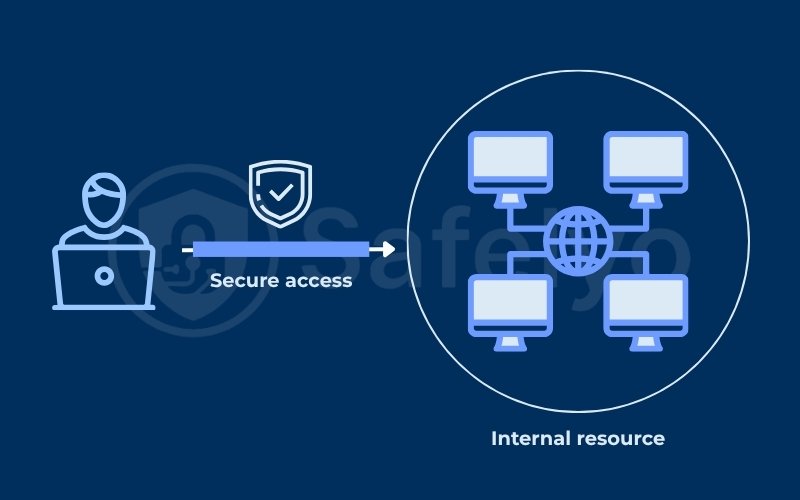
What is a VPN gateway? A VPN gateway is a physical or virtual network device that serves as a secure entry point. It creates an encrypted tunnel over a public network, such as the internet, to connect users to a private corporate network.
Imagine a remote employee trying to access confidential company files from a public Wi-Fi hotspot. Without a secure connection, they risk exposing sensitive data to anyone on that network. The VPN gateway is the “digital drawbridge” to the company’s private “castle.” It verifies the employee’s identity and wraps all their data in a layer of strong encryption, making it unreadable to outsiders.
Key takeaways:
- A VPN gateway is the “digital drawbridge” that validates and protects all traffic entering a private network.
- It uses strong encryption and authentication to secure data.
- It is essential for both individual remote access (point-to-site) and connecting entire offices (site-to-site).
- While effective, traditional gateways have limitations in the modern cloud era, leading to alternatives like ZTNA.
1. What is a VPN gateway?
A VPN gateway is the central “gatekeeper” for all virtual private network traffic. Its job is to sit at the edge of a private network (like a corporate office) and manage all secure connection requests.
This is different from a consumer VPN service you might use to watch geo-restricted content. A consumer VPN connects you to a VPN server to hide your identity and encrypt your traffic on the public internet.
In contrast, a VPN gateway connects you to a specific private network, giving you secure access to its internal resources like file servers, printers, and internal websites.
2. How does a VPN gateway work?
Understanding what it is is the first step. Now, let’s look at how a VPN gateway actually forges that secure connection for your data. It relies on two core concepts: tunneling and authentication.
2.1. How does a VPN gateway create a secure “tunnel”?
A VPN gateway creates a secure connection through a process called “encapsulation,” which is often called a “tunnel.”
Think of it like this: You have a private, sensitive letter (your data packet) you need to send through the public mail (the internet). Instead of just sending the letter for anyone to see, you put it inside a secure, armored diplomatic pouch (a new, encrypted packet).
The VPN gateway and client first agree on a VPN protocol, which sets the rules for building a secure tunnel. Your information is then wrapped inside a protected packet and sent across the internet. At the destination, the receiving gateway or client decrypts it to restore the original content. This tunnel ensures your data remains safe, even on untrusted public networks.
2.2. What is the role of encryption and authentication?
The tunnel itself is only part of the solution. It needs two more critical security pillars:
- Encryption: This is the process of “scrambling” the data inside the tunnel. The gateway uses powerful traffic encryption standards (like those in IPsec) to make your data completely unreadable to anyone who might intercept it.
- Authentication: This is the “verification” process that happens before the tunnel is even built. The gateway must confirm that you are who you say you are. This is often done with a username and password, but modern systems also use digital certificates or two-factor authentication (2FA) for stronger security. Protocols like Internet Key Exchange (IKE) help manage this verification process securely.
