What is a VPN? Think of it as your own private, encrypted tunnel-shielding your data from prying eyes, protecting your online privacy, and masking your IP address whenever you’re online.
In today’s increasingly complex digital world, understanding how to secure your personal information and fortify your cybersecurity isn’t just beneficial – it’s essential. Whether you’re working remotely, managing finances online, or simply browsing on public Wi-Fi, a VPN offers critical protection.
If you want to understand how a VPN secures your digital life, here are the essential answers you need:
- What is a virtual private network?
→ It acts as a private, encrypted tunnel for your internet traffic, shielding your data and masking your IP address from prying eyes. - Why should you use one?
→ It secures your connection on risky public Wi-Fi, prevents ISPs from tracking your browsing history, and enhances overall online privacy. - Can it bypass geo-blocks?
→ Yes. By masking your real location, a VPN allows you to access restricted content and streaming libraries from other countries. - Does a VPN make you 100% anonymous?
→ No. While it hides your location, it cannot stop tracking via browser cookies or if you log into accounts like Google or Facebook. - Are free VPNs safe?
→ Generally, no. Many free services sell your data to cover costs; for real security, choose a provider with a verified no-logs policy.
With a hands-on experience in cybersecurity and network infrastructure, I’ve seen how often users become targets of data breaches – all because they overlooked this simple, powerful tool. A VPN isn’t just for tech experts; it’s a fundamental privacy measure for anyone navigating the internet today.
Don’t wait for a data leak to take your security seriously. Let me walk you through everything you need to know to take control of your online privacy-starting now.
1. What is a VPN?
You’ve probably heard the term “VPN” thrown around, maybe in discussions about online security or accessing your favorite shows while traveling. So, what is a VPN exactly? VPN stands for Virtual Private Network.
Browsing the internet without one is like walking down the street holding a sign with all your personal details for everyone to see. But when you use a VPN, it’s like turning invisible. No one can track what you’re doing – not advertisers, not hackers, not even that creepy dude watching network traffic.
That’s essentially what a VPN does for your internet connection. It creates a secure, encrypted “tunnel” for your data to travel through when you’re using a public network like the internet. Think of the VPN tunnel as your personal, digital bodyguard for your online activities.
The core VPN definition boils down to this: It’s a technology that establishes a protected network connection when using public networks. Its main goals are pretty straightforward: To safeguard your online identity by masking your IP address (your internet “home address”), to encrypt your data so hackers and snoopers can’t read it. However, to helps you bypass geo-restrictions, giving you access to content that might otherwise be blocked in your region.
>> You might also like this related article:
2. How does a VPN work?
How does a VPN work in simple terms? A VPN establishes a secure and private VPN connection for you by performing three core actions:
1. Creating an encrypted pathway for your data
2. Scrambling your information to make it unreadable to outsiders
3. Concealing your true online location

Let’s break down each of these key components. Before any data is sent, a crucial authentication process takes place. This step ensures that you are connecting to a legitimate VPN server and not an impostor. Strong authentication confirms the identity of both the client (your device) and the server, establishing a trusted foundation for the secure connection. After successful authentication, the tunneling process can begin.
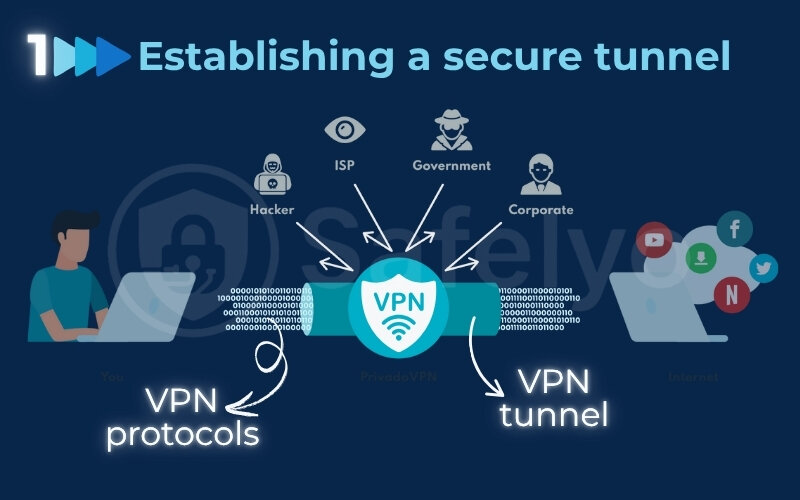
2.1. Establishing a secure tunnel: The role of VPN tunneling protocols
The first thing a VPN does is create a VPN tunnel. You can picture this as an exclusive, encrypted channel between your device (like your laptop or phone) and a remote VPN server, establishing a secure connection. This process, known as tunneling, encapsulates your data packets within standard network packets before sending them across the Internet.
The tunneling itself is what creates the private pathway through the public network. The specific method of tunneling is defined by the protocol in use, ensuring both privacy and data integrity. This tunnel effectively shields your online activities from the general traffic of the public internet.
The way this tunnel is built and secured is determined by various types of VPN protocols. You might come across names like IKEv2/IPSec, or the newer WireGuard. When I recommend VPNs, I always stress checking for support of modern, reputable protocols.
From my experience advising individuals and small businesses on cybersecurity, you don’t need to become an expert in the nitty-gritty of each protocol. It’s important to understand that they are the foundational blueprints ensuring your VPN tunnel is both secure and stable. Effective tunneling is the first line of defense in a VPN’s security architecture, creating a shield around your data from the very start.
2.2. Data encryption: Making your information unreadable
Once your data enters the secure tunnel, VPN encryption takes over. This is a vital step in how a VPN safeguards your information. Essentially, encryption transforms your data into a complex code, making it completely unreadable to anyone who doesn’t possess the specific decryption key.
