPs only log the connection, not its contents.
Why do I get “Are you a robot?” CAPTCHAs when using a VPN?
CAPTCHAs appear because websites suspect automated or shared activity from your VPN IP. When too many users access the same site through one address, security filters respond by requiring human verification. Switching to another VPN server or using a dedicated IP often reduces CAPTCHA frequency.
Do dedicated IPs help avoid VPN blocks?
Yes, dedicated IPs usually face fewer blocks because they are used by one person instead of many. Websites see them as stable, individual addresses rather than shared ones. However, some platforms still detect them if the IP range belongs to a known VPN provider. Dedicated IPs improve reliability but do not guarantee invisibility.
Will clearing cookies fix VPN detection issues?
Clearing cookies helps reduce mismatched location data between sessions. When you connect to a VPN, old cookies may still contain login or region information from your real IP. Deleting them before browsing helps avoid conflicts, but it does not fix network-level detection. You should combine this with good VPN hygiene and leak protection.
Does switching to port 443 reduce VPN flags?
Yes, using port 443 can lower detection rates because it mimics normal HTTPS traffic. Firewalls and websites rarely block this port since it is essential for secure web browsing. Changing your VPN protocol to TCP on port 443 helps the connection blend with regular encrypted traffic. It is one of the safest and simplest adjustments to try.
7. Conclusion
Websites detect VPNs by analyzing IP reputation, traffic behavior, browser data, and network leaks. These signals are not always perfect, but when several appear together, detection becomes much more accurate. Understanding “how do websites know I’m using a VPN” helps you adjust your setup and reduce unnecessary blocks.
To summarize:
- Websites check IP databases to identify addresses belonging to VPN providers.
- They analyze shared IP activity and suspicious traffic patterns.
- They compare browser fingerprints, cookies, and GPS data for mismatched regions.
- Proper VPN configuration and leak protection can lower detection risks.
I once faced constant CAPTCHA challenges while using a common VPN service. After enabling obfuscated mode and disabling WebRTC in my browser, the issue stopped completely. Small adjustments like using obfuscation, changing ports, or cleaning browser data can make your VPN far less visible without breaking any rules.
For more practical privacy and security tutorials, explore the VPN Guides section on Safelyo and keep learning how to stay protected online.