What is a VPN client? It is a software application installed on your device that initiates a secure, encrypted connection to a private network. While its primary function has traditionally been privacy, the technology continues to evolve to meet emerging cybersecurity threats.
In 2026, the adoption of post-quantum encryption (PQE) continues to expand across VPN clients. This technology protects encrypted data against future decryption attempts by powerful quantum computers, adding a critical layer of long-term security.
This guide breaks down exactly how the software functions, the key differences between a VPN client and a VPN service, and practical scenarios where you need it most.
Key takeaways:
- A VPN client is the software installed on your device that manages the encrypted connection.
- It protects internet traffic by routing it through a private data tunnel.
- Reliable clients provide essential features like a kill switch and leak protection.
- Choosing the right protocol, such as WireGuard or OpenVPN, balances speed and security.
1. What is a VPN?
A VPN (Virtual Private Network) is a security technology that encrypts your internet traffic and routes it through a private data tunnel.
This process keeps your online activity hidden from ISPs, advertisers, and potentially malicious actors. By masking your real IP address, a VPN improves your privacy and online security, which is particularly important when you use public networks like those in airports or coffee shops.
In practice, a VPN ensures that any data leaving your device, whether you are browsing news sites, streaming video, or working remotely, stays unreadable to outsiders.
For a deeper understanding of the technology, you can read our complete guide on the VPN page.
2. What is a VPN Client?
A VPN client is the actual software installed on your device (computer, smartphone, or tablet) that establishes and maintains a secure connection to a VPN server.
It handles the complex tasks of encryption, authentication, and configuration automatically, giving you a simple interface to protect your digital life.
When you open the client and click “Connect,” it performs three essential actions:
- Authenticates your identity with the server using your credentials or cryptographic keys.
- Applies encryption protocols to lock your internet traffic inside a secure code.
- Creates a data tunnel that routes all your network requests through the VPN server instead of your ISP’s direct connection.
Modern VPN clients typically feature an intuitive user interface. This dashboard allows you to easily check your connection status, select servers in different countries, and toggle advanced settings like split tunneling or a kill switch.
Most reputable providers offer clients for all major operating systems, including Windows, macOS, iOS, Android, and Linux.
3. VPN client vs. VPN service vs. VPN server
These terms are often used interchangeably, but they refer to different parts of the privacy ecosystem. Understanding the difference helps you troubleshoot issues and choose the right setup.
| Component | What it does | Who controls it | Typical examples |
|---|---|---|---|
| VPN client | The software on your device that initiates the connection and encrypts data. | You, the user | NordVPN app, OpenVPN GUI, WireGuard client |
| VPN service | The commercial provider that manages the network infrastructure and accounts. | The VPN company | ExpressVPN, Surfshark, Proton VPN |
| VPN server | The remote physical or virtual machine that decrypts and routes your traffic. | The provider or IT admin | Servers located in New York, London, Tokyo, etc. |
In simple terms, the client is the tool you use, the service is the subscription you pay for, and the server is the destination you connect to.
4. How a VPN client works
Once you understand what a VPN client is, the next step is knowing how it functions behind the scenes. This helps you recognize why certain features or settings improve your online security and performance.
Quick explanation: Launch client → Authenticate → Select protocol and server → Connect (encrypted tunnel established).
4.1. Connection, encryption, and authentication explained
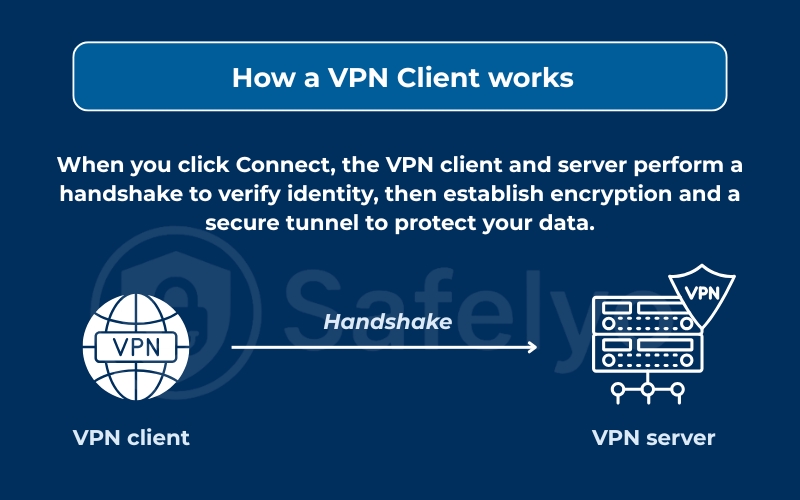
When you click “Connect,” the client performs a seamless three-step process:
Handshake and authentication:
The client first verifies the identity of the server. This ensures you are connecting to a legitimate server and not a malicious “honeypot” set up by hackers.
Encryption negotiation:
The two endpoints agree on a protocol (like WireGuard or OpenVPN) and a cipher to decide exactly how your data will be scrambled.
Tunnel establishment:
A secure data tunnel is created. All traffic leaving your device, from DNS requests to file downloads, is encrypted into unreadable gibberish. To any outsider on the network (like a hacker on public Wi-Fi), your data is useless noise.
You can visualize this as sending a letter inside a locked steel box rather than a transparent plastic envelope. Only the VPN server has the key to open the box, read the request, and forward it to the internet.
2026 Security Update: The Rise of Post-Quantum Encryption (PQE)
The cybersecurity landscape has shifted due to the “Harvest Now, Decrypt Later” threat, where attackers hoard encrypted data to crack later with future quantum computers.
To combat this, modern VPNs have adopted Post-Quantum Encryption. Industry leaders like NordVPN and ExpressVPN now enable this quantum-resistant protection, ensuring your data remains secure against both today’s hackers and tomorrow’s supercomputers.
4.2. Key features that enhance security
A reliable VPN client does more than just connect; it actively safeguards your session with advanced features.
- Kill switch: This is a critical safety net. If your VPN connection drops unexpectedly, the kill switch instantly blocks all internet traffic. This prevents your real IP address from leaking to websites or apps during the brief moment of reconnection.
- Leak protection: High-quality clients ensure your DNS requests and IPv6 traffic do not bypass the encrypted tunnel. Without this, your ISP could still see which websites you visit, even if they can’t see the content.
- Auto-connect: This feature activates the VPN automatically when your device starts up or joins an untrusted Wi-Fi network. It removes the risk of human error, ensuring you never inadvertently browse unprotected.
Additional security tools
Modern VPN apps also include options such as:
- Split tunneling: choose which apps use the VPN and which connect directly.
- MultiHop (Double VPN): route traffic through two servers for extra encryption layers.
- Bypasser: allow specific websites to skip the VPN tunnel for better compatibility.
- Protocol selection interface: lets you switch between protocols for faster speed or stronger encryption.
- Connection status indicators: show real-time details such as ping, load, or IP changes.
- Advanced features: app-based allow or deny lists, and multi-factor authentication (MFA) for extra login security.
Together, these tools transform a basic VPN connection into a smart and adaptive privacy system that keeps your information secure wherever you connect.
5. Why use a VPN client?
You might wonder if you really need a dedicated client, especially since some operating systems have built-in VPN capabilities. While manual setup is possible, using a dedicated VPN client offers significant advantages for most users.
5.1. Ease of use and visual management
The primary benefit is simplicity. A VPN client provides a graphical interface that replaces complex manual configuration. Instead of typing server addresses and importing certificates, you simply click a location on a map or a list.
- Instant access: You can switch from a server in London to one in Tokyo in seconds.
- Visual feedback: The client clearly shows your connection status, current IP address, and server load, so you know exactly when you are protected.
5.2. Access to advanced features
Manual connections often lack the sophisticated security tools found in dedicated clients.
- Feature availability: Essential tools like the kill switch, split tunneling (choosing which apps use the VPN), and Double VPN (routing traffic through two servers) are typically only available through the client software.
- Protocol flexibility: A client lets you switch between tunneling protocols (like changing from OpenVPN to WireGuard for better speed) with a single click, whereas manual setups usually lock you into one protocol.
5.3. Automatic updates and maintenance
Security threats evolve constantly. VPN providers regularly update their clients to patch vulnerabilities, improve encryption standards, and fix bugs.
Using a client ensures you always have the latest protection without needing to manually reconfigure your network settings every time a security update is released.
6. Common uses of a VPN client
Beyond just technical encryption, a VPN client provides practical solutions for everyday internet activities. Here are the most common reasons users install this software.
6.1. Securing public Wi-Fi
Public networks in coffee shops, airports, and hotels are often unsecured, making them hunting grounds for hackers.
A VPN client encrypts your traffic, ensuring that even if someone intercepts your data on these networks, they cannot read your passwords, credit card numbers, or emails.
You may also be interested in this article: 7 Simple ways on how to use a public Wi-Fi network safely
6.2. Bypassing geo-restrictions
Many streaming platforms and websites limit access based on your location.
By using a VPN client to connect to a server in a different country, you can mask your physical location. This allows you to access content that is otherwise blocked in your region, such as Netflix libraries, BBC iPlayer, or news sites.
6.3. Preventing ISP throttling
Internet Service Providers (ISPs) sometimes intentionally slow down your connection when they detect heavy bandwidth usage like streaming or gaming.
Since the VPN client encrypts your traffic, your ISP cannot see what you are doing and is less likely to throttle your speed based on your activity.
6.4. Secure remote access
For remote workers, a VPN client is essential because it creates a secure tunnel to the company’s internal network.
This allows employees to access sensitive files and resources safely from home or while traveling, without exposing the corporate network to outside threats.
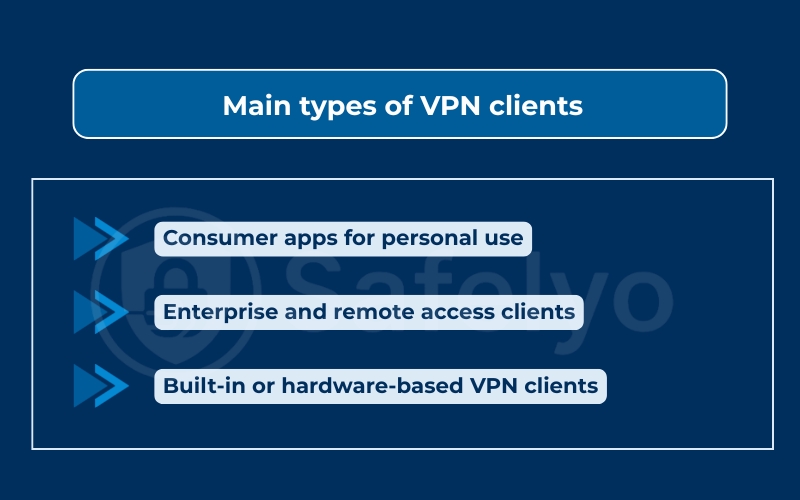
7. Main types of VPN clients
Choosing the right VPN client depends on who you are and where you plan to use it. Some people prefer a dedicated app for quick privacy and streaming, while businesses rely on managed solutions for secure remote access to internal systems. Others may use built-in or hardware-based options that protect entire networks.
7.1. Consumer apps for personal use
These are the most common VPN clients available through app stores and provider websites. They focus on simplicity and performance rather than complex configuration.
A consumer VPN client typically includes:
- A user-friendly interface with one-click connection.
- Support for multiple operating systems such as Windows, macOS, Android, and iOS.
- Built-in features like Kill Switch, Auto-connect, and split tunneling.
- Quick access to geo-blocked websites for streaming or browsing privately.
Because they are designed for everyday users, these apps are ideal for anyone who wants immediate privacy protection without advanced setup. Examples include NordVPN, ExpressVPN, and Surfshark.
7.2. Enterprise and remote access clients
Businesses and organizations use specialized VPN clients to protect connections between employees and corporate networks. These are often managed by IT departments to ensure consistent security policies across devices.
An enterprise VPN client usually offers:
- Integration with company credentials through SSO (Single Sign-On) or MFA (Multi-Factor Authentication).
- Device posture checks that verify if a laptop or mobile device meets security standards before connecting.
- Always-on profiles that keep sensitive data encrypted at all times.
- Centralized monitoring and configuration for compliance.
This type of client ensures safe remote access to internal tools, servers, or databases without exposing the network to outside threats.
7.3. Built-in or hardware-based VPN clients
Some operating systems come with their own VPN functionality that can connect to various protocols such as IKEv2 or L2TP/IPsec. These built-in clients on Windows, macOS, iOS, or Android allow users to connect without installing extra software.
In addition, a hardware device such as a router or firewall may include VPN capability. Setting up the VPN at this level can secure every device on the network, which is useful for small offices or home users who want protection for all connected systems.
- Advantages: Always-on protection and no need for per-device configuration.
- Disadvantages: Limited feature set compared to dedicated apps and fewer updates.
Built-in or hardware-based VPN clients work best for users who prefer a set-and-forget approach and value network-wide encryption.
8. Free vs. paid VPN client
When searching for a VPN client, you will encounter both free and paid options. The difference often comes down to how the provider sustains their business model, and how they treat your data.
| Feature | Free VPN client | Paid VPN client |
|---|---|---|
| Privacy | Often logs/sells data | Strict no-logs policy (Audited) |
| Speed | Throttled, congested | Unlimited, high-speed (WireGuard) |
| Security | Weak/Outdated encryption | AES-256, kill switch, leak protection |
| Support | None/FAQ only | 24/7 live chat |
In my experience testing various services, paid clients consistently provide a more stable connection.
On a free client, I frequently encountered buffering and dropped connections during peak hours, whereas paid clients maintained high speeds regardless of the time.
9. VPN protocols you’ll encounter
Every VPN client relies on a tunneling protocol to decide how your data is encrypted and transmitted. Choosing the right protocol affects both speed and security. Below are the most common options you will see in most modern VPN clients.
9.1. WireGuard
WireGuard is a newer and lightweight protocol designed for simplicity and performance. It uses advanced cryptography to deliver faster speeds and lower latency compared to older options. It is ideal for users who frequently switch between Wi-Fi and mobile data because it reconnects almost instantly.
9.2. OpenVPN
OpenVPN is one of the most established protocols and remains the industry standard for privacy. It offers high flexibility, strong encryption, and wide compatibility with many operating systems. Users can choose between UDP for speed or TCP for stability, depending on their network environment.
9.3. IKEv2/IPsec
IKEv2, often paired with IPsec, provides a secure and stable connection that automatically reconnects when your device changes networks. It is especially useful for mobile users and enterprise setups. Its balance between speed, security, and reliability makes it a popular choice on both iOS and Windows devices.
Choosing the right protocol:
- Use WireGuard for the best performance on modern networks.
- Choose OpenVPN when you need strong encryption or support for routers and legacy systems.
- Pick IKEv2/IPsec for mobile stability and automatic reconnection.
Selecting the right protocol depends on whether you value speed, compatibility, or maximum encryption strength.
10. Should you configure your VPN manually?
Most users should stick to the dedicated VPN client, but there are specific scenarios where manual configuration is necessary.
10.1. When to use the dedicated client
For 99% of users, the app is the superior choice. It offers the highest level of security (via the kill switch), the easiest server switching, and automatic updates.
If you want a “set it and forget it” solution that guarantees privacy, download the client.
10.2. When to configure manually
Manual setup is useful in niche situations where a native app is unavailable or deeper control is required:
Specific smart TVs:
Older Samsung models (running early Tizen versions) or LG TVs (WebOS) often lack native VPN apps. In these cases, you must manually configure the DNS settings or use the Smart DNS feature provided by the VPN service.
Basic routers:
Many ISP-provided routers do not have a graphical interface for VPNs. To protect your home network, you may need to flash custom firmware (like DD-WRT) or manually upload OpenVPN configuration files to the router’s backend.
Strict control: Network administrators or privacy enthusiasts might prefer using open-source clients (like the official WireGuard or OpenVPN Connect apps) to have full transparency over the code running on their machine.
11. FAQs about What is a VPN Client
What is the difference between a VPN and a VPN client?
A VPN (Virtual Private Network) is the overarching technology and network infrastructure that secures your internet connection.
A VPN client is the specific software application installed on your device that you use to connect to that network.
Think of the VPN as the “service” and the client as the “remote control” you use to access it.
Is a VPN client safe?
Yes, a VPN client is safe if it comes from a reputable, paid provider. Legitimate clients encrypt your data and protect your identity.
However, be cautious with obscure free VPN clients, as some have been found to contain malware or trackers that compromise your privacy instead of protecting it.
How to tell if someone is using a VPN on your network?
As a network administrator, you can’t easily see what someone is doing if they use a VPN, but you can tell that they are using one.
You might notice traffic directed to a known VPN server IP address, or see encrypted traffic using a specific port (like UDP 1194 for OpenVPN or UDP 51820 for WireGuard).
Deep Packet Inspection (DPI) tools can also identify the unique signatures of VPN protocols.
Can I use any VPN client?
Not always. While third-party clients like OpenVPN Connect or Tunnelblick work with many providers, they require manual configuration files.
Generally, it is best to use the proprietary client provided by your VPN service, such as the NordVPN app. It is optimized for their network and includes specific features like their proprietary protocols.
Does Windows 10 have a VPN client?
Yes, Windows 10 (and 11) has a built-in VPN client located in the Network & Internet settings.
However, it is just a “container” for connection profiles. You still need to subscribe to a VPN service and manually enter the server address, username, and password to use it.
It lacks the advanced features (like a kill switch or server map) found in dedicated VPN apps.
Is a VPN client the same as a VPN app?
Yes. In most cases, a VPN client and a VPN app refer to the same thing. Both describe the software that connects your device to a VPN server.
The only difference is that “VPN client” is the technical term, while “VPN app” is the consumer-friendly name used in app stores and marketing.
Do I need a VPN client if my operating system already has one built in?
Most operating systems include a basic VPN tool, but dedicated clients from VPN providers offer more control and stronger protection.
A built-in client can handle standard connections, but it often lacks features such as kill switch, leak protection, or automatic updates.If privacy and ease of use are priorities, a dedicated VPN client is the better choice.
Which protocol should I use?
The right tunneling protocol depends on your needs:
- WireGuard offers the fastest speed and simplest setup.
- OpenVPN provides excellent encryption and broad compatibility.
- IKEv2/IPsec is best for mobile users who switch between networks frequently.
If your VPN client allows it, experiment with each protocol to find the best mix of speed and reliability for your connection.
Can a VPN client make me completely anonymous online?
No VPN can make you completely anonymous. A VPN hides your IP address and encrypts your data, but websites can still track you using cookies, browser fingerprints, or third-party analytics.
A VPN client is one layer of online security, not a full anonymity tool. For stronger privacy, combine it with safe browsing habits, private search engines, and cookie blockers.
12. Conclusion
Understanding “what is a VPN client” helps you see how this small piece of software keeps your digital life private and secure.
It manages encryption, authentication, and network routing, turning your internet connection into a protected channel that resists tracking and data theft.
If you want more step-by-step privacy tutorials or want to learn how to configure advanced VPN settings safely, visit the VPN Guides section on Safelyo.