3. Why do businesses use a VPN gateway?
A VPN gateway isn’t just a technical curiosity; it’s a fundamental tool for modern business operations. Its value is clearest when looking at these common cybersecurity scenarios.
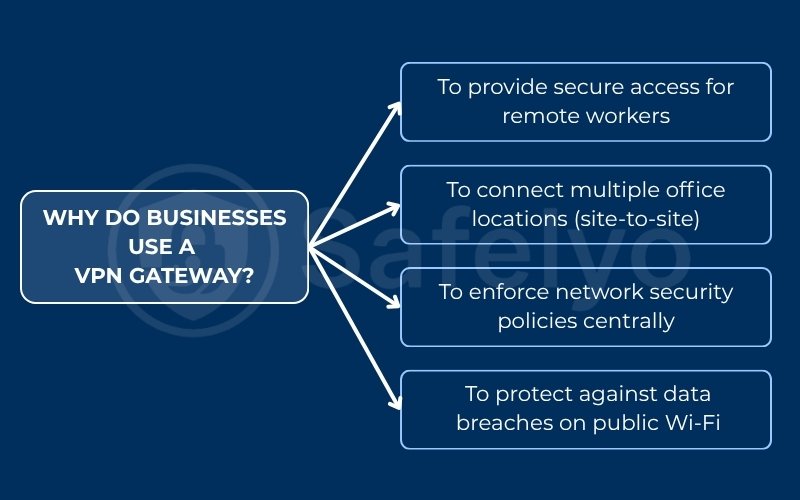
3.1. To provide secure access for remote workers
This is the most common use case, known as a point-to-site VPN. An individual employee (the “point”) working from home, a hotel, or a coffee shop uses a VPN client on their laptop.
The client connects to the central VPN gateway, also known as the “site.” This connection provides secure, encrypted access to internal files and applications. It allows employees to work as if they were at their office desks.
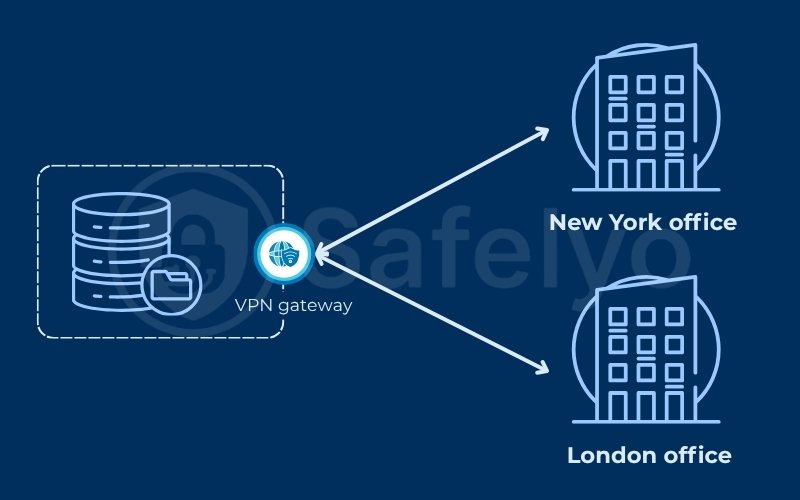
3.2. To connect multiple office locations (site-to-site)
This model is known as site-to-site connectivity.
Imagine a company with main offices in New York and London. Instead of paying for an expensive, private data line between them, each office can install a VPN gateway.
The two gateways create a permanent, secure tunnel between each other over the public internet. This effectively merges the two separate offices into a single, private, and secure wide-area network (WAN), a solution that is both cost-effective and scalable.
3.3. To enforce network security policies centrally
Because all remote access traffic must pass through the VPN gateway, it provides a perfect chokepoint for centralized management. IT and security teams can apply consistent security rules, access control policies, and monitoring to all remote users in one place.
They can decide exactly who gets access to what, ensuring that a user in the marketing department can’t access sensitive financial data, for example.
3.4. To protect against data breaches on public Wi-Fi
When an employee connects to a public Wi-Fi network, they are sharing that network with potentially malicious users who can “eavesdrop” on unencrypted traffic.
By forcing all traffic through the encrypted tunnel to the VPN gateway, the company ensures that even on a compromised network, all sensitive corporate data remains encrypted and safe from prying eyes, preventing costly data breaches.
4. What are the core components of a VPN gateway?
To make this secure connection happen, a VPN gateway setup relies on three essential components working in harmony.
4.1. The VPN server (the gateway itself)
This is the core component: the hardware appliance or virtual server software that sits at the edge of the private network.
It receives connection requests from clients, handles the authentication process, terminates the encrypted tunnels, and decrypts the incoming traffic before forwarding it to the correct internal resource.
4.2. The VPN client (software on the user’s device)
This software runs on a remote device such as a laptop, phone, or tablet. It connects to the VPN gateway, encrypts outgoing data, and decrypts incoming traffic. In essence, it serves as the endpoint of the secure tunnel.
4.3. VPN protocols (OpenVPN, IPsec, WireGuard)
VPN protocols are the “rulebooks” or standards that define how the secure tunnel is built, how data is encrypted, and how keys are exchanged. The client and the gateway must both support the same protocol to communicate. Common examples include:
- IPsec: A very common, secure, and flexible set of protocols.
- OpenVPN: An open-source and highly configurable protocol known for its reliability.
- WireGuard: A modern, fast, and simpler protocol that has gained enormous popularity.
5. What are the main types of VPN gateways?
While the core technology is similar, VPN gateways are typically deployed in two distinct models based on who or what is connecting.
5.1. Remote Access VPN: For individual users
This is the point-to-site VPN model we discussed earlier. It’s built on a one-to-many architecture: many individual, remote users (the “points”) connecting to one central network (the “site”) via the gateway.
This is the classic solution for supporting a remote workforce.
5.2. Site-to-Site VPN: For connecting entire networks
This is the site-to-site connectivity model used to link office locations. It’s a “network-to-network” connection.
In this setup, the VPN gateways on each end handle all the traffic routing and encryption automatically. The individual users in each office don’t need to run any special client software themselves.
6. VPN gateway vs. VPN server: What’s the difference?
The terms “VPN gateway” and “VPN server” are often used interchangeably, which can be confusing. While closely related, they describe different roles.
6.1. Is a VPN gateway just a server?
Yes, a VPN gateway is a type of VPN server. However, the term “gateway” specifically implies its role as a secure entry point that connects users or other networks to a private network.
The term “VPN server” is broader. A commercial VPN provider (like ExpressVPN or NordVPN) runs thousands of “VPN servers.” When you connect to one, its purpose is not to provide access to a private network. Instead, it encrypts your traffic and routes it through the public internet to hide your IP address.
6.2. Comparing functions and typical use cases
Here is a simple breakdown of the main differences:
| Feature | VPN Gateway | General VPN Server (Consumer) |
| Primary goal | Provide secure access to a private network. | Provide secure/anonymous access to the public internet. |
| Typical user | An employee, a remote office, or a business partner. | An individual consumer. |
| Use case | Accessing internal company files, servers, and apps. | Bypassing geo-restricted content, hiding your IP address. |
| Who manages it? | Your company’s IT department. | A commercial VPN provider. |
7. VPN gateway vs. VPN router: Which do you need?
This is another common point of confusion. A VPN router is typically a home or small office device that initiates a VPN connection as a client. You can configure it to connect to a consumer VPN service. This setup protects every device on your home Wi-Fi, such as a smart TV or game console, without requiring separate apps.
A VPN gateway is an enterprise device that accepts incoming VPN connections.
The simplest takeaway is: a VPN router connects out; a VPN gateway lets others connect in.
8. What are the limitations of traditional VPN gateways?
For all their benefits, traditional VPN gateways are not a perfect solution, especially in today’s cloud-centric world. As a remote user, I’ve personally felt this frustration.
There are days when I connect to my company’s VPN, and my connection to cloud apps like Salesforce or even just Google Workspace becomes incredibly slow.
I once complained about this to a friend who works in IT, and she explained that our central VPN gateway was the bandwidth bottleneck. My traffic was ‘hairpinning’, routing all the way to the main office and back out just to reach a cloud service, causing that exact latency.
8.1. Performance bottlenecks and latency issues
This “tromboning” or “hairpinning” effect is a major issue. Traffic from a remote user in London may need to reach a cloud service hosted in Ireland. It might first travel to the company’s VPN gateway in New York, then return to the cloud in Ireland.
This unnecessary detour adds significant latency (lag) and consumes bandwidth, frustrating users and hurting productivity.
8.2. Complex configuration and management
Setting up and managing traditional VPN gateways is known for its complexity. IT teams must maintain complex access control lists (ACLs) and routing tables to define who can go where. As the company grows, this centralized management can become a brittle and time-consuming bottleneck.
8.3. Security risks of “all-or-nothing” access
This is one of the main weaknesses of the traditional VPN model. A gateway typically follows a “castle-and-moat” approach: once users are authenticated, they’re treated as trusted and may gain wide network access. If an attacker compromises those credentials, they can infiltrate the internal network and move laterally to locate and extract sensitive data.
9. Are there modern alternatives to VPN gateways?
Because of these limitations, the cybersecurity industry has shifted toward new models designed for a decentralized, cloud-first workforce.
9.1. How Zero Trust Network Access (ZTNA) improves security
The modern solution is Zero Trust Network Access (ZTNA). This model operates on the principle of “never trust, always verify.” Unlike a VPN that grants broad network access, ZTNA grants access on a per-session, per-application basis.
When a user wants to access an app, the ZTNA solution verifies their identity, checks their device’s security, and then creates a direct, secure connection only to that specific application. The user is never “on the network,” and they have no ability to see or attack other resources. This cloud-native solution effectively stops lateral movement and is a much more secure model.
9.2. Understanding mesh networks and SASE
Two other terms you’ll hear in this space are:
- Mesh networks (e.g., Tailscale, Twingate): These cloud-native solutions create direct, peer-to-peer encrypted tunnels between devices (the user’s laptop and the server they need), completely eliminating the central bottleneck.
- SASE (Secure Access Service Edge): This is an “all-in-one” cloud-native framework. It combines networking (like SD-WAN) with security functions (like ZTNA, firewalls, and deep packet inspection) into a single, globally distributed cloud service. It’s designed to securely and efficiently connect any user or device to any app, anywhere in the world.
10. FAQs about what is a VPN gateway
Here are a few quick answers to other common questions about VPN gateways.
Is a firewall the same as a VPN gateway?
No. A firewall is a “filter” that blocks or allows network traffic based on a set of security rules. A VPN gateway is a “tunnel” that encrypts traffic and authenticates users to grant them access to a private network. Many modern gateways include firewall features, but their primary jobs are different.
Can I use a consumer VPN as a VPN gateway?
No. A consumer VPN, such as ExpressVPN or NordVPN, is designed to encrypt your internet traffic and hide your IP address. A VPN gateway, on the other hand, is a managed device or service that lets authorized users securely connect to a private network.
What is a cloud VPN gateway?
This is a VPN gateway that runs as a virtual service inside a cloud services platform like Amazon Web Services (AWS), Microsoft Azure, or Google Cloud. It’s used to securely connect your physical offices or remote users directly to your applications and resources hosted in the cloud.
How do I set up a VPN gateway?
Setting up a VPN gateway is typically a complex task reserved for network administrators or IT professionals. It involves configuring the network, setting up VPN protocols (like IPsec or OpenVPN), creating user authentication policies, and distributing VPN client software to end-users.
11. Conclusion
In short, what is a VPN gateway? It’s the essential, secure bridge that has connected the remote workforce to the central office for decades.
- A VPN gateway acts as a secure entry point, using encryption and authentication.
- It enables both remote access for individuals and site-to-site connectivity for offices.
- Traditional gateways face latency and security challenges in the modern cloud world.
- Newer models like ZTNA and SASE are now offering more granular, cloud-native alternatives.
Understanding these concepts helps you ask the right questions about how your own data is secured, whether you’re a remote worker or an IT decision-maker.
To learn more about VPN fundamentals like VPN gateways and how to set up secure VPN connections, explore more step-by-step tutorials in the VPN Guides category on Safelyo.