What is IKEv2? It’s a modern VPN protocol that works with IPsec to provide secure connections that are stable and mobile-friendly, and is widely used in most VPN apps today.
When I first connected my laptop to a coffee shop’s Wi-Fi, the VPN app gave me an option between OpenVPN and IKEv2. At the time, I didn’t know what IKEv2 meant, but later I realized it was the reason my connection quickly recovered after switching from Wi-Fi to mobile data.
In this guide, you’ll learn:
- What the IKEv2 protocol is and how it works
- Where it fits among VPN standards like OpenVPN and WireGuard
- What IKEv2 is used for, including mobile and corporate access
- Its pros, cons, and setup best practices
Let’s start by breaking down the basics of IKEv2.
1. What is IKEv2 protocol?
What is IKEv2 protocol? IKEv2 (Internet Key Exchange version 2) is a VPN tunneling protocol often paired with IPsec. It’s designed to securely establish and maintain encrypted connections between two devices.

Unlike older protocols, IKEv2 is optimized for mobility and resilience, which makes it popular in modern VPN apps.
1.1. What does IKEv2 mean?
The term IKEv2 stands for Internet Key Exchange version 2, a cryptographic framework developed jointly by Microsoft and Cisco. Its main purpose is to negotiate security associations (SAs), which define how two devices agree on encryption and authentication before data transmission is exchanged.
According to CISA (2024), key swapping protocols like IKEv2 are critical in protecting VPNs against interception and replay attacks because they enforce mutual authentication and secure key negotiation.
1.2. What is IKEv2/IPsec
IKEv2 is rarely used alone. It almost always works in combination with IPsec (Internet Protocol Security). In this pairing:
- IKEv2 handles authentication, negotiation, and key management.
- IPsec secures the actual data packets with encryption and integrity checks, ensuring safe data transmission across networks through modern cryptographic mechanisms.
Together, they form a strong VPN protocol stack often labeled as IKEv2/IPsec, which is supported natively on Windows, macOS, iOS, and many routers.
1.3. Where IKEv2 fits in VPN protocols
In the wider landscape of VPN protocols, IKEv2 stands out for:
- Mobility: Fast reconnection when switching between Wi-Fi and mobile networks.
- Performance: Lower overhead compared to older standards like L2TP/IPsec.
- Stability: Works well for commuters, frequent travelers, and mobile users.
While newer protocols like WireGuard are gaining attention, IKEv2 remains a trusted option, particularly when stability and native OS support are priorities.
2. How IKEv2 works
If you’re wondering how IKEv2 works, it operates in two main phases to set up and maintain a secure VPN tunnel. First, it establishes a trusted control channel, and then it uses that channel to negotiate and refresh encrypted tunnels for your data. Its efficiency comes from streamlined message exchanges and built-in mobility support.
Understanding these steps helps explain why many VPN providers prefer IKEv2 for speed and stability.
2.1. Key sharing steps (SA_INIT, AUTH, child SAs)
The IKEv2 handshake unfolds in these stages:
- SA_INIT (Phase 1): The client and server agree on algorithms (e.g., AES encryption, SHA-2 hashing) and establish a secure channel.
- AUTH (Phase 1): Both sides prove their identity with pre-shared keys, certificates, or EAP methods. Mutual authentication ensures the tunnel isn’t hijacked.
- Child SAs (Phase 2): Secure data tunnels are created for actual traffic. These can be refreshed or replaced (rekeyed) during long sessions without breaking the connection.
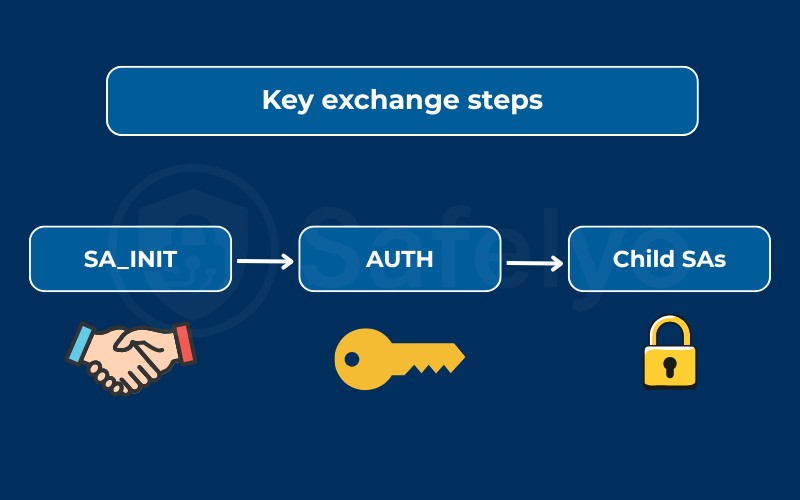
This step-by-step process makes IKEv2 more resilient than older protocols. For example, when I tested IKEv2 with NordVPN, the handshake consistently completed faster than OpenVPN, reducing connection delays.
2.2. MOBIKE roaming & NAT-T basics
Two key features make IKEv2 especially useful for mobile users:
- MOBIKE (IKEv2 Mobility and Multihoming Protocol): This allows a VPN session to continue seamlessly if your device changes IP addresses (e.g., switching from home Wi-Fi to 4G). Instead of dropping, the tunnel adapts automatically.
- NAT Traversal (NAT-T): Many networks use NAT firewalls, which can interfere with VPN traffic. Proper firewall handling is essential for maintaining stable tunnels. NAT-T encapsulates IKEv2 packets inside UDP, helping these connections pass through such barriers.
According to NIST (2024), mobility-friendly tunneling protocols like IKEv2 are essential in today’s environments where users frequently roam between different networks. This makes IKEv2 one of the most reliable choices for commuters and remote workers.
3. What is IKEv2 used for
IKEv2 is widely adopted because of its ability to balance speed, security, and mobility. It’s not just a theoretical protocol. It solves everyday connectivity problems faced by individuals and organizations.
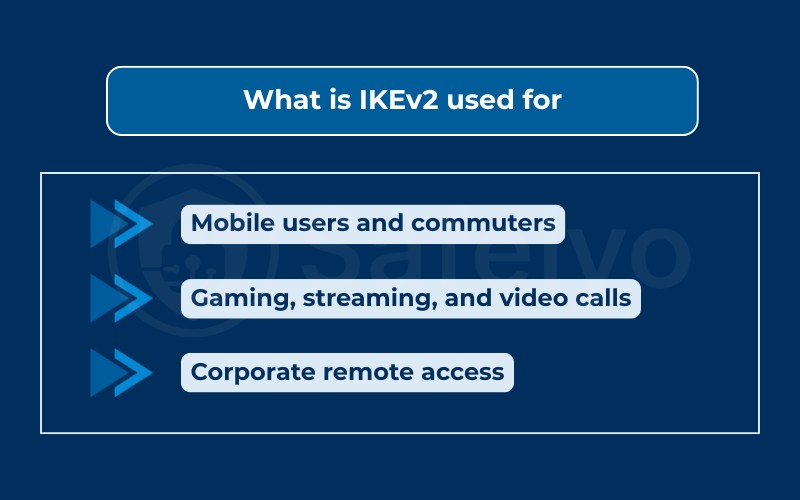
3.1. Mobile users and commuters
One of the strongest use cases for IKEv2 is on mobile devices. Since it supports MOBIKE, connections don’t drop when switching between Wi-Fi and cellular networks.
Key benefits for mobile users:
- Stable connections while roaming
- Quick reconnection after network drops
- Native support in iOS and Android
3.2. Gaming, streaming, and video calls
IKEv2 is also a good choice for latency-sensitive tasks:
- Gaming: Its fast handshake and low overhead reduce lag compared to heavier protocols.
- Streaming: Smooth playback with fewer buffering issues when moving between networks.
- Video calls: Maintains stable sessions in apps like Zoom or Teams without frequent drops.
3.3. Corporate remote access
Enterprises also rely on IKEv2 for remote employee connectivity. With certificate-based authentication and strong encryption via IPsec, organizations can enforce secure access to internal systems. Many corporate VPN gateways (Cisco, Fortinet, Microsoft) ship with IKEv2 support as a default option.
Benefits for business use:
- Works well with enterprise authentication systems
- Enforces strong encryption for compliance
- Scales easily for distributed workforces
4. IKEv1 vs IKEv2
IKEv1, the original Internet Key Exchange protocol, was introduced in the late 1990s. While it laid the foundation for secure VPN tunneling, it had several inefficiencies. IKEv2 was developed as a major upgrade to simplify negotiation and improve stability.
Here’s how they compare:
- Handshake process: IKEv1 often required multiple message exchanges, making connections slower. IKEv2 streamlined this into fewer, more efficient steps.
- Mobility support: IKEv1 lacked features like MOBIKE. IKEv2 added mobility and multihoming support, making it far more suitable for mobile users.
- Security improvements: IKEv2 fixed several weaknesses in IKEv1, such as better handling of denial-of-service protections and stronger cryptographic negotiation.
- Standardization: IKEv1 is now considered obsolete, with most modern VPN providers recommending IKEv2/IPsec as the secure replacement.
According to ENISA (2024), organizations are strongly encouraged to phase out IKEv1 because of its inefficiency and limited resilience against modern threats.
5. IKEv2 vs other VPN protocols
IKEv2 is not the only option for securing VPN traffic. To understand where it stands, it helps to compare it with other widely used protocols like OpenVPN, WireGuard, and L2TP/IPsec.
5.1. IKEv2 vs OpenVPN
Both IKEv2 and OpenVPN are highly trusted, but they serve slightly different needs. Here are the main differences:
- Performance: IKEv2 usually connects faster and recovers more quickly when the network changes. OpenVPN is slower to reconnect but can handle more complex configurations.
- Compatibility: OpenVPN works on almost every platform, including routers and third-party firmware, while IKEv2 also offers native IPv6 support for broader compatibility across networks. IKEv2 has strong support on Windows, macOS, iOS, and Android, but fewer options on some custom devices.
- Security: Both are considered secure when configured properly, but OpenVPN has been audited more extensively.
5.2. IKEv2 vs WireGuard
WireGuard is often seen as the new challenger to IKEv2. One area where IKEv2 still stands out is its compatibility with enterprise systems, while WireGuard is still maturing in terms of broad compatibility:
- Speed: WireGuard is generally faster thanks to its lean codebase. IKEv2 is quick, but not quite at WireGuard’s level.
- Security model: WireGuard uses modern cryptography but has a smaller track record. IKEv2/IPsec has been tested for decades.
- Simplicity: WireGuard is easier for developers to implement. IKEv2 has more complex negotiation steps.
5.3. IKEv2 vs L2TP/IPsec
L2TP/IPsec was once popular, but compared to IKEv2, it shows its age. The main differences are:
- Performance: IKEv2 is faster and more stable, especially on mobile networks.
- Security: L2TP/IPsec is considered weaker and more outdated; it’s often blocked by firewalls.
- Support: Both are widely supported, but most providers are moving away from L2TP/IPsec in favor of IKEv2 or WireGuard.
Besides faster performance, IKEv2 also delivers improved battery efficiency, while L2TP/IPsec tends to drain more power on mobile. In my experience, L2TP/IPsec connections struggled on hotel Wi-Fi, while IKEv2 reconnected without manual intervention.
6. Pros and cons of IKEv2
Like any VPN protocol, IKEv2 has both strengths and weaknesses. Knowing these helps you decide whether it’s the right fit for your needs.
6.1. Strengths (speed, stability, mobility)
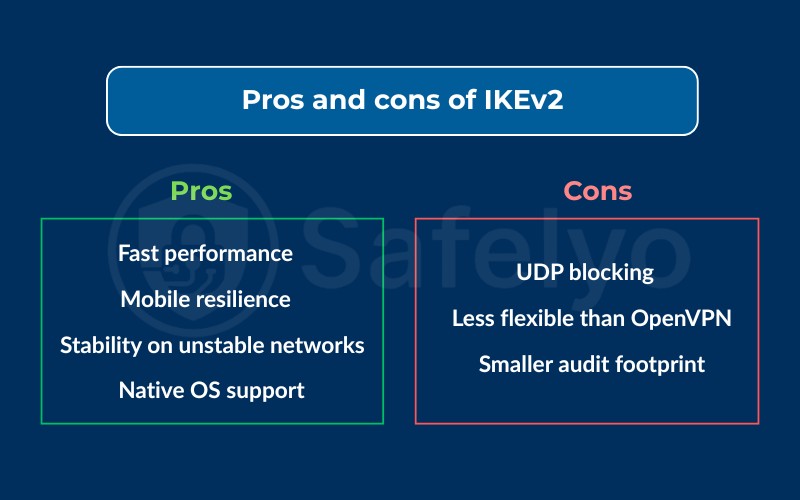
IKEv2 offers several advantages that make it a preferred choice for many users:
- Fast performance: Its streamlined handshake means quicker connection times compared to older protocols like L2TP/IPsec, making IKEv2 a solid choice when performance is a priority.
- Mobile resilience: Thanks to MOBIKE, IKEv2 can maintain a VPN tunnel while switching between Wi-Fi and cellular data.
- Stability on unstable networks: IKEv2 recovers from interruptions faster than OpenVPN in many real-world scenarios.
- Native OS support: It’s built into Windows, macOS, iOS, and widely supported on Android through strongSwan.
When I tested IKEv2 on a long-distance train ride, the VPN session remained active across multiple network changes, which wouldn’t have been possible with many older protocols.
6.2. Weaknesses (UDP blocking, limited flexibility)
Despite its strengths, IKEv2 also has limitations that users should be aware of:
- UDP blocking: Because IKEv2 uses UDP port 500/4500, it can be blocked on restrictive networks (e.g., public Wi-Fi at airports).
- Less flexible than OpenVPN: OpenVPN supports both TCP and UDP, making it easier to bypass firewalls and censorship.
- Smaller audit footprint: While considered secure, IKEv2 has not been audited as extensively as WireGuard or OpenVPN.
According to CSO Online (2024), these weaknesses mainly affect users in highly restrictive regions, but for everyday browsing and mobile connectivity, IKEv2 is still a strong choice.
7. Setup and best practices
Proper configuration details and thoughtful customization matter to ensure both security and performance. Setting up IKEv2 is usually straightforward since most major operating systems support it natively. Still, following best practices ensures both security and performance.
7.1. Windows/macOS/iOS
On Windows and macOS, IKEv2 can be configured directly in the system VPN settings, and this configuration is usually straightforward for most users.. Most commercial VPN providers also include it as a one-click option in their apps. On iOS, IKEv2 is often the default protocol because of its efficiency on mobile networks.
Best practices include:
- Always use certificate-based authentication if possible, and check advanced configuration options for stronger security.
- Verify the provider supports AES-256 encryption with SHA-2
- Test the connection with DNS leak checkers after setup
7.2. Android/strongSwan
While Android supports IKEv2, it often requires the strongSwan VPN client for advanced configuration, especially when dealing with certificates and keys.. Once installed, the setup involves importing the VPN server address, verification method, and certificates, and a correct configuration helps prevent errors, and a proper setup ensures stable connections on Android.
Good tips for Android users:
- Use official strongSwan builds from the Play Store
- Enable “Always-on VPN” for constant protection
- Check battery usage since persistent connections may impact power consumption
7.3. Router basics + leak testing
Many routers support IKEv2/IPsec either natively or through firmware like pfSense and MikroTik, giving users broad compatibility across different home and office setups.. Setting it up on the router protects all devices in your home or office.
When configuring a router, proper configuration ensures that all devices benefit from the VPN tunnel.:
- Keep firmware up to date to patch vulnerabilities
- Use strong pre-shared keys or certificates for verification
- Run periodic leak tests (DNS, IPv6, WebRTC) to confirm the VPN is properly tunneling all traffic, since proper IPv6 handling is crucial for avoiding leaks
8. Troubleshooting IKEv2 connections
Even though IKEv2 is stable, users may sometimes face connection issues such as failed negotiation or DNS leaks. Most issues can be solved with a few checks and adjustments.
8.1. Connection stuck / negotiation errors
When a VPN app shows “connecting” without success, it’s often due to:
- Incorrect authentication (wrong password or certificate mismatch) or misapplied configuration settings are common causes of failure.
- Firewall or NAT blocking UDP ports 500/4500
- Outdated VPN client or router firmware
To fix this, double-check login details, allow IKEv2 traffic through the firewall, and update software. In some cases, adjusting firewall rules may be necessary to restore connectivity. In my experience, switching from hotel Wi-Fi to mobile data often resolved stuck connections caused by restrictive captive portals.
8.2. No internet or DNS leaks
Sometimes the VPN connects, but the internet doesn’t work, or DNS requests still leak outside the tunnel. Common causes include:
- Misconfigured DNS servers in the VPN profile or incomplete configuration can often cause leaks.
- Split tunneling rules bypass secure traffic.
- Router settings override VPN-provided DNS.
Troubleshooting steps:
- Test the VPN connection at dnsleaktest.com.
- If leaks appear, set DNS to trusted servers (e.g., Cloudflare 1.1.1.1, Quad9 9.9.9.9).
- Disable split tunneling unless required for specific apps.
According to EFF (2024), DNS leaks are one of the most common privacy gaps in VPN setups, and regular testing is essential to maintain anonymity.
9. FAQs about what is IKEv2
Many users still have common questions about IKEv2, especially around its security, ports, and practical use cases. Below are clear answers to the most frequently asked ones.
Is IKEv2 secure today?
Yes. When combined with IPsec and modern ciphers (AES-256, SHA-2), IKEv2 is considered highly secure. According to NIST (2024), it remains suitable for government-grade communications when properly configured.
Does IKEv2 work without IPsec?
No. IKEv2 is only a key exchange and authentication framework. It requires IPsec to actually encrypt and protect data packets.
Which ports does IKEv2 use?
IKEv2 typically uses UDP ports 500 and 4500. If these are blocked by a firewall, the connection may fail unless NAT-T is supported.
Is IKEv2 good for gaming?
Yes, in many cases. Its fast handshake and low overhead help reduce latency. However, some restrictive networks may block it, which can interrupt gameplay.
Can IKEv2 be blocked?
Yes. Since it relies on specific UDP ports, network administrators or censorship systems can block it. In such cases, OpenVPN over TCP may work better.
IKEv2 or OpenVPN/WireGuard?
The best choice depends on your needs:
- IKEv2: Great for mobile stability and fast reconnection.
- OpenVPN: More flexible for bypassing censorship.
- WireGuard: Faster speeds and simpler design, but newer in adoption.
Can IKEv2 be customized?
Yes. While the protocol itself is standardized, providers and enterprises can add customization through authentication methods, encryption choices, or routing rules. Advanced customization ensures better alignment with corporate needs.”
10. Conclusion
What is IKEv2? It’s a modern VPN protocol that balances speed, mobility, and security, making it one of the most reliable standards still in use today.
To summarize, IKEv2 offers:
- Fast and stable performance, especially on mobile devices
- Strong encryption when paired with IPsec
- Smooth reconnection when switching networks
- Native support across major operating systems
From my own experience, IKEv2 was the protocol that kept my VPN session alive during a cross-country train ride where my laptop jumped between Wi-Fi, mobile tethering, and public hotspots. That stability is why many VPN providers and enterprises continue to recommend it in 2025.
If you often move between networks or want a secure default option built into your devices, IKEv2 is a VPN protocol worth enabling. For more practical VPN tutorials and privacy tips, explore the Privacy & Security Basics section at Safelyo.