I always emphasize to my clients that strong encryption is non-negotiable for true VPN security. This robust data protection means that even if a cybercriminal or your ISP were to intercept your traffic, they’d only see a jumble of nonsensical characters.

Many top-tier VPNs utilize AES-256-bit encryption, a standard so secure it’s used by governments for classified information. For instance, I use it when handling sensitive work files or online banking on a network I don’t fully trust. Knowing my connection is secured with AES-256 encryption gives me significant peace of mind.
2.3. IP address masking: Hiding your real online identity
Your IP address (Internet Protocol address) acts like your device’s unique mailing address on the internet. It can reveal your general physical location and is often used by websites and services to track your online footprint.
A VPN helps you effectively hide your IP address. When you connect through a VPN server, your internet traffic appears to originate from that server’s location and IP address VPN, not your own. This is a simple yet powerful way to enhance online anonymity and bypass geographic content blocks.
I find this feature incredibly useful in my day-to-day online activities. For example, I might need to research content in a different country or access my home streaming library while traveling. The VPN makes it seem like I’m browsing from that location by assigning me a local IP address.
3. Types of VPN
Not all VPNs wear the same cape. While they all share the fundamental goal of protecting your digital life, they’re designed for different missions. Let’s break down the three main types you’ll encounter.
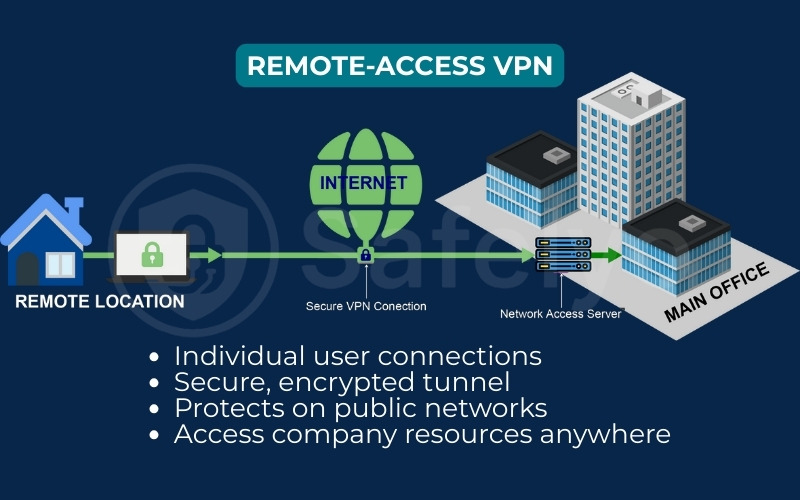
3.1. Remote-access VPN
This is the most common type of VPN and likely the one you’re picturing. This type of VPN is specifically designed to provide secure remote access for individual users. For example, it can be used by a remote employee connecting to their company’s network or a traveler securing their connection on sketchy airport Wi-Fi.
It works by creating a secure, encrypted tunnel from your personal device (your laptop or phone) to a private network. The primary goals are to secure your internet traffic from prying eyes on public networks and access internal company resources from anywhere in the world. This model is also commonly referred to as a client-to-site VPN, as it connects an individual client device to a central site or network.
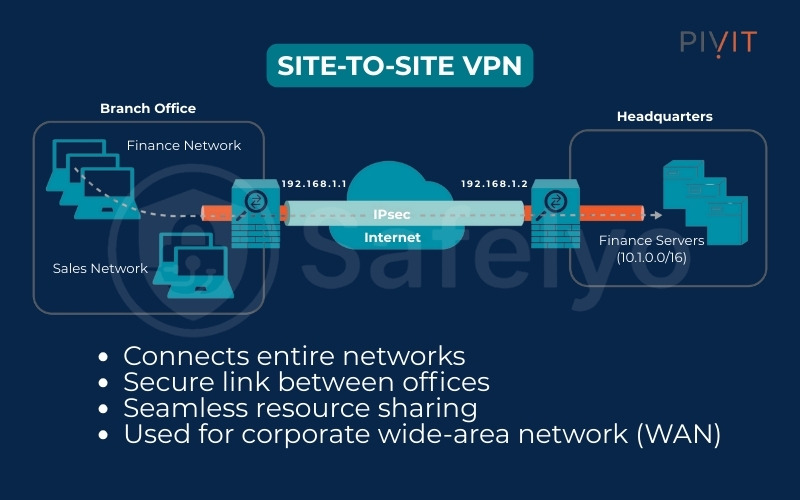
3.2. Site-to-site VPN
Think of this as the heavy-duty, corporate version. Instead of connecting a single user to a network, a site-to-site VPN connects entire networks together, essentially acting as a secure, private bridge over the public internet.
For example, a company with headquarters in New York and a branch office in London would use a site-to-site VPN to securely link both office networks. This allows employees in both locations to share resources seamlessly as if they were all in the same building.
This solution is almost exclusively used by businesses to create a unified, secure wide-area network (WAN). The reliability and security of a site-to-site VPN are paramount for ensuring business continuity and seamless collaboration across geographically dispersed locations.
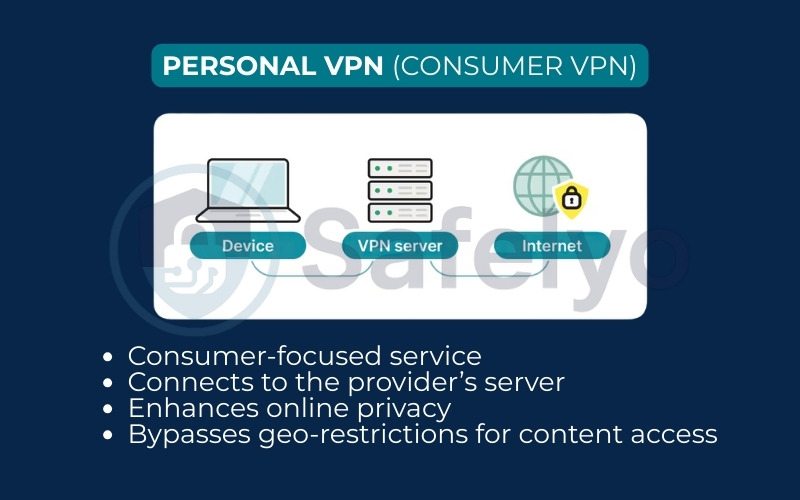
3.3. Personal VPN (Consumer VPN)
This is a specific kind of remote-access VPN and is what most of us mean when we say we “use a VPN”. These are the commercial services you subscribe to (like NordVPN, ExpressVPN, or Surfshark) and install as an app on your devices.
While a corporate remote-access VPN connects you to a specific company network, a personal VPN connects you to a server run by the VPN provider. Their main job is to boost your everyday online privacy. They hide your IP address from websites and bypass geo-restrictions. This allows you to stream your favorite content from back home while traveling.
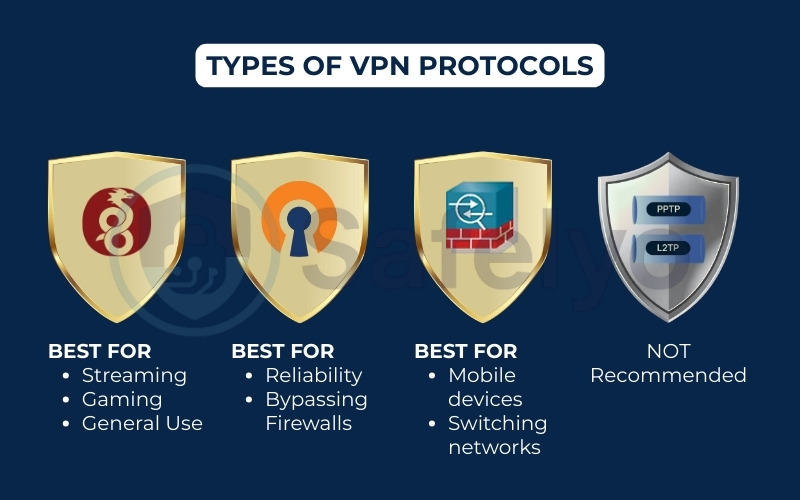
4. VPN protocols explained (Simple for Beginners)
If a VPN is a private tunnel, then a VPN protocol is the specific type of armored vehicle that transports your data through it. These protocols are the underlying technologies that create the secure connection, each offering a different balance of speed, security, and stability.
| Protocol | Speed | Security | Stability | Best For |
|---|---|---|---|---|
| WireGuard | Very Fast | Excellent | Good | Streaming, Gaming, General Use |
| OpenVPN | Fast | Excellent | Very Good | Reliability, Bypassing Firewalls |
| IKEv2/IPsec | Fast | Very Good | Excellent | Mobile Devices, Switching Networks |
| PPTP / L2TP | Slow / Medium | Poor (Avoid) | Fair | Not Recommended |
Now, let’s break down what each one actually means.
WireGuard
WireGuard is the modern, fast, and efficient protocol that’s quickly becoming the favorite for most users and providers.
- Top-tier speed: Its lightweight code makes it ideal for activities that need a fast connection, like streaming 4K video, online gaming, and large downloads.
- Excellent security: It uses the latest, strongest encryption standards.
OpenVPN
For years, OpenVPN was the gold standard. It’s trusted, battle-tested, and incredibly reliable. It often utilizes the SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols for its encryption and authentication processes, which is the same technology used to secure HTTPS websites. This reliance on proven standards like SSL/TLS is a key reason for its robust security reputation.
- Highly secure & versatile: Being open-source means its code has been thoroughly audited by security experts worldwide.
- Great for tough networks: It’s known for being one of the best protocols for bypassing restrictive firewalls at work or school.
IKEv2/IPsec
Internet Key Exchange version 2 (IKEv2) paired with IPsec is built for stability, especially when you’re on the move. The Internet Key Exchange protocol is responsible for establishing the security association in the VPN session.
- Extremely reliable: It excels at reconnecting instantly if your connection drops or you switch from Wi-Fi to cellular data.
- Fast and secure: It’s a great choice for anyone who primarily uses a VPN on their smartphone. The Internet Protocol Security (IPsec) component handles the encryption and authentication of each data packet, making it a highly secure framework.
PPTP & L2TP/IPsec
These are legacy protocols with well-known and serious security flaws.
- Slow performance: They are significantly slower and less reliable than modern alternatives.
- Strongly not recommended: Any reputable VPN service will no longer use or recommend these. You should avoid them completely.
>> You may also be interested in the showdown between:
5. Why use a VPN? Top benefits for your online experience
Essentially, what can a VPN do for you? The benefits of VPN extend far beyond just a techy tool. It’s about enhancing your everyday online life. It provides a shield of privacy, a cloak of security, and a key to unlock a more open internet. Let’s look at some key VPN uses and explore how VPN protects you with practical examples.
VPN benefits summary: Key advantages at a glance
- Enhanced online privacy: Keeps your browsing activity hidden from your ISP and minimizes tracking by websites and advertisers for greater anonymity.
- Improved security on public Wi-Fi: Encrypts your internet connection to safeguard your sensitive information against hackers and threats when connected to unsecured public networks.
- Access to geo-restricted content: Allows you to bypass geographical limitations and content moderation, enabling access to global content, streaming services, and websites from anywhere.
- Secure remote login: Provides a safe and encrypted connection for remote workers and businesses to access internal networks and sensitive company data securely.
>> Read more: What can VPN do? Top benefits & 12 key uses
For many, a VPN is an indispensable tool for a safer and more open internet experience. Here’s a closer look at how VPN protects you and why you might consider using one.
5.1. Enhanced online privacy and anonymity
One of the primary drivers for using a VPN is to boost your online privacy. Without a VPN, your Internet Service Provider (ISP) can see every website you visit, effectively logging your entire browsing history. A VPN encrypts this connection, making your browsing activity unreadable to your ISP. This data can be collected, stored, and sometimes even sold to third parties.
Furthermore, advertisers and websites constantly track your online behavior to build a detailed profile of your interests. I personally find it quite unsettling how, after searching for a specific product, ads for that exact item or similar ones start popping up everywhere I go online.

A VPN significantly curtails this by masking your IP address and encrypting your traffic, making it much harder for ISPs and advertisers to track your digital trail. This greater VPN privacy allows you to browse the web with more anonymity.
5.2. Improved security on public Wi-Fi networks
Public Wi-Fi hotspots – like those in cafes, airports, or hotels – are incredibly convenient, but they’re also notorious hotspots for cyber threats. These networks are often unsecured, making it relatively easy for hackers to snoop on your connection through “man-in-the-middle” attacks and potentially steal sensitive information like passwords or credit card details.
This is where VPN security becomes indispensable. By encrypting your connection, a VPN creates a secure internet connection even on these untrusted public networks.

I make it a strict habit to never connect to public Wi-Fi without first activating my VPN. It’s a simple step that acts like a personal bodyguard for my data, ensuring that even if the network itself is compromised, my information remains scrambled and safe.
>> You may also be interested in the best VPN for public Wi-Fi toplist. Find your perfect match!
5.3. Bypassing geo-restrictions and censorship
Have you ever tried to watch your favorite show while traveling abroad, only to be met with a “not available in your region” message? This is due to geo-restrictions. A VPN excels at location spoofing, a technique that makes it appear as though you are browsing from a different country. This not only unblocks streaming services but can also be useful for things like online shopping, where prices may vary by region.
A VPN can help you bypass geoblocking by allowing you to connect to a server in a different country. This makes it appear as though you are browsing from that location, granting you access to content that would otherwise be unavailable.

For example, when I travel, I often use my VPN to connect to a server in my home country. This allows me to keep up with local news and access my usual streaming subscriptions like Netflix or BBC iPlayer. Similarly, software developers or IT professionals might use a VPN to test how their applications or websites perform and appear from different geographical regions, ensuring a consistent user experience worldwide.
5.4. Secure remote access for work and business
For remote workers and businesses, a VPN is essential for secure remote network access. The most common type of this is a client-to-server VPN, where an employee’s device connects to the company network. For connecting entire offices, businesses might use a site-to-site VPN. This technology allows employees to safely access sensitive files and resources from anywhere, as if they were physically in the office.
As a consultant, I often see SMBs overlook this, but implementing a VPN for remote access is a foundational step in modern data security. This is crucial for protecting confidential business data, especially when employees might be using less secure home networks or public Wi-Fi. By ensuring all remote connections are encrypted and tunneled through the VPN, businesses can significantly reduce the risk of data breaches and maintain operational security.
>> Maybe you will need: Best VPN for working from home in 2025 (secure & stable)
6. Is a VPN safe? What you must know
The short answer is yes, a reputable VPN is one of the safest tools you can use to protect your online privacy. But the keyword here is reputable. The level of safety you get depends entirely on the provider you choose.
Think of it like the lock on your front door. A high-quality lock from a trusted brand will keep you safe. A cheap, flimsy one from a shady seller might break easily or, even worse, have a secret backdoor. To be truly safe, a VPN must have a few non-negotiable features. This includes robust authentication methods to verify your identity and protect your account from unauthorized access. The authentication phase is critical to prevent attackers from hijacking your VPN session.
6.1. VPN encryption safety
The core of a VPN’s security is its encryption. A trustworthy VPN scrambles your internet traffic into unreadable code, making it impossible for your ISP, hackers on public Wi-Fi, or government agencies to spy on your activities.
The industry standard is AES-256 encryption, the same level used by banks and militaries to protect top-secret information. When a VPN uses this level of encryption, your data is, for all practical purposes, uncrackable.
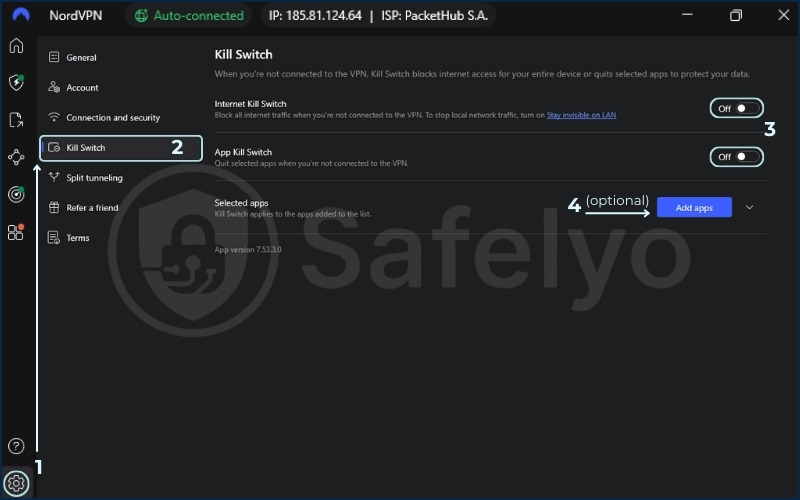
6.2. The all-important kill switch
Imagine your VPN tunnel is a protective invisibility cloak. What happens if the cloak suddenly rips? A kill switch is an essential safety net that prevents this from exposing you.
If your VPN connection unexpectedly drops for even a split second, the security switch instantly blocks your device from accessing the internet. This prevents your real IP address and unencrypted data from being accidentally leaked until the secure VPN connection is restored. I never use a VPN that doesn’t have this feature enabled.
6.3. DNS & IPv6 leak protection
This sounds technical, but it’s a simple concept. Even with a VPN active, your computer can sometimes “leak” requests through your normal internet connection.
- DNS leaks: Your browser might accidentally send your website requests (like google.com) to your ISP’s servers instead of the VPN’s private servers.
- IPv6 leaks: Some older VPNs don’t properly handle traffic over the newer IPv6 protocol, causing your real IP address to leak out.
A secure VPN must have built-in protection to force all traffic and all requests through the encrypted tunnel, ensuring there are absolutely no leaks.
6.4. When VPNs are NOT safe
A VPN is a powerful tool, but it’s not a magic bullet. There are specific situations where a VPN can be ineffective or even dangerous:
- If you use a “free” VPN. Most free VPN services have a hidden cost: Your privacy. They often make money by tracking your browsing data and selling it to advertisers, or worse, by injecting malware and ads into your connection.
- If the VPN provider keeps logs. If a VPN records your online activity (the websites you visit, files you download), your “private” history isn’t private at all. This data could be handed over to authorities, sold, or stolen in a data breach. Always choose a VPN with a strict and audited no-logs policy.
- If your device is already infected. A VPN encrypts your connection, but it is not antivirus software. If your computer has malware, that malware can still steal your data before it ever gets encrypted and sent through the VPN tunnel.
- If you fall for phishing or scams. A VPN can’t protect you from human error. It won’t stop you from clicking a malicious link in an email or willingly entering your password into a fake website. To add another layer of protection for your VPN account itself, always enable two-factor authentication (2FA) if your provider offers it. This prevents anyone from logging into your account even if they manage to steal your password.
6.5. Advanced Features: Split Tunneling
Many reputable VPNs offer a feature called split tunneling, which gives you more control over your traffic. Split tunneling allows you to choose which apps use the VPN and which connect to the internet directly. For example, you could route your web browser through the VPN for security while allowing a gaming app to connect directly for lower latency. This flexibility makes split tunneling a highly practical feature for everyday use.
7. Do VPNs track you? VPN logging policies explained
This is the million-dollar question, and the honest answer is a paradox: A VPN is designed to stop tracking, but it’s also in the perfect position to track you itself.
Think of it this way: to hide your mail from the post office, you hire a private courier. You trust the courier to deliver your packages without opening them. A VPN is your digital courier. All your internet data passes through its servers, so you have to trust that it won’t peek inside.
This trust is defined by one single, critical document: The logging policy.
7.1. What VPNs can see
By design, a VPN provider’s server acts as the middleman for your entire internet connection. This means that, technically, they have the ability to see and record:
- The websites you visit
- How long do you stay connected
- Your original, real IP address
- The device you’re using
- How much data are you downloading or uploading
This is precisely why a provider’s promise not to record this information is the most important feature they can offer.
7.2. The meaning of a “no-logs” policy
When a VPN claims to have a no-logs policy, it means they promise not to store any information that could identify you or reveal what you do online. However, not all “no-logs” claims are created equal.
| Type of Log | What it records | Privacy risk | Should you accept it? |
|---|---|---|---|
| Usage / Activity Logs | Your browsing history, downloads, and app usage. | Very High | Never. This defeats the entire purpose of a VPN. |
| Connection Logs | Metadata: connection times, data used, server location. | Low to Medium | Acceptable if the data is anonymized and minimal. |
| True No-Logs | Nothing that can be tied to a specific user’s identity or activity. | None | Yes. This is the gold standard for privacy. |
In short, a true no-logs policy is the only guarantee that your online activities remain private. It ensures that even if the VPN provider were legally compelled to hand over user data, there would be no data to share.
7.3. How to check if a VPN is truly no-logs
Talk is cheap. Any company can write “no-logs policy” on their homepage. As an expert who reviews these services, here’s the checklist I personally use to verify their claims:
- Look for independent, third-party audits. This is the strongest proof. Reputable VPNs hire major auditing firms (like PricewaterhouseCoopers (PwC), Deloitte, or Cure53) to comb through their systems and publicly verify that their no-logs claims are true. If a VPN has been audited, it will almost always boast about it.
- Read their privacy policy (the easy way). You don’t need to be a lawyer. Open their privacy policy and use Ctrl + F to search for key terms like “log“, “track“, “store“, “data collection“, and “third parties“. Watch out for vague or confusing language. A trustworthy company will state its policy in clear, simple English.
- Check their jurisdiction. Where is the VPN company legally based? VPNs based in privacy-friendly countries like Panama or the British Virgin Islands are not subject to invasive data retention laws. Conversely, those based in countries within the 5/9/14 Eyes intelligence-sharing alliances (like the US, UK, or Australia) could potentially be pressured by governments to log user data.
8. VPN vs Proxy vs Tor: What’s the difference?
While exploring online privacy tools, you’ll often see VPNs mentioned alongside proxies and Tor. All three can hide your IP address, but they are fundamentally different tools built for different purposes.
Choosing the right one depends entirely on what you need: security, simple location spoofing, or maximum anonymity.
| Feature | VPN | Proxy Server | Tor |
|---|---|---|---|
| Hides your IP address | Yes | Yes | Yes |
| Encrypts your traffic | Yes (Strongly) | No | Yes (Multi-layered) |
| Speed | Fast | Medium to Fast | Very Slow |
| Primary use case | Daily privacy, security, streaming | Bypassing simple geo-blocks | Maximum anonymity |
| Ease of use | Very Easy (App-based) | Easy (Browser settings) | Medium (Requires Tor Browser) |
| Privacy level | High | Low | Very High |
VPN: The all-around protector
As we’ve discussed, a VPN is the best all-in-one solution for the average user. It encrypts your entire internet connection, not just your browser, making it secure and private. It’s fast enough for streaming and downloading, easy to use with dedicated apps, and provides a high level of privacy.
Proxy: The quick disguise
A proxy server is the most basic of the three. It acts as a simple middleman, port forwarding your traffic to make it look like it’s coming from a different location. It can help you bypass a simple regional block on a website, but that’s where its usefulness ends. It does not encrypt your traffic, leaving you vulnerable and exposed. It’s a flimsy mask, not a suit of armor.
Tor: The anonymity network
Tor (The Onion Router) offers the highest level of anonymity possible. It routes your traffic through a series of volunteer-run servers, wrapping it in multiple layers of encryption at each “hop”. This makes it nearly impossible to trace the traffic back to its origin.
However, this complex process comes at a huge cost: Speed. Tor is incredibly slow, making it impractical for streaming, downloading, or even general browsing. It’s a specialized tool designed for journalists, activists, and individuals who require absolute anonymity and are willing to sacrifice speed for it.
>> Read more:
9. Downsides of using a VPN
Like any technology, they aren’t without a few potential drawbacks. One risk is data leakage if the VPN connection suddenly drops, which could expose your real IP address. To prevent this, reputable VPNs include a feature called a security switch, which automatically blocks your internet access until the secure connection is restored. Being aware of these points helps you set realistic expectations.
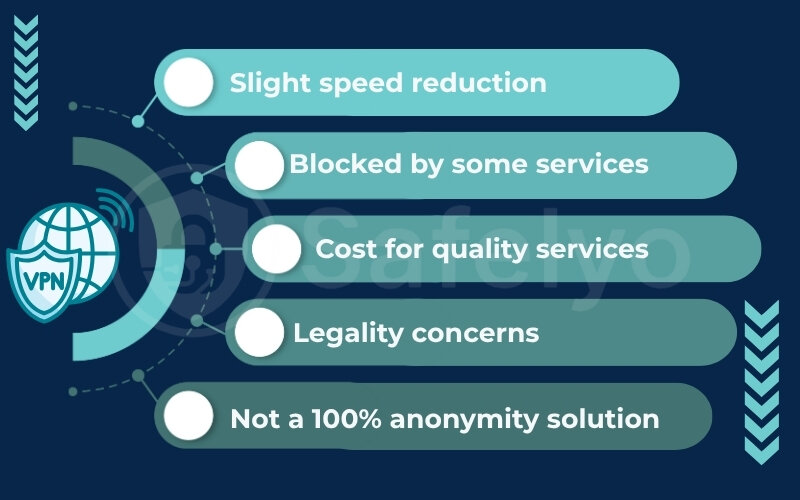
Slight speed reduction
One common concern is a potential reduction in internet speed. Because your data is being encrypted and routed through an extra server, a slight slowdown can occur. However, in my experience, with a quality VPN provider, this speed difference is often negligible for everyday browsing, streaming, and even gaming. Choosing a server geographically close to you can also minimize this impact.
Blocked by some services
Occasionally, you might find that some streaming platforms and websites actively block VPN connections. This is often because VPNs have been misused in the past for activities that violate their terms of service. While frustrating, this is becoming less common as VPN use becomes more mainstream.
Cost for quality services
Another point to consider is that reputable, high-quality VPNs usually come with a subscription fee. While free VPNs exist, they often come with significant limitations like slower speeds, data caps, and fewer server choices. More concerningly, they might compromise your privacy by logging your activity or selling your data. Investing a small amount in a paid service generally ensures better performance and stronger privacy protections.
Legality concerns
Although using a VPN is legal in most countries, it’s crucial to remember that using a VPN to conduct illegal activities remains illegal. Always be mindful of the laws in your specific location.
Not a 100% anonymity solution
Finally, while significantly enhancing privacy, a VPN alone doesn’t guarantee complete anonymity – other factors like cookies or user behavior can still reveal identity.
Despite these points, I firmly believe the benefits of a trustworthy VPN far outweigh the minor downsides for most people. This is especially true when you consider the enhanced privacy and security you gain.
11. Checklist: Do you really need a VPN?
A VPN is a powerful tool, but like any tool, its necessity varies from person to person. This brings us to a crucial question many people ask: Is a VPN necessary for me?
While I’m a strong advocate for VPN use, the honest answer is: It depends on your individual needs, online habits, and how much you value your digital privacy and security. To help you figure out the question “Do I need a vpn?” for your specific situation, ask yourself and consider the following checklist.
| Question | Yes | No |
|---|---|---|
| Do you frequently use public Wi-Fi networks (e.g., at cafes, airports, hotels, libraries)? | ☐ | ☐ |
| Are you concerned about your Internet Service Provider (ISP) tracking your online activity or collecting your browsing history? | ☐ | ☐ |
| Do you want to access content that is geographically restricted (e.g., online streaming platforms, websites)? | ☐ | ☐ |
| Do you handle sensitive information online, such as personal data, financial transactions, or confidential work documents? | ☐ | ☐ |
| Do you simply want an extra layer of security and privacy for your everyday online activities? | ☐ | ☐ |
For me, I view using a VPN as a fundamental part of good digital hygiene in today’s world. For me, it’s become a daily habit, much like locking my front door. It provides that essential layer of protection and freedom, whether I’m working, banking, streaming, or just casually browsing. It gives me peace of mind knowing my connection is more secure and my online footprint is less exposed.
However, you need to weigh these benefits against your own online behavior and concerns. If you answered “yes” to several of these questions, then incorporating a VPN into your online routine is likely a very good idea. The more “yes” answers you have, the more benefits you stand to gain.
>> Read more: How to set up a VPN on any device in 3 simple steps

12. Do VPNs block ads, trackers, or malware?
This is a fantastic question, and the answer has changed a lot over the last few years. Traditionally, the answer was a simple “no”. A standard VPN’s only job is to encrypt your connection and hide your IP address. It didn’t look at the content of your traffic, so it wouldn’t know if that traffic was an ad, a tracker, or a piece of malware.
However, the VPN market is incredibly competitive. To stand out, many top-tier VPN providers have built extra security features directly into their apps. So, the modern answer is: no, not by default, but many of the best VPNs now offer these features as part of their subscription.
Here’s how they typically work:
- Ad Blocking: This feature works at the network level. The VPN identifies and blocks requests to domains that are known to serve advertisements. The result? A cleaner, faster browsing experience with fewer annoying pop-ups and banners, especially on mobile.
- Tracker Blocking: Similar to the ad blocker, this feature prevents your device from communicating with known third-party tracking domains. This stops companies like Google and Meta from following you across different websites to build a profile of your browsing habits. It’s a huge boost for your day-to-day privacy.
- Malware & Phishing Protection: This acts as a first line of defense. The VPN maintains a blacklist of websites known to be dangerous – sites that host malware, attempt to phish for your passwords, or engage in other malicious activities. If you try to visit one of these sites, the VPN will block the connection before it can do any harm.
Important: While these features are incredibly useful, you need to remember one critical thing: a VPN’s malware blocker is not a replacement for a dedicated antivirus program.
The VPN can prevent you from visiting a known dangerous website, but it can’t scan files on your computer. It also cannot protect you from threats that arrive through other means, such as a malicious email attachment. For complete protection, you should always use both.
13. Mobile VPN: How VPN works on phones
Your phone is your life, and it’s constantly online, hopping between your home Wi-Fi, the coffee shop’s public network, and your cellular data plan. Each of those networks presents a different risk, making a VPN on your phone arguably even more important than on your desktop.
The good news is that using a VPN on a mobile device is incredibly simple and works just like it does on a computer: It creates a secure, encrypted tunnel for all the internet traffic leaving your phone.
13.1. How a VPN works on iPhone and Android
Getting started is surprisingly simple. Both iOS (iPhone) and Android have built-in support for VPN connections, which makes the setup process seamless.
You don’t need to mess with any complicated settings. You simply:
1. Choose a reputable VPN provider and sign up for a plan. Download their official app from the Apple App Store or Google Play Store.

2. Log in with your credentials.
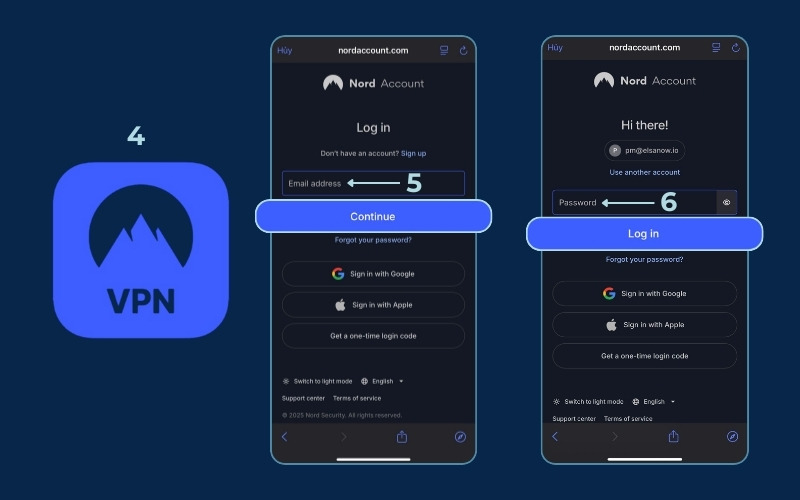
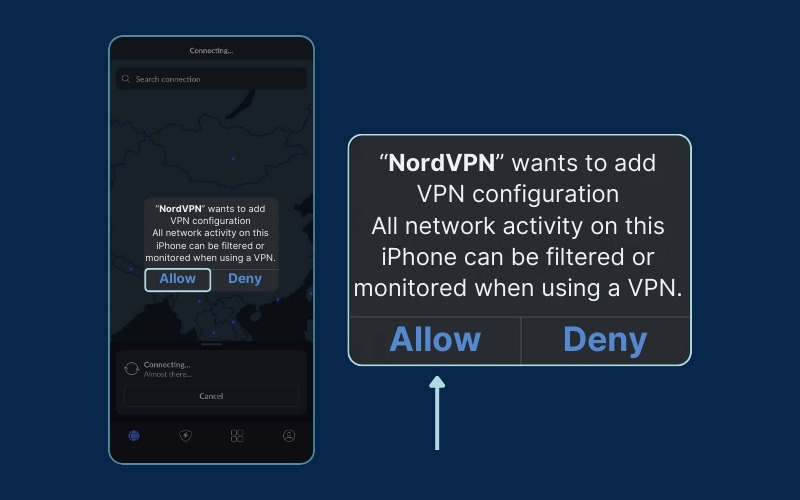
3. Allow the app to add VPN configuration on your phone.
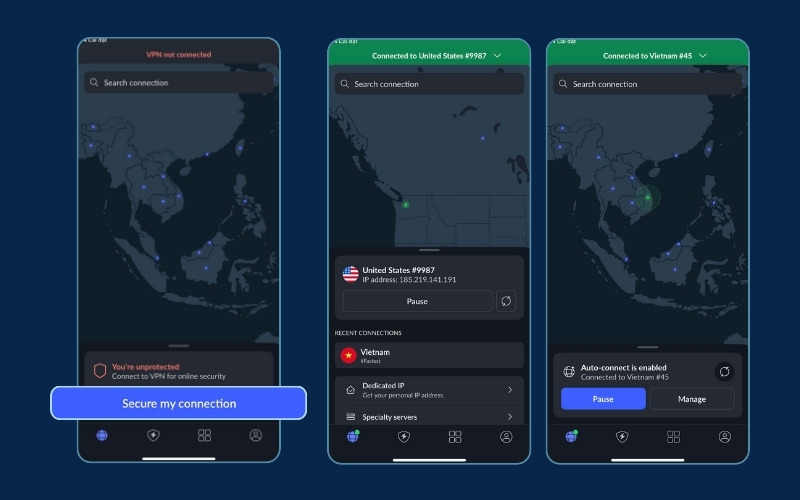
4. Tap the Connect button.
The app handles all the heavy lifting for you, choosing the best server and protocol. Once connected, you’ll see a small VPN icon in your phone’s status bar. This indicates that your entire connection is secured, from your web browser to your banking and social media apps.
>> Find out:
13.2. Does a VPN work on cellular data and Wi-Fi?
Yes, and you should absolutely use it on both.
Most people know to use a VPN on public Wi-Fi. That coffee shop or airport network is notoriously insecure, making it easy for hackers on the same network to snoop on your activity. A VPN is essential protection in these environments.
But what about your 4G or 5G connection? While your cellular data is more secure than public Wi-Fi, your mobile carrier (like AT&T, Verizon, or T-Mobile) can still see every website you visit. They often use this data for targeted advertising. A VPN encrypts your connection on any network, hiding your activity from your mobile carrier just as effectively as it does from hackers on public Wi-Fi.
13.3. Does a VPN drain your phone’s battery?
This is a common concern, and it’s not entirely untrue. Because a VPN is constantly working in the background to encrypt and decrypt your data, it does require some processing power, which in turn uses the battery.
However, the impact is much smaller than you might think, especially with modern VPNs. Here’s why:
- Efficient protocols: Newer protocols like WireGuard were designed from the ground up to be lightweight and energy-efficient, making them perfect for battery-powered devices.
- Optimization: Top VPN providers have spent years optimizing their apps to minimize battery consumption.
In my experience, the battery drain is minimal – often less than leaving a social media app running in the background. The massive boost in privacy and security you get is well worth the tiny hit to your battery life.
14. FAQ about VPN
What is a VPN, and why do I need it?
A VPN, or Virtual Private Network, is a service that encrypts your internet traffic and hides your IP address. You might need it to enhance your online privacy, secure your data (especially on public Wi-Fi), bypass geo-restrictions, and prevent tracking by your ISP or advertisers.
How does a VPN work?
A VPN establishes a secure, encrypted tunnel between your device and a remote server. All your online traffic passes through this tunnel before reaching the internet, replacing your real IP address with the server’s and protecting your data from prying eyes.
Is there a downside to using a VPN?
Potential downsides can include a slight reduction in internet speed, some websites or services blocking VPN connections, and the cost of reputable paid VPN services. However, for most users, the benefits outweigh these minor issues.
Are VPNs legal to use?
Yes, using a VPN is legal in most countries. However, using a VPN to engage in illegal activities is still illegal. Always be aware of your local laws.
Can a VPN make me 100% anonymous online?
No, a VPN significantly enhances your anonymity, but it cannot make you 100% anonymous. Other factors like browser cookies, device fingerprinting, and your own online behavior can still affect your anonymity.
Will using a VPN slow down my internet connection?
It can, slightly, due to the encryption and routing processes. However, with good VPN providers and by choosing a server close to you, the speed difference is often negligible. Sometimes, it might even improve speeds if your ISP throttles certain traffic.
Are VPNs free, or do I have to pay?
Both free and paid VPNs exist. Free VPNs often come with limitations (speed, data, and servers) and potential privacy risks. Paid VPNs generally offer better security, performance, and features.
How do I know if I have a VPN connection?
Most VPN apps will clearly indicate when you are connected. You can also check your IP address online (e.g., by searching “what is my IP”) before and after connecting to the VPN. If the IP address changes (and shows the VPN server’s location), your VPN is working. If not, maybe your VPN not connecting.
What’s the difference between a VPN and a proxy?
Both can hide your IP address, but a VPN encrypts all your internet traffic, offering system-wide security and privacy. Proxies usually only work for specific applications (like a web browser) and may not offer robust encryption.
Can VPNs be used on all my devices?
Yes, most reputable VPN providers offer a dedicated VPN client (the app you install) for a wide range of devices. It includes VPN on computers (Windows, macOS, Linux), smartphones (like VPN on iPhone and VPN on Android), tablets, and even routers.
How VPN protect you?
A VPN protects you by encrypting your internet connection and hiding your real IP address. It also prevents ISPs, hackers, and advertisers from tracking your activities or intercepting your data.
What does a VPN do?
A VPN secures your internet connection and enhances your online privacy by masking your IP address. It also encrypts your data to protect it from snooping and allows you to bypass content moderation and geo-restrictions.
Does a VPN protect you from hackers?
Yes, but only against specific types of attacks. A VPN is extremely effective at protecting you from “man-in-the-middle” attacks on public Wi-Fi, where a hacker tries to intercept your data. By encrypting your connection, the VPN makes your data unreadable to them.
However, a VPN is not an antivirus. It cannot protect you if you download malware, click on a phishing link, or if a hacker gains access to your device through other means.
Does a VPN hide your browsing from Google?
No, not if you are logged into your Google account. A VPN successfully hides your real IP address from Google, so they won’t know your physical location.
But if you are signed into Chrome, Gmail, or YouTube, Google still knows exactly who you are and will continue to track your searches and activity through your account. To browse with more privacy from Google, you would need to use a VPN and log out of your Google account (or use incognito mode).
Does a VPN use more data?
Yes, but the increase is very small. The process of encrypting your data adds a little bit of “overhead” to your connection. This typically increases your total data usage by about 5% to 15%.
For most people with unlimited data plans, this is unnoticeable. You would only need to be mindful of it if you are on a very limited mobile data plan.
15. Conclusion
Understanding what is a VPN and how it operates is the crucial first step towards actively taking control of your online privacy and security. In summary, a VPN offers several key advantages:
Considering a VPN isn’t just for tech experts; it’s for anyone concerned about protecting their digital footprint in today’s interconnected world. As you continue to explore and choose the best solution for your needs, Safelyo invites you to delve deeper into our other informative Blogs within the Privacy & Security Basics section